Phishing attack is a kind of social engineering where it’s the practice of sending fraudulent communications that appear to come from a reputable source. It is usually done through e-mail with attachment files. The main goal is to steal sensitive data like credit card and login credentials like username & password etc.

Target – Internal Revenue Service (IRS), a social media company, or any banking sector.
Goals – Stealing personal data or financial information.
Infection Chain
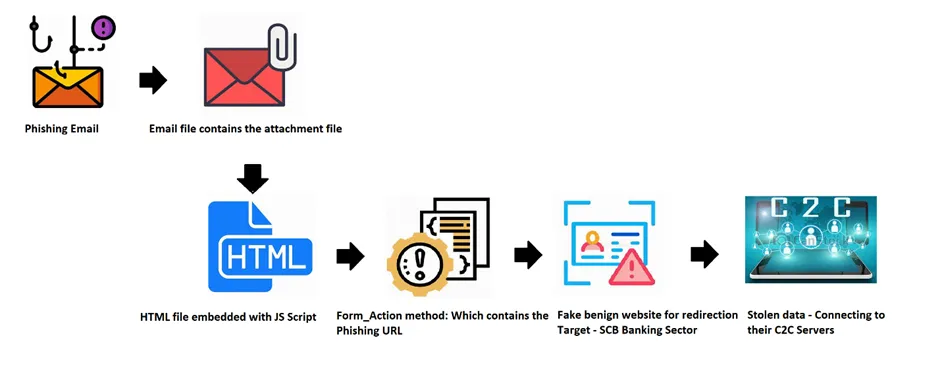
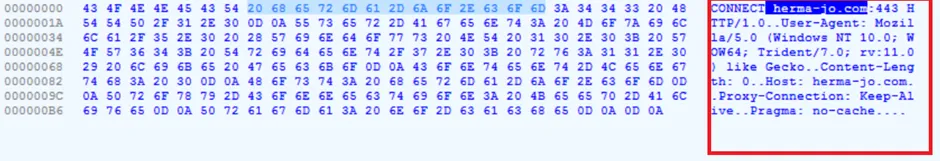
Usually, phishing campaigns infect the victims through initial infection vectors of embedded attachments, javascript shellcode, and/or malspam e-mails. This kind of e-mail file comes with attachment files of HTML/JS files. In this sample, the .html file is embedded with .JS script with malicious URL to download the payload file, likewise it uses known infection from [XXXX.com] domain in-order to download the payload files.
Psychology 101- What’s the psychology behind phishing attacks?
Let’s walk you through a few psychological concepts associated with phishing here.
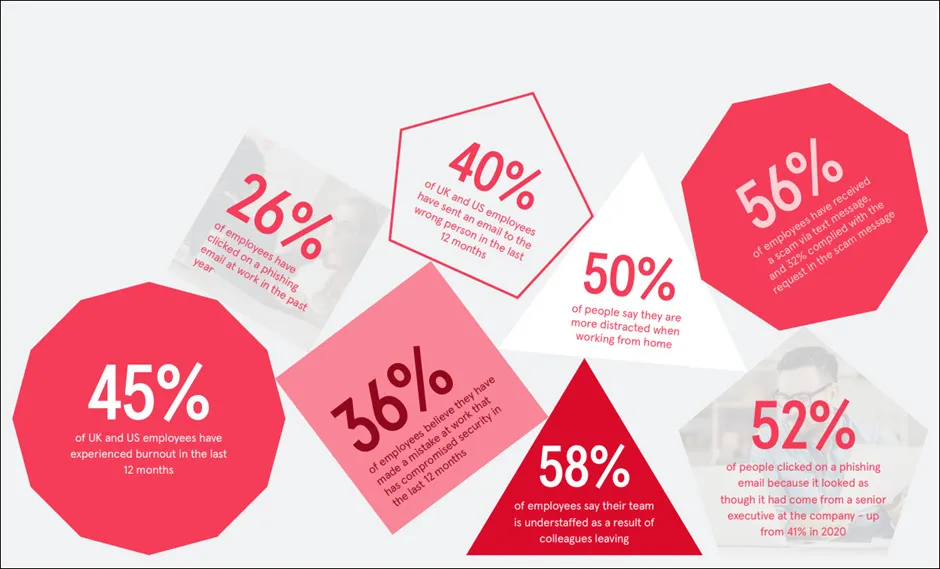
Reciprocity in social situations, helping a coworker, and consistency when paying your vendor or contractor on time, maybe considered as examples of influence over a victim clicking a phishing e-mail link. According to Tessian’s Research report Psychology of Human Error 2022, a follow-up to their 2020 report with Stanford University, 52% of people clicked on a phishing e-mail because it looked as though it had come from a senior executive at the company — up from 41% in 2020.
