
Are QR Codes safe to use, or can your mobile phone be hacked using QR codes? Let’s be clear – QR codes by themselves can only be tampered with, altered, or generated, they can NOT be hacked. They can be used by thieves as a novel attack vector to enable a malicious hacking attempt. For this reason, security researchers at LMNTRIX feel it’s best to avoid making payments with QR codes.
QR Code – Quick Response Code
QR Codes, or Quick Response Codes, have gained immense popularity globally. Originally developed by Toyota’s subsidiary – Densowave for tracking vehicle parts in the 1990s, these codes have become ubiquitous for internet users in 2021/22. By scanning these distinctive barcodes using your smartphone’s camera, you are swiftly directed to websites offering product information, videos, and touchless payments post-COVID. However, the widespread use of QR codes has opened a door for cyber threats, necessitating a vigilant approach, such as cloud security assessment, to mitigate potential risks associated with phishing campaigns and unauthorized access attempts

Another cause for concern is malicious software can be embedded on the website, and deployed using QR codes. This A concerning aspect of cybersecurity intelligence is the potential for malicious software embedded on websites and deployed through QR codes. Cyberthreat intelligence reveals that the QR code’s associated URL may coax victims into downloading seemingly harmless files, ultimately installing malware. In sophisticated cases, victims may not initiate downloads willingly but can be forced through manipulated QR codes. The shellcode and delivery mechanisms vary, adapting to each mobile phone’s make, model, and operating system. Staying informed about cyber threat intelligence is essential to comprehend and counter evolving cybersecurity risks

We have outlined a few scenarios, that cybercriminals often employ with QR codes,
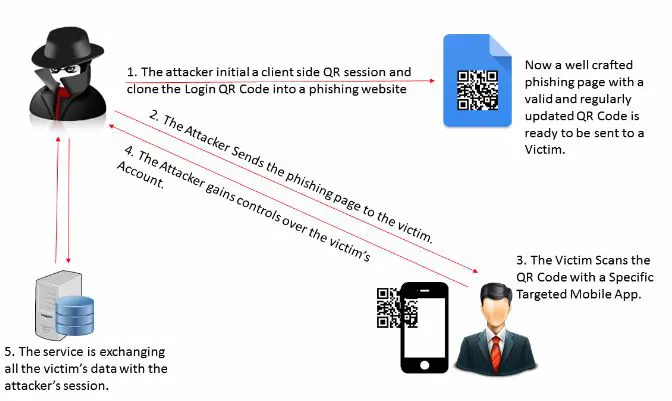
- Phishing Attacks: Since QR codes are more likely to breach standard email protection, they can also be used in email as part of a larger social engineering attack. When users scan their codes, they are taken through a process in which they must eventually enter their credentials or other information.
- Cybercriminals have used a simple QR code trick to replace original codes placed by a company at a specific touch point with fake/counterfeit codes. When users scan the fake QR code, they are redirected to a phishing site or see an i-frame pop-up that allows malware to be installed.
- Scanning a malicious QR code mirrors the risk of clicking on a malevolent link in a traditional social engineering attack. Cybercriminals employ social engineering tactics, combining QR codes with enticing text like “Scan to win an iPhone 14 Pro Max,” to deceive individuals into scanning and compromising their devices. Exploiting curiosity, these codes may be strategically placed in high-traffic areas within an organization, often with minimal accompanying text. Implementing effective managed detection response is crucial to promptly identify and neutralize such threats, ensuring robust cybersecurity in the face of evolving attack vectors
- Clickjacking attacks: Clickjacking is another method used by cyber criminals to redirect users who scan a QR code to a credible-looking website with actionable content, such as buttons that encourage visitors to click through. In most cases, they result in the installation of malware on your device or other forms of private information being stolen.
- Financial theft: Cyber criminals can use QR codes as a payment method, placing a QR code as a form of payment, but having your money sent to their bank account. Cybercriminals follow up by then swindling a higher amount as part of an incremental theft scheme.
According to a survey by LMNTRIX, more than 89% of end users were not able to differentiate one QR code from the other. Error correction built-in to QR codes allows even malicious QR codes to resemble the original, and a fake QR code can end up redirecting the helpless user to a phishing page, a page with malicious code, or a drive by download.
QR codes have become more popular in today’s customer-centric world. QR codes are no longer limited to their original purpose of tracking inventory in factories. They’re now used for everything from marketing, real estate, and digital business cards to smart packaging while COVID amplified their use ubiquitously in more restaurants than one could have ever imagined. We need to understand the risks and limitations of this mechanism. After scanning a QR Code, just like with phishing emails “check the URL you are redirected to for typos, or misplaced letters”, before blindly clicking OK. For physical QR codes, the real challenge is to spot tampered QR codes with the naked eye.
Conclusion
You don’t have to take our word for it, if all this sounds like a theoretical joke, check out this talk from Defcon 29 – Old MacDonald Had a Barcode, E-I-E-I CAR, or https://www.kitploit.com/2019/04/qrljacker-v20-qrljacking-exploitation.html – a framework now available in Kali Linux. Such frameworks bring down the barrier to perform social engineering attacks, while reiterating our message – slow down and think twice when using QR codes. Go with your intuition, always consider the source and slow down when scanning a QR code; if you think a QR code is suspicious don’t use it. Installing a mobile antivirus, cleaning tool and a security tool to filter links by reputation, and lastly setting up alerts with your bank to flag unauthorised payments, and/or suspicious activity may help in reducing instances of QR code exploitation.


