
QBot malware is an advanced banking Trojan that focuses on Windows-based systems. Referred to as QakBot or Pinkslipbot, this malicious software aims to pilfer sensitive information, including login credentials, banking details, and personal data, from compromised computers. Email phishing campaigns and exploit kits are commonly employed to distribute the QBot malware.
In LMNTRIX Labs, we are covering the trends in the Qakbot campaign from last year. In 2022, we observed the QBot malware campaign through ISO files, and in March 2023, we blogged about the infection chain of QBot using OneNote. In the recent campaign, we observed that the QBot started to perform the attack campaign using archive files in emails that have malicious PDF files.
Infection Chain
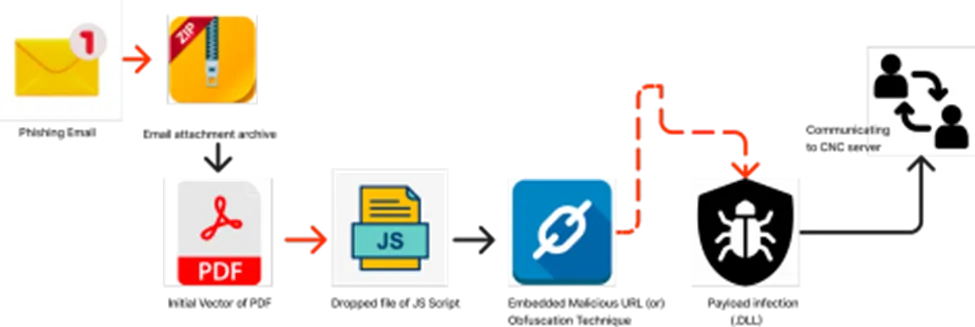
Upon execution on a system, the QBot malware takes measures to maintain a long-term presence by altering system settings and registry entries. It also possesses the ability to propagate through networks, infecting other interconnected devices. With its sophisticated features like keylogging, network reconnaissance, and remote access functionality, QBot can discreetly manipulate compromised machines, granting cybercriminals control and enabling them to engage in various malicious activities.
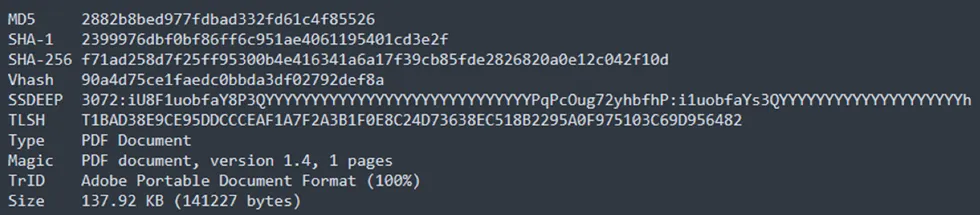
Sample Information
Threat Name: QBot | Classification: Banking Trojan / RAT
What makes Qbot stand out from the rest?
Qbot (Qakbot) stands out among bots and information stealers due to many distinguishing qualities and capabilities that make it a formidable and long-lasting threat;
- Persistence and Resilience: Qbot deploys advanced persistence methods, making removal from infected systems difficult. Its ability to make several copies, modify registry entries, and schedule tasks ensures that it persists even after removal attempts.
- Worm-like spread: Qbot shows worm-like behaviour, allowing it to propagate over a network and infect other machines. It copies itself to shared discs and removable storage devices, greatly expanding its reach and the possibility of future infection.
- Financial Focus: Unlike many other bots and information theft, Qbot’s primary goal is monetary gain. It is primarily designed to target banking credentials, financial information, and other vital financial data.
- Polymorphism: Qbot employs polymorphic code to constantly change its own structure. Given these dynamic code changes, it is able to avoid standard signature-based detection methods employed by antivirus software.
- Evasion Techniques: Qbot employs a variety of anti-analysis and anti-detection techniques, including the ability to identify virtual environments and sandboxes. It can postpone execution and/or alter its behaviour to prevent detection and analysis by security professionals.
- Network Reconnaissance and Internal Propagation: Qbot has network reconnaissance features that let it to locate and target weak devices on a local/internal network. It can also spread within the organisation looking for new targets to infect.
- Reverse Proxy Function: The malware functions as a reverse proxy, allowing attackers to utilise the infected system as a proxy, to access other internal network resources, allowing for lateral movement within a compromised network.
- Botnet Capabilities: Qbot can infect and control a botnet of infected machines, providing the attackers the ability to launch coordinated attacks, propagate spam, and engage in other forms of malicious activity.
- Dynamic Configuration Updates: Qbot may acquire new instructions and adapt its behaviour in real-time by dynamically updating its configuration from the command-and-control (C2) server.
