
In this article, LMNTRIX Labs will focus on the ransomware group “Cl0p” – an extortionist Ransomware group who were operating and targeting companies from 2019. The Cl0p ransomware group techniques and tactics resemblance with TA505 a financially motivated threat group active since 2014.
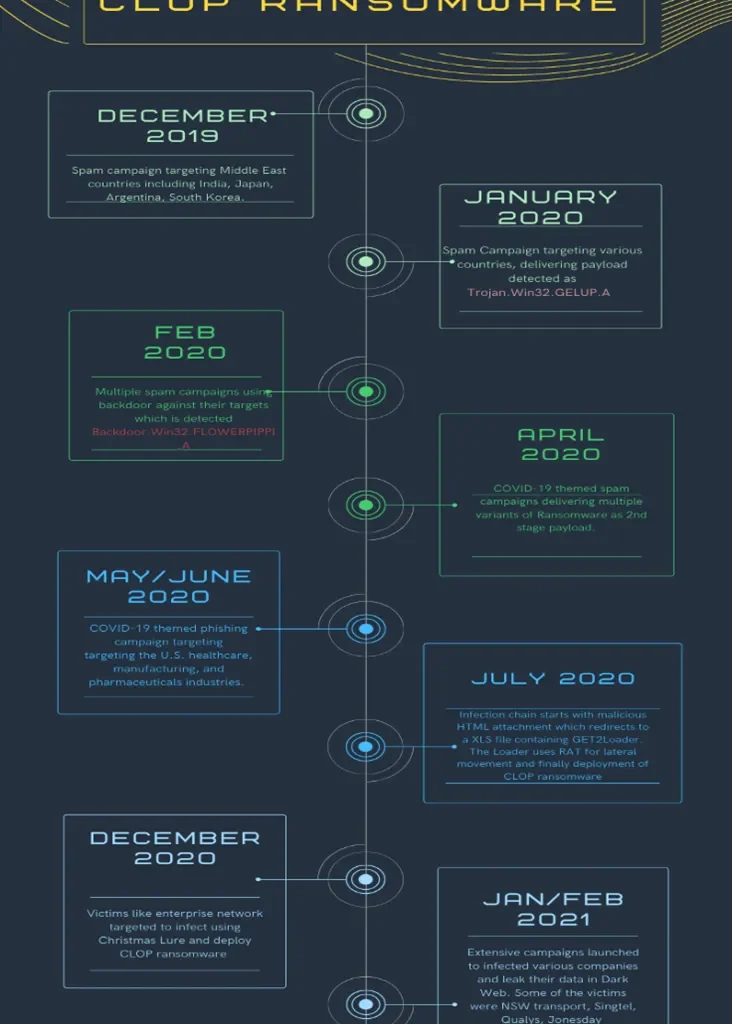
In recent days, LMNTRIX Labs have observed an increased activity of the Cl0p ransomware gangs targeting multiple enterprises, companies across the globe. Following is their activity timeline from the last two years. This particular group has been visibly active throughout COVID-19 spike phases and targeted pharmaceutical companies extensively. Interestingly, the Accellion breach which was reported due to a FTA vulnerability exploitation was also linked to the Cl0p ransomware group.
Activity Timeline
Sample Analysis
Following sample was recently used by the Clop Ransomware group in their latest campaign
SHA256: 15f9ed36d9efc6e570b4f506791ce2c6a849853e2f6d587f30fb12d39dba2649
Sample Name: Ul7Koup6DD.bin
Process path: C:\Users\Xmp\Desktop\hfq3LofMt4.exe
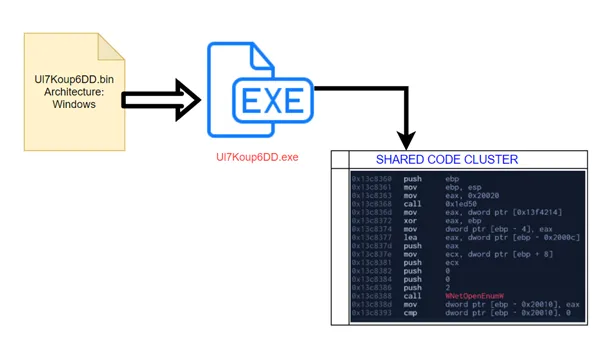
Analysing the sample, we have seen the malicious binary is sharing the code among all the samples seen for the Cl0p ransomware sample. Around 480+ strings reuse by the sample has also been observed.
