In the previous post, we saw how the Agent Tesla malware has infected its victims by using the PS1 Powershell script to invoke the web request from the blacklisted IPs. Agent Tesla’s successful delivery method is through email, either in the form of spam or more targeted phishing campaigns with OPEC (Oil Production Export Countries) and a COVID-19-based theme, where the malware is sent as an attachment, a macro-enabled Microsoft document (.DOC,.XLA/.XLS,.PPT file format), Microsoft document add-on files (.XLL), or a compressed archive. According to LMNTRIX CDC’s observations, there were reports of over 8000 customers delivering files infected with Agent Tesla RAT as recently as 2021/22.
This kind of email contains Microsoft Office documents (Excel) of .XLA/.XLS files, but this sample uses the .PPAM extension, which contains VBA macros to execute and automate tasks. ‘.PPAM’ is an add-in file used by Microsoft PowerPoint where a program is used to develop slideshow presentations.
It contains components that can provide additional functionality, including extra commands, customized macros, and new tools for extending default PowerPoint functions. Mainly, it supports “add-ins” developed by third parties to add new features that attackers can abuse to automatically execute macros for further action on objectives.
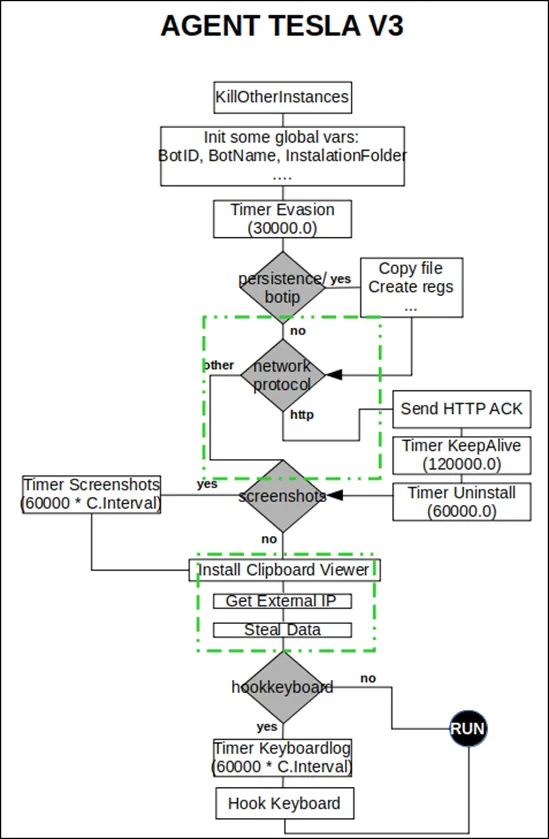
Control Flow Diagram of Agent Tesla RAT (Version 3x)
Infection Chain
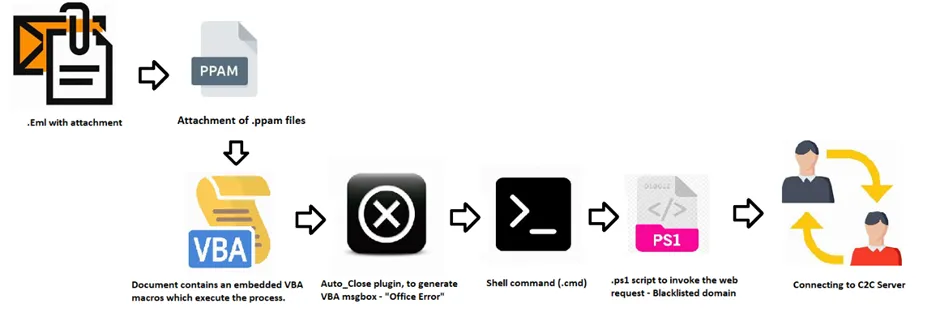
The initial vectors may vary depending on their targets and, it’s well known that the threat actors will perform basic reconnaissance methodologies before deciding on their method of infection.