Also, weary workers were more likely to make mistakes, which threat actors frequently tend to prey upon. Most phishing attacks are delivered between 2 and 6 p.m., Tessian revealed in 2021, the post-lunch dip when staff members are most likely to be fatigued, distracted or preoccupied – making them more prone to click on a phishing link.
Employees may be hesitant to report the phishing incident after realising they were duped and acted out of misplaced trust. They are likely to feel bad, or feel guilty about themselves and may even face repercussions from their employer. The best-case scenario is to report the incident to IT / IT Sec team.
Employees falling prey to phishing attempts and then brushing it under the rug is how a cyber event can escalate into a large-scale cyber incident. Instead, organisations should foster an open dialogue about phishing & similar cyber threats fostering a culture in which cyber security becomes a shared responsibility.
Recent phishing campaigns that we have seen in the last 18 months through LMNTRIX CDC include;
- COVID-19 Scams: Hackers have used the pandemic to prey on people’s fears and anxieties. They may e-mail or, contact you about COVID-19 vaccine discounts or freebies, but they’re trying to steal your personal information.
- Fake bank alerts: Fake bank alerts are another prevalent occurrence used by phishing groups. The bank’s notice may indicate your account has suspicious behavior, request you to change a password, and/or ask you to click a link (with a drive-by download) to fix it. The link leads to a bogus website where hackers can steal your login details using info-stealer malware.
- Fake Job Offers: Fraudsters may e-mail you a job offer from a well-known organisation using open mail relays. They ask for your Social Security number and bank account information to “process your application.” But what they’re really after is your identity, personally identifiable information and your money.
Always go with your gut instinct when you suspect a particular e-mail attachment, or link, as the old saying goes, “If anything appears too good to be true, it probably is!”
Sample Information
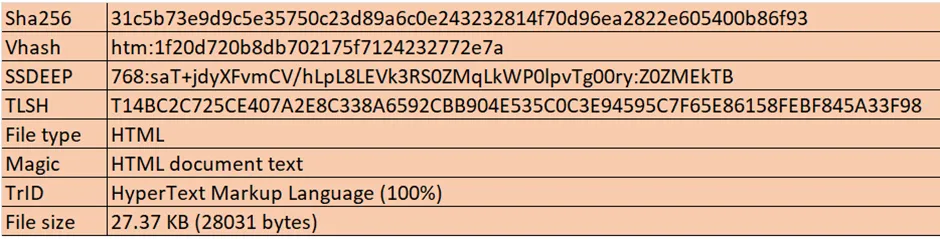
Anatomy of malicious HTML files
An HTML file contains Hypertext Markup Language that formats the structure of a webpage. HTML code is based on tags, or hidden keywords, which provide instructions for formatting the document.
Types of HTML files:
- Transitional:
Transitional is the most common type of HTML. It has a flexible syntax, or grammar and spelling component. Over the years, transitional HTML has been used without syntax restrictions, and browsers support a ‘best effort’ approach to reading the tags. If tags are misspelled, the browsers do not correct web developers’ errors, and they display the content anyway. Browsers do not report HTML errors – they simply display what they can. This is the ‘best effort’ concept. - Strict:
The strict type of HTML is meant to return rules into HTML and make it more reliable. For example, the strict type requires closing all tags for all opened tags. This style of HTML is important on phones, where the processing power may be limited. A clean and error-free code helps to load pages faster.
