
A new strain of Chinese malware, dubbed Fireball by researchers, has recently been discovered on more than 250 million computers around the globe. Indian machines are the most heavily infected (10 per cent), followed by Brazil, Mexico and Indonesia (Nine, six and five per cent respectively).
Once installed, Fireball hijacks internet browsers, effectively turning them into zombies. Currently, the malware’s aim is to install plugins and other configurations to enhance ad performance and manipulating traffic in order to increase advertising revenue.
While in its current form Fireball seems relatively benign, it has the security community worried as it has the capability to serve any other PUA (potentially unwanted application).
Researchers have linked the malware to a Chinese advertising agency named Rafotech.
Below is a technical analysis we’ve conducted on Fireball’s code – the sample hashes are below:
FAB40A7BDE5250A6BC8644F4D6B9C28F
69FFDF99149D19BE7DC1C52F33AAA651
B56D1D35D46630335E03AF9ADD84B488
8C61A6937963507DC87D8BF00385C0BC
7ADB7F56E81456F3B421C01AB19B1900
This set contains three dll files and two exe files. We started our analysis with exe files.
MD5: 69FFDF99149D19BE7DC1C52F33AAA651
After digging into static analysis of the sample, one of the first things we saw was a suspicious URL inside the strings.
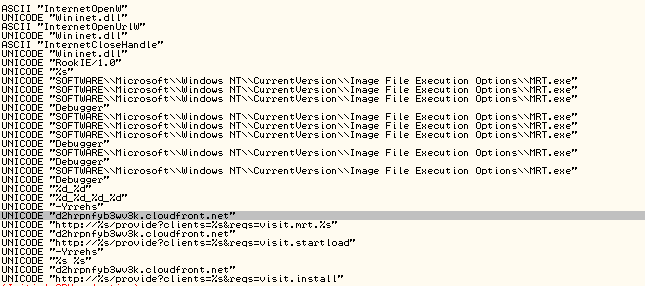
We then ran the suspicious URL in Virus Total, here are the results:
https://virustotal.com/en/url/28e8eec84c1342d64f8b20b2624e095f5fdddd7329b90b53dcf5adeba7cc2af4/analysis/1496656286/
URL Scanner Result
Dr.Web Malicious site
Avira (no cloud) Malware site
Fortinet Malware site
Kaspersky Malware site
Sangfor Malware site
The above five vendors were the only ones out of 65 who flagged this site as a malware site.
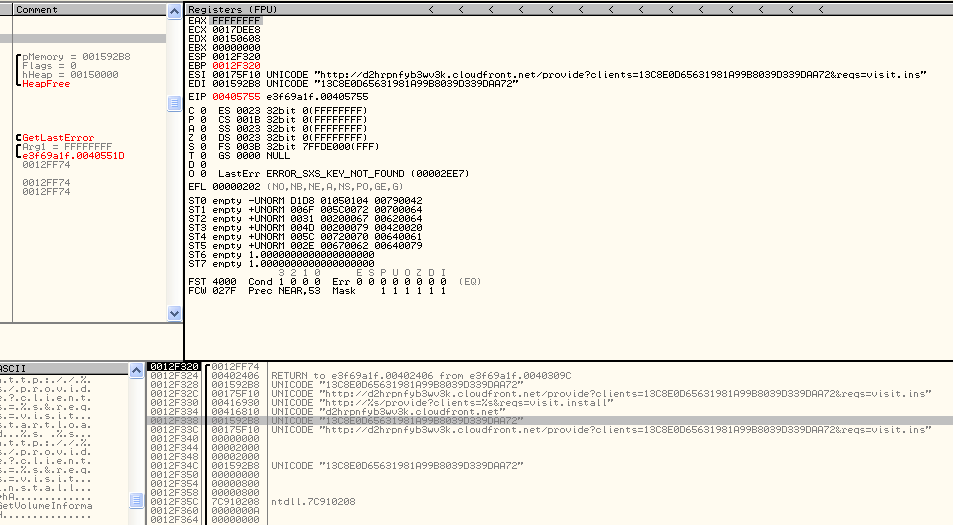
Additionally, we encountered registry traces in the code which led to an image file execution entry.
