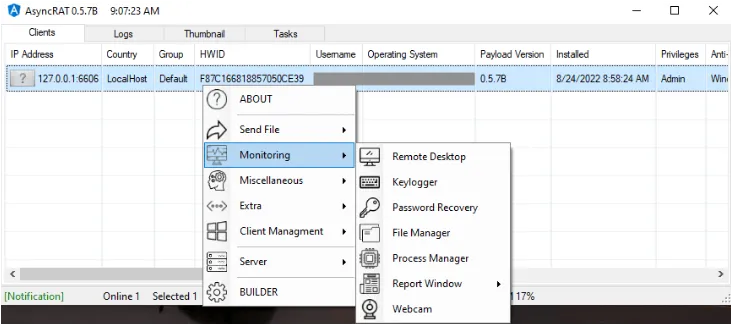
AsyncRAT (Asynchronous Remote Access Trojan) is an open source remote administration malware that enables an attacker to take control of a victim’s computer. It is a powerful tool that allows the attacker to perform various malicious activities, such as stealing sensitive data, executing arbitrary code, aside from controlling the victim’s computer. Its payload files were written in .NET and can be easily customised by the attacker to achieve their targets. The malware is usually spread through phishing emails or by exploiting vulnerabilities in software or operating systems. Also, the malware uses asynchronous communication to evade detection.
Threat actors who are able to effectively exploit the CVE-2022-30190 (MSDT Dogwalk) vulnerability can run arbitrary code and introduce new processes into the system. LMNTRIX CDC has observed, threat actors utilising this vulnerability to infect consumers and businesses in both North America and Europe with backdoors and remote access tools such as AsyncRAT, Qakbot, and other malware families.
Infection Chain

Infection Vectors
Initial Access: Malspam campaign, or phishing Emails.
Objective of Malware: Keylogging, data exfiltration, info-stealing, remote shell, remote code execution (RCE).
Targets Geography: Asia, Latin America, North America, South America, Central America.
Industry: Banking & Finance, Healthcare, Government, Education, Travel and Manufacturing industries etc.
Sample Information
Threat Name: AsyncRAT | Category: Backdoor
Anti-debugging and the evasive nature of Async RAT
One of the key features of Async RAT is its ability to evade detection and analysis through anti-debugging techniques. Anti-debugging refers to a set of techniques employed by malware authors to prevent or delay the process of debugging and analyzing their malicious code. Async RAT utilizes various anti-debugging mechanisms to make it challenging for security researchers and analysts to understand its inner workings and develop countermeasures.
One common anti-debugging technique employed by Async RAT is the detection of debugging tools and virtual machines. It checks for the presence of debuggers and virtual environments that could be used to analyze its behavior. If such tools are detected, Async RAT may terminate or modify its behavior, making it difficult for analysts to gain insight into its malicious activities. Async RAT often employs code obfuscation and encryption techniques to obfuscate its payload and make it harder to reverse engineer. By encrypting critical parts of its code or using packing techniques, Async RAT can ensure that its functionality remains hidden from static analysis techniques.
Another evasive characteristic of Async RAT is its ability to communicate covertly with its command-and-control (C&C) servers. It may use various communication protocols, such as HTTP or DNS, to disguise its network traffic as legitimate traffic. Additionally, Async RAT may employ encryption and other obfuscation techniques to hide the content of its communications, making it difficult for network defenders to detect and block its activities.
Furthermore, Async RAT can dynamically change its behavior to avoid detection. It may have the ability to mutate or update itself, altering its code signature and evading traditional signature-based detection methods. This makes it challenging for antivirus and security software to keep up with the rapidly evolving threat landscape.
Technical Analysis of AsyncRAT Campaign
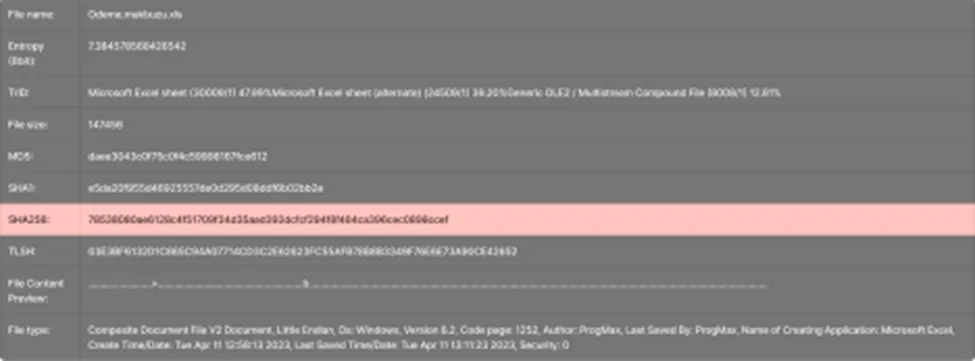
The new AsyncRAT malware infects its victim by the initial vector of phishing email, where it contains an attachment file of MS excel spreadsheet. Once the victim opens the .xls the execution parent file drops another .xls file to trigger the VBA macros and to communicate with their malicious C2C servers to download the payload file (.net framework) and starts its infection. Let’s begin with the sample analysis.