3. Frameset:
Finally, a frameset allows web developers to create a mosaic of HTML documents where multiple documents can be connected into a single screen. This technique is often used to create a menu system. You click on a menu item on the left side of the screen, and only the right side of the screen re-loads. The menu stays in place.
Technical Analysis of HTML Phishing Sample
Snap 1: Static View of the Sample Code
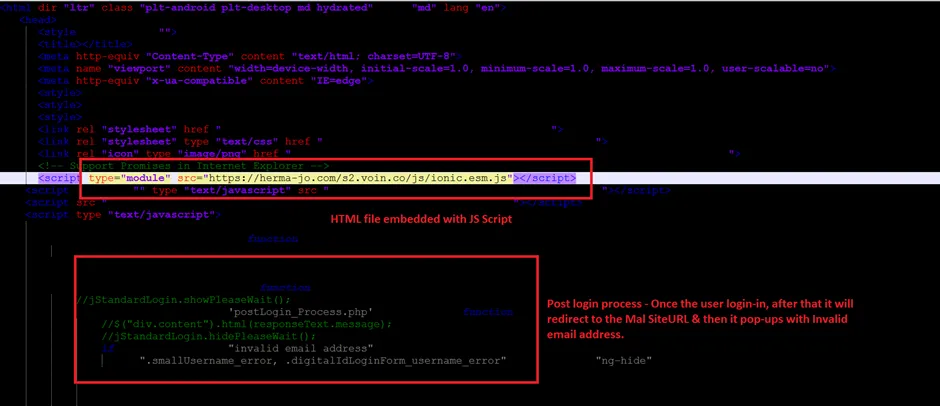
Snap 2: Sign_In page
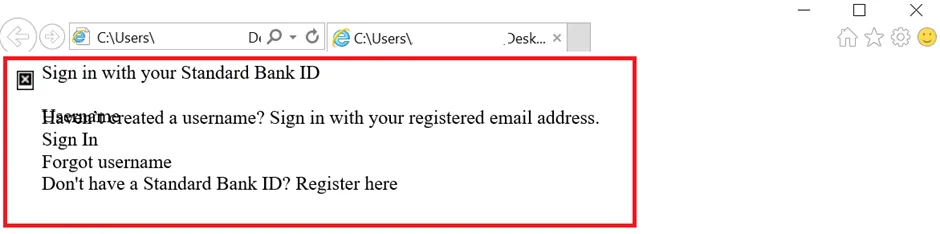
Snap 3: Phishing URL
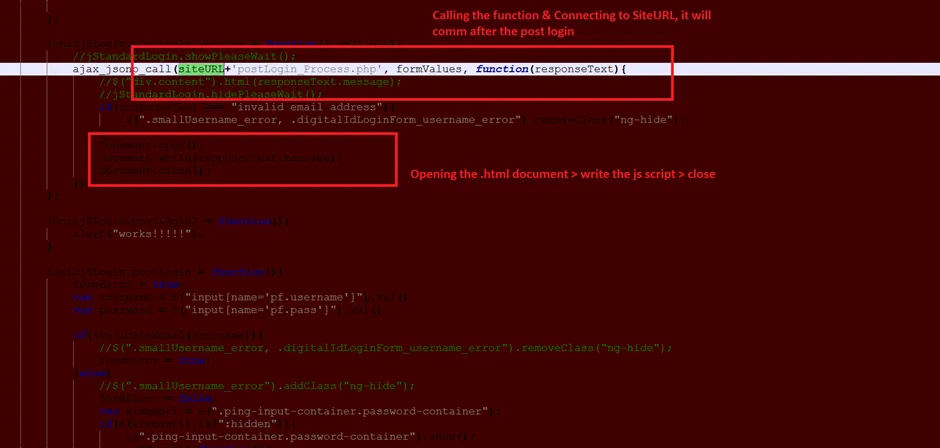
Snap 4: Creation of the FORM
