Cobalt Strike is a popular penetration testing tool that allows users to emulate advanced threats, perform reconnaissance, hide communications, escalate privileges, move laterally across the network, and deploy additional payloads. The main payload of Cobalt Strike is called “Beacon.”
Functionality of the Beacon Payload:
● Modify and query the Windows registry.
● Inject malicious code into legitimate processes (Process Injection).
● Receive commands and communicate over HTTP, HTTPS, and DNS.
● Capture keystrokes and Take screenshots.
● Set up proxies.
● Escalate privileges and Bypass UAC.
● Dump password hashes.
● Launch obfuscated Powershell and execute binaries.
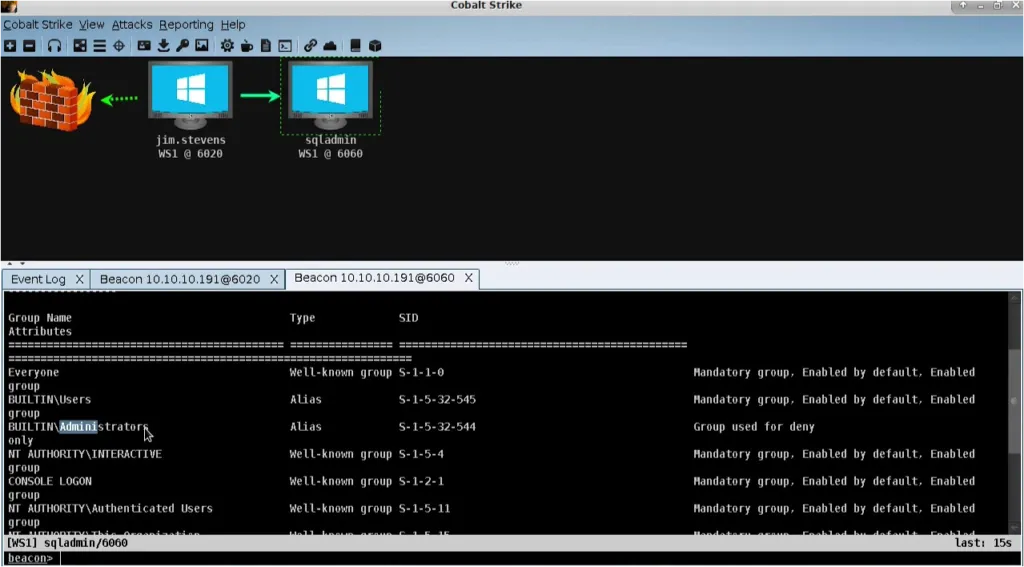
The Beacon payload is used by many advanced APT groups such as:
APT29, APT32, APT41, AQUATIC PANDA, Anunak, Cobalt, Codoso, CopyKittens, DarkHydrus, FIN6, FIN7, Leviathan, Mustang Panda, Shell Crew, Stone Panda, TianWu, UNC1878, UNC2452, Winnti Umbrella etc.
Cobalt Strike was designed to be a legitimate penetration testing tool widely used by cybersecurity professionals. However, threat actors have recognized its capabilities and leveraged it to their advantage in the cyber threat landscape. There have been several notable malware strains in recent years, such as Iced ID, Cozy Bear, Emotet, Qbot, and Conti, which have been associated with various cyberattacks.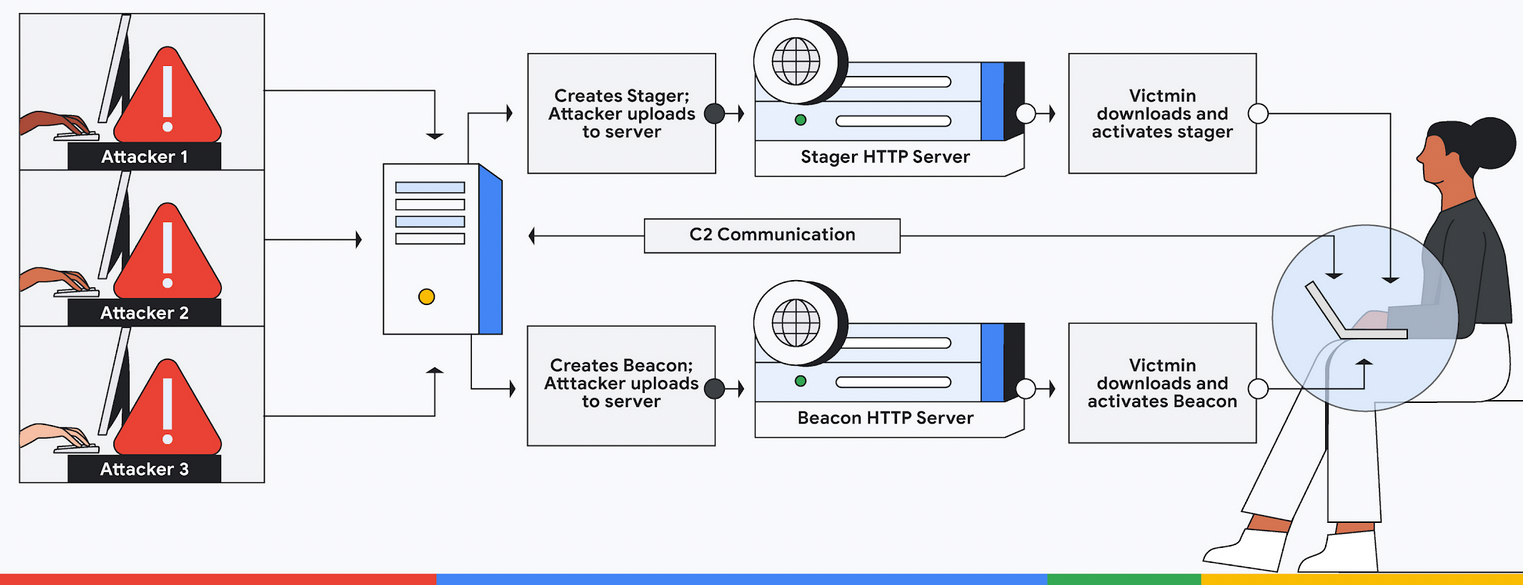
While it is not accurate to claim that “all infections lead to Cobalt Strike,” it is true that Cobalt Strike has been observed as a common payload or post-exploitation tool used by threat actors after infecting systems with these malware strains. One interesting aspect that’s less discussed is the connection between these malware families & Cobalt Strike, what could be potential the implications for your cybersecurity posture?
Iced ID is a banking trojan that primarily targets financial institutions and online banking users. It is designed to steal sensitive information, such as login credentials and financial data, from infected systems. While Iced ID itself does not directly use Cobalt Strike, it has been observed that once a system is infected with Iced ID, threat actors often use Cobalt Strike as a post-exploitation tool to gain further access, perform lateral movement, and exfiltrate data from compromised networks.
