
DoNot APT Group, also known as APT-C-35, targeting government-related organisations has emerged once again with an updated version of their malware. DoNot APT team mainly spreads malware via spear-phishing emails containing malicious documents and other attachment files. Mostly the malicious programs are developed in C++, Python, .NET, and other languages.
APT-C-35, also known as the DoNot APT team is a group of advanced persistent threat actors that have been operational since 2016. They are the primary creators and users of the Windows and Android spyware frameworks. Many of their attacks have been directed against South Asian people and institutions.
Target: APT attacks against India, Pakistan, Argentina, and the countries in South Asia.
Cyber security researchers from around the globe have described DoNot Team as “very persistent” – they hammer a target for years with their TTPs, until they find a way in. While the advanced persistent threat (APT) group tends to stay within a particular geographical area – such as South Asia, the DoNot Team has also been traced to attacks against embassies in the Middle East, Latin America, North America, and Europe.
Infection Chain:
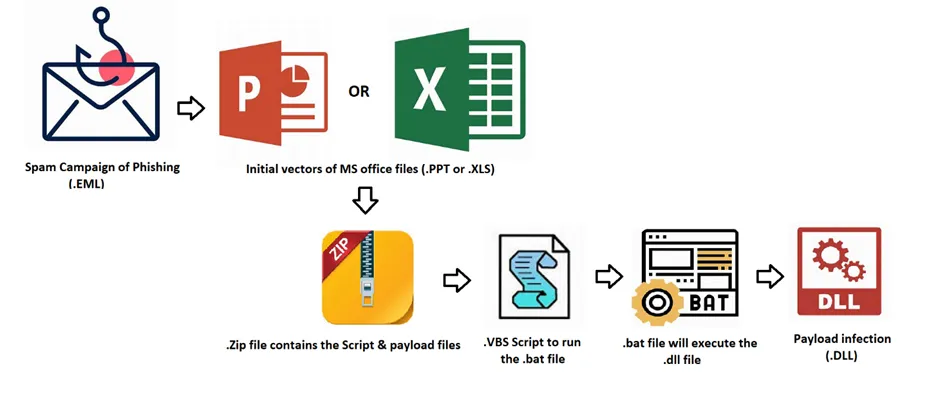
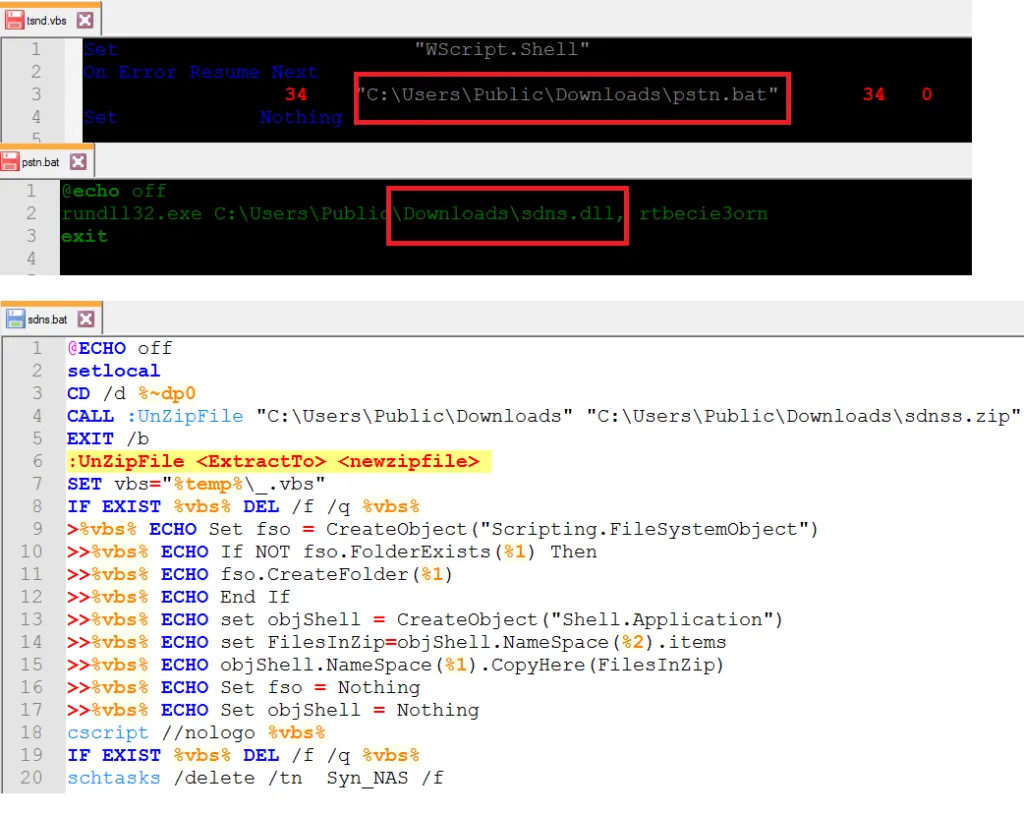
This Advanced Persistent Threat arrives as a spear-phishing email attachment. This kind of e-mail contains Microsoft Office files such as MS Word documents (.docx) or Powerpoint (.ppt) or MS Excel (.xls) attachments. This kind of attack requires the victim to enable macros, once the user opens the document, then it drops the payload in their target locations. Once dropped, the zip file will unzip with the help of .bat script and then it will run the .VBS script to run the another .BAT file to execute the .DLL file.
