
IcedID, also known as BokBot, is a Trojan-type malware that specifically targets Windows-based systems. Its primary objective is to steal sensitive information like login credentials, banking details, and personal data. IcedID focuses on carrying out financial fraud and supporting various forms of cyber crime. It achieves this through web injection attacks, which involve manipulating web pages to capture user credentials and sensitive information during online banking sessions.
The stolen data is then transmitted to command-and-control (C2) servers under the control of the attackers. Furthermore, IcedID possesses the ability to download and execute additional payloads, enabling it to enhance its functionality and engage in various malicious activities. It is also capable of lateral movement within a network, potentially compromising multiple systems.
Before we delve into the technical analysis, let’s take a look at the key characteristics of IcedID malware:
- Distribution: IcedID is often distributed through phishing emails containing malicious attachments or links. These emails might appear legitimate and convincing, luring victims into opening attachments or clicking on links that ultimately lead to malware installation.
- Infection Chain: Once a victim’s system is infected, IcedID typically employs a multi-stage infection chain. This means that the malware goes through multiple steps to download and install its various components, making it more challenging to detect and analyze.
- Information Theft: IcedID specializes in stealing sensitive information, primarily focusing on financial data. It can capture login credentials from web browsers, financial software, and other applications. Additionally, it can intercept and manipulate online banking sessions to initiate fraudulent transactions.
- Evolution of IcedID code: Malware developers often update and evolve IcedID to stay ahead of security measures. New versions might include improved evasion techniques, encryption methods, and more advanced communication protocols with command and control servers.
- Botnet Functionality: IcedID can turn infected machines into part of a botnet. This means that attackers can remotely control and utilize the infected computers for various malicious activities, such as spreading malware further or launching distributed denial-of-service (DDoS) attacks.
- Persistence: IcedID aims to establish persistence on an infected system, making it difficult to remove. It can create registry entries, scheduled tasks, or use other techniques to ensure that it remains active even after a reboot.
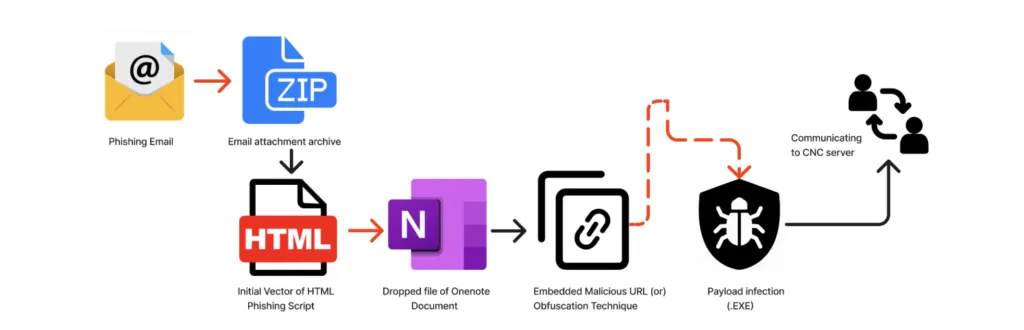
Infection Chain:
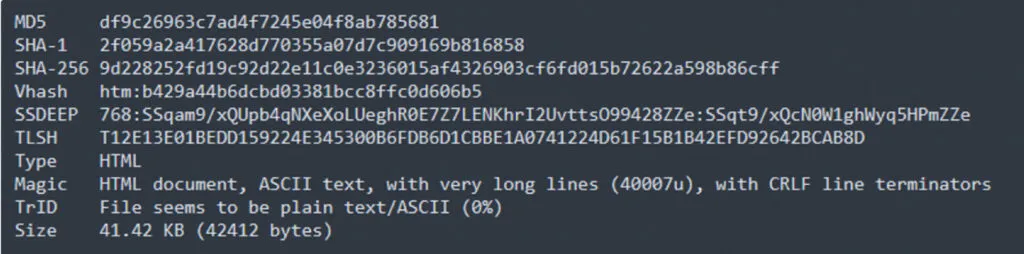
Sample Information:
Threat Name: IcedID | Classification: Trojan | Category: Dropper
Technical Analysis of IcedID HTML:
HTML, short for Hypertext Markup Language, is a markup language utilized to establish the structure and visual presentation of web pages. An HTML file is composed of various elements that define the content and organization of a web page.
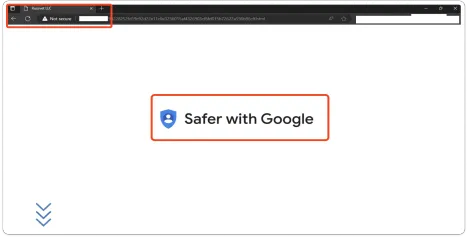
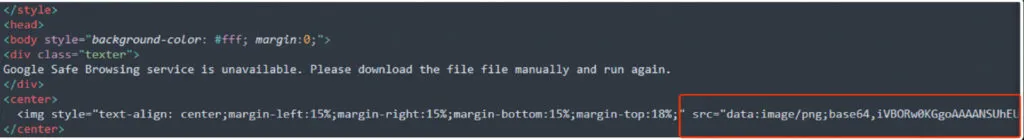
After opening the HTML file, the victim will get this page. Also, it states that it’s from the safer google link.