Sample Information
PPT: 34c5d4ce20a550336303c0bdb5df78f6ed1727c3993e79e27d58f30ac5cbc055
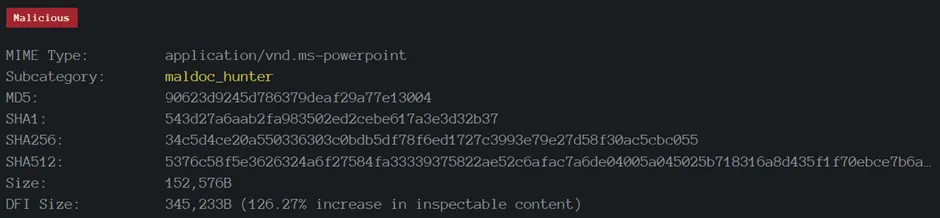
File Metadata
Technical Analysis of .PPAM Document
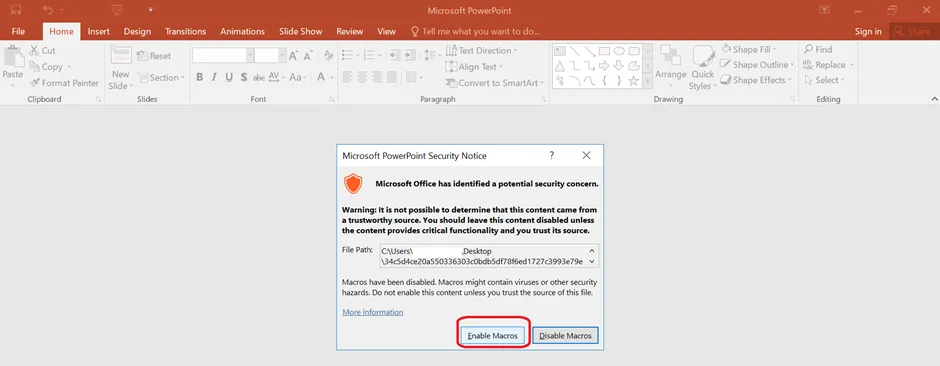
When a user opens an office file containing macros, then the macros will execute from the Internet. We are well aware that the VBA macro is a common method for malicious actors to gain initial access to deploy malware. These files are based on the Office Open XML standard. This is an XML-based file format introduced by Microsoft that is unreadable with PowerPoint versions earlier than MS Office 2010/2013. Now, we can extract & view the contents of the file. The XML file format is human-readable or machine-readable and designed to transport data over the internet.
The XML file format contains three categories:
- Section one with Document Identification
- The Document Content
- Meta Data with fields and facets
Malware Persistence
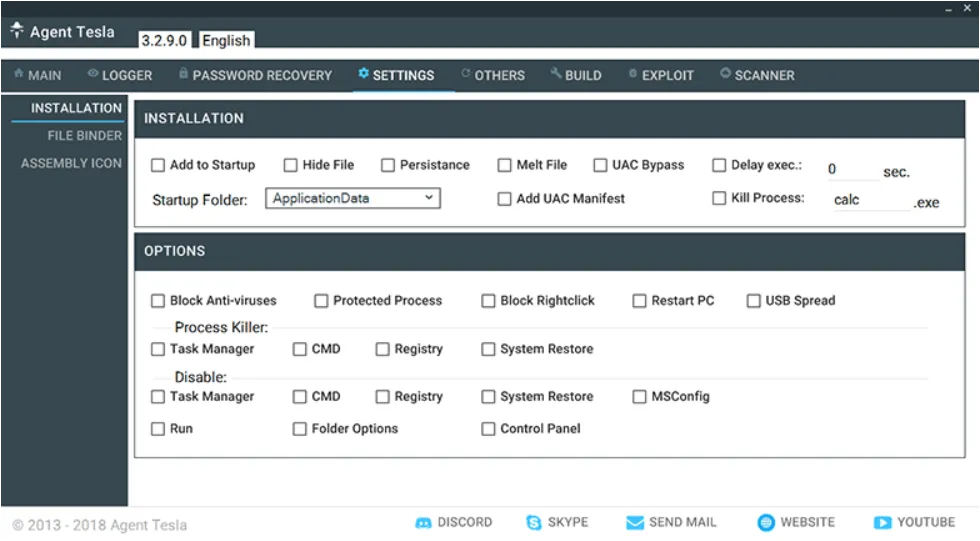
Agent Tesla malware can achieve persistence by creating the following registry entries on Windows:
