Snake Keylogger is a specific type of malware that operates as a modular program developed using the .NET platform. It was initially detected in November 2020 and is known for its ability to steal credentials, extract clipboard data, and gather various types of information. Both individuals and organizations are potential targets for Snake Keylogger, which can be obtained from illicit marketplaces like hacking forums.
A keylogger is a malicious program designed to record keystrokes, capturing every key pressed on a keyboard. This means that if your device is infected with a keylogger, it can log sensitive information such as passwords, text conversations, and payment details—essentially anything typed via the keyboard.
Interesting features of the Snake Keylogger:
- Accessing Clipboard Data: To avoid typing complex passwords, people frequently copy-paste passwords and other authentication information. Snake Keylogger may search the clipboard for passwords and other confidential data, exfiltrating the same for further cyber criminal activity.
- Stealth and Persistence: The Snake keylogger is renowned for its ability to operate covertly on compromised machines for extended periods of time. It conceals itself using cutting-edge methods, making it challenging for conventional antivirus and security products to find and get rid of it.
- Advanced Backdoor Functionality: By acting as a backdoor, the software grants attackers remote access to infected systems. This gives the attackers the ability to exfiltrate private data, upload new malicious payloads, and keep hold of the targeted infrastructure for an extended period of time.
- Targeted Espionage: The main usage of Snake is for espionage. It is intended to steal confidential information, intellectual property, and sensitive data from its targets. The stolen information is then utilized for cyberespionage or intelligence collection, or it might even be sold on the dark web.
- Modular Design: The malware’s modular construction enables attackers to modify its features to suit their own requirements. It is more difficult for security experts to accurately assess and detect it due to its versatility.
- Spear Phishing: Snake uses a variety of clever tactics to spread and keep its presence present on infected computers. To infect new targets and keep persistence within the network, it combines spear-phishing tactics, watering hole assaults, and exploits.
- Connections to Advanced Threat Actors: The Turla organization, which is believed to be connected to Russian state-sponsored cyber operations, has been linked to the Snake keylogger malware. However, because different deception techniques are employed, it can be difficult to link particular perpetrators responsible for cyberattacks.
Infection Chain
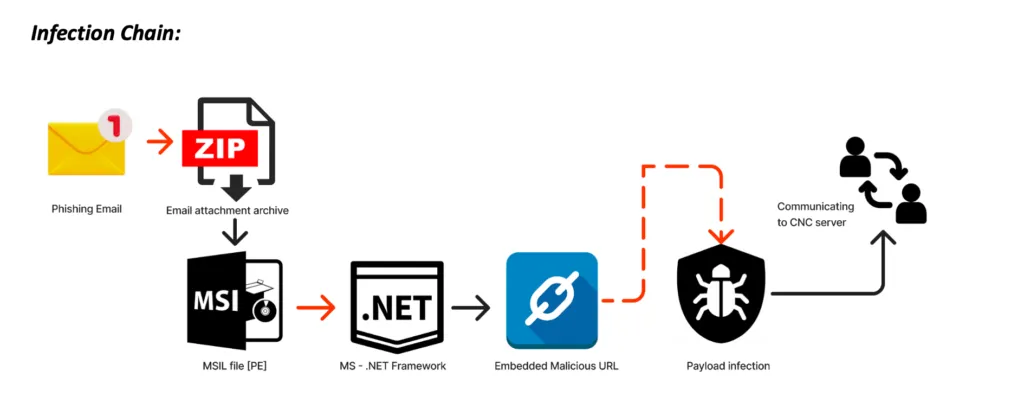
Target – MS Windows Platform
Infection Vector – Malspam campaign of phishing emails.
Sample Information
Threat Name: Snake Keylogger | Classification: Spyware
Technical Analysis of MSIL Campaign
First of all MSIL is a low-level, platform-independent representation of .NET code. When you compile a .NET application, the source code is typically compiled into an intermediate language called MSIL. Also, it enables cross-language interoperability within the .NET ecosystem. As long as a language can compile down to MSIL, it can seamlessly interact with other .NET languages. This promotes code reuse and flexibility in development across multiple platforms.

