
Cyber experts have continually developed and refined more advanced methods to combat cybercriminals in the realm of cybersecurity, a field characterized by ongoing calls for new strategies to counter evolving threats. The importance of red teaming assessment has not changed in this environment.
A Red Team Assessment is a cybersecurity testing technique that finds weaknesses in an organization’s security defenses by simulating real-world cyberattacks using a team posing as attackers. Enhancing an organization’s overall security posture and evaluating the efficacy of security procedures are the objectives.
In today’s blog post, we will take a closer look at what a Red Teaming Assessment really is, explore its key benefits, and discuss why your organization needs it. Get ready to buckle up and dive into this essential Red Team cybersecurity practice to strengthen your defenses!
What is Red Team Assessment?
Red team assessment is a method for thoroughly testing an organization’s security policies, strategies, systems, readiness, and incident response capabilities, as the name suggests. To put it simply, ethical hackers who act and think like enemies make up a red team.
Red team assessments are used to demonstrate how real-world attackers can combine seemingly unrelated vulnerabilities to achieve their objectives. If an attacker can leave the data center with an unencrypted hard disk, it shows a powerful technique that even the most advanced firewall in the world is not particularly effective against. It is preferable to adopt a defense-in-depth strategy and consistently enhance your people, processes, and technology rather than relying on a single network appliance to protect critical data.
For instance, red team cyber security exercises have long employed methods such as social engineering and privilege escalation, dating back to the early 2000s. However, modern red teaming now leverages advanced frameworks, such as MITRE ATT&CK, significantly enhancing its effectiveness.
The Importance of Red Team Assessments
Businesses must understand how effective their security solutions are against complex threats. Red team evaluations create a safe space to test response procedures. They help find security weaknesses and improve incident response times. These exercises are key to keeping security strong. They also help meet industry standards and rules that focus more on preventive security measures. In the current digital business age, red teaming is important for the following reasons:
- Cyberattacks have increased by 31% annually, raising overall business vulnerability.
- 70% of SMBs lack strong security protocols to combat a cyberattack.
- 72% of ransomware attacks on governments resulted in data encryption.
- 40% of CEOs find implementing hybrid IT infrastructures the most difficult cybersecurity challenge.
- Nearly half (47%) of healthcare breaches are due to third-party insiders, with insider threats causing 43% of security breaches.
Red teams verify the efficacy of existing security measures to determine whether security procedures are sound and consistently followed by staff members. These evaluations help companies keep ahead of the curve by determining the effects of new cyber threats and evaluating how well their security procedures hold up against them.
How Red Team Assessment Works?
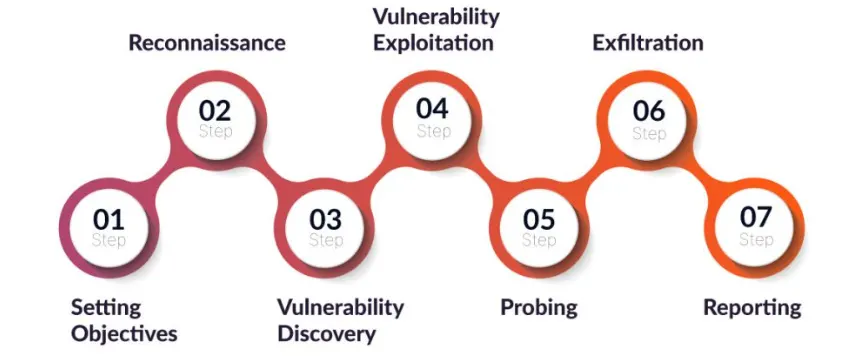
A red team assessment mimics a real-world cyber threat situation by following a methodical, planned process that is divided into several phases. The following are the usual phases of a red team assessment:
Step 1. Setting Objectives:
Planning and goal mapping are included in the first stage. The rules and objectives of the process are guaranteed to be understood by all parties involved.
Step 2. Reconnaissance:
Information regarding the company’s IT network, technology, infrastructure, and personnel is gathered during this phase by the Red Team cybersecurity.
Step 3. Vulnerability Discovery:
Red teamers conduct active testing to identify vulnerabilities and potential attack routes based on the reconnaissance step’s findings.
Step 4. Vulnerability Exploitation:
Once vulnerabilities have been identified, the red team attempts to employ safe exploitation techniques to bypass security measures and gain access to the target’s systems.
Step 5. Probing:
The red team now assesses their range of lateral movement within the network. The objective is to understand the depth of the network and identify additional opportunities to achieve their goals.
Step 6. Exfiltration:
The red team’s goal during this phase is to steal confidential data from the target environment without being discovered.
Step 7. Reporting:
In this final phase, the red team provides a comprehensive report that details the vulnerabilities identified, how they were exploited and offers practical suggestions to enhance incident response capabilities.
Key Benefits of Red Team Assessment
1. Detailed Analysis of security Posture:
Red team assessments help businesses uncover hidden flaws in their people, technology, and processes. The assessment helps CISOs review the internal security and find effective solutions.
2. Improved Security:
Red teams are groups of cybersecurity professionals. They know how to handle the latest threats. By doing this, you may increase security readiness and reduce the possibility of expensive breaches.
3. Raised ROI:
Assessing the security system’s effectiveness helps avoid millions in losses after a breach. It also boosts the return on investment for securing an organization.
4. Effective Prioritization:
Red team tactics help prioritize fixing vulnerabilities, improve cybersecurity measures, and manage security costs. This approach boosts overall security by focusing on targeted testing and smart planning.
5. Improved Compliance:
Red team analysis helps companies spot key weaknesses in regulatory compliance. This allows them to fix these issues quickly, ensuring they meet regulations and boost overall security.
Why Does Your Organization Need Red Team Assessment?
At LMNTRIX, we specialize in offering Red Team Assessments that replicate the tactics, methods, and procedures (TTPs) of actual adversaries in order to assist companies in strengthening their cybersecurity defenses. Here’s how we guarantee optimal coverage and outcomes.
Customized Attack Simulations
We create custom Red Team tactics that focus on the most important and pertinent aspects of the client’s organization, taking into account its size, industry, and unique security concerns.
Expert Team
Our red team is made up of cybersecurity industry professionals with a wealth of experience, including cybersecurity specialists from the business sector and former military cyber warfare experts. This breadth of expertise guarantees that our evaluations offer realistic attack simulations.
Integrated Technologies
We use cutting-edge technology and intelligence collection to mimic the most sophisticated enemies. Our strategy is informed by the most recent Red Team cybersecurity research and up-to-date global cyber threat intelligence.
Actionable Insights
After the assessment, we provide comprehensive reports and debriefings that highlight vulnerabilities and offer focused, doable recommendations for strengthening systems and training personnel.
Continuous Improvement
Security is an ongoing activity rather than a one-time occurrence. Through regular evaluations and security strategy updates based on emerging threats, we help our clients enhance their security posture.
Final Words
Red Team Assessment services assist you in recognizing and responding to attacks before they cause real damage. By simulating the strategies of real-world threat players, these assessments reveal blind spots in your people, processes, and technologies. This proactive approach helps organizations boost their defenses, enhance incident response, and make smart choices about security investments. As cyber threats become more advanced, testing your systems in real-world conditions is key to staying strong.
At LMNTRIX, our expert-led Red Team Assessments are tailored to your specific risk profile, industry, and threat landscape. We offer detailed analysis, practical recommendations, and ongoing support. This helps you create strong cyber resilience. Partner with LMNTRIX today to gain a clearer view of your security posture and stay ahead of emerging threats.