\Software\Microsoft\Windows\CurrentVersion\Run
\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\StartupApproved\Run
Agent Tesla can also create a scheduled task by using schtasks.exe to add and/or modify the task schedule,
Process created: C:\Windows\System32\schtasks.exe” /Create /TN “” /XML “C:\Users\\AppData\Local\Temp\.tmp
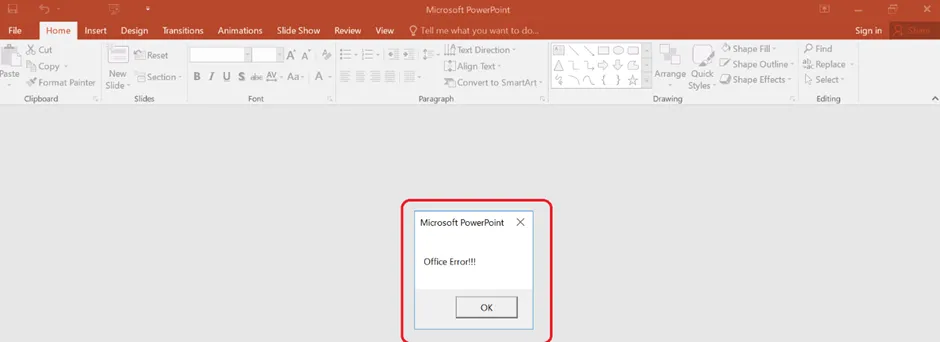
VBA_ Dialog msgbox

Once the user successfully executes the macros, the above mentioned message box will be displayed.
It can occur during the opening of the document, or, while closing the document.
This is a simple and known method to evade detection rules. (i.e;) Auto_Open () or Auto_Close () method.
File structure of the .PPAM file
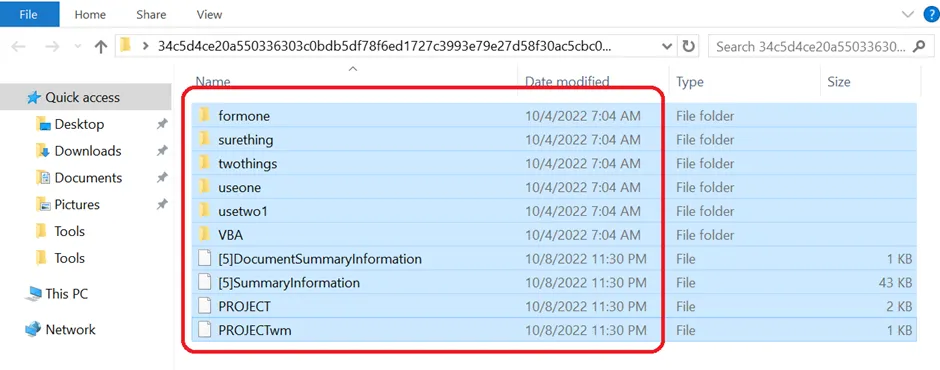
The folders shown above contain the base function of the process, which is used to initiate the VBA_Project macros. The VBA Project is where the modules and forms are stored when you write VBA code in Excel. Microsoft Forms is an Object Library Adding a reference to the Forms library, in-order to use the Forms library in a VBA project.