Initial Template of the Iced ID Campaign
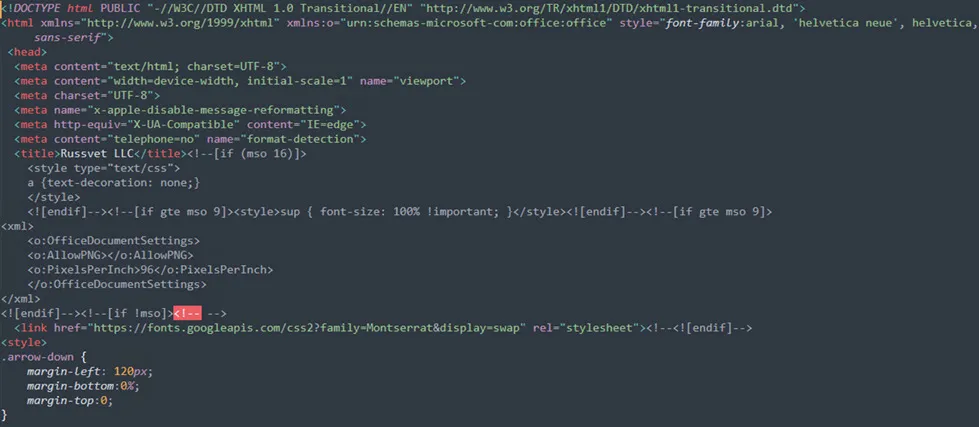
Main Content of the HTML file
Let’s examine the HTML file structure:
<!DOCTYPE html>: This declaration specifies that the document is an HTML5 document.
<html>: The root element that encompasses the entire HTML document.
<head>: Contains meta-information about the document, such as the title, character encoding, and external file references.
<title>: Sets the title of the web page, displayed in the browser’s title bar or tab.
<meta charset=”UTF-8″>: Specifies the character encoding of the document as UTF-8, supporting a wide range of characters.
<link rel=”stylesheet” type=”text/css” href=”styles.css“>: Connects an external CSS file to style the web page.
<body>: Contains the visible content of the web page, such as headings, paragraphs, images, and other elements.
<header>: Represents the introductory content of the web page, often containing branding, logo, and primary navigation.
<h1>: Denotes various levels of headings, with <h1> being the highest level. ❖ <nav>: Defines a section of the web page containing navigation links.
<ul> and <li>: Used to create an unordered list and its list items.
<main>: Represents the main content of the web page, excluding header, footer, and minor sections.
<section>: Defines standalone sections within the web page.
<p>: Indicates a paragraph of text.
<img src=”image.jpg” alt=”Image”>: Inserts an image into the web page, with the source (src) attribute specifying the image file and the alt attribute providing alternative text.
<footer>: Contains the footer of the web page, usually including copyright information, links to terms of service, and other relevant details.
Base64 Embedded Content:
Here we can see the text content which states that “Google safe browsing service is unavailable. Please download the file manually and run again” It’s a fake template to believe that the file is from the legit google domain.
Base64 Encoded Technique:
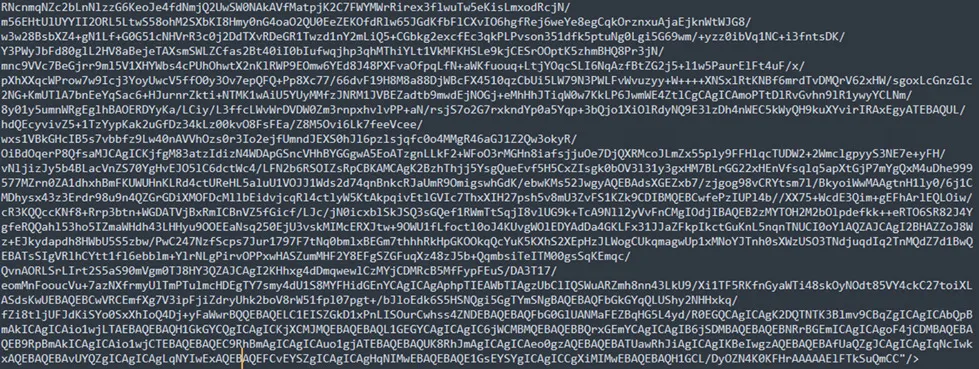
Base64 Main Content:

Decoded Content:

Downloaded Decoded Sample
The choice of encoding is important as it influences the storage of strings, which consist of character collections, in memory. Additionally, managing encoding can be challenging due to potential information loss, errors, or inconsistencies they may introduce.