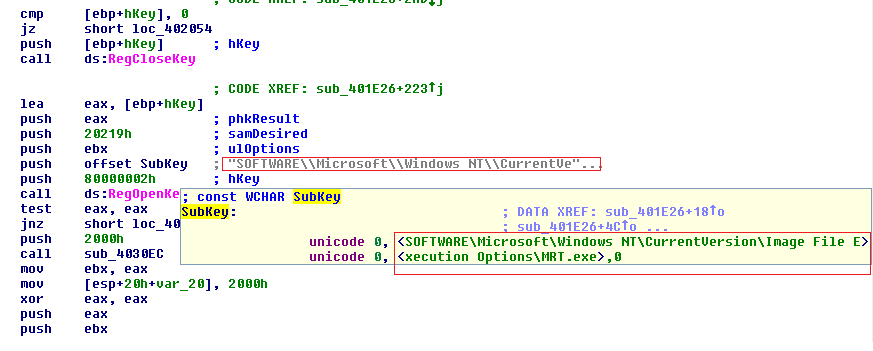
We executed these instruction sets and watched for any changes in the system registry traces.
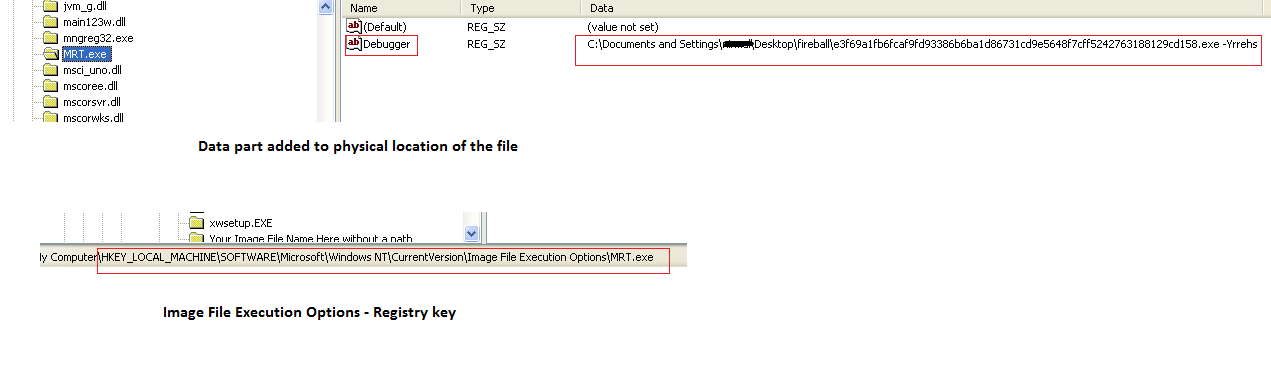
What we’re seeing here is that the image file execution option entry can be used to replace a file with another process using the ‘debugger’ value. To see how this works, let’s take a process explorer, a similar tool to Windows Task Manager, and view the running processes:
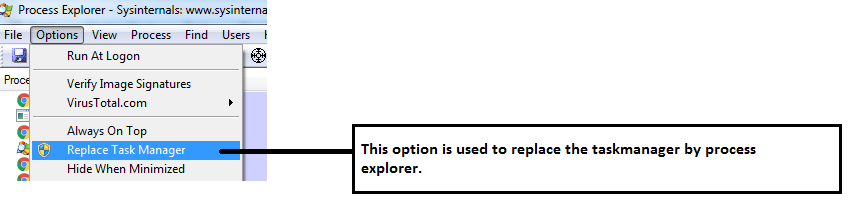
After doing this, we can see the registry trace changes in the Image file execution option.