AsyncRAT Spreadsheet Template
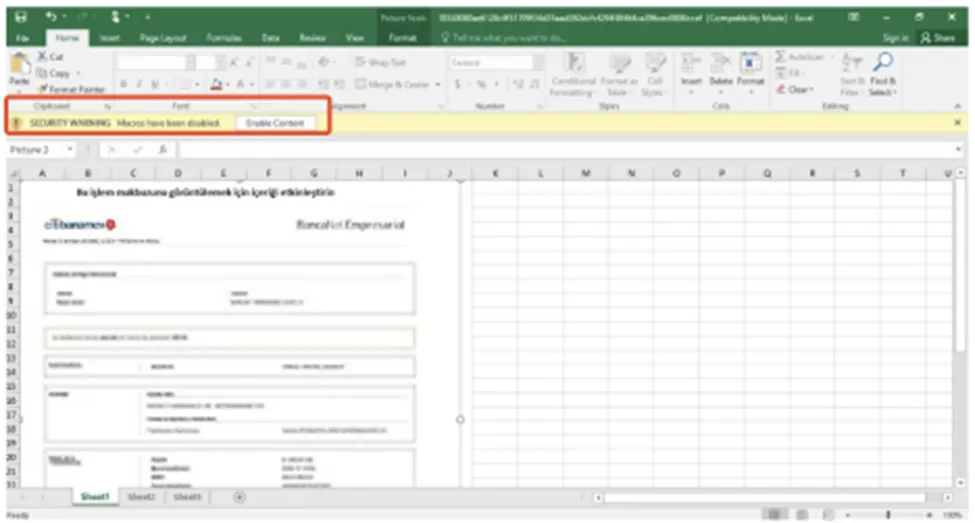
Here, the template is blurred and in-order to view the image, the user should enable the macros. It’s a known trick used by the malware author.
Why VBA Macros?
In general, VBA macros can perform a variety of tasks, such as formatting data, creating charts, generating reports, and performing calculations. They can also interact with other applications, automate web interactions, and perform other more advanced functions.
Also we can save significant amounts of time and improve productivity by automating repetitive tasks, reducing errors, and allowing users to focus on more important tasks. This facilitates malware authors to embed the malicious code inside the macros.
OLE Embedded keywords
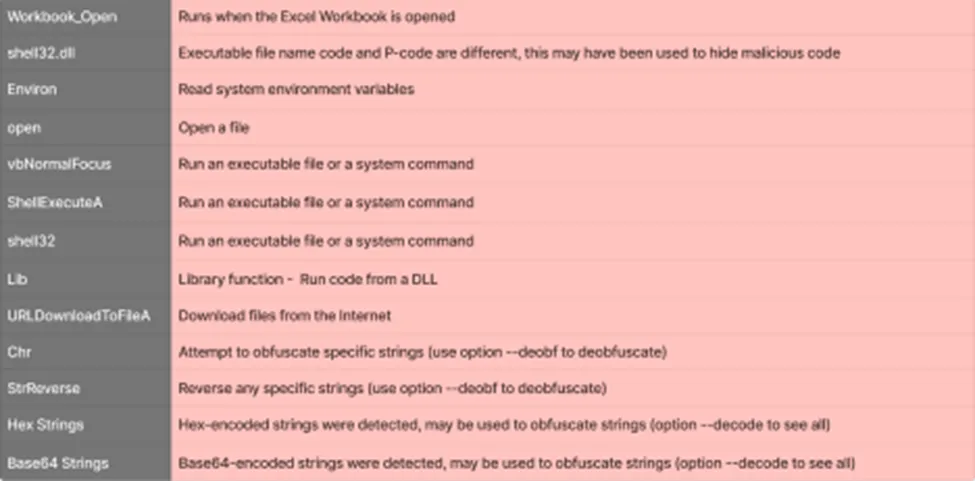
Using these API calls, the macros will execute, especially URLDownloadToFileA – Once the user opens the Excel spreadsheet, this windows API function which downloads a file from the Internet to a local file quickly and easily. Luckily, we can capture that file, using a network capturing tool.