Sample 1: Distributed via PPT
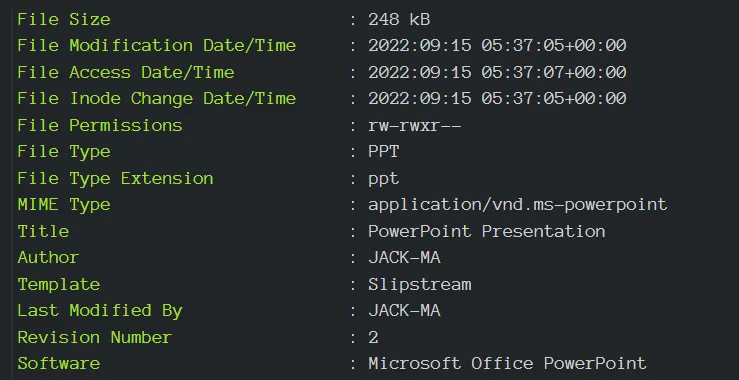
Technical Analysis of PPT:
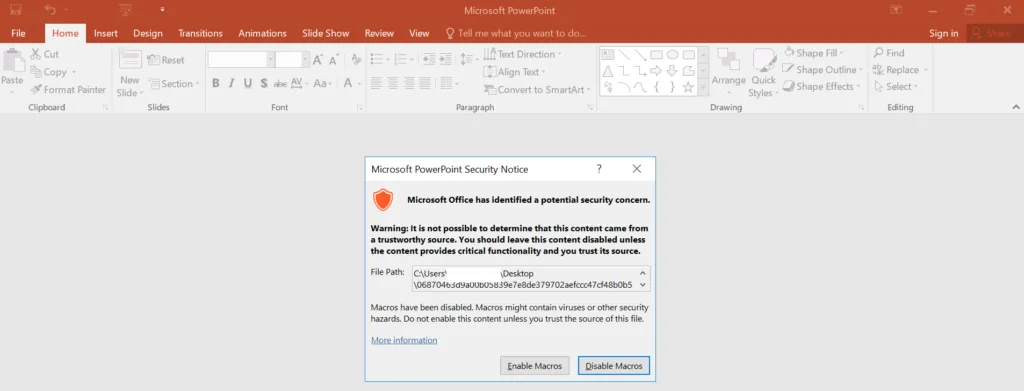
Once the user enables the macros, the payload files will drop in their targeted location. Here, they used to drop in the C: > User > Public > Downloads.