- Continuous Development: Qbot has been around since at least 2008, suggesting that the authors are constantly updating and improving the malware in order to stay profitable and current in the ever-changing cybersecurity arena.
Technical Analysis of QBot
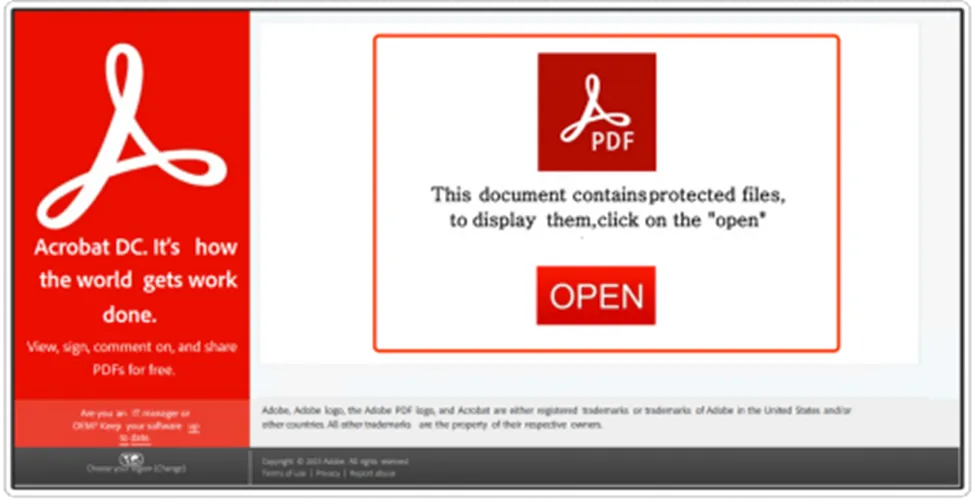
As usual this campaign commences through the distribution of spam emails, featuring content that states, “This Document contains protected files. To access them, please click on the OPEN button.”
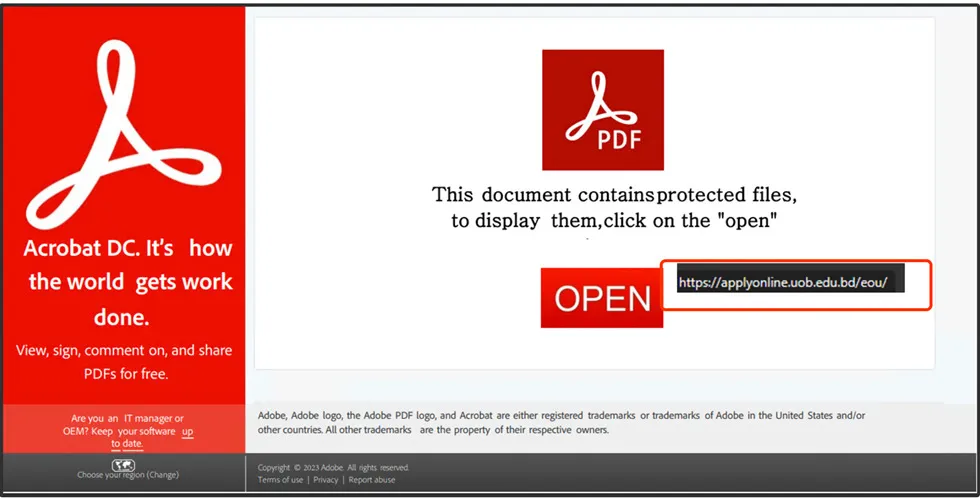
This is a trick used by the author to urge the victim to open the attachment file where it’s embedded with a malicious URI to perform various malicious activities to achieve their objective, and the Office document tries to convince them to disable security protection (Ex: Enable ActiveX or Macros), and so on.
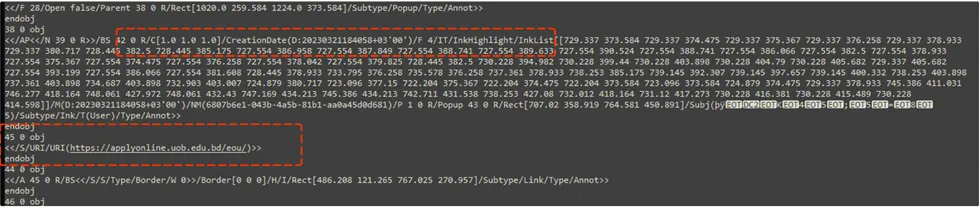
Insights on the Dropped .JS Script
After the PDF infects the victim’s machine, it proceeds to inject a Javascript file that contains an assortment of randomised functions, enhancing the complexity of the malware sample and enabling it to evade detection from AV vendors.
