
From start of 2020, there has been an increased activity of Conti Ransomware variant targeting our client networks across industries such as Financial Institutions, Healthcare, multiple Critical infrastructures in southern California – disrupting plant operations and government institutions. However, it is not yet clear if any OT specific asset/operation has been impacted by this variant.
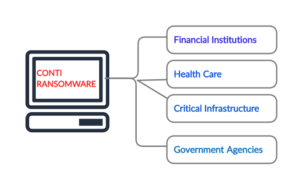
Conti is a new variant of ransomware observed in the wild by our threat research team. Unlike most ransomware, Conti contains unique features that separate it in terms of performance and focus on network-based targets.
The initial analysis of Conti Ransomware shows various aspects of attribution towards the Ransomware families Ryuk and Hermes which were both seen in the wild from 2018. This variant of Ransomware raises sharp speculation that like its predecessor, Ryuk ransomware, will also target the Critical Infrastructures and Key Partner (CKIP) sector. Technicality, the trade craft adopted by Conti ransomware mimics the Ryuk campaign starting from the delivery method, payload execution, threat actor’s communication method, such as autogenerated random email addresses. Furthermore, the attackers behind the Conti ransomware have also been known to threaten to leak their victim’s data as part of their ransom collection strategy, which we experienced first-hand at one of our CKIP clients.
Conti Ransomware features:
- The ransomware uses independent threads to perform faster than average encryption rates, with up to 32 simultaneous encryption efforts.
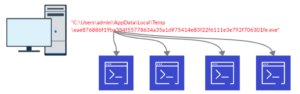
- The Windows Restart manager has been used for the application shutdown and ready to be encrypted.
- The command “net stop” has been used extensively to stop installed antivirus, database and backup solutions.


- The strategic and common move for any ransomware, clearing of Shadow Volume copies for the file encryption initiation.

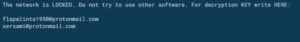
- The encrypted files includes “.conti” extension and the readme file dropped from the process is being placed in each application folder, with a following note:
- EXECUTION
(T1059- Command Line Interface): Starts cmd.exe for commands execution
(T1035- Service Execution): Starts net.exe for service management.
- DISCOVERY
(T1007- System Service Discovery): For system services used the command “net stop” to kill the designated services.
- IMPACT
(T1490- Inhibit System Recovery): A number of native Windows utilities have been used by adversaries to disable or delete system recovery features:
vssadmin.exe can be used to delete all volume shadow copies on a system –
vssadmin.exe delete shadows /all /quiet
Adversary Hunting Rules:
Following are some of the EQL queries, which can be used to hunt the Conti ransomware related activities in a endpoint and should raise alarms among the security team:
- process where subtype.create and process_name == “vssadmin.exe” and command_line == “*delete shadows*”
- process where subtype.create and process_name== “net1.exe” and command_line== “*stop Acrnois VSS provider*”
- process where subtype.create and process_name == “vssadmin.exe” and command_line == “* resize shadowstorage /for=c: /on=c: /maxsize=unbounded*”
Indicators of Compromise:
| Hashes | Hash Type |
| 596f1fdb5a3de40cccfe1d8183692928b94b8afb | Hash/SHA-1 |
| b7b5e1253710d8927cbe07d52d2d2e10 | Hash/MD5 |
| eae876886f19ba384f55778634a35a1d975414e83f22f6111e3e792f706301fe | Hash/SHA-256 |
| da778748ef41a4482da767de90e7ae2a8befa41e | Hash/SHA-1 |
| 61653b3cd1a290bbc531181edec807b20e263599aa6a2908dc259b867ec98297 | Hash/SHA-256 |
| 67f9404df22c6b1e82807f5c527805083f40b70b9dac6bc27c2583b70de17390 | Hash/SHA-256 |
| 6b1b4bbff59456dfaa3307a20171fd7394f49a5f6d1b3cd59392ba41e4881878 | Hash/SHA-256 |
| 749c4c343978b9f236838034f868dac937fdfd9af31a6e5dd05b993a87d51276 | Hash/SHA-256 |
| 895007b045448dfa8f6c9ee22f76f416f3f18095a063f5e73a4137bcccc0dc9a | Hash/SHA-256 |
Overall, Conti represents a unique twist in modern ransomware. LMNTRIX Labs have tracked numerous families that are designed to be driven by the adversary while on the network, with access gained through weak RDP access or vulnerable Internet-facing services. Conti shows an intention behind the actor to also respond to reconnaissance to determine worthwhile servers in the environment that are sensitive to data encryption. It’s implementation of multi-threaded processing, as well as the use of the Windows Restart Manager, shows a feature of incredibly quick, and thorough, encryption of data. The use of large-scale service termination supports this with a focus on targeting a vast array of backup applications that can be found all across the small business and enterprise fields.


