
Amongst COVID-19 related campaigns being carried out by multiple threat actors, multiple others are targeting Australian users to carry out credential harvesting & data stealing, to conduct financial fraud & to install malware.
As the lodgement for tax return has started from July 2020, threat actors are actively targeting Australian users by impersonating the Australian Taxation Office & myGov via Email & SMS phishing campaigns. While another focus has been fraud and scams against users of financial services such as National Australian Bank, AIB, American Express and others.
Threat Type: Spam, Phish, Spearphishing, SMShing, Credential Harvesting
MITRE ATT&CK – Techniques Used –
- 001 – Phishing: Spearphishing Link – T1566.001
- 002 – Phishing: Spearphishing Attachment – T1566.002
- T1102 – Web Service
- T1528 – Steal Application Access Token
How does the scam work?
Phishing scams are attempts by threat actors to trick users into giving out personal information such as bank account numbers, passwords and credit/debit card numbers.
The threat actor contacts a user pretending to be from a legitimate business such as a Government department, a bank, telephone, internet service provider. There are multiple mediums like email, social media, phone call, or text message, by which an actor scams the users.
The actor may alert the user to ‘unauthorised or suspicious activity on his account’. Or the user might be informed that his tax return has been lodged and certain amount is ready to get credited in bank account after confirming the baking details – bank account number and credentials. In some cases, the actors may already have user’s credit/debit card number and ask him to confirm his identity by quoting the 3- or 4-digit security code (CVV) printed on the card.
If user provides the actor with his details online or over the phone, they will use them to carry out fraudulent activities, such as stealing or transferring the money online using banking details.
Technical Analysis
Phishing is an attempt to lure the user into giving out their personally identifiable information (PII) and/or financial details. Whereas Spear phishing is an email or electronic communications scam targeted towards a specific individual, organization or business. Although often intended to steal data for malicious purposes, cybercriminals may also intend to install malware on a targeted user’s computer.
LMNTRIX Labs has identified the actors utilizing various Phishing & Spearphishing techniques. This phishing has taken the form of:
- links to credential harvesting websites
- emails with links to malicious files, or with the malicious file directly attached
- links prompting users to grant Office 365 OAuth tokens to the actor
- use of email tracking services to identify the email opening and lure click-through events.
Here are the few examples of recent phishing scams discovered –
1. SMS Phishing (SMShing)
One of the recent SMS scam campaigns looks like they have come from a myGov or ATO. They also might appear in user’s legitimate ATO or myGov SMS message thread.
SMS Scam campaign begins with –
- A scam SMS containing a malicious shortener URL with message showing some urgency related to ATO or MyGov.
- Upon clicking on the Shortener URL, it redirects to malicious phish page crafted similar to ATO or myGov to lure users and steal credentials.
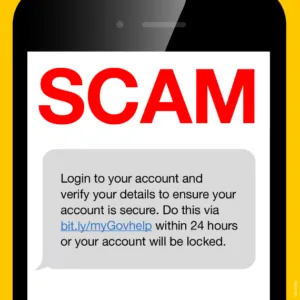
Image 1: myGov SMS Scam
Note: Don’t click any links and don’t provide the information requested.
Malicious Links used in Scam –
Original Shortener URL: hxxp://bit[.]ly/myGovhelp
Long (redirected) URL: hxxp://mygov-secure-au[.]com/
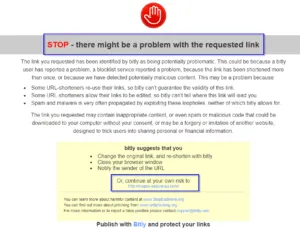
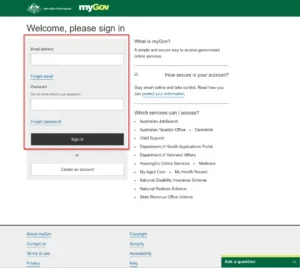
If a user clicks on the link given in an SMS, he will be redirected to a phishing page of myGov as shown in Image 3. But as the phishing domain has been detected by 3rd party security software, Bitly (a URL shortener service) has also started showing warning that the given link is suspicious in nature as shown in Image 2.
Upon further analysis, LMNTRIX Labs found that the domain used in phishing is being detected as malicious by multiple security vendors including Google Safebrowsing as on 9th of August. But still many vendors were not detecting the same domain as malicious.
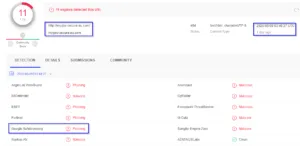
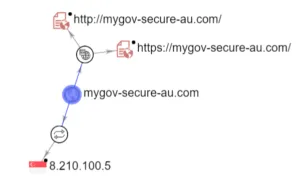
Image 5: VirusTotal Phishing Domain Graph
We can also observe the domain graph (connection between domain & IP) for the specific myGov phish domain. Domain is hosted on a Singaporean IP (8.210.100[.]5), which also hosts multiple other phishing domains for Office 365, ANZ & AIB banking, and multiple others as shown in Image 6.
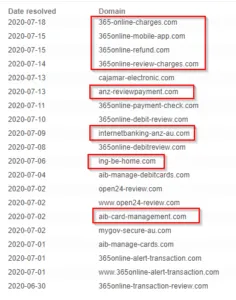
Another example of SMShing scam for ATO where actors lure users by showing fake tax refund message with malicious phish link.