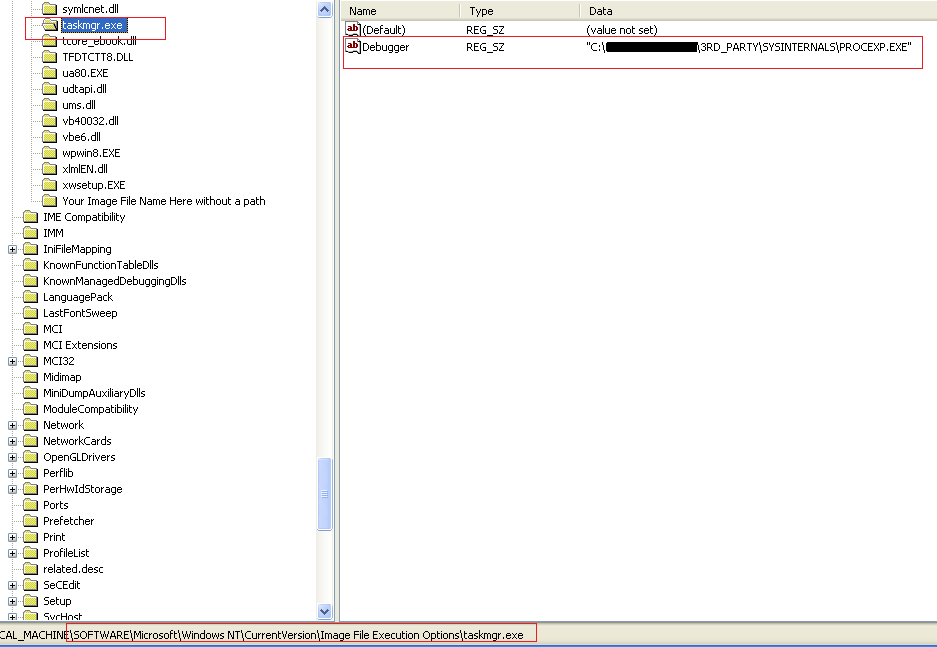
This is the process we would undertake to replace task manager manually, and the malware author uses this same technique to replace important files with the ‘debugger’ value.
If we now refer back to Figure 4, we can see that MRT.exe is replaced by the Fireball malware – MRT.exe is Microsoft’s malicious software removal tool.
Now we’ll move on to our next executable file.
MD5: 7ADB7F56E81456F3B421C01AB19B1900
This file doesn’t have any embedded url, but we do see the peculiar registry entry “HKEY_LOCAL_MACHINE\SOFTWARE\ScreenShot”.
It is supposed to be a screenshot application but didn’t show any behaviour in our virtual machine, so we proceeded with the other dll files.
DLL file analysis:
We started our analysis on the dll (MD5: FAB40A7BDE5250A6BC8644F4D6B9C28F).
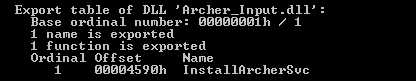
Interesting strings:
- 00000001B36F 00001001C56F 0 d\\.\PhysicalDrive%d
- 00000001B3F0 00001001C5F0 0 %u_%u
- 00000001B404 00001001C604 0 %s_%s
- 00000001B410 00001001C610 0 %s_%08X
- 00000001B450 00001001C650 0 cloud
- 00000001B45C 00001001C65C 0 front
- 00000001B468 00001001C668 0 .net//v
- 00000001B480 00001001C680 0 ?action=
- 00000001B49C 00001001C69C 0 http://
- 00000001B4E0 00001001C6E0 0 HTTP/1.0
- 00000001B54C 00001001C74C 0 rundll32.exe “
- 00000001B368 00001001C568 0 unnamed
- 00000001B4AC 00001001C6AC 0 Internet Open Failed!
- 00000001B4C4 00001001C6C4 0 Internet Connect Failed!
- 00000001B4FC 00001001C6FC 0 Http Open Failed!
- 00000001B510 00001001C710 0 Http Send Request Failed!
- 00000001B5D8 00001001C7D8 0 C:\Users\Administrator\Desktop\archer_lyl\Release\ Archer_Input.pdb
- 00000001CAC8 00001001DCC8 0 InternetOpenW
- 00000001CAD8 00001001DCD8 0 InternetCrackUrlW
- 00000001CAEC 00001001DCEC 0 InternetReadFile
- 00000001CB00 00001001DD00 0 InternetConnectW
- 00000001CB14 00001001DD14 0 HttpSendRequestW
- 00000001CB28 00001001DD28 0 HttpQueryInfoW
- 00000001CB3A 00001001DD3A 0 HttpOpenRequestW
- 00000001CB4E 00001001DD4E 0 InternetCloseHandle
We registered the DLL to find any behaviour changes in the system. It creates a new registry entry in the StartMenu2 program.