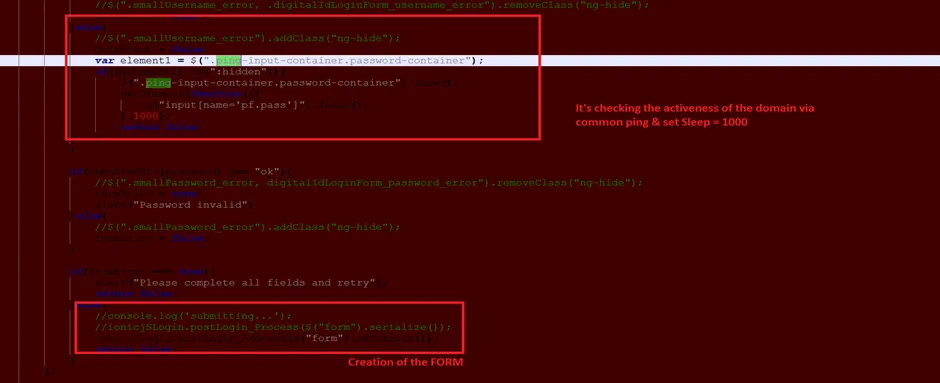
Snap 5: Method FORM_ACTION
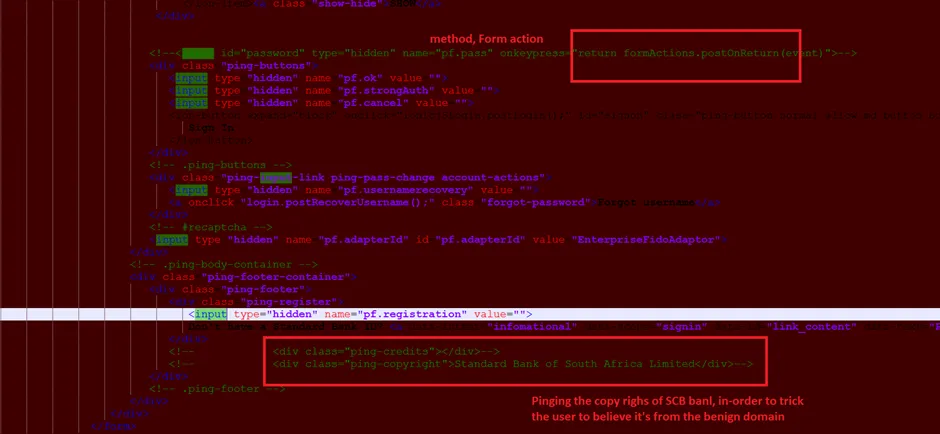
Snap 6: Initial – Indicator of Compromise [IOC]
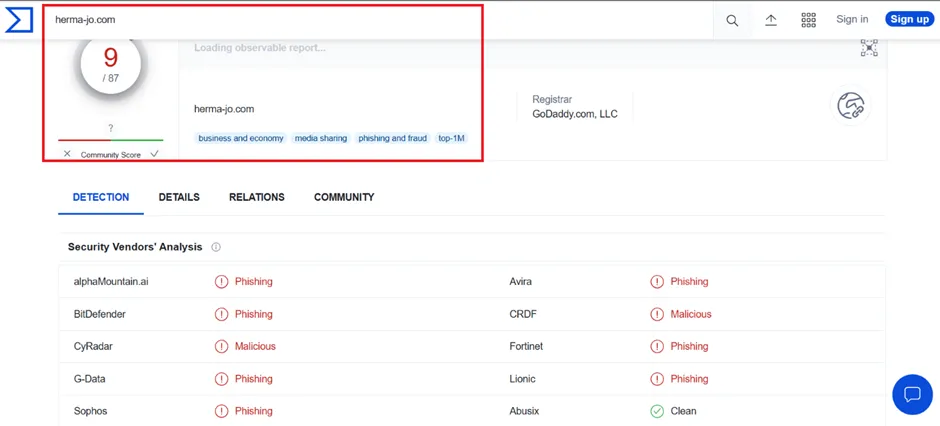
Snap 7: AV Vendor Results
Goals of Phishing Attack
The main goal of a phishing attack is to steal personal or financial information. First we should identify and understand what data is at risk, next we assess why it’s important for adversaries to hack. Once the data is stolen, they will sell username, passwords, location, identity proof and relevant PII information on the dark web to either cashout with data dumps, or demand a ransom from the owner.
