
Last week, multiple ransomware campaigns taught the world a valuable lesson: cyberthreats and the attackers behind them are constantly evolving – often at a pace victims can’t hope to keep up with.
In this blog, I’d like to take a closer look at another facet of this evolution. Increasingly, we are witnessing a trend of attackers turning their attention toward the Industrial Control (ICS) and SCADA Systems used in the manufacturing and industrial production process.
For some background to this trend, these systems have only recently emerged as a target of criminal cyber groups. The reason for this is the devices and technology of Industrial Control Systems are increasingly becoming more network-connected. These systems are becoming more connected while at the same time there is a cultural divide emerging behind the scenes between security teams. This divide stems from the tensions created when combining IT (Information Technology) and OT (Operational Technology) networks and usually involves a tug-of-war between security control and visibility.
From recent research, we have seen that ever-opportunistic cyber attackers are taking advantage of this divide.
For example, a team of LMNTRIX researchers has identified infections in Industrial Control System devices which uses a cryptocurrency Mining Trojan. As further evidence of the ongoing evolution of cyberattacks, this Mining Trojan is not looking for bitcoins (the traditional target of mining programs) but rather the newer digital currency, Monero. The below graph shows the rise and fall of digital currency mining between Monero and bitcoin.
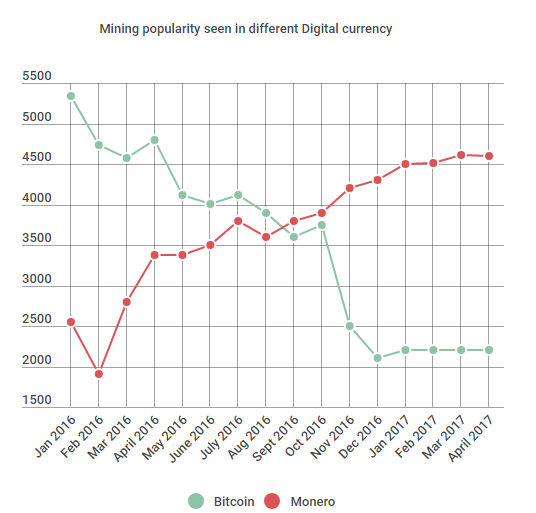
As the popularity in Monero Mining has increased, we have witnessed more and more criminals spreading a new malware payload that uses infected machines to mine coins at the expense of the victim’s CPU and GPU resources.
We have identified one such mining trojan in an ICS system on the shop floor of a European auto-manufacturer. The machine in question handles the SCADA unit of the car assembly process. Such machines are easy targets because of the legacy operating systems which they still use – this infected machine still ran Windows XP, an operating system which Microsoft has not supported since April 2014 (except for the out-of-bounds patch Microsoft recently released in a bid to close the SMB vulnerability WannaCrypt was exploiting to spread itself).
We became suspicious of the infected machine when it began to make DNS requests to multiple Monero mining pool domains. The following network information was then pooled out from the infected machine:

From the above, we confirmed that domains like mine[dot]moneropool[dot]com, xmr[dot]hashinvest[dot]net and monero[dot]crypto-pool[dot]frwere all contributing to the Mining Pool, and, in this instance, moneropool[dot]com was the major contributor.
We then found that the malware propagates through the below threat name:
Mal/Miner-C
Filename: Photo.scr
PE Imphash: 7fa974366048f9c551ef45714595665e
The malware uses this technique to spread and get new nodes to help calculate hashes for the cryptocurrency. It also attempts to copy itself to open (or weak) FTP folders in the hope of executing on their machines.
Once the Mining Trojan is executed, it drops multiple files:
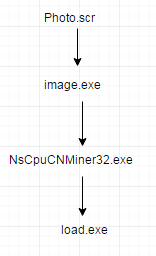
These miner files are downloaded onto the machine and are then joined to the large crypto-mining pools. From analysis of the Trojan, no ICS-related command or spoofing has been identified. We believe that this confirms that the sole intention of the Trojan is to add the machine into a large mining pool for Monero digital currency.
We suspect this new focus on the Monero crypto-currency is due to the fact it is gaining a reputation for an enhanced anonymity, a characteristic prized by cyber criminals.