Cozy Bear, also known as APT29, is an advanced persistent threat group attributed to the Russian government. They have been involved in several high-profile espionage campaigns. While Cozy Bear does not rely on Cobalt Strike as its primary infection vector, it has been observed that once Cozy Bear gains initial access to a target network, they often deploy Cobalt Strike payloads to maintain persistence, evade detection, and conduct further reconnaissance and data exfiltration.
Emotet is a notorious banking trojan and botnet that has been active since 2014. It is primarily distributed through spam emails containing malicious attachments or links. Once Emotet infects a system, it can download additional payloads, including Cobalt Strike. In some cases, threat actors use Cobalt Strike to establish command-and-control (C2) communication, enable remote access with the target, and launch secondary attacks on compromised systems.
Qbot, also known as QakBot, is a banking trojan and information stealer. It is primarily distributed through spam emails and exploit kits. Similar to Emotet, Qbot can download and execute additional payloads, and Cobalt Strike has been observed as one of the tools deployed by threat actors after infecting systems with Qbot. Cobalt Strike enables attackers to carry out various malicious activities, including lateral movement, privilege escalation, and data exfiltration.
Conti, also known as Ryuk, is a ransomware strain that gained significant attention due to its high-profile attacks on various organizations worldwide. While Conti does not directly use Cobalt Strike as an infection vector, it has been observed that threat actors often employ Cobalt Strike in post-exploitation stages to move laterally within a compromised network, escalate privileges, and deploy ransomware payloads.
Infection Chain
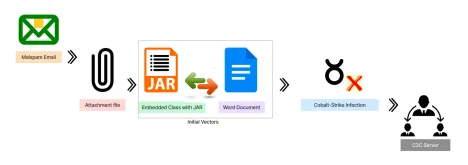
In this blog, we will analyse two different file types of Cobalt-Strike (JAR & DOC file formats).