Temp files
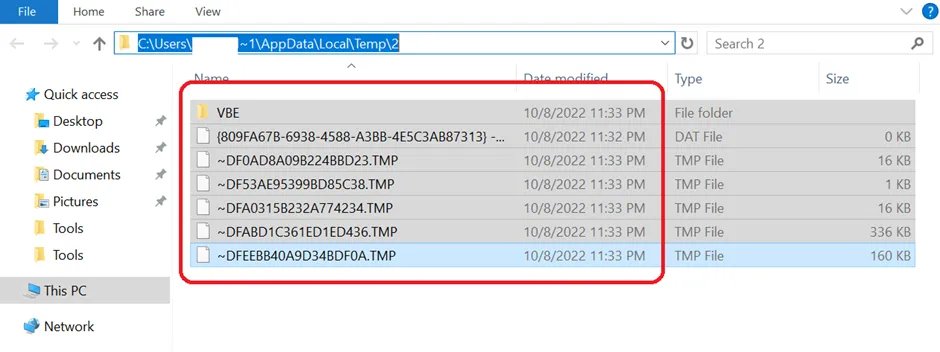
We all know that TEMP files (aka foo files) with the .TMP extension are temporary files that may be created by various software programs. It is typically generated while the program is running to temporarily store information, then is automatically deleted when the program is closed.
The temp folder is a prime target for malware such as Agent Tesla. Recent strains malware are often attached to or embedded in legitimate programs to perform malicious actions.
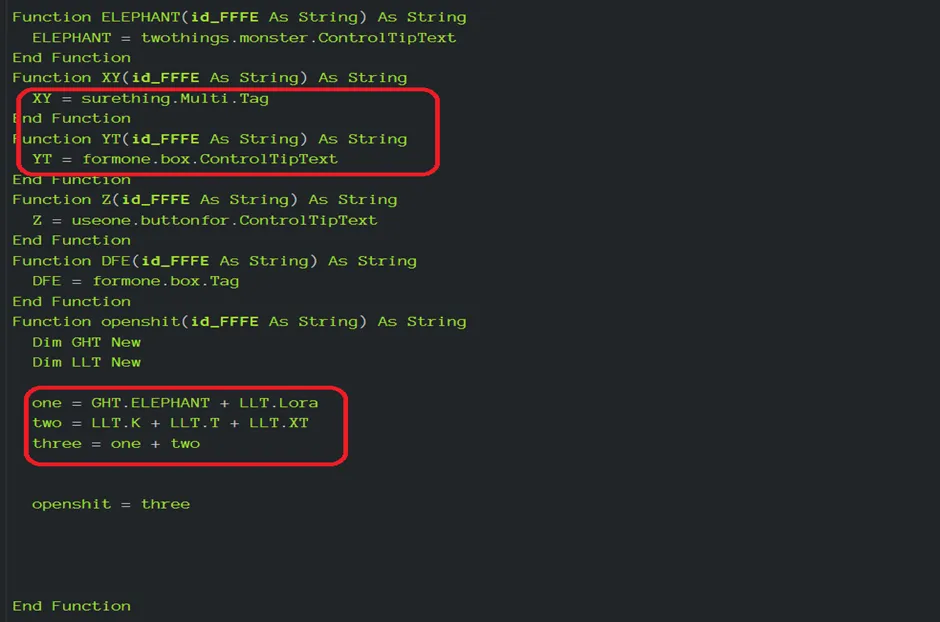
VBA Project Content
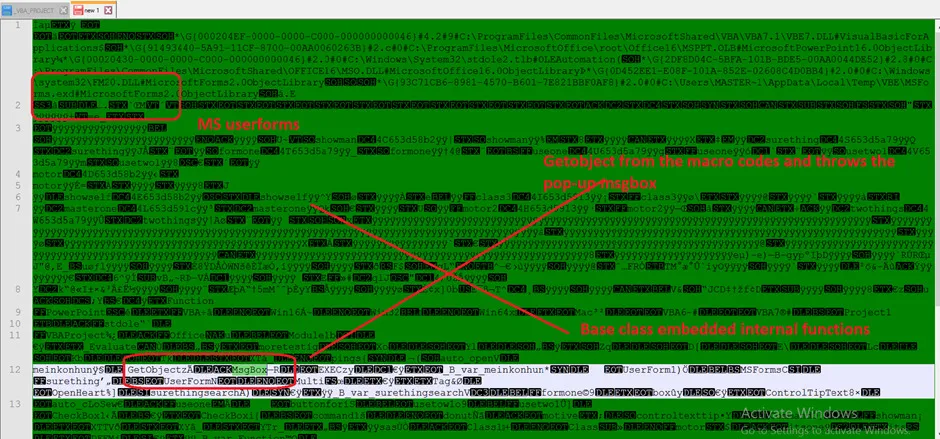
Decoded Content
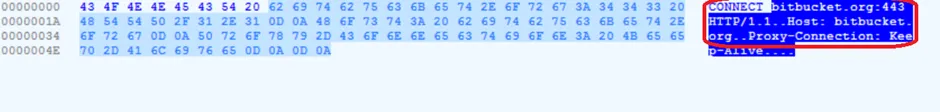
Command line for Powershell [.PS1] script
Once the macros are executed, using the powershell script, the malware invokes web requests from the domain shown above (bigXXXXet domain). Actually, the connecting domain is a legitimate website, but as we noticed the full URI of the website makes use believe it’s a phishing website.
