Quasar RAT (aka: CinaRAT, Yggdrasil) is a well-known open-source remote access trojan (RAT) that has been widely spread in the wild which is developed using the C# programming language and also as per the records, it is used by a wide range of hacking groups including APT33, APT10, Dropping Elephant, Stone Panda, and The Gorgon Group. It has the capabilities include capturing screenshots, recording webcam, reverse proxy, editing registry, spying on the user’s actions, keylogging and stealing passwords.
Features of Quasar RAT
Quasar RAT being a versatile tool that gives threat actors a variety of options.
Some of the essential characteristics of Quasar RAT include;
Remote control: Quasar RAT allows threat actors to take full control of a victim’s computer from a distance, allowing them full access to all of the computer’s files and system preferences.
Keylogging: This function enables threat actors to keep track of all keystrokes typed on the infected computer, even those containing passwords and other private/confidential data.
File management: The Quasar RAT gives threat actors access to the machine’s infected files so they may upload, download, and delete files at will.
Screenshots: The ability to capture screenshots of the victim’s desktop gives attackers a visual picture of what the victim is doing on their computer immediately.
Remote Command Execution: Quasar RAT gives threat actors access to the machine that has been infected, enabling them to take control of a variety of privileged system operations.
Target – Windows Platform.
Infection Vector – Malspam campaign of phishing emails.
Infection Chain
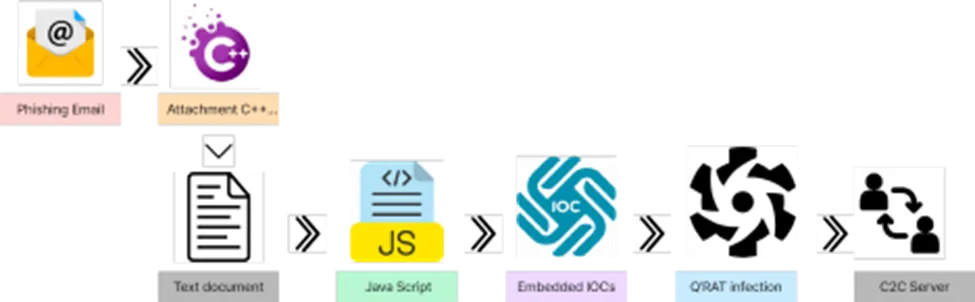
LMNTRIX CDC has observed numerous ways of spreading the Quasar RAT used commonly by threat actors;
Malicious Email Attachments: A common method employed by threat actors is attachment – a Quasar RAT-infected file is transmitted through an email sent out to potential victims.
Links that are dangerous: A threat actor may include a link to websites that host the Quasar RAT. The malware gets downloaded into the victim’s computer when they click the link.
Drive-by downloads: This technique involves Quasar RAT infecting a trustworthy website. The malware is downloaded into the victim’s computer without any action being required, the file gets dropped on to their computer without alerting the victim when they visit the website.
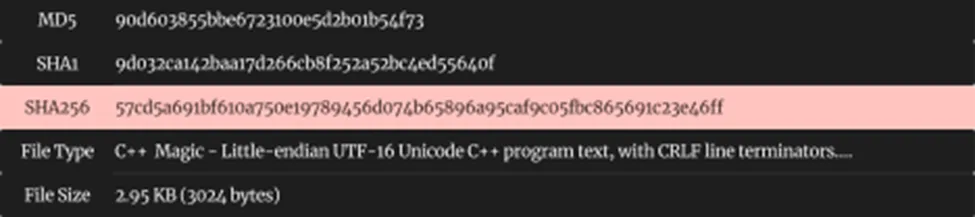
Sample Information
Threat Name: Quasar RAT | Category: Downloader | Classification: Backdoor
Technical Analysis of C++ Quasar RAT
A C++ file is a source code file written in the C++ programming language, which is a general purpose programming language used for developing a wide range of applications, including operating systems, device drivers, video games, and high-performance software.
C++ code can be written using a simple text editor or an Integrated Development Environment (IDE) such as Visual Studio, Eclipse, or Code::Blocks. Once the code is written and compiled, the resulting executable file can be run on a computer to perform the desired task.
Let’s begin with the sample analysis. Here’s the main content of the .cpp file where the file is embedded with a script file.