Sample 2: Distributed via XLS
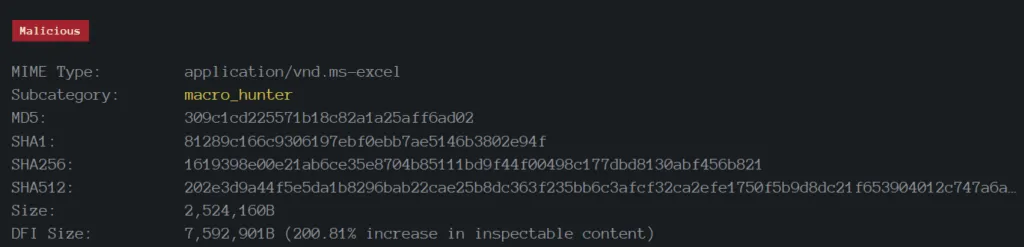
Technical Analysis of XLS Document:
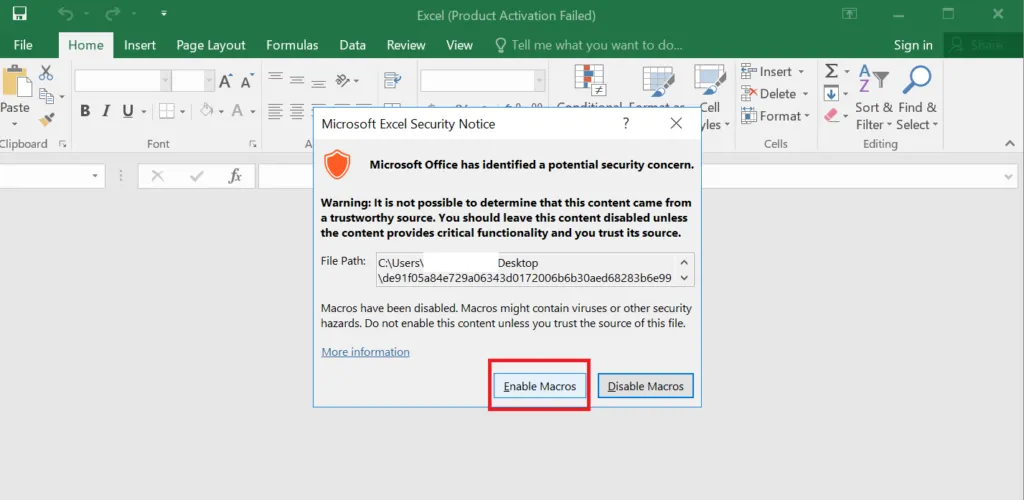
In this instance also, there is not much difference, the attackers just changed the initial vector from PPT to XLS attachment document but the same payload facilitates infection. With respect to all of the aforementioned initial vectors, once the user enables the macro function, the following actions will be performed.
Dropped Files:
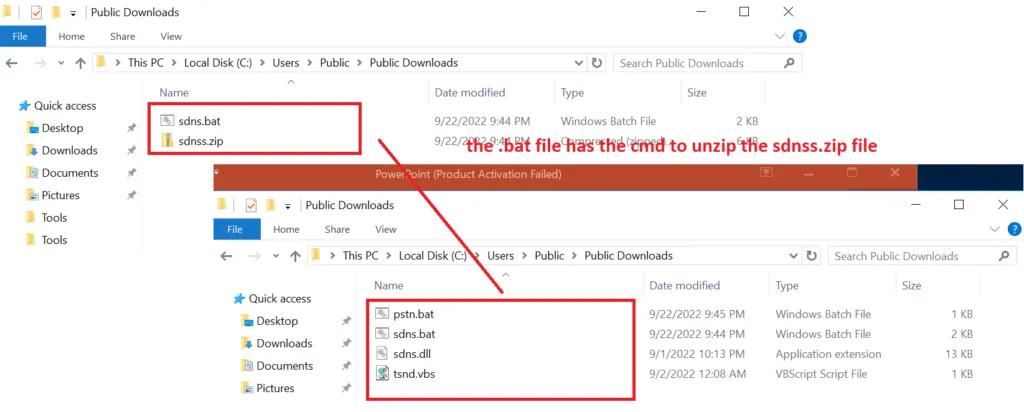
Here, we can see the ((XXXX))((.))zip file. This file will automatically unzip contents with respect to the .BAT script. When the contents are extracted successfully, there are four different files, that will be dropped in the C: > User > Public > Downloads location.