We checked the next DLL file (MD5: 8C61A6937963507DC87D8BF00385C0BC) to find whether this file also had any similar behaviour.
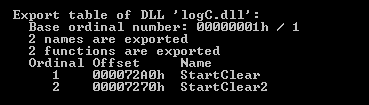
Interesting strings inside this file:
- strings [C:\ProgramData]
- strings [msmpeng]
- strings [C:\Windows\System32\cmd.exe /c “”]
- strings [C:\Windows\System32\cmd.exe /c “]
- strings [ -l >> ]
- strings [ttttt.exe]
- strings [Microsoft\Windows Defender\Support]
- strings [hhhhh.exe]
- strings [kernel32]
- strings [Microsoft\Microsoft Antimalware\Support]
- strings [d\\.\PhysicalDrive%d]
- strings [\\.\Scsi%d:]
- strings [MachineGuid]
- strings [SOFTWARE\Microsoft\Cryptography]
- strings [%s_%08X]
- strings [inqmqq]
- strings [.cloud]
- strings [front.net]
- strings [?action=]
- strings [clean/]
- strings [http://]
- strings [HTTP/1.0]
- strings [list.dat]
- strings [ -stop “]
- strings [msmpeng]
- strings [“,StartClear2]
- strings [C:\Windows\System32\Rundll32.exe “]
- strings [cle.log.4]
- strings [cle.log.3]
- strings [cle.log.2]
- strings [cle.log.1]
- strings [ -accepteula]
- strings [hhhhh.exe]
- strings [ttttt.exe]
We then moved to the final file (MD5: B56D1D35D46630335E03AF9ADD84B488), which contains the following export function:
Export table of DLL ‘WinSAP.dll’:
Base ordinal number: 00000001h / 1
- 2 names are exported
- 2 functions are exported
Ordinal Offset Name
- 00002F80h MAIN
- 0000B990h ServiceMain
We found the following strings in this file:
- strings [\\.\PhysicalDrive%d]
- strings [\\.\Scsi%d:]
- strings [SOFTWARE\Microsoft\Windows NT\CurrentVersion\Svchost]
- strings [NOT UPDATE]
- strings [UPDATE OVERWRITE]
- strings [SOFTWARE\Microsoft\Windows NT\CurrentVersion\Svchost]
- strings [%s\svchost.exe -k %s]
- strings [%s\svchost.exe -k %s]
- strings [Advapi32]
- strings [SYSTEM\CurrentControlSet\Services\%s]
- strings [Parameters]
- strings [ServiceDll]
- strings [explorer.exe]
- strings [SeDebugPrivilege]
- strings [ADFWAGAADF_Example/1.0]
- strings [2.7.38]
- strings [2.7.38]
- strings [explorer.exe]
- strings [winsap]
- strings [\SETUP.dll]
- strings [winsap]
- Strings [Copyright (c) 1992-2004 by P.J. Plauger, licensed by Dinkumware, Ltd. ALL RIGHTS RESERVED.]