How is it done? As per the VBA_project code, the URI is formed and please refer the decoded content.z
Indicators of Compromise for Agent Tesla Sample
| SHA256 |
| a47fdea7d22e15007dca78175d2b62d0a88d745ab5e5ff8d6ad371366f676ddd |
| 577af409d937659015fec1e5e48981c09cda84abc8a4705390904bac95a59fe3 |
| 56478080767f5507c7297a6d46b4ce6226a63e782050ee5e47bd102b747d006a |
| 40eacf74e5f8d9b40c3a70ba66a6c30deee60c2843f94fe387ccb0dbb7a2cd59 |
| 23e455928e180012c11d6badfd0959df2fdb57f10d9ce564fe2834e59a67ea77 |
| e3f7150d12f8307444828499346082247460fd350ea530f299d1c72f02f79404 |
| 0c49335c5d0b6ec74c37d319949f107c32b4b214094cb8a43498e01b45ac914d |
| c688588a8aa476d6803129466c7e30cc00a6b7de93b2a075b4c05d73e6478908 |
| bf088d4fba9d3eb52931451176129bbe7ac4e36522eee4316fee8c76fb230ea0 |
| 319917e9a462c0df63b73515651cb2fb4410cef2d55a1f1e54ea58c9867a32f5 |
| e4df172065976803c837e59f4036a3030f9e3c8594bc7c10bbee3649d10453d2 |
| 7f12e599786592ff2f1300213fb1349bef078589697ca483e4656ebc97533c9d |
| 375debad2f10b83029639f0824e336c0ca81b617c665209f67ccf6f4cb88c9e4 |
| 65a4a789f106ee9731dfa6e4afe2f09b4db15170c6d925332dd20f97d1fbdf2c |
| 44f3e7854ea6963412d6040957bfc7f8b753858abf9a0b84be9d8068463209ff |
| 83bd1e1e6f20f8e17e71f89f2a0c0d283903de6a81198fae6d96d3a55144d395 |
| 6b4ae1bde5c68bdc96647dc1154eeea23eda290a970f8ddd9991a67337ab3689 |
| df55c97ad5964486c9bfd99b7c977c96e3a6a44e3c9f8fcc12c481d4f779d06b |
| 051e42d9f748a49794271b9e766284caba867ec60371c41d338b192cb44a9eaf |
| 930001a1fabb96c66c6c995b48b17b3dfb8597c89f8a68947456b9700b974310 |
| 6713a526ffb1f9608dfb3769e696aff9908b0fc018447639c94c71f46dfe7ebe |
| ebe062b6f50f9d654583a7e4e10bfeb6a1b548b31f1a6ddd0168816437edc227 |
| 5429b2d7a20873db5dde39b1a2d3f202751ac3c732c02a4003a07d53b52d0d54 |
| 7ca99db4bd0190e141d3fd718f772fde1098131cdf5aee025d17eeb7c607a2ce |
Preventive Measures for Agent Tesla RAT
Recent updates from MSRC Security blog, suggests that users can block the execution of MS Office macros in files which are obtained from the Internet, or from an unknown source.
If you don’t use the “Block macros from running in Office files from the Internet” policy, you can use the “VBA Macro Notification Settings” policy to manage how macros are handled by Office. This policy prevents users from being lured into enabling malicious macros.
For more information, please check “Macros from the internet will be blocked by default in Office” from MSDN.