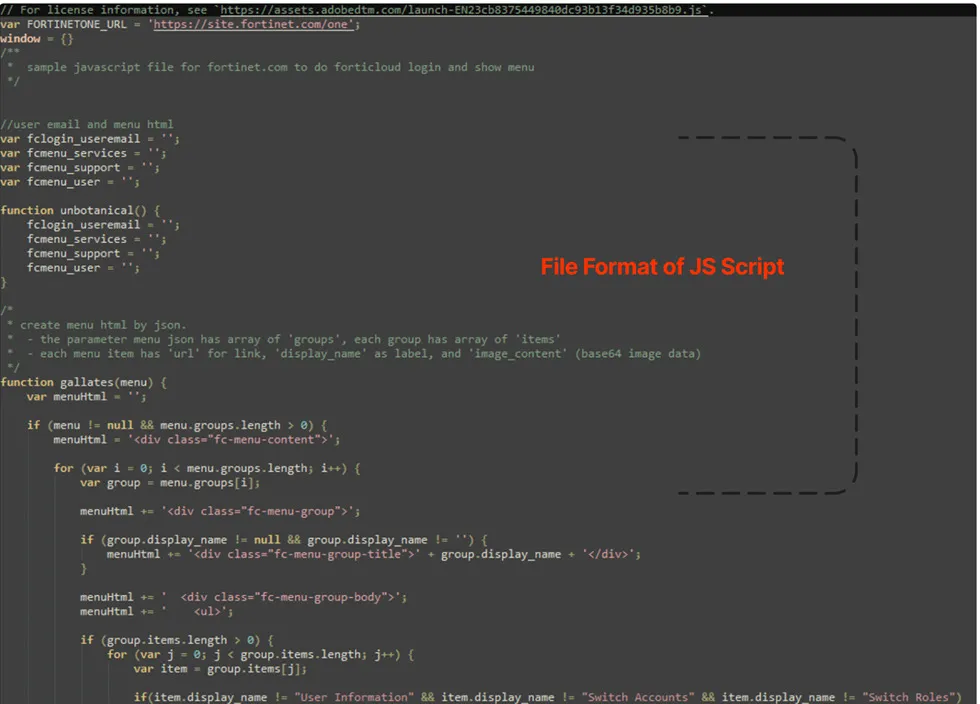
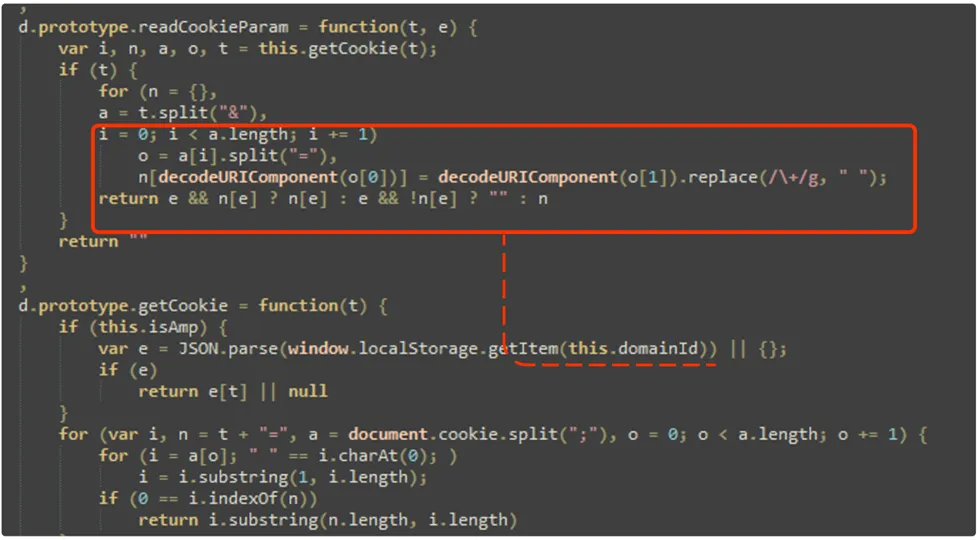
Here, the decodeURIComponent() function is used to decode a Uniform Resource Identifier (URI) component that has been encoded using the encodeURIComponent() function.
When data is passed in a URI, certain characters (such as spaces or special characters) need to be encoded to ensure they are properly represented in the URI string. The encodeURIComponent() function is used to perform this encoding.
The decodeURIComponent() function, on the other hand, is used to reverse the encoding process. It takes an encoded URI component as input and returns the decoded version of the component, restoring it to its original form. This function is commonly used to extract data from a URI that has been encoded.