Here are different ways the attackers can make money from your data:
- Steal data for personal gain.
- Selling data on the dark web.
- Obtain data for another entity which will act as a info-stealing service, or hacking as a service.
How to prevent Phishing attacks?
- Never trust any alarming messages.
- Employ common sense before handing over sensitive information.
- Do not open attachments from unknown persons.
- Avoid clicking embedded links from unknown resources and hyperlinks.
- Ensure your software and operating system is updated periodically
Indicators of Compromise – HTML Phishing Sample
| SHA256 | MD5 |
| 31c5b73e9d9c5e35750c23d89a6c0e243232814f70d96ea2822e605400b86f93 | 7b964e275c7aaba4872cb4149aec31d9 |
| e71ea10bf6478be49986762ee2582618549b91e5c298543ab0c2f9fae9695fea | fb40d341a1f849276016e54dd117627d |
| 6e2d5b4ea4ad25a26365fd8fd05dd1415998a81bc5a193d49cf8b68c3097b9c1 | e29d52e26cb26c1befbdc6b7f4ea5019 |
| bd56fae802c6baba63fb81297f440637829d6b1b94fd740dff855496e88ec874 | 2b3f3b5ad10d130149f7b7df82746b3b |
| 0649a6f75fefafe32227168bec17ceb5ef32a8949b77d8cd268f7b98fefa5688 | b3f002b3e65dae18e536871f08c095d9 |
| 625558994bae853add81771f9031a9f18d27b629b4f50a60c5a70a7e592bfda1 | 0721ec7ed184a965e6d0cee9cca7c815 |
| ec0acbfa70e80b60129313181f1f82ef0cc5616029294572579f31f83b792a01 | 0d5f14531c6257e9bd47a6fd1dc1daa3 |
| e9efa79b011448ce550d2e2de4c0afa348abbe8ad394691a4f9c9d9d7deb2b93 | 65b3d0f106282b427682e7d0d54c1051 |
| 2a5c9c5f50f83d73d0b933672ec6c87e7887efc6cbad1b7f8a787e8bbb066be7 | 3fc8a6814241b2d428eaf984db12b4ea |
| 0e22029654cfde2029b1cdc4c9386f83c838285bd30a8d846ceee985b524014b | e514de697f9f72c8138cf75a112149fa |
| 9427270e2b592afc3f49e67e025055ced06c2890c7f43466956c4b6ae9257123 | ef747b979cd66e121e5a063c0ca3355e |
| 3b3453e9063a2e80ae63ad528d9f0521ccd88f2eca7d482d35ed76b605c32fdf | 8e0cd15b03bc3cf16790a244c5c9fd2e |
| fe0863ce546dc81fa06729d0df8510dfdee7f119100e1f14210f983d3c614518 | c080f4cc983308e65640cab47f3313b0 |
| e4f62c7539ce7486aeb9d332a25cb77d505822f8e6e9932f661c9ba1c85b8988 | f032651553b4570f4dc403a79ea1689c |
| a46b1f4c858f458e0e979609b7a73cd335131ed6cf47972c3a130ecf810d759d | abf99d36d1a13a3a751f06a39a4e9ca5 |
| 45c12fcc3a012dc4536369a149906c697b4f66be03c918eec678f563d3014f78 | dacf65dbe92bba49a281359861e8a79a |
| 2473f0e216afc8be9d4d0f061e31d418efaf2d34bbc904fc254f4018adb8b4cb | f8def69761689c15937c67c2a3645cdb |
