Version:1.0 StartHTML:000000270 EndHTML:000015702 StartFragment:000007053 EndFragment:000015634 StartSelection:000007053 EndSelection:000015630 SourceURL:https://www.lmntrix.com/Lab/Lab_info.php?id=9&url=Analysis%20of%20Malware%20Sample%20-%20Proforma%20Invoice LMNTRIX Labs LMNTRIX Labs
Summary
This malware sample was found in a recent spear phishing attack on one of our client networks. The sample in question is a .net file and comes with the name ‘Proforma Invoice’. We are sharing it for the benefit of the community.
File details
MD5 3ed79c9a988e427db39aa62e625a2116
SHA-1 85b0198ba27fa5b8e1d3625dbcd45776d64cd741
SHA-256 de30a5cc95453a372b717a632fc6c9ec0b101c2afa9ba5e472e95025fd227ddd
Size 929.5 KB (951808 bytes)
Type Win32 EXE
Magic PE32 executable for MS Windows (GUI) Intel 80386 32-bit Mono/.Net assembly
Detection ratio 37 / 57
First submission 2016-09-23 07:41:57 UTC ( 5 months, 1 week ago )
This malware is already present in Virus Total, having been initially submitted in September 2016.
Characteristics and Behavior
• Sends PC main information to external server
• Injects code into other processes
• Common autorun registry key
• Access browser sensitive data: Mozilla SeaMonkey
• Access Mozilla Firefox security module
• Contains cryptographic functionality
• Access Opera passwords
• Steals Internet Explorer passwords
• Loads PE into other process memory
• Runs dropped executable
• Access Mozilla Firefox history
• Contains HTML page
• Access Mozilla Firefox passwords
• Access email client software sensitive data: Thunderbird
• Access email client software sensitive data: Windows Livemail
• Access email client software sensitive data: Outlook
• Access email client software sensitive data: IncrediMail
• Access email client software sensitive data: Eudora
• Access email client software sensitive data: Group Mail
• Access Mozilla Firefox certificates
• Access FTP software sensitive data: Filezilla
• Access instant messaging software sensitive data: Google Talk
• Access Mozilla Firefox file that stores the annotations, bookmarks, favorite icons, input history, keywords, and browsing history
• Access instant messaging software sensitive data: Paltalk
• Access instant messaging software sensitive data: Yahoo Pager
• Runs existing executable
• Suspicious delay
• Check user main folders path
• Drops .EXE file
• Access Windows sensitive data: Windows Profiles information
• EntryPoint points inside a writable section
• Gathers system main data (MachineGuid, ComputerName, SystemBiosVersion …)
• Loads PE into its own memory
Process, Registry, Network Activities
%appdata%\sapp.exe
This created sample is a duplicate of an original file – it also created an autostart entry for this file to keep persistence.
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run “Application”
Type: REG_SZ
Data: C:\Documents and Settings\user\Application Data\sapp.exe
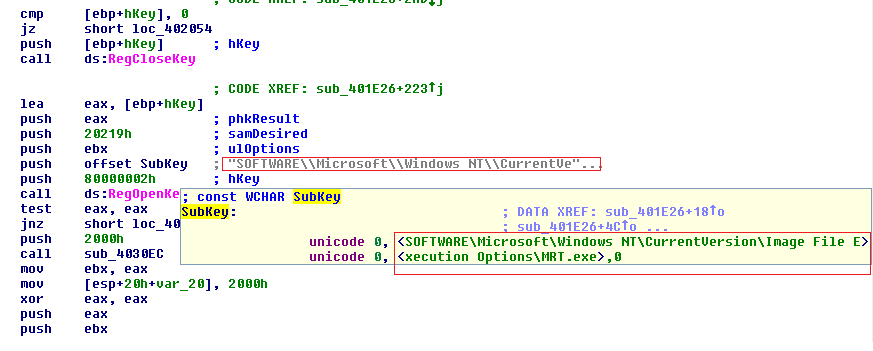
We noticed that sample creates a new process called Regasm.exe, which is part of the .net framework in Windows. Strings within regasm.exe confirmed that this malware collects passwords by logging keystrokes.