- strings [SCSIDISK]
- strings [CreateServiceW]
- strings [StartServiceW]
- strings [-install]
- strings [-update]
- strings [-install]
- strings [-uninstall]
- strings [-update]
- strings [aHR0cDovL2QzaTFhc29zd3VmcDVrLmNsb3VkZnJvbnQubmV0L3Y0L2d0Zy8lcz9hY3Rpb249dmlzaXQud2luc2FwLndvcmsmdXBkYXRlMz12ZXJzaW9uLCVz]
- strings [aHR0cDovL2QzaTFhc29zd3VmcDVrLmNsb3VkZnJvbnQubmV0L3Y0L2d0Zy8lcz9hY3Rpb249dmlzaXQud2luc2FwLmluc3RhbGw=]
- strings [aHR0cDovL2QzaTFhc29zd3VmcDVrLmNsb3VkZnJvbnQubmV0L3Y0L2d0Zy8lcz9hY3Rpb249dmlzaXQud2luc2FwLnVwZGF0ZW9r]
- strings [aHR0cDovL2QzaTFhc29zd3VmcDVrLmNsb3VkZnJvbnQubmV0L3Y0L2d0Zy8lcz9hY3Rpb249dmlzaXQud2luc2FwLnN0YXJ0aW5zdGFsbA==]
- strings [aHR0cDovL2QzaTFhc29zd3VmcDVrLmNsb3VkZnJvbnQubmV0L3Y0L2d0Zy8lcz9hY3Rpb249dmlzaXQud2luc2FwLnN0YXJ0dXBkYXRl]
- strings [aHR0cDovL2QzaTFhc29zd3VmcDVrLmNsb3VkZnJvbnQubmV0L3Y0L2d0Zy8lcz9hY3Rpb249dmlzaXQud2luc2FwLmlzZXhpc3RlZA==]
- strings [aHR0cDovL2RjNDRxandhbDNwMDcuY2xvdWRmcm9udC5uZXQvd2luc2FwL3VwP3B0aWQ9JXMmc2lkPSVzJmxuPSVzXyVzJnZlcj0lcyZ1aWQ9JXMmZHA9MA==]
This is the interesting part in this file, some strings appeared to be encoded:
- aHR0cDovL2QzaTFhc29zd3VmcDVrLmNsb3VkZnJvbnQubmV0L3Y0L2d0Zy8lcz9hY3Rpb249dmlzaXQud2luc2FwLndvcmsmdXBkYXRlMz12ZXJzaW9uLCVz
- aHR0cDovL2QzaTFhc29zd3VmcDVrLmNsb3VkZnJvbnQubmV0L3Y0L2d0Zy8lcz9hY3Rpb249dmlzaXQud2luc2FwLmluc3RhbGw=
- aHR0cDovL2QzaTFhc29zd3VmcDVrLmNsb3VkZnJvbnQubmV0L3Y0L2d0Zy8lcz9hY3Rpb249dmlzaXQud2luc2FwLnVwZGF0ZW9r
- aHR0cDovL2QzaTFhc29zd3VmcDVrLmNsb3VkZnJvbnQubmV0L3Y0L2d0Zy8lcz9hY3Rpb249dmlzaXQud2luc2FwLnN0YXJ0aW5zdGFsbA==
- aHR0cDovL2QzaTFhc29zd3VmcDVrLmNsb3VkZnJvbnQubmV0L3Y0L2d0Zy8lcz9hY3Rpb249dmlzaXQud2luc2FwLnN0YXJ0dXBkYXRl
- aHR0cDovL2QzaTFhc29zd3VmcDVrLmNsb3VkZnJvbnQubmV0L3Y0L2d0Zy8lcz9hY3Rpb249dmlzaXQud2luc2FwLmlzZXhpc3RlZA==
- aHR0cDovL2RjNDRxandhbDNwMDcuY2xvdWRmcm9udC5uZXQvd2luc2FwL3VwP3B0aWQ9JXMmc2lkPSVzJmxuPSVzXyVzJnZlcj0lcyZ1aWQ9JXMmZHA9MA==
Here are the same values decoded:
- hxxp://d3i1asoswufp5k(.)cloudfront(.)net/v4/gtg/%s?action=visit.winsap.work&update3=version,%s
- hxxp://d3i1asoswufp5k (.)cloudfront (.)net/v4/gtg/%s?action=visit.winsap.install
- hxxp://d3i1asoswufp5k (.)cloudfront (.)net/v4/gtg/%s?action=visit.winsap.updateok
- hxxp://d3i1asoswufp5k (.)cloudfront (.)net/v4/gtg/%s?action=visit.winsap.startupdate
- hxxp://d3i1asoswufp5k (.)cloudfront (.)net/v4/gtg/%s?action=visit.winsap.isexisted
- hxxp://dc44qjwal3p07 (.)cloudfront (.)net/winsap/up?ptid=%s&sid=%s&ln=%s_%s&ver=%s&uid=%s&dp=0
All these are malicious URLs present in the file. We advise readers to block these urls in their firewall and if you notice any strange behaviour from your web browser, please revert the web browser settings back to default and remove any extensions you did not install.