Dropped Payload File
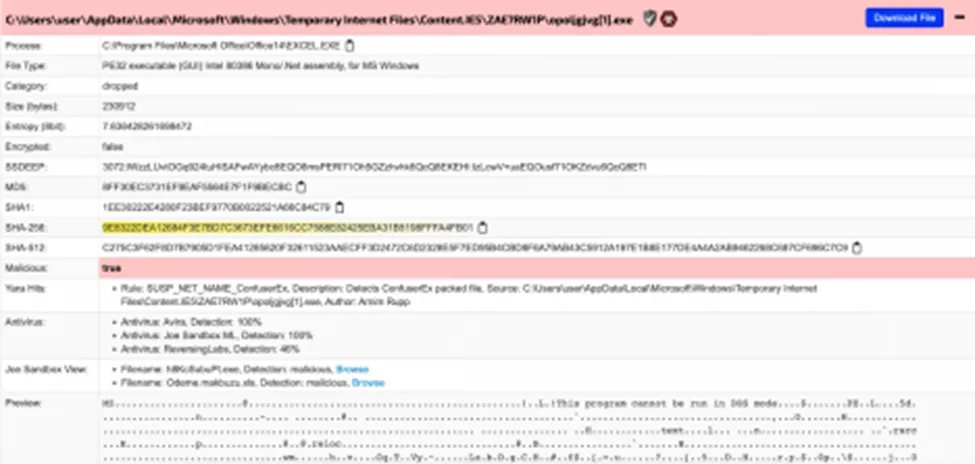
Payload – Filenames
{{
server1][.][exe
1ee30222e4280f23bef9770b0022521a66c84c79][.][bin
iitt][.][exe
opoljgjvg[1]][.][exe
asri][.][exe
opoljgjvg[][.][exe
jjii][.][]exe
}}
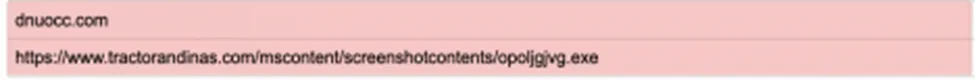
Indicator of Compromise
AV Detection Results
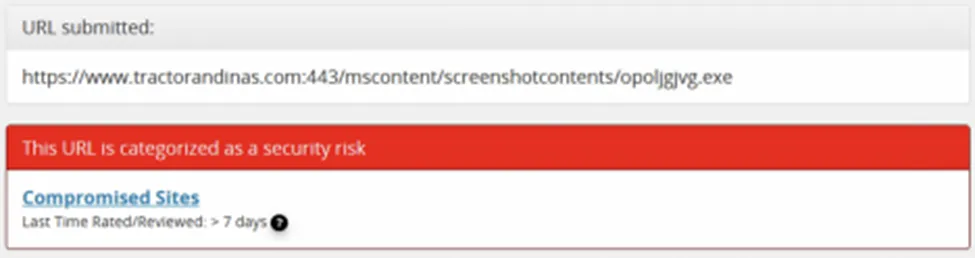
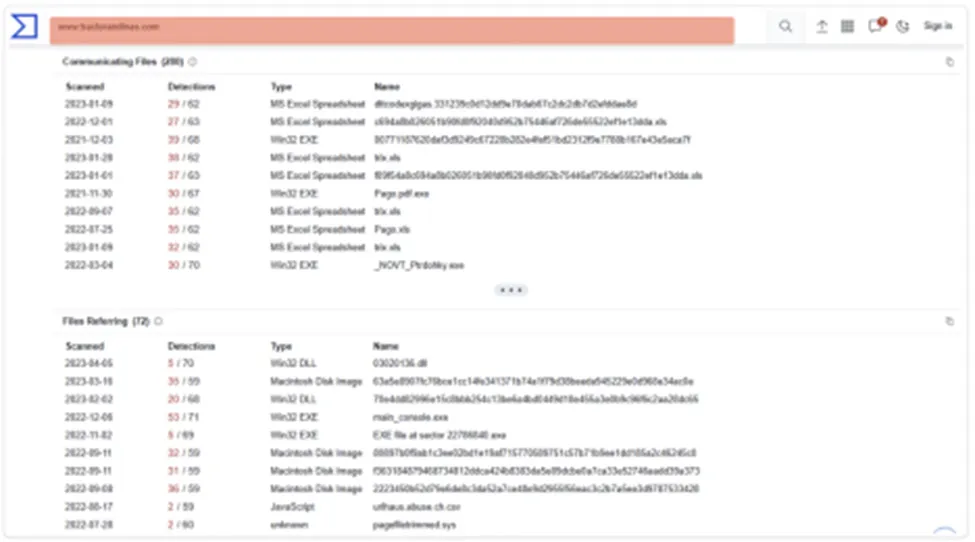
Communicating files & relevant C2 references
Functionality of Async RAT
Once the AsyncRAT malware infects a victim’s computer, it establishes a backdoor, allowing the attacker to remotely access and control the computer. The attacker can then execute commands on the victim’s computer, capture keystrokes, and steal sensitive information such as passwords, credit card details, and other personal information.