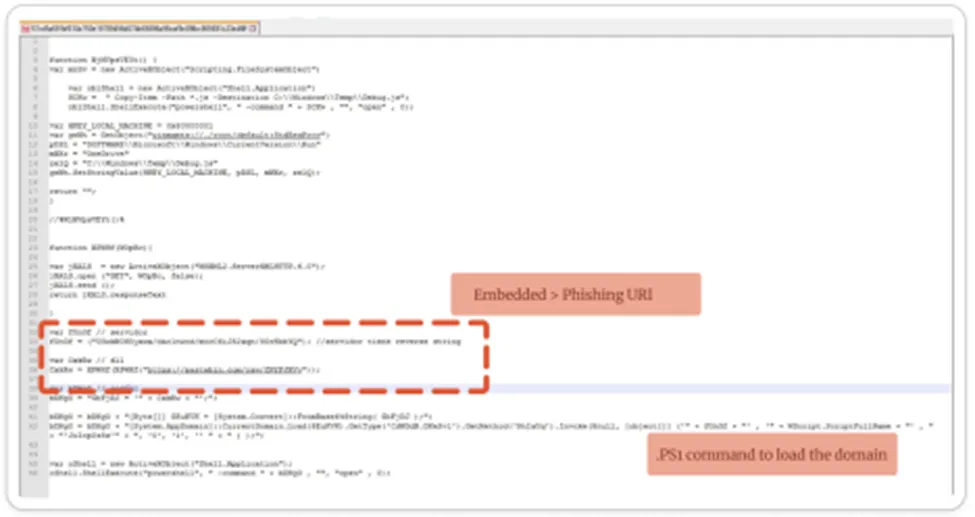
At the 36th line, there’s a declared variable of .DLL with the pastebin URI, and it’s connecting to a phishing site.
Also, the children files are dropped in the C:\windows\temp\xxxx.js folder and then it will execute the powershell in the background to connect to another phishing site to download the Payload file.
Dropped Files
Let’s analyze the dropped files in the temp folder.
Any program or any application may function as intended, but executing it may create malware in the form of a temporary file. Temp folder is typically used as a staging point once the malware installer is attached to or embedding in legitimate programs and applications. Also, the malware itself has the escalated privileges.
Embedded Content [.JS]
Decoded Content
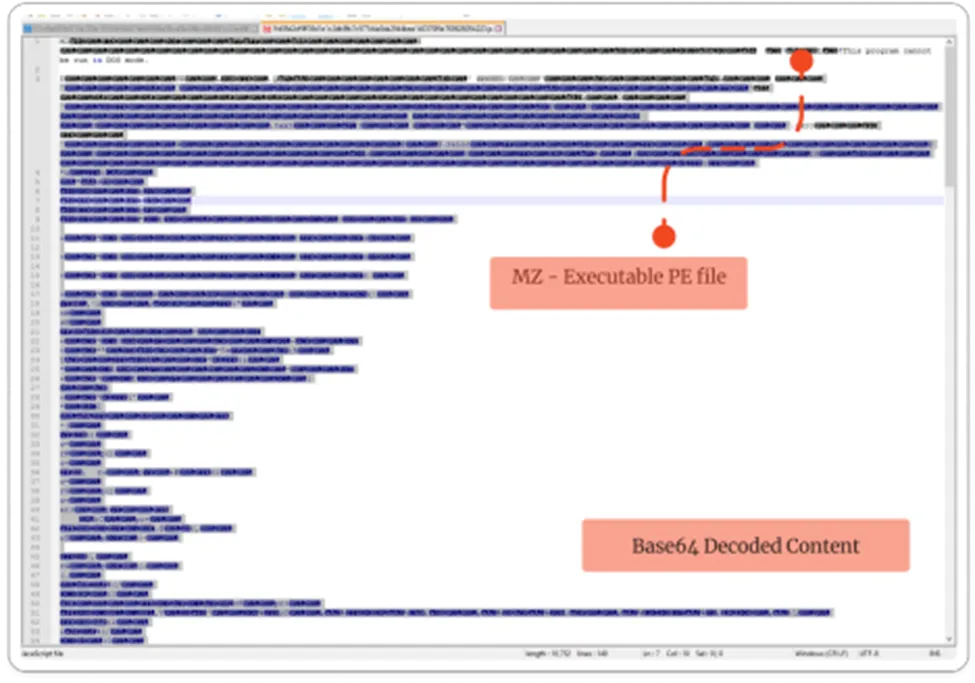
After decoding the script file, you will get the payload file. Actually, it’s a MSIL – .NET compiled file, which will perform further malicious action.
Why are the threat actors using .NET compiled files?
.NET framework is a built-in component of Windows, includes components that enable developers to compile and execute C# source code during runtime. This allows programs to update or load modules without having to restart. But now-a-days the .NET framework is originally intended to help cyber criminals have found a way to abuse its features to compile and execute malware in the wild.