Very Important Strings
Important.exe
hxxp://www(.)twentysixjune(.)biz/jonoTwo-4sept-14oct/
Window title:
End:]
Machine Time:
Keystrokes typed:
Keystrokes
[Back]
Notification
Time:
Text:
$C$l$i$p$b$oa$rd$
SupremeQuality
MediumQuality
LowQuality
#image#/#upload#.#php#
.jpg
ylbmessAgnitucexEteG
Key
$pos$t$.$ph$p$?$ty$p$e$=$k$eys$tro$ke$s$&$mac$hi$ne$na$me$=$
&windowtitle=
&keystrokestyped=
=emitenihcam&
sdrowssaP
#po#st.#ph#p?#typ#e=p#assw#ords#&mach#inen#ame=#
&application=
&link=
&username=
=drowssap&
draobpilC
$po$st$.$ph$p$?$ty$pe$=$cl$ip$boa$rd&$mac$hine$nam$e=$
&clipboardtext=
Screenshot
$pos$t.$p$hp$?$typ$e=$not$ific$a$tion$&$mac$h$in$e$n$a$m$e$=$
Software\Paltalk
InstallerAppDir
Win32_LogicalDisk.DeviceID=”
VolumeSerialNumber
Software\Paltalk\
nickname
pwd
Passwords
Paltalk
Program: FileZilla
FileZilla\recentservers.xml
FileZilla\sitemanager.xml
$<$H$os$t$>$
$<$/H$o$s$t$>$
$$
$<$/$P$a$ss$>$
Filezilla
Programfiles(x86)
programfiles
$\jDow$nloader\$config\dat$abase.scr$ipt
programfiles(x86)
$\jD$ownloader\con$fig\databa$se.sc$ript
#INS#ERT INT#O CON#FIG VA#LUE#S(‘A#ccoun#tContr#oller#’,’
JDownloader
Software\DownloadManager\Passwords\
Program: Internet Download Manager >6
User
EncPassword
IDM
Advapi32
RegOpenKeyEx
RegCloseKey
RegQueryValueEx
Software\IMVU\username
Software\IMVU\password
Imvu
Chrome
Firefox
Internet Explorer
Opera
Safari
URL
User Name :
Password :
URL :
Web Browser :
Browsers.txt
Password
/stext
RecoverBrowsers
Outlook
_Thunder_bird
Eudora
Incredimail
Netscape
\Mails.txt
RecoverMail
Application
Email :
Server :
Application :
kernel32
KeyBase
ntdll
LoadLibraryA
.dll
user32
$Set$Window$sHook$Ex$A$
These strings show that this file is a password stealer. It collects keystrokes and copies clipboard images then uploads them to hxxp://www.twentysixjune.biz/jonoTwo-4sept-14oct/image/upload.php
It also collects information from the following:
Software\Paltalk\
nickname
pwd
Program: FileZilla
FileZilla\recentservers.xml
$\jDow$nloader\$config\dat$abase.scr$ipt
JDownloader
IDM
Software\IMVU\username
Software\IMVU\password
Imvu
Chrome
Firefox
Internet Explorer
Opera
Safari
URL
User Name :
Password :
URL :
Web Browser :
Browsers.txt
Password
/stext
RecoverBrowsers
Outlook
_Thunder_bird
Eudora
Incredimail
Netscape
\Mails.txt
RecoverMail
Application
Email
Malicious Url
hxxp://twentysixjune(.)biz
Ip address is: 80(.)82(.)78(.)57 : 80
This is the malicious url we found within the strings, even Virus Total flagged this url as malicious by six vendors.
https://virustotal.com/en/url/03f84b1e66f394d4d506d16c44434136496399f7ed3cfeccb69c9725951d5ea2/analysis/1488780554/
AegisLab WebGuard Malicious site
Sophos Malicious site
Trustwave Malicious site
BitDefender Malware site
Fortinet Malware site
G-Data Malware site
Code Injection
Process Code size Virtual Address
C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe 516096 400000
C:\Windows\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe 364544 400000
Conclusion
We recommend blocking the malicious url and searching for the executable (sapp.exe) in the application data location then removing the sapp.exe.