Indicators of Compromise for IcedID sample:
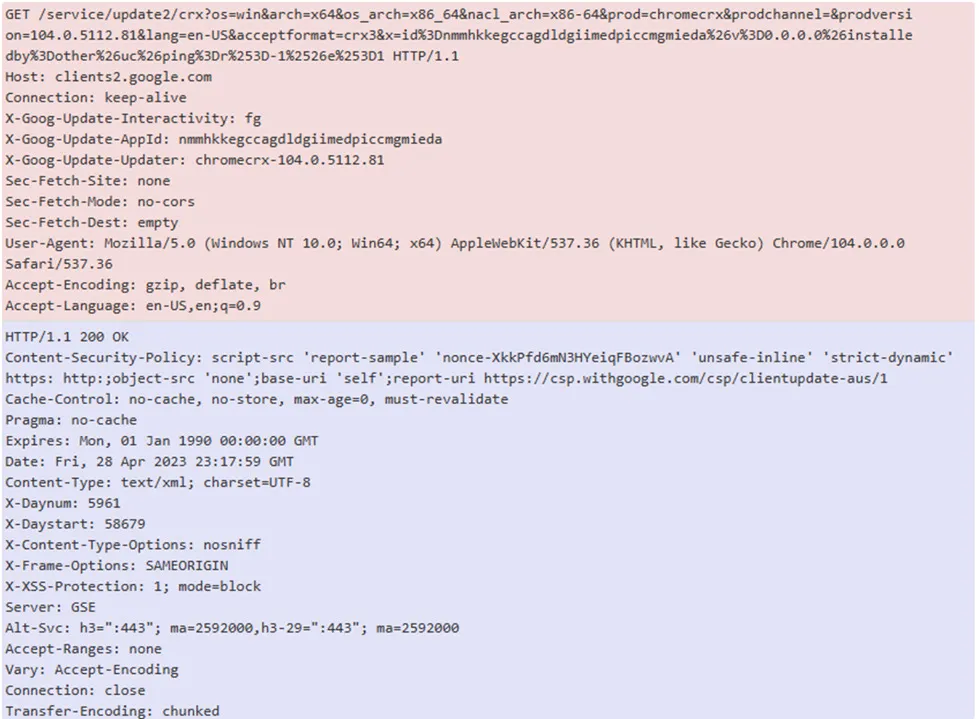
Here’s the captured data of GET /crown20(.))js HTTP/1.1 Packets
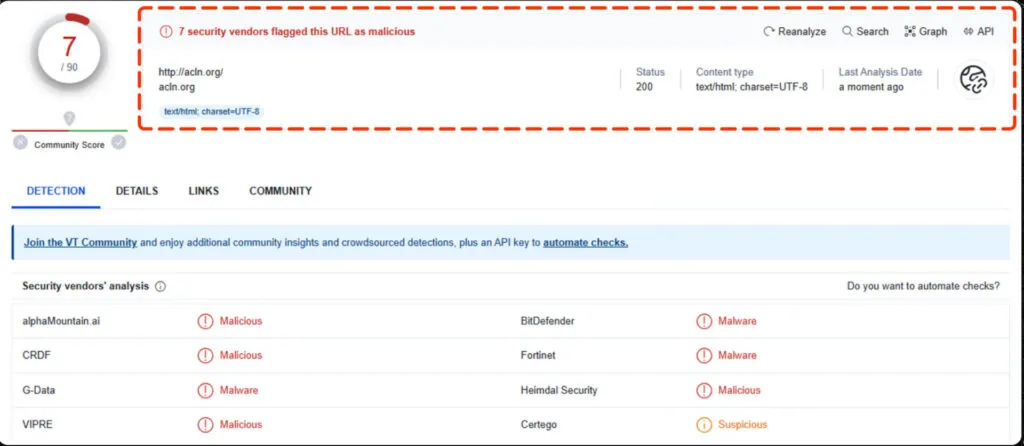
VT Results:
In the VT results, it shows the submitted URL is malicious and it’s downloading the IcedID payload malware and surprisingly it’s still in live.
MITRE ATT&CK Tactics & Techniques for IcedID sample,
| ID | Tactic | Technique |
| TA0001 | Initial Access | Spam Email Phishing Attachment |
| TA0002 | Execution | Windows Scripting – HTML |
| TA0003 | Persistence | Modify Registry Log-on Initialization Scripts |
| TA0004 | Privilege Escalation | Scheduled Task / Job Process Injection |
| TA0005 | Defense Evasion | Virtualization and Sandbox Evasion Technique Obfuscated file or Information |
| TA0006 TA0007 | Credential Access Discovery | OS Credential Dumping LSASS Memory Input Capture System Software Discovery Process Discovery File and Directory Discovery Query Registry |
| TA0008 | Lateral Movement | Remote file copy |
| TA0009 | Collection | Credential API Hooking Archive Collected Data Data from Local System |
| TA0011 | C&C Server | Encrypted Channels Non-Application Layer Protocol Web Protocols – Standard Application Layer Protocol Ingress Tool Transfer |