Process Tree:
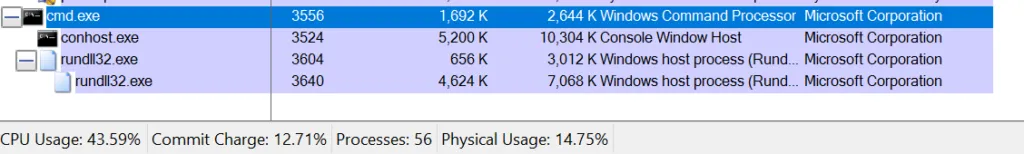
Analysis of Dropped files:
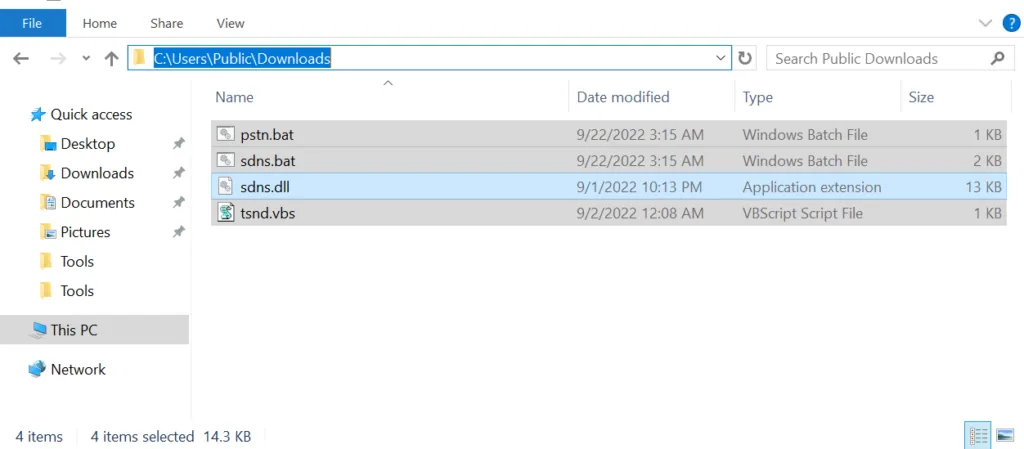
.BAT file:
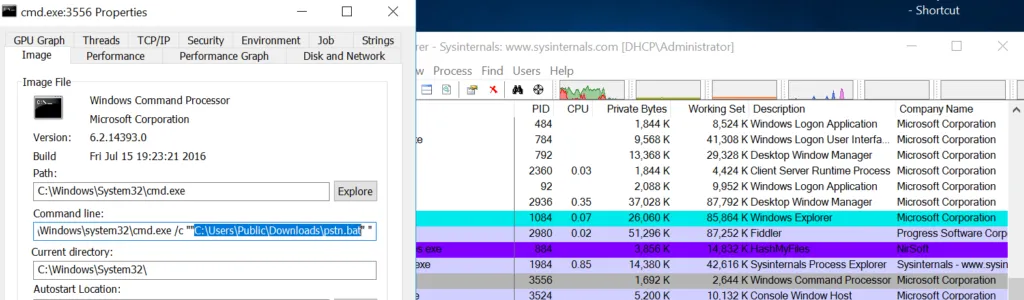
WRT .RunDLL32 > will run the payload file:
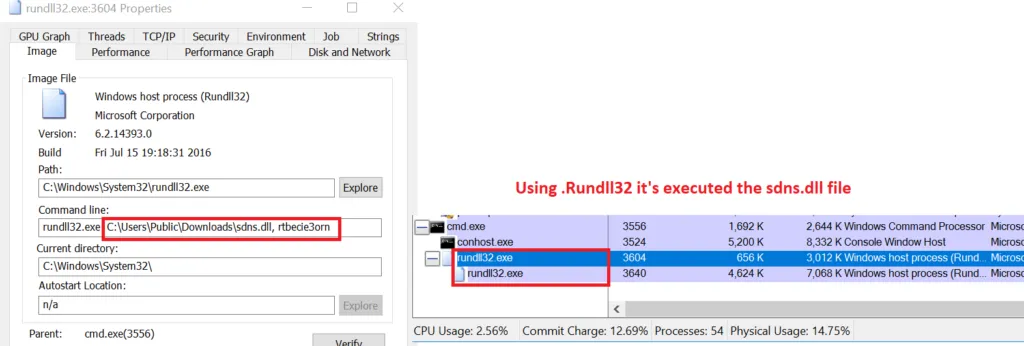
Code View of the dropped files:
YTY Malware Framework
The yty malware framework, discovered initially by Net Scout in 2018, is a less complex and poorly built successor to an older framework known as EHDevel. The yty framework is made up of a series of downloaders that together download a backdoor with very limited capability that is used to download and install further elements from the malicious toolset.