.DLL Payload File:
Following the successful injection of the JS script, it proceeds to download a DLL file, which is then utilised to execute a DLL side-loading injection attack.
Here’s the Process Tree for the Qbot sample,
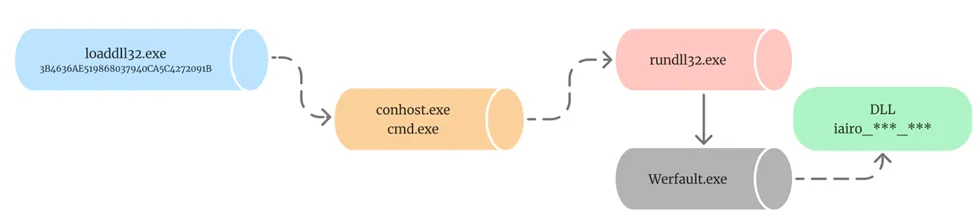
What is a DLL side-loading injection attack?
Attackers use a technique known as a DLL side-loading injection attack to take advantage of the way Windows applications behave when loading dynamic-link library (DLL) files. This attack takes advantage of applications that do not explicitly define the specific location from which a DLL should be loaded.
The attack involves the placement of a malicious DLL file in a directory where the targeted application searches for DLLs during the loading phase. When the application is initiated, it inadvertently loads the malicious DLL file instead of the intended one, thereby providing the attacker with control over the application’s execution and potential unauthorised access to the system.
HTTP Packet Capture:
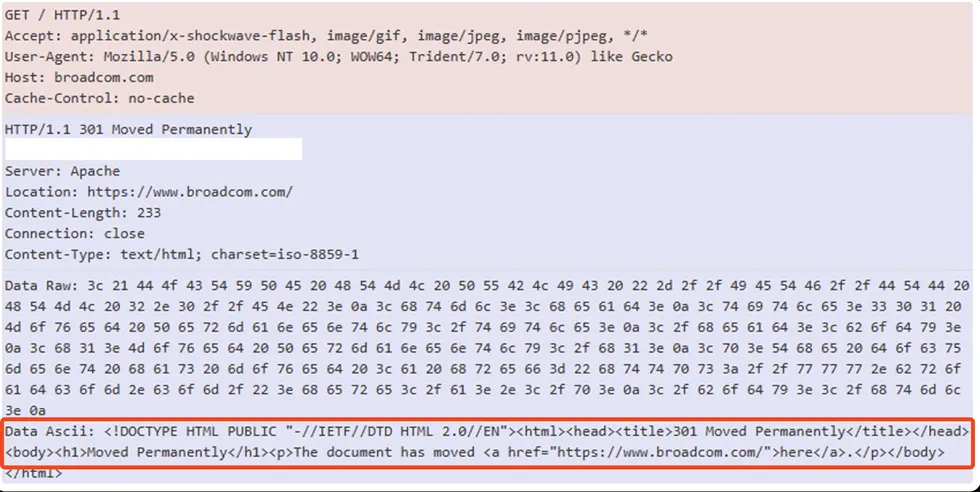
Indicator of Compromise for Qbot
In the AV results, it shows the submitted URL is malicious and it’s downloading Qbot payload malware with DLL Side loading injection attack.
Overall, Qbot should not be taken lightly, since it is a one-of-a-kind dangerous botnet and infostealer due to its tenacity, spreading mechanism, financial focus, evasion techniques, and long-standing presence throughout the threat landscape. To protect against such ‘complex’ threats, individuals and organisations must focus on resilience, maintain their systems and software up to date, and employ effective cyber security measures such as the ones offered by LMNTRIX.
MITRE ATT&CK Tactics & Techniques for Qbot,
| ID | Tactic | Technique |
| TA0001 | Initial Access | Phishing Attachment External Remote Services |
| TA0002 | Execution | Windows Scripting – .JS (or) .PDF Exploitation for client Execution |
| TA0003 | Persistence | DLL Side Loading |
| TA0004 | Privilege Escalation | Scheduled Task / Job DLL Side Loading |
| TA0005 TA0006 TA0007 | Defense Evasion Credential Access Discovery | Modify Registry Masquerading Process Injection Rundll32 Virtualization and Sandbox Evasion Technique Obfuscated file or Information Credential API Hooking LSASS Memory Input Capture System Software Discovery Process Discovery File and Directory Discovery Query Registry |
| TA0008 | Lateral Movement | Remote file copy |
| TA0009 | Collection | Credential API Hooking Archive Collected Data Data from Local System |
| TA0011 | C&C Server | Encrypted Channels Non Standard Ports Web Protocols – Standard Application Layer Protocol Ingress Tool Transfer |


