We come across data breaches daily, in the news, and in our professional careers. These can impact the biggest S&P 500 company or a much smaller start-up looking to change the world. Hackers are capable of stealing information about credit cards, personally identifiable information, and health records belonging to customers and staff. Worse yet hackers are capable of stealing an organisation’s intellectual property, the same property that grants any organisation an edge over the competition.
Being able to secure data, whether stored or being communicated over a distance, then is a major concern for private and public organisations, including military, law enforcement, and other government departments.
By utilising some of the weirder aspects of quantum physics, namely superposition, a whole new field of cryptography is being developed that promises important data is kept secure, even while in transit.
Quantum Communication
Anything regarding quantum physics leads to no small amount of head scratching. At the risk of grossly over simplifying the massively complex world of quantum communication, it makes use of some of the stranger aspects of quantum physics.
One such aspect is superposition. In quantum communication a photon of light, typically used as information carriers in fiber optic cables, can be any combination of 1s and 0s. Traditional communication meant that the photon had to be a 1 or a 0 and not a combination of them. In quantum communication this ability for a photon to be a combination of 1s and 0s represents a quantum bit of information, referred to a qubits.
The big advantage for cybersecurity purposes of sending information using qubits is that they are “super fragile”. This means that if a hacker tries to intercept the information, it is observed and collapses to either a 1 or a 0. The collapse of the qubit to a simpler 1 or 0 leaves a telltale sign that someone was trying to incept the message. The collapsing of the quantum state central to the qubit effectively corrupts the information sent preventing the “would be” hacker from using the information for any malicious purpose.
Companies have looked to take advantage of quantum communication by creating, at least in theory, ultra-secure communication networks. These networks make use of quantum key distribution (QKD) to create these secure communication networks.
Quantum Key Distribution
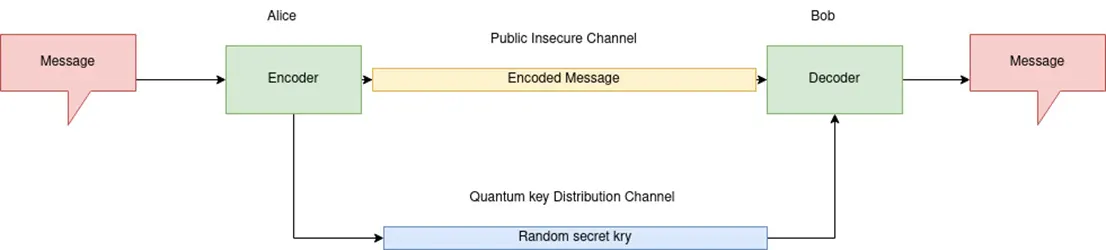
Quantum key distribution (QKD) is a hybrid of of more traditional encrypted communication and quantum communication. In QKD tradinitional bits of information are encrypted and sent over the network. The use of quantum physics comes in with the encryption key that is encoded into qubits and transmitted over a specialised QKD channel.
As the technology is still in its relative infancy several protocols have been developed in an attempt to standardise the varying approaches to QKD. Perhaps the most popular protocol is BB84. The protocol can be simplified by an example, say you need to send secure data to another computer. The person sending the data will create an encryption key which will be used to decrypt the actual message. The key is encrypted using qubits.
The data and the encryption key are then sent to the recipient and through a process of key sifting it can be determined that the key is the same for both the sender and receiver. The data can then be decrypted using the confirmed encryption key.
It should be noted that due to the fragile state of the qubits some will inevitably collapse. The trick then is to see what an acceptable error rate is and an error rate that would indicate a malicious actor was attempting to gain access to the encryption key. If the error rate is perceived to be too high a new encryption key is generated. This process can be repeated until an acceptable error rate is achieved and both parties are confident no hacker is attempting to access the encryption key.
Quantum Communication real-world applications
As many industries are dependent on the secure transfer of data and the legal requirements now in place to protect sensitive data QKD has seen real-world adoption. Although adoption has been limited due to cost constraints and several other factors it is interesting to see how specific industries are seeing value in quantum communication.
Banking Industry
ID Quantique has successfully introduced the use of quantum communication for securing crucial banking data. Banks contain sensitive client and proprietary information data, so securing data is one of the highest priority for the banking industry.
Banks also have to make sure that data is available quickly on a real-time basis. Key generation for authentication, secure access control, and digital signatures by quantum random generators for generating encryption keys, as an example, has successfully been used by IDQ.
Credit Card Industry
Credit Card Information is one of the most crucial digital footprints of an individual. If this footprint is available publically, it can cause a huge loss to an individual as well as the nightmare of identity theft. Annually, 14 billion dollars are lost to credit card fraud. This number highlights the problem faced by credit card companies like Visa and Master Card.
Quantum communications have tremendous potential for encrypting credit cards against threats. Research on Quantum computing-based credit card encryption holds potential to completely replace obsolete magnetic stripes and EMV.
The quantum communication-based security arrangement would use a strip of nanoparticles. A unique pattern is generated by a laser which is then sent to the nanoparticles. The pattern is hard to observe as it is created using the unique properties of quantum mechanics. This implies that the same super-fragile state of qubits can be used to secure card purchases. According to researchers, this can be a game-changing revolution in the credit card industry.
Government and Defense Industry
The government and defense industry holds incredibly sensitive data. From nation’s secrets to high valuable proprietary technology, highly sensitive data protection is the responsibility of the Government and Defense Industry. Securing this data can be of vital importance to a countries safety and security against foreign and local aggressors that Quantum communication offers.
Future of Secure Quantum Communication
Soon the backbone of the Internet and communications will the sub-atomic particles whose properties read more like science-fiction but are indeed science fact. It is clear that quantum technologies will play a fundamental part in our future.
The U.S. Department of Energy (DOE) allocated 625 million dollars in 2020 to set up several research labs that will harness the collective firepower of academia, government, and private companies to develop the quantum internet. To this extent they have developed a blueprint that points to what a possible quantum Internet will look like.
As far as QKD is concerned it is not without criticism. The current high cost for limited return is a major issue to be ironed out. In terms of the ultra-secure communication, experts have argued that the technology will still be vulnerable to some of today’s attacks methods. Other critics say QKD simply doesn’t go far enough. This is because QKD is designed to work with the conventional, non-quantum communications that are in use today. While QKD encrypts them with a quantum key, it doesn’t transform communications into actual quantum information.
The criticisms are important as they will need to be answered in the affirmative if QKD will be the dominant form of quantum communications in the near future.



[…] Secure Quantum Communication & Its Applications To Security – LMNTRIX Blog – https://lmntrix.com/blog/secure-quantum-communication-its-applications-to-security/ […]