Related Sample
| Sample Timeline | SHA256 |
| Feb 2021 | 09ab880f3021ac2d05e09bebd567ddf5f6f7cfb396573efd819a056931f3b391 |
| Dec 2019 | cff60c9c30bf71112c79f788c4ccbd7151285d52be31c8e891b365d93a7e241d |
| Nov/Dec 2020 | 7c19c49836ed7dccd0ebcd5a5a56f6b6411ecc59fdc7fa31f0ee0f64eee7aa89 |
| Dec 2020 | 7c6e5cd61fafd38e420c2bd9e12ed1ec06e31dd5d20c081d214a96c16b1492c8 |
| Jan 2021 | 968307a367471e25bef58b0d4687ab4fdf34539bbfb603b5b19ae99d4d0c0340 |
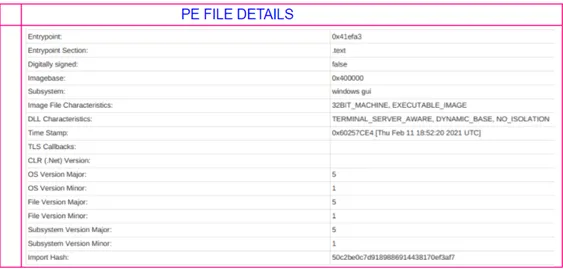
The ransomware program is written in C ++ and developed in Visual Studio. So far observed Cl0p samples are for the x86 architecture. The size of the unpacked sample is between 100 and 200 KB. Cl0p renames the encrypted files and appends the file ending with (“. Cllp ” OR “. CI0p”.)
MITRE MATRIX
Attribution
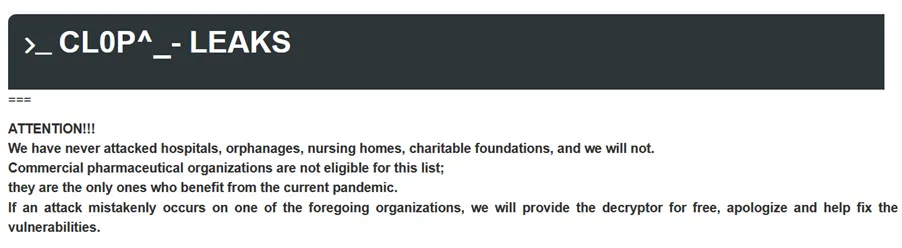
The modus operandi of the gang has been to use the double extortion technique. They use lateral movement technique to exfiltrate large amount of victim’s data from their network and then finally launches the Ransomware. This is a full proof method, that even though the victims have a backup of their data, and refuse to pay the ransom, the Gang still threatens to leak the data stolen onto their dark Web leak site as shown below. The gang also uses a chat site to chat with their victims to fix the extortion amount.
NSW Transport’s terabytes of data was leaked onto the Dark Web in a similar fashion, when it was dumped in 9 different parts. These include contract details, email communications, and much more. Here is the snapshot from the NSW Transport leak:
Mitigation
*****YARA RULE FOR CLOP RANSOMWARE************************
rule win_clop_auto {
meta:
date = “2021-2-21”
version = “1”
/* DISCLAIMER
* The strings used in this rule have been automatically selected from the
* disassembly of memory dumps and unpacked files, using .