A) Technical Analysis of JAR file
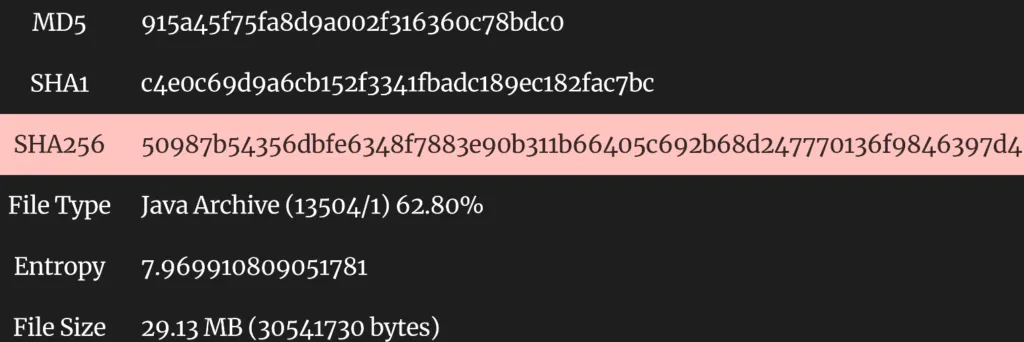
Sample Information (1)
Threat Name: Cobalt Strike | Classification: Hack Tool/Backdoor | Category: Dropper
JAR (aka Java Archive) is a file format that combines many files into one file. This Java environment differs from other programming environments in that the Java compiler does not generate machine code for a hardware-specific instruction set. Instead, the Java compiler converts Java source code into Java virtual machine instructions, which Java class files store. Basically, we can use JAR files to store class files. The class file does not target a specific hardware platform, but instead targets the Java virtual machine architecture.
Manifest – JAR File Info
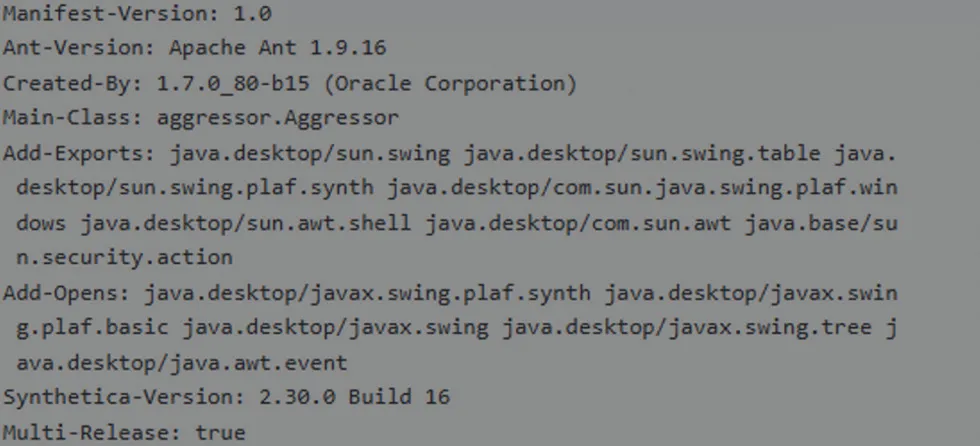
Manifest is important in Java where any executable JAR file that contains a stand-alone application, a Main-Class attribute should exist providing the name of the first piece of code for the Java Runtime Environment (JRE) to invoke when the application is executed.
