
Incident Response (IR) Service is a service offered by many cyber security companies. The service is built on the promise to provide organisations with a security company on standby to assist in the event of a grave security incident or a massive breach. While this may initially seem like a prudent & precautionary measure, it’s time to explore the truth behind IR retainers and whether they really provide value or if they are simply a waste of money for many organisations.
A False Sense of Security
One of the primary arguments in favor of IR retainers is that they offer peace of mind by having a dedicated team of experts ready to respond to an incident swiftly. However, this may create a false sense of security. Many organisations already possess robust Security Operations Centers (SOCs). These typically include the necessary capabilities for malware analysis, incident response, and forensics. The frequency of investigations conducted by these enterprise SOCs is often a testament to their adeptness at detecting and monitoring potential threats.
A lack of regular investigations might indicate that an organisation’s security posture is not as strong as it should be. In such cases, investing in an IR retainer might not address the root cause of the problem and may only serve as a band-aid solution.
The Redundancy of Managed Detection and Response (MDR) or MSSP Services
For organisations that have already invested in Managed Detection and Response (MDR) or Managed Security Services Provider (MSSP) services, an IR retainer can be a redundant cost. Reputable MDR or MSSP providers should already include the necessary incident response capabilities as part of their service offering. If they do not, it might be a sign to reevaluate the effectiveness of the current cyber security provider.
Paying for the Intangible Threats
One of the major drawbacks of IR retainers is the cost involved, more so if their services are determined to be redundant. The hefty fees charged by these services can quickly add up, even if an incident never occurs. Organizations may find themselves paying thousands of dollars monthly for a service they might not utilize. This financial strain can be particularly burdensome for smaller businesses and may not be a cost-effective approach to handling cyber security.
A Tailored Approach to Incident Response
Every organization’s security needs are unique, and a one-size-fits-all approach is often insufficient to address specific threats effectively. IR retainers often adopt a generic approach, which might not cater to the intricacies of an organization’s IT infrastructure and security protocols. In some cases, IR teams arrive on-site to discover insufficient logs or incompatible systems, leading to delayed response times and potential damages. A more prudent approach would be, collaborating with a cyber security provider to develop a customized incident response plan tailored to an organization’s specific needs and risks. This tailored approach ensures that the organization is better prepared to handle any potential incidents with greater efficiency and effectiveness.
Preventive, Detective or Reactive?
While having a cyber security firm on standby for incident response is undoubtedly valuable, it should not overshadow the importance of prevention. Proactive security measures, including robust security controls, regular security assessments, and vulnerability testing, form the foundation of a strong security posture. Organisations should prioritise prevention over reaction, as preventing a breach or incident in the first place is significantly more cost-effective and less damaging to an organisation’s reputation.
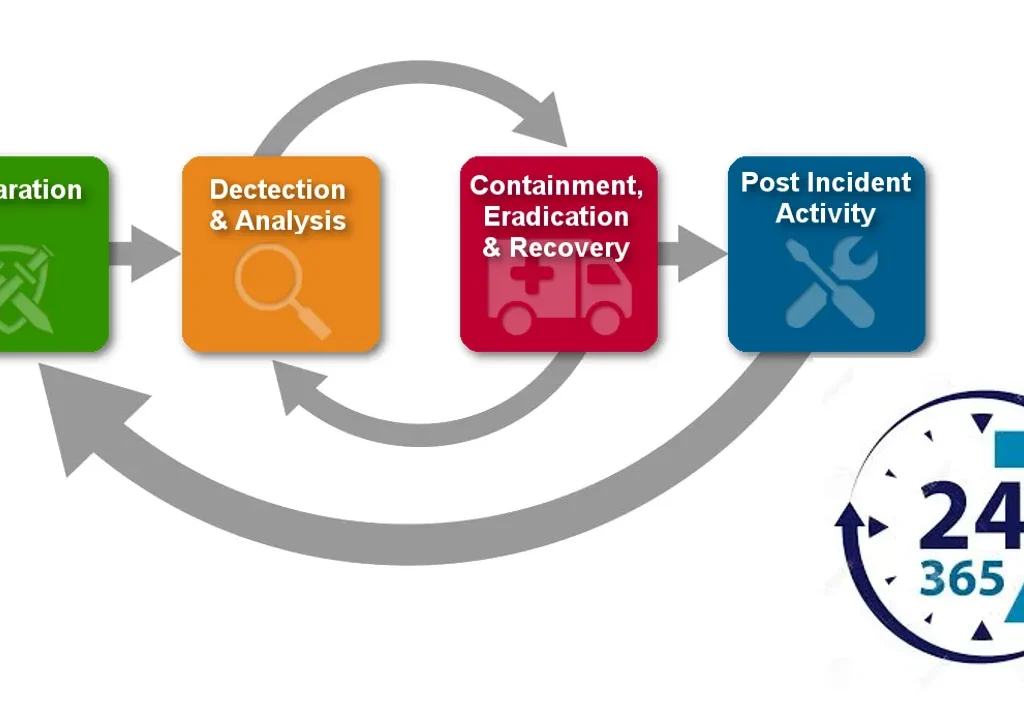
The Human Factor in Incident Response