Connected C2 Servers for Quasar RAT sample
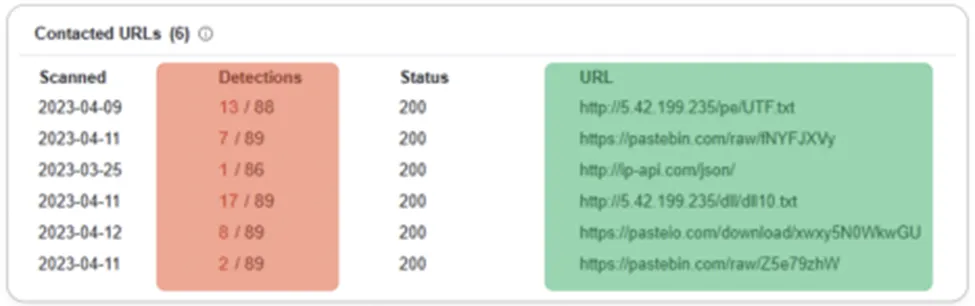
Initial – Indicator of Compromise for Quasar RAT sample
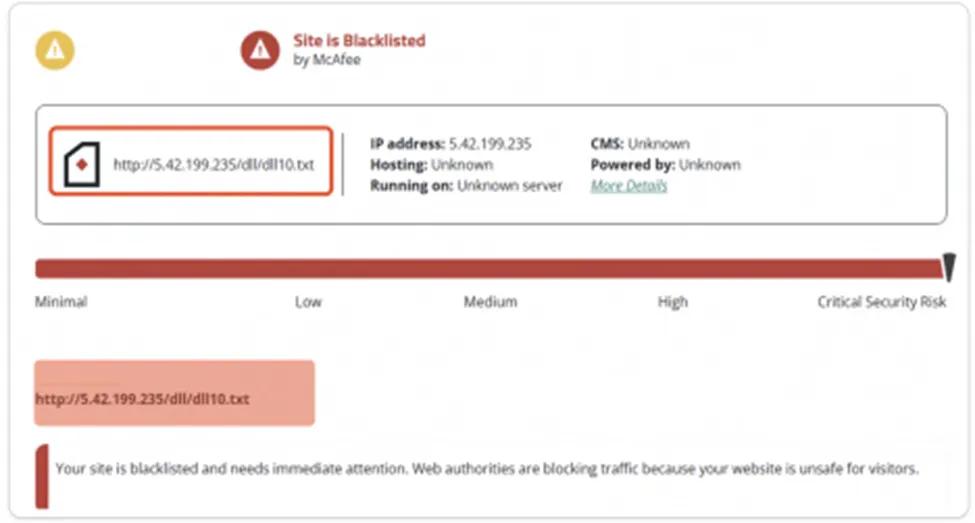
This is the one of the Indicators (IOC), found during our Quasar RAT analysis. This URL is tagged under Security Risk and it’s a phishing URL. Upon this, it will download the payload file in the concern path. As it’s a remote access trojan, they will simply take the victims’ machines and capture their activity without their knowledge.
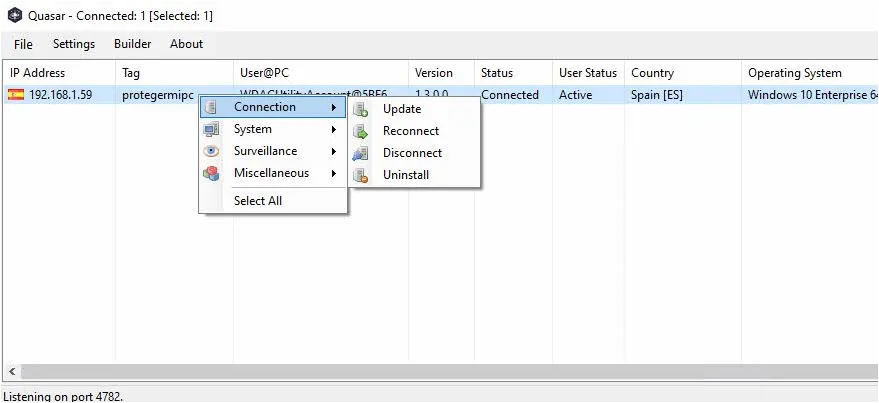
Once the Quasar RAT is infected, the following actions can be performed by a threat actor;
Task and file management like File download, upload, and retrieval.
Closing connections and terminating processes.
Building and configuring client executable.
Encrypting and compressing communications post infection.
Running computer commands on the remote system.
Recording the webcam and/or taking screenshots of the desktop.
Editing the system registry, and using reverse proxy functionality.
Stealing passwords & logging keystrokes for monetary gain.
Monitoring user activity for identity theft, lateral movement or further criminal actions.
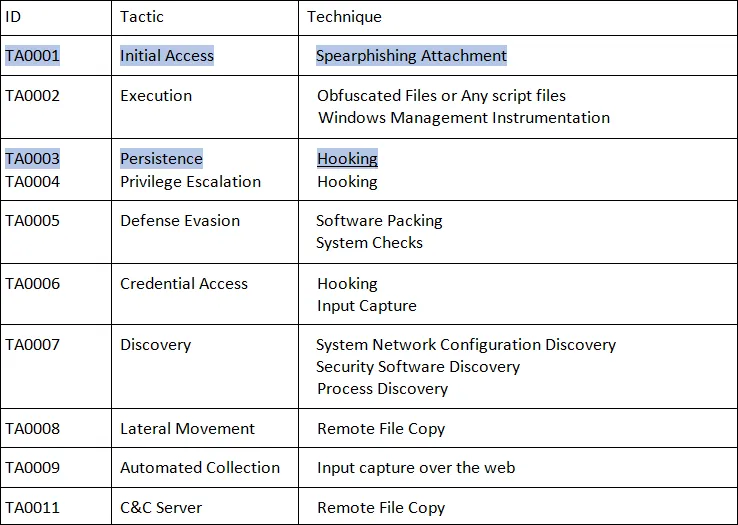
MITRE ATT&CK Matrix for Quasar RAT,