Main Context of the JAR File
Suspicious Strings
Vast Structure of JAR file
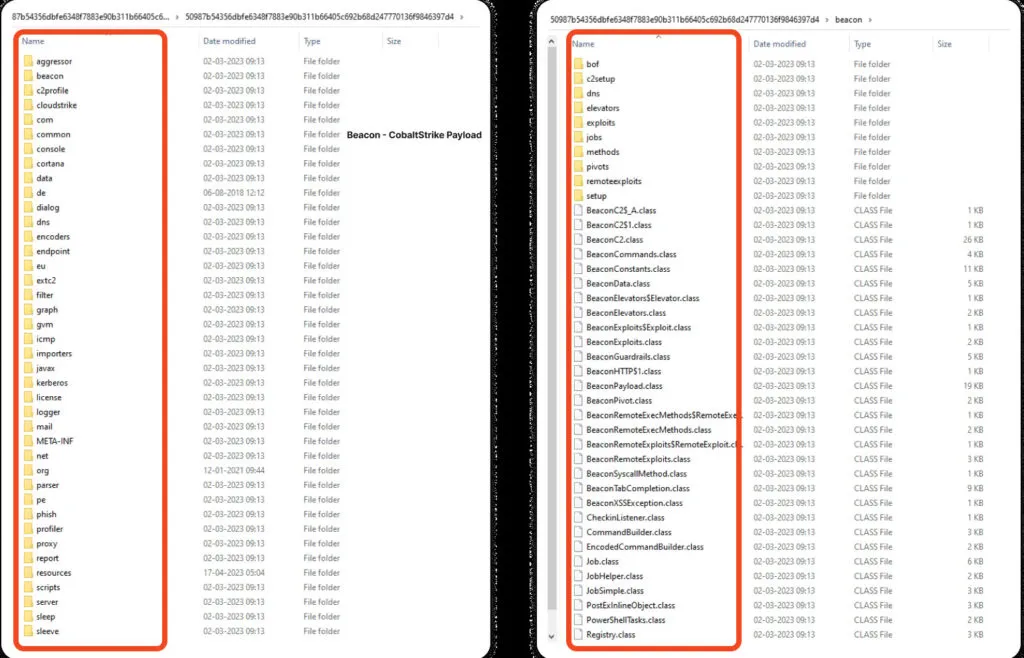
Embedded folders – Beacon Payload
Inside the .jar – we can see multiple folders and mainly the CobaltStrike malicious payload file folder also present.
These kind of files take a longer time to load. Next we will check another initial vector, that of a MS Word – Document.
B) Technical Analysis of MS Word Document
Sample Information (2)
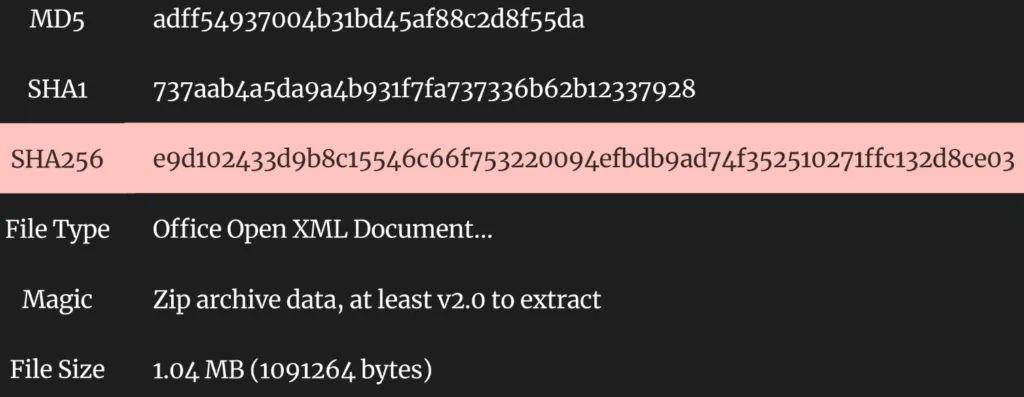
MS Word – Enable Macro Template
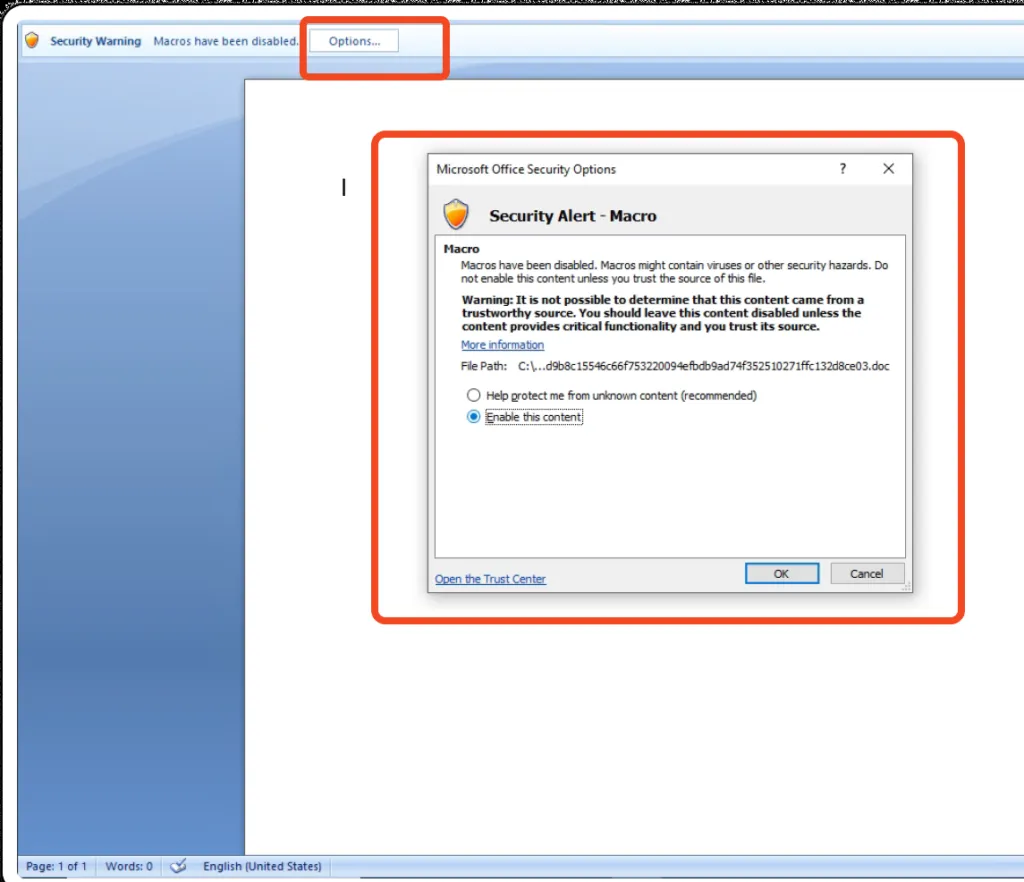
Once the user opens the attachment word document. There’s a pop-up window“ Security Warning – Macros have been disabled – Options”. Which guides us to enable the macro to do further analysis.
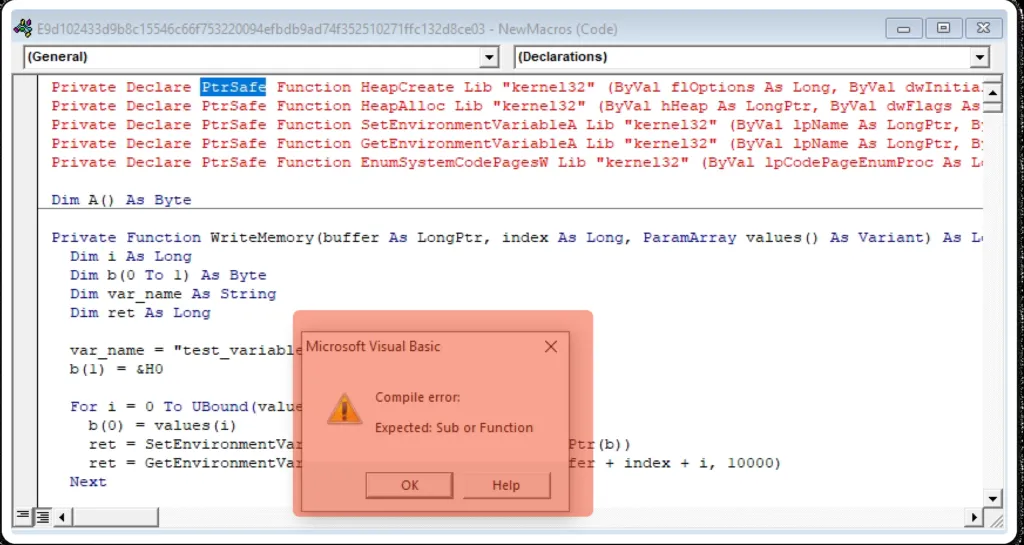
New Macro – Code
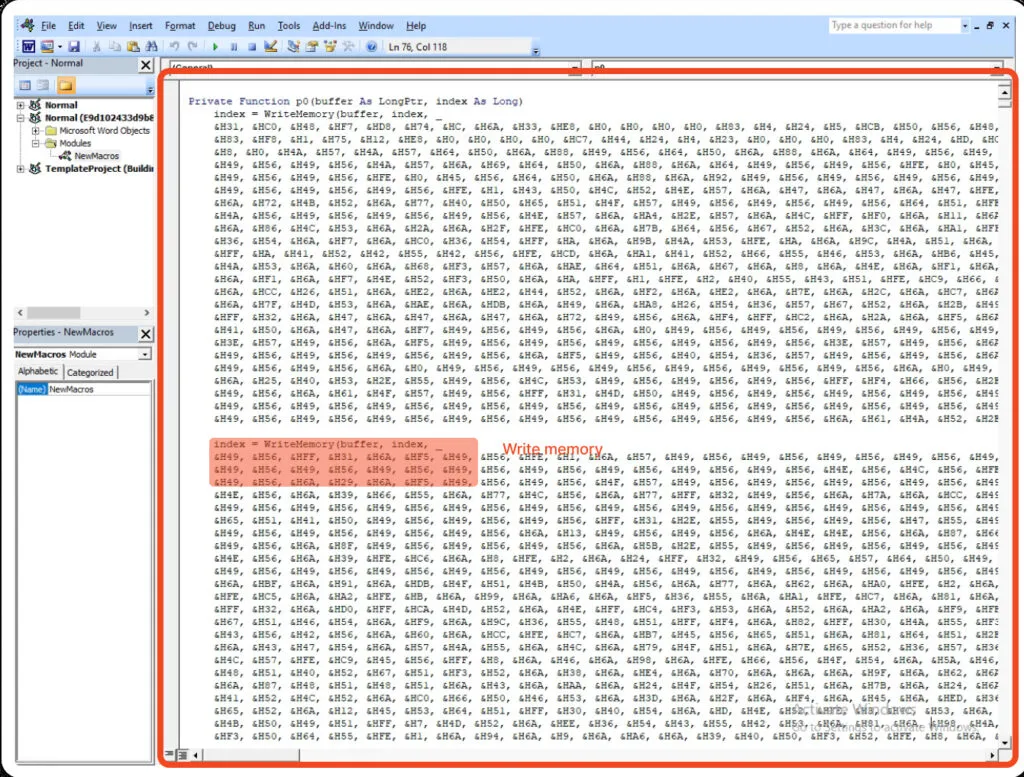
Character – Encoding Technique
The malware author uses huge character encoding technique, to make it complicated. Function = writememory (buffer, index (char…)) In each function, they have added more than 2000+ lines in each sector, hence we need to replace every char and form the code, making deobfuscating a difficult task. It’s hard to deobfuscate, therefore we dynamically analyze the sample and get the beacon payload.