Another critical aspect to consider is the human factor in incident response. While cyber security firms can provide expertise and technical support, the organization’s internal team plays a vital role during an incident. IR retainers might not adequately address the need for internal training, awareness, and preparedness. Empowering internal teams with the right knowledge and tools can lead to faster detection, containment, and recovery during an incident.
Post-Incident Analysis and its role in a Security Incident
Incident response does not end with containing and mitigating an incident. Proper post-incident analysis is essential to identify weaknesses in the organization’s security posture and to implement necessary improvements. While IR retainers might provide incident response support, they might not offer the same level of attention and dedication to post-incident analysis as a specialized cyber security provider. Organizations should seek comprehensive incident response services that include thorough post-incident analysis to strengthen their defenses for the future.
The Role of Contextual Threat Intelligence
Effective incident response relies on accurate and timely threat intelligence. A well-informed cyber security team can better anticipate potential threats, identify emerging attack patterns, and respond proactively. While some IR retainers may offer access to threat intelligence, it might not be as comprehensive or up-to-date as what specialized cyber security providers can deliver. By partnering threat intelligence specialists, organizations can benefit from real-time insights into the evolving threat landscape. This intelligence can be integrated into an organization’s incident response plan, enabling a faster and more targeted response when faced with a security incident.
Building Strong Partnerships for Resilience
Rather than solely relying on IR retainers, organizations should aim to build strong partnerships with cyber security providers. Establishing a long-term relationship with a trusted cyber security partner can yield more significant benefits than a one-time IR retainer. A dedicated cyber security partner can gain a deeper understanding of an organization’s unique security challenges, internal systems, and risk profile. This enables them to provide more personalized and effective incident response and mitigation strategies.
Continual Improvement and Preparedness
The world of cyber security is constantly evolving, and threats are becoming increasingly sophisticated. As such, organizations must view incident response as an ongoing process of continual improvement and preparedness. A proactive approach involves regular incident response drills, simulations, and table-top exercises to test the organization’s readiness and identify areas for improvement.
Conclusion
In conclusion, while the concept of Incident Response (IR) Retainers may initially seem like a prudent investment in cyber security, it becomes clear that they can be a wasteful expense for many organizations. Most enterprise SOCs already possess the necessary capabilities to conduct investigations, and organizations using MDR or MSSP services might find redundant coverage in an IR retainer.
A more effective approach involves focusing on prevention; developing a tailored incident response plan; empowering internal teams; conducting thorough post-incident analysis; and integrating real-time threat intelligence. By adopting proactive security measures, organizations can build a robust security posture that minimizes the likelihood of incidents and reduces the potential impact when they do occur.
Rather than relying solely on an IR retainer, organizations should invest in a comprehensive cyber security strategy that prioritizes prevention, continuous improvement, and collaboration with cyber security experts to ensure optimal protection against emerging threats. By building strong partnerships with cyber security providers fosters resilience and preparedness, making incident response an integral and well-integrated component of an organization’s cyber security defense.