For persistence, the DoNot team’s malware employs scheduled tasks and switches between DLL and EXE files between campaign execution cycles. When it comes to DLLs, scheduled tasks run rundll32.exe to load them and run one of the exported functions.
The yty framework’s developers primarily use the C++ programming language. They have possibly ported their components in to other languages such as VBScript, Python, Visual C#, and Auto It in an attempt to avoid detection. However, at LMNTRIX CDC, we have seen them use only components written in C++ and Golang since 2019 to 2022.
Goals of the DoNot Team (APT-C35) attacks:
Primarily the DoNoT team’s browser stealer, shellcode loader and new DLL that spawns a reverse shell have the following objectives,
- Theft of Personally Identifiable Information (PII) or other sensitive data.
- Theft of intellectual property.
- Theft of classified data.
- Sabotage, for example database deletion.
- Complete site takeover.
- Obtaining data on infrastructure for reconnaissance purposes.
- Obtaining credentials to critical systems.
- Access to sensitive or incriminating communications etc.
Conclusion
As we have mentioned earlier, DoNot APT team makes up for its low sophistication with tenacity. LMNTRIX CDC expects this group will continue to push on with more attacks regardless of its many setbacks. Imagine defending against APTs such as the DoNot team, without an in-depth strategy that uses multiple layers of security for cyber defense, the impact of a persistent attacker has been documented time and again with recent breaches including Uber. There’s an old saying, Persistence is the twin sister of excellence, whether it comes to the attackers, or the cyber defenders protecting their organisation’s data.
IOC – Indicators of Compromise for Detecting DoNoT APT Malware
Hashes
2c84b325b8dc5554f216cb6a0663c8ff5d725b2f26a5e692f7b3997754c98d4d
a70038cdf5aea822d3560471151ce8f8bacd259655320dea77d48ccfa5b5af4f
d3a05cb5b4ae4454079e1b0a8615c449b01ad65c5c3ecf56b563b10a38ecfdef
d71fa80d71b2c68c521ed22ffb21a2cff12839348af6b217d9d2156adb00e550
7fc0e9c47c02835ecbbb63e209287be215656d82b868685a61201f8212d083d9
6e7b6cc2dd3ae311061fefa151dbb07d8e8a305aed00fa591d5b1cce43b9b0de
90cb497cad8537da3c02be7e8d277d29b78b53f78d13c797a9cd1e733724cf78
93ca5ec47baeb7884c05956ff52d28afe6ac49e7aba2964e0e6f2514d7942ef8
9b2ef052657350f5c67f999947cf8cd6d06a685875c31e70d7178ffb396b5b96
80f2f4b6b1f06cf8de794a8d6be7b421ec1d4aeb71d03cccfc4b3dfd1b037993
f0c1794711f3090deb2e87d8542f7c683d45dc41e4087c99ce3dca4b28a9e6f6
5ebee134afe192cdc7fc5cc9f83b8273b6f282a6a382c709f2a21d26f532b2d3
d566680ca3724ce242d009e5a46747c4336c0d3515ad11bede5fd9c95cf6b4ce
28c71461ac5cf56d4dd63ed4a6bc185a54f28b2ea677eee5251a5cdad07077b8
9761bae130d40280a495793fd639b2cb9d8c28ad7ac3a8f10546eb3d2fc3eefc
41c221c4f14a5f93039de577d0a76e918c915862986a8b9870df1c679469895c
Domains / URLs
hxxp://mak.logupdates.xyz/DWqYVVzQLc0xrqvt/HG5HlDPqsnr3HBwOKY0vKGRBE7V0sDPdZb09n7xhp0klyT5X.mp3
hxxp://mak.logupdates.xyz/DWqYVVzQLc0xrqvt/HG5HlDPqsnr3HBwOKY0vKGRBE7V0sDPdZb09n7xhp0klyT5X.doc
worldpro[.]buzz
ser.dermlogged[.]xyz
doctorstrange[.]buzz
clipboardgames[.]xyz
beetelson[.]xyz
tobaccosafe[.]xyz
kotlinn[.]xyz
fitnesscheck[.]xyz
dayspringdesk[.]xyz
srvrfontsdrive[.]xyz
globalseasurfer[.]xyz
esr.suppservices[.]xyz