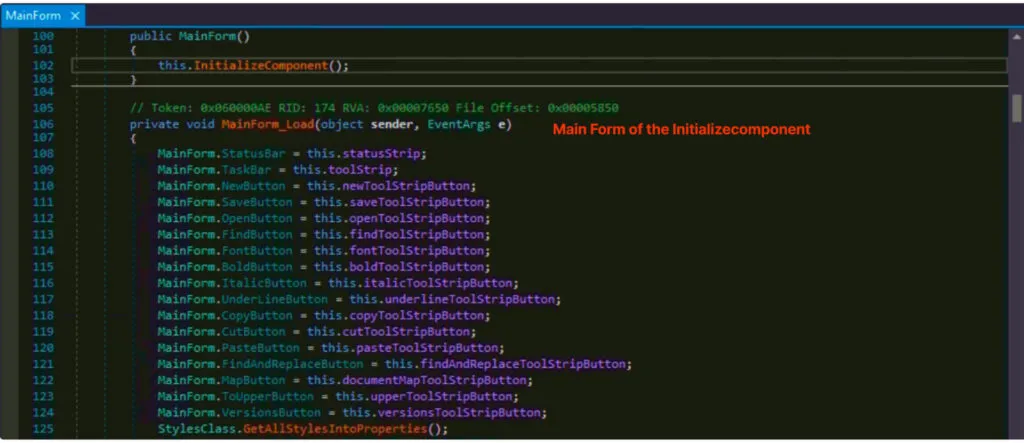
InitializeComponent()
The InitializeComponent method is commonly encountered in Windows Forms applications developed using the .NET framework. It is automatically generated by the Windows Forms designer when you create or modify a form using Visual Studio.
In MSIL (Microsoft Intermediate Language) files, the InitializeComponent method is represented as a sequence of instructions that handle the initialization and configuration of the form’s visual elements and properties. Its primary purpose is to create and position controls, define their properties, and establish event handlers.
Obfuscated strings can be particularly useful when dealing with sensitive information like passwords, API keys, or other confidential data embedded within the code.
Message Box Window
It is a standard dialog box that displays a message to the user and typically provides buttons for the user to choose from, such as OK, Cancel, Yes, or No.
Using this common feature, the malware author embedded the malicious URL to download the payload file into the victim machines.
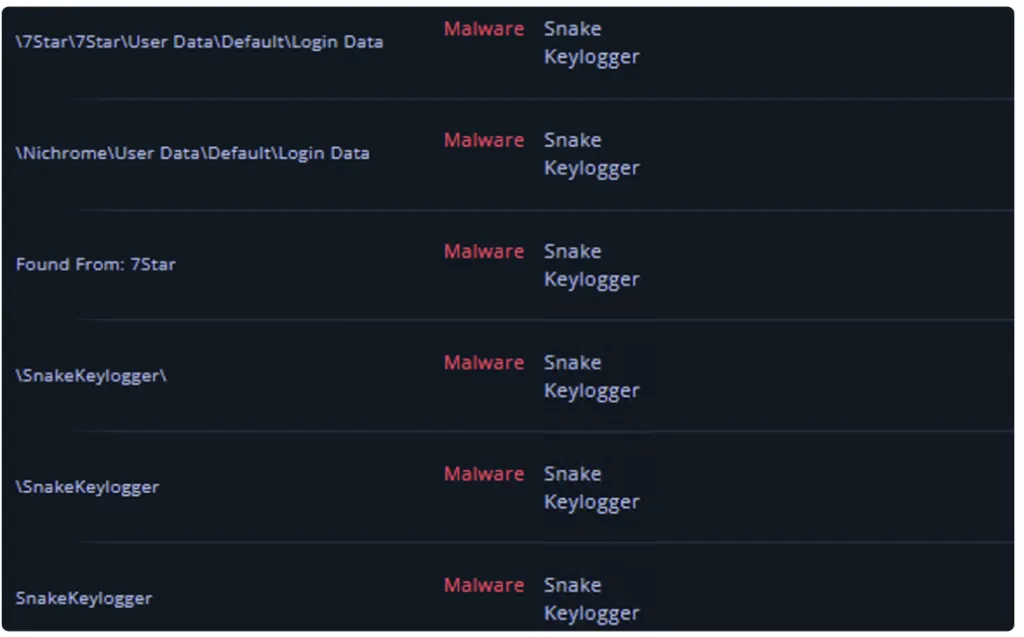
Malicious Library Functions:
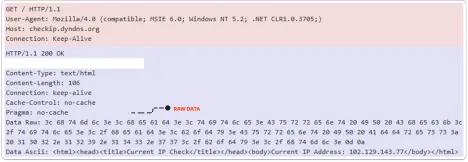
Captured RAW Data Packets:
MITRE ATT&CK Tactics & Techniques for Snake Keylogger,
| ID | Tactic | Technique |
| TA0001 | Initial Access | Spearphishing Attachment |
| TA0002 | Execution | Windows Scripting – .NET compiled Framework Scheduled Task |
| TA0003 | Persistence | Registry Run Keys / Startup Folder |
| TA0004 | Privilege Escalation | Process Injection Scheduled Task / Job |
| TA0005 | Defense Evasion | Masquerading Modify Registry Virtualization and Sandbox Evasion Technique Disable or Modify Tools |
| TA0006 | Credential Access | OS Credential Dumping LSASS Memory Input Capture |
| TA0007 | Discovery | System Software Discovery Process Discovery File and Directory Discovery Query Registry |