Note: Don’t click any links and don’t provide the information requested.
Malicious Links used in Scam –
Phishing URLs : hxxp://ato.gov.au.txreturn[.]info/ & hxxp://webmail.txreturn[.]info/
Domain : hxxp://txreturn[.]info/
2. Email Phishing
In another scam, various threat actors are targeting users via fake ATO, myGov verification or refund notices through scam emails with attachments.
Here are few more scams of PDF & Excel phishing by imitating ATO / myGov.
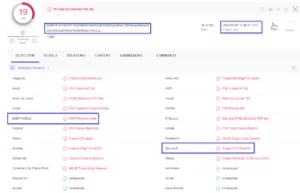
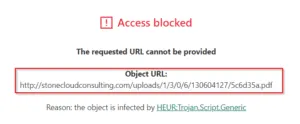
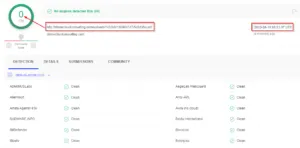
In another scenario, a threat actor leverages a phishing mail containing malicious office file as attachment to initiate an attack. They make use of social engineering (E.g. ATO Indirect Tax Concession Scheme – ITCS) as a bait to lure the victim into enabling the macros. Once the macro gets executed, it downloads malicious payload intended to steal data on a targeted user’s computer.
Threat actors continue to deliver the malicious macro enabled excel files as attachments via spear-phishing emails as shown below.

Actor luring user to enable macro to infect the system with malicious payload


In another phishing scam, actor tweaks a fake Captcha with malicious pdf link inside a scam pdf as shown below.
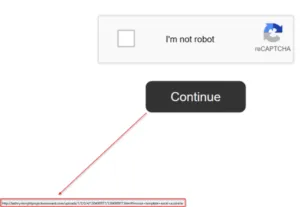
Here actor is not only faking captcha but also giving multiple fake pdf (embedded with links) to lure a user to click on any of those documents which redirect the user to phishing / scam websites.

As part of phishing scams, few threat actors are targeting users by imitating Australian banks & companies.
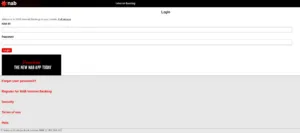
Intention behind the Phishing Scams
Through phishing, actors steal confidential information such as online banking logins, credit card details, business login credentials, passwords/passphrases, by sending fraudulent messages. Additional trojans and malware infections can also be installed to exfiltrate data in future.
In 2019, phishing was the most common method for scamming, with 25,168 reports. 513 of those reported resulted in a financial loss, valued at AU$1.5 million.
The greatest losses in 2019 by type of scam were:
- AU$132 million to business email compromise (BEC) scams,
- AU$126 million to investment scams, and
- AU$83 million lost to dating and romance scams.
Indicator of Compromise (IOC)
MITRE ATT&CK
Attack: Phishing: Spearphishing Link/Attachment
Platforms: Linux, Windows, macOS
Tactic: Initial Access
Techniques:
- 001 – Phishing: Spearphishing Link – T1566.001
- 002 – Phishing: Spearphishing Attachment – T1566.002
- T1102 – Web Service
- T1528 – Steal Application Access Token
Threat Actors may send phishing messages to elicit sensitive information and/or gain access to victim systems. All forms of phishing are electronically delivered via social engineering.
Threat Actors may send victim’s emails containing malicious attachments or links, typically to execute malicious code on victim systems or to gather credentials for use of Valid Accounts. Phishing may also be conducted via third-party services, like social media platforms.
How to protect from Phishing?
Phishing emails have become increasingly sophisticated since the online banking, shopping and business transactions have increased in last 15 years.
Here are few steps to protect from phishing –
- Ensure anti-virus software and associated files are up to date.
- Search for existing signs of the indicated IOCs in your environment.
- Block all URL and IP based IOCs at the firewall, IDS, web gateways or other security perimeter-based devices.
- Do not click or open links from unsolicited emails.
- Train end-users for securityawareness to flag suspicious behaviour such as phishing emails or social engineering attempts.
Scam Reporting (Australian Government)
If you’re not sure if an ATO interaction is genuine, don’t reply to it. Instead:
- Phone on 1800 008 540 and report it.
- Visit Verify or report a scam, which explains how to spot and report a scam.
- Report fraudulent SMS or Email to reportemailfraud@ato.gov.au.
- Report an SMS or email that looks like it’s from myGov but it contains a link or appears suspicious, email reportascam@servicesaustralia.gov.au.
- If you have clicked on a link or provided your personal information, contact Services Australia on 1800 941 126.
References
- https://exchange.xforce.ibmcloud.com/collection/Phishing-Australia-0ab129d0b6cf194e3eb2c45f09a16dc7
- https://www.ato.gov.au/general/online-services/identity-security/scam-alerts/
- https://urlscan.io/search/#mygov-secure-au.com
- https://urlscan.io/result/302e17b3-7a4b-4531-ba4e-1157dce02ef7/#summary
- https://www.virustotal.com/gui/domain/mygov-secure-au.com/detection
- https://www.virustotal.com/gui/domain/txreturn.info/detection