| 6708deac2c48d44a3ae2e804ec128279fa9499a35e8c3c3f3b8e49b66e3bdf0f | afecd14f25b5956d8650c110bd10eefd |
| 08923c59f3d68541dd1fcc8dac4dee4559d941b833cba11a84c6d2c578a9f53e | 1f34bc811b268faf8c6b2cc23350e9d9 |
| eab3c0440b9d2226ab80c7f368c8378616e4034a144cc99a3c3f189618798600 | a1501bfa7b98921fb2e38e42432a4716 |
| be22e18c25e6b41ddfa10cdd9b458cfc0f51a29db0713af26912435781f1e125 | 43e424d3db6344652103c7d468d874ab |
| bbf8020232a4996791d2d05684390113373bacef08c10a72aa2e68259c4872a0 | 635d91390ad3282ccd5272f554a23421 |
| e249435b653a4ca721c31d14544a756d41d94b3539a0963aea75befef72a0de4 | 9e29ad7f215e3d6c6bc606f84f8d4ec4 |
| 21562256520a74aa82e25999c9ccd18def86bc9d7103bb8808e8d65ee0aded44 | 09471691d09ab9f29d0d4df7b02fedac |
| 79cc9586c94e236cd5d577852ee6cee651feba4fc07399de131659b754aa7a05 | 19a111708d6beadfa532bed29d77e0bb |
| cd8b0fa56fe0e13f60d36d39a0b47869fe4f3def800cf8c77c3d4472b8764d81 | 51bc6549267e4fb61e530c95ed052360 |
| da0cc800071db57d40590268b3c0a7310b0f56d6326d3a5d662ca940bc3ebd9c | 6de6a08bd12e0ea982d619823e1e12c7 |
| e3c643f9dc479830b2c29b005a5d72d4bb42240ec1b0e04264d1b962043fb009 | 1bc78e394b79ca469415d6606ee80d04 |
| e0b0cd913409b859591667294a1faaef7bed41ffc2e1956904b0ff494daea529 | d9b3a01a77a800ccacbfc865354889ee |
| fedeb8d6ad38156ea47bbe310cd62c6676526456f1b61ace361134c37ca7ef05 | 9f8e3524b4377e8893fde9f06a412ff0 |
| ca7af2c1d9100e49e8b9232e98db8ed4b8dab6c5f302e63c330be2d0686d9897 | d31490ec88e0001c655ce383c6c1a512 |
| c88286743063982453ede36651710d7e60643cd9ab64c6d600a2f629487f29b8 | 4ace21945e68c1208191748cfced0b7b |
| 0480803702ad747a019ae7fc655a53aaaa87e79ab60b24887ea86089fc33d336 | 333341dec8cb9f2f84872f3d60f699ea |
| 693fdf0adaf807317e36c4591e6983cae6fb57cc09820b8dc08492e7dd6cb87e | b812986fb4a33854018a40e3375608ad |
| 2ecf2e3955d9b718c62d19b5d20be3486d546120364ffff1baa436a521f9b727 | 58b73f9f6cb45471a0944e5273711c32 |
| 0f75c1833bd91d9331d2c3f7dfeabe6671e2557c16489cd11dc078c2577081b9 | 20ef5b3e3a62ee5ef523c50e177f61c4 |
| b30d2268925772e3f0bf72eb0a4504a3aa479d2bcb195bd43773375bed3d6dce | 4e39c525e8d732673de68601bd5d3a1b |
| 3754dc2a8d23354029b0f96170e03b80d65355ae28d9c421772ef22eb4346b21 | 0ac5f853e0a24b4b3a9b956b8b92e399 |
| 2836ba0b0d27bde924f5bb5198e3377fb9daec9031f1b590a0251d4af09d5971 | d61deb4122049070cf4ed7568e8744ee |
| 2eb51ebccea8c88941c9fea4a17f854ee3accc855dbc5fa4dd39f885c52bb5ba | d7a11a5291d997183ff9b945ab79074e |