Attack Vectors used by Async RAT;
- Phishing emails: Attackers often use phishing emails to trick users into downloading and running malware on their systems. These emails may contain malicious links or attachments that download the AsyncRAT malware onto the victim’s computer.
- Malicious downloads: AsyncRAT malware may be bundled with other software downloads, such as free games or utility programs. Users who download and install these programs unknowingly also install the malware.
- Exploiting vulnerabilities: The malware can exploit vulnerabilities in software or operating systems to gain access to a victim’s computer. Attackers may use tools such as exploit kits to automate the process of identifying and exploiting vulnerabilities.
- Social engineering: Attackers may use social engineering techniques to trick users into downloading and installing the malware. For example, an attacker may pose as a legitimate software vendor or service provider and send a message asking the user to download an update or patch for their software.
- Drive-by downloads: Here, the malware is downloaded onto the victim’s computer when they visit a compromised website.
Threat Actors using the Async RAT, for the last 3 years,
In 2020 and 2021, LMNTRIX CDC observed several threat actors utilized Async RAT in their malicious campaigns. While it is difficult to attribute specific attacks to individual actors with absolute certainty, the following are some notable instances where Async RAT was observed:
- Lazarus Group: Lazarus Group, a North Korean state-sponsored threat actor, has been known to employ Async RAT in their operations. They have targeted various industries, including financial institutions, government organizations, and cryptocurrency exchanges. The impact of their attacks has been significant, resulting in data breaches, theft of funds, and disruption of critical systems.
- TA505: TA505, a financially motivated cybercriminal group, has utilized Async RAT in its campaigns. They primarily focus on distributing banking trojans and ransomware. The impact of their attacks has been widespread, with numerous organizations falling victim to their malware. This has resulted in financial losses, data breaches, and operational disruptions.
- APT32: APT32, also known as OceanLotus Group, is a threat actor associated with Vietnamese state interests. They have employed Async RAT as part of their espionage campaigns targeting Southeast Asian countries, particularly those with political and economic significance. The impact of their attacks includes theft of sensitive information, monitoring of victims’ activities, and potential geopolitical implications.
- Various cybercriminal groups: Async RAT has also been leveraged by multiple cybercriminal groups with varying motivations. These groups often distribute the malware through phishing emails, exploit kits, or social engineering techniques. The impact of their attacks can range from unauthorized access to systems, data theft, installation of additional malware, and even the establishment of botnets for future malicious activities.
The impact of attacks involving Async RAT can be severe. It can lead to the compromise of sensitive information, financial losses, operational disruptions, reputational damage, and even potential harm to individuals or national security. The primary objective of these attacks is often financial gain, espionage, or furthering geopolitical interests.
MITRE ATT&CK Tactics & Techniques for Async RAT
| ID | Tactic | Technique |
| TA0001 | Initial Access | Spearphishing Attachment |
| TA0002 | Execution | VBA Scripting Windows management Execution |
| TA0003 | Persistence | Registry Run Keys / Startup Folder |
| TA0004 | Privilege Escalation | Scheduled Task |
| TA0005 | Defense Evasion | Modify Registry Virtualization Evasion Technique |
| TA0006 | Credential Access | OS Credential Dumping Password Guessing Steal Credentials from Web Browsers |
| TA0007 | Discovery | System Network Configuration Discovery Process Discovery File and Directory Discovery |
| TA0008 | Lateral Movement | Remote file copy |
| TA0011 | C&C Server | Web Protocols Standard application layer protocol Standard Cryptographic protocol etc., |