Caveat: It is essential to note that the use of Cobalt Strike in conjunction with these malware families does not imply that Cobalt Strike itself is malicious. As mentioned earlier, it was originally designed to be a legitimate tool for use by penetration testers and ethical hackers.
Conclusion
To defend against advanced threats such as Emotet, Conti, Iced ID and Qbot which deploy Cobalt Strike based payloads organizations should implement a multi-layered security approach. This includes robust email filtering and user awareness training to prevent initial infections, regular patching and vulnerability management to address software vulnerabilities, and strong network segmentation to limit lateral movement. The LMNTRIX XDR Platform is able to detect and prevent IcedID, QBot, Conti/Ryuk, and Emotet using multi-layered protection that detects and stops malware at every stage with EDR, NGAV, NDR capability, contextual threat intelligence, machine learning, dark web intelligence, and forensic replay capability that’s built in for incident response and/or post-mortem analysis.
Interesting file names in the payload;
{{
CV
unknown
adff54937004b31bd45af88c2d8f55da[[.]]dotm
7EE406A8[[.]]{tmp
}}
MITRE ATT&CK Tactics & Techniques for detecting Cobalt Strike – Beacon payload,
| ID | Tactic | Technique |
| TA0001 | Initial Access | Spearphishing Attachment Valid Accounts Checking |
| TA0002 | Execution | Command and Scripting Interpreter Exploitation for Client Execution |
| TA0003 | Persistence | Services File Permissions Weakness Boot or Logon Initialization Scripts |
| TA0004 | Privilege Escalation | Scheduled Task Process Injection Logon Scripts |
| TA0005 TA0006 TA0007 TA0008 | Defense Evasion Credential Access Discovery Lateral Movement | Modify Tools Obfuscated Files or Information Registry Modification OS Credential Dumping LSASS Memory Security Account Manager NTDS System Network Configuration Discovery Process Discovery File and Directory Discovery & Query Registry Remote Desktop Protocol |
| TA0009 | Collection | Archive Collected Data Data from Local System |
| TA0011 | C&C Server | Data Obfuscation Web Protocols – Standard Application Layer Protocol. |