strings:
$sequence_0 = { 68???????? 68???????? e8???????? 83c424 6aff }
// n = 5, score = 300
// 68???????? |
// 68???????? |
// e8???????? |
// 83c424 | add esp, 0x24
// 6aff | push -1
$sequence_1 = { ffd0 c3 8bff 55 8bec 83ec1c 8d4de4 }
// n = 7, score = 300
// ffd0 | call eax
// c3 | ret
// 8bff | mov edi, edi
// 55 | push ebp
// 8bec | mov ebp, esp
// 83ec1c | sub esp, 0x1c
// 8d4de4 | lea ecx, [ebp – 0x1c]
$sequence_2 = { 6a04 6800300000 6887000000 6a00 }
// n = 4, score = 300
// 6a04 | push 4
// 6800300000 | push 0x3000
// 6887000000 | push 0x87
// 6a00 | push 0
$sequence_3 = { 8d85bcefffff 50 ff15???????? 68???????? }
// n = 4, score = 300
// 8d85bcefffff | lea eax, [ebp – 0x1044]
// 50 | push eax
// ff15???????? |
// 68???????? |
$sequence_4 = { ff15???????? 68???????? 8d85dcf7ffff 50 }
// n = 4, score = 300
// ff15???????? |
// 68???????? |
// 8d85dcf7ffff | lea eax, [ebp – 0x824]
// 50 | push eax
$sequence_5 = { 6a00 ff15???????? 68???????? 8bd8 }
// n = 4, score = 300
// 6a00 | push 0
// ff15???????? |
// 68???????? |
// 8bd8 | mov ebx, eax
$sequence_6 = { e8???????? 83c408 6aff ff15???????? 33c0 }
// n = 5, score = 300
// e8???????? |
// 83c408 | add esp, 8
// 6aff | push -1
// ff15???????? |
// 33c0 | xor eax, eax
$sequence_7 = { 8d85c8efffff 50 6a08 6a01 ff15???????? 85c0 }
// n = 6, score = 300
// 8d85c8efffff | lea eax, [ebp – 0x1038]
// 50 | push eax
// 6a08 | push 8
// 6a01 | push 1
// ff15???????? |
// 85c0 | test eax, eax
$sequence_8 = { 83c40c 33f6 85ff 7428 }
// n = 4, score = 300
// 83c40c | add esp, 0xc
// 33f6 | xor esi, esi
// 85ff | test edi, edi
// 7428 | je 0x2a
$sequence_9 = { 53 8bf8 ff15???????? 8bf0 56 6a40 }
// n = 6, score = 300
// 53 | push ebx
// 8bf8 | mov edi, eax
// ff15???????? |
// 8bf0 | mov esi, eax
// 56 | push esi
// 6a40 | push 0x40
$sequence_10 = { 83c40c 6860070000 6a40 ff15???????? }
// n = 4, score = 300
// 83c40c | add esp, 0xc
// 6860070000 | push 0x760
// 6a40 | push 0x40
// ff15???????? |
$sequence_11 = { 8bf0 56 53 ff15???????? 50 ff15???????? 56 }
// n = 7, score = 300
// 8bf0 | mov esi, eax
// 56 | push esi
// 53 | push ebx
// ff15???????? |
// 50 | push eax
// ff15???????? |
// 56 | push esi
$sequence_12 = { 53 56 ff15???????? 56 ff15???????? 53 ff15???????? }
// n = 7, score = 300
// 53 | push ebx
// 56 | push esi
// ff15???????? |
// 56 | push esi
// ff15???????? |
// 53 | push ebx
// ff15???????? |
$sequence_13 = { 50 ff15???????? 56 53 8bf8 ff15???????? }
// n = 6, score = 300
// 50 | push eax
// ff15???????? |
// 56 | push esi
// 53 | push ebx
// 8bf8 | mov edi, eax
// ff15???????? |
$sequence_14 = { 83c424 53 50 ffd6 }
// n = 4, score = 300
// 83c424 | add esp, 0x24
// 53 | push ebx
// 50 | push eax
// ffd6 | call esi
$sequence_15 = { 50 e8???????? 83c40c c785f0efffff00080000 8d85f0efffff c785ecefffff00000000 c785f4efffff00000000 }
// n = 7, score = 200
// 50 | push eax
// e8???????? |
// 83c40c | add esp, 0xc
// c785f0efffff00080000 | mov dword ptr [ebp – 0x1010], 0x800
// 8d85f0efffff | lea eax, [ebp – 0x1010]
// c785ecefffff00000000 | mov dword ptr [ebp – 0x1014], 0
// c785f4efffff00000000 | mov dword ptr [ebp – 0x100c], 0
condition:
7 of them and filesize < 630784
}
____________________________XXXXXXXXXXXXXXXXX_______________________________________


