While the recent Petya (NotPetya?) pandemic made the world recognise just how devastating ransomware can be, another variant slipped largely under the radar.
This variant, dubbed ‘Karo’, may not have shut down hospitals and other critical services, but it’s still worth examining because it’s essentially a mash up of several other successful strains.
Karo uses the classic ‘phishing email, word document attachment, malicious macro’ propagation formula (we’ve covered malicious macros in more depth, so read here if you’d like more information on how it works), though it also includes a slight twist; the document is password protected.
This password protection helps the document evade security controls by allowing it to bypass many sandbox environments. The password is generally included in the body of the phishing email so the victim can open the document and enable macros.
I won’t spend too much delving into its background, instead let’s jump straight into the analysis.
Static analysis
The sample we’re analysing today is ‘svchost.exe’:
| File Name | Svchost.exe |
| File Size | 708kb |
| Md5sum | 51c7fff87a2fc5d62a31990643a5083c |
| Sha1 hash | e65ca51e8d82a5dfac95d858d0f497824e84cc1c |
Below, static analysis highlights multiple suspicious strings: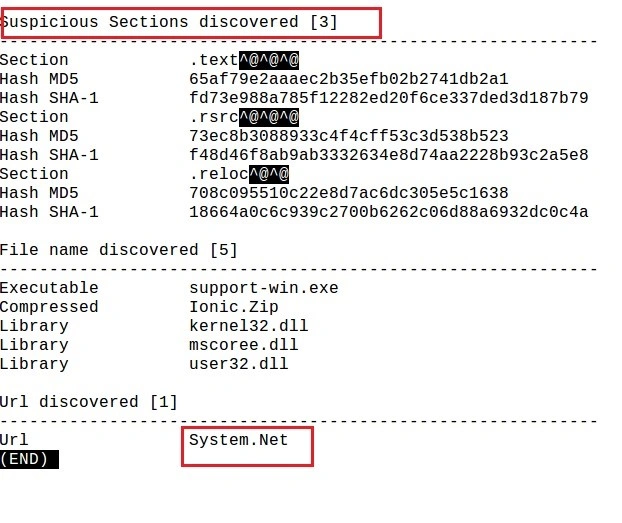
When further examined, these strings illuminate the ransomware’s specific functionality: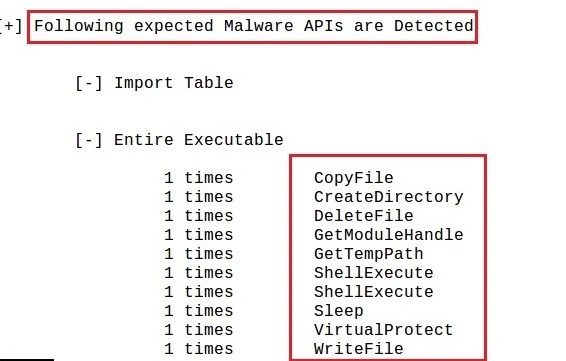
Once executed, Karo checks for the username and machine name, as well as for the %TEMP% and %appdata folders: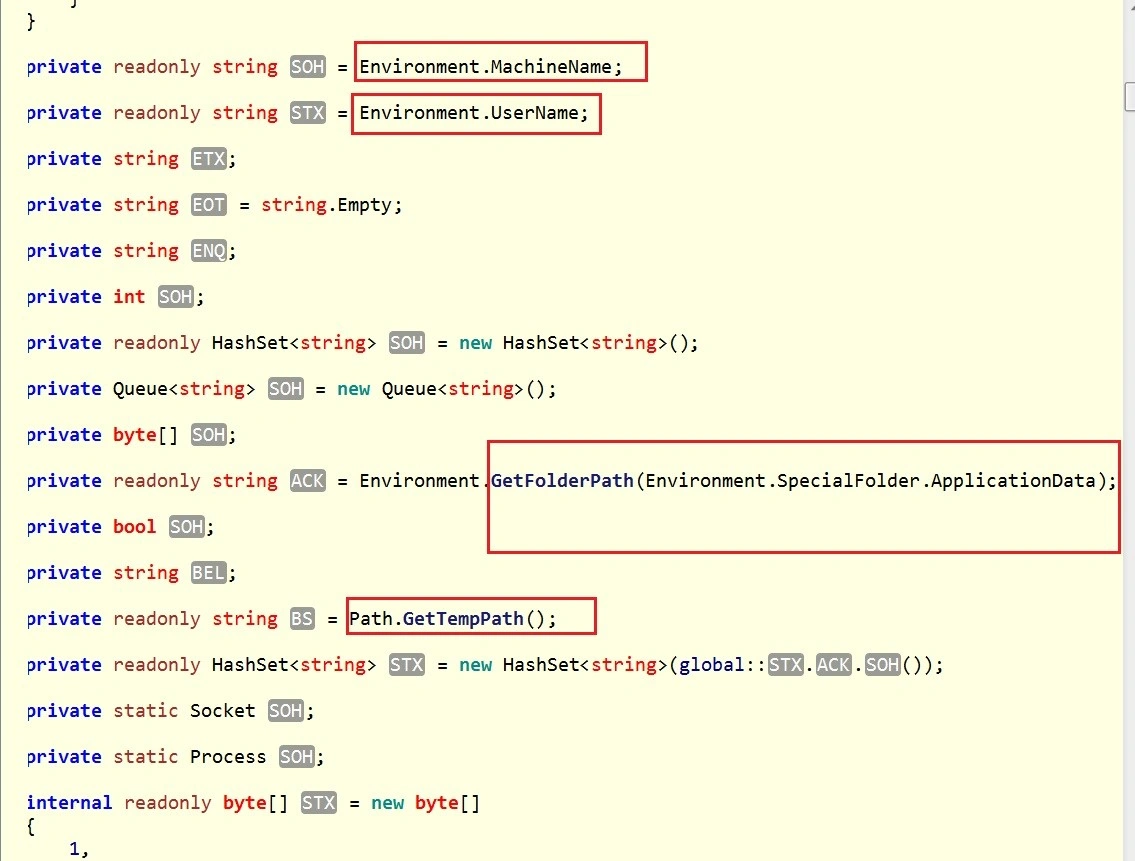
Here we see the folder’s target path: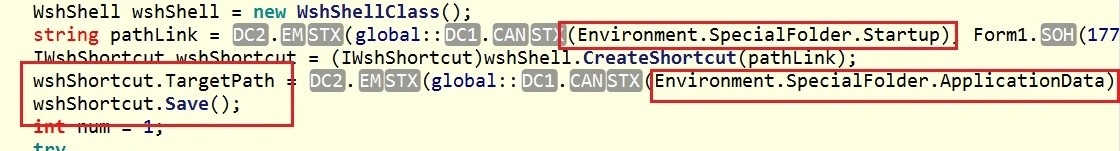
Next, Karo confirms file attributes…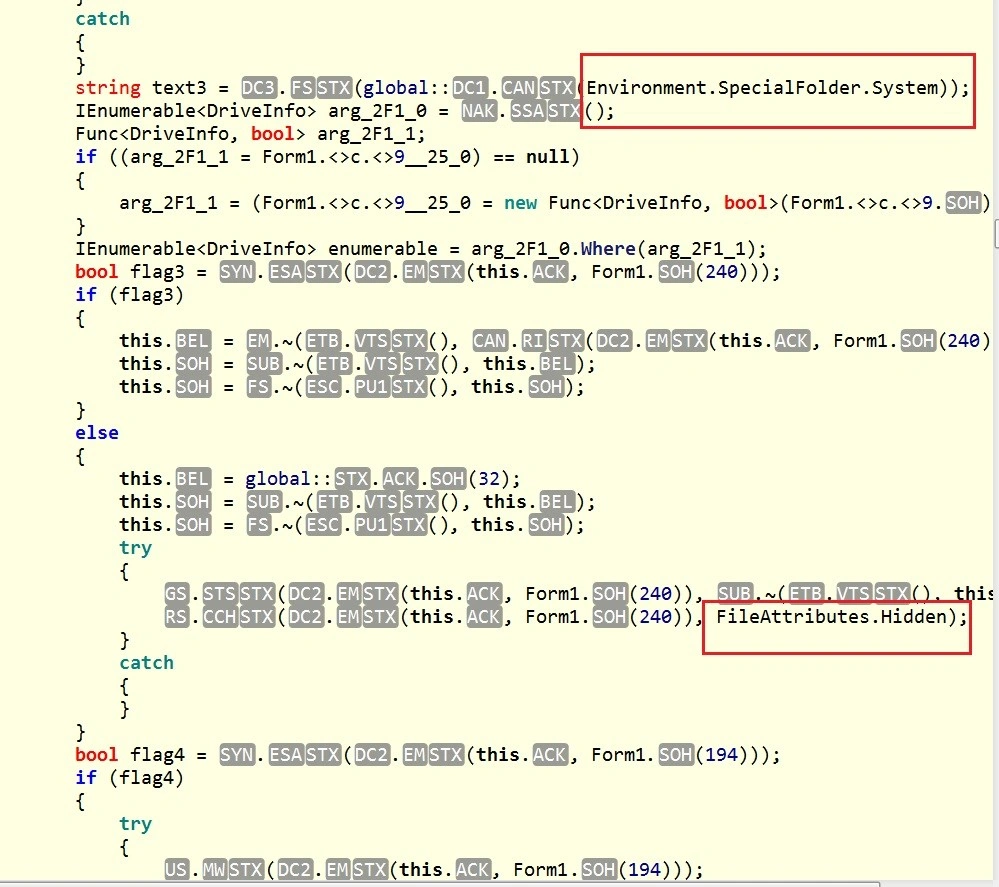
… and then it tries to retrieve process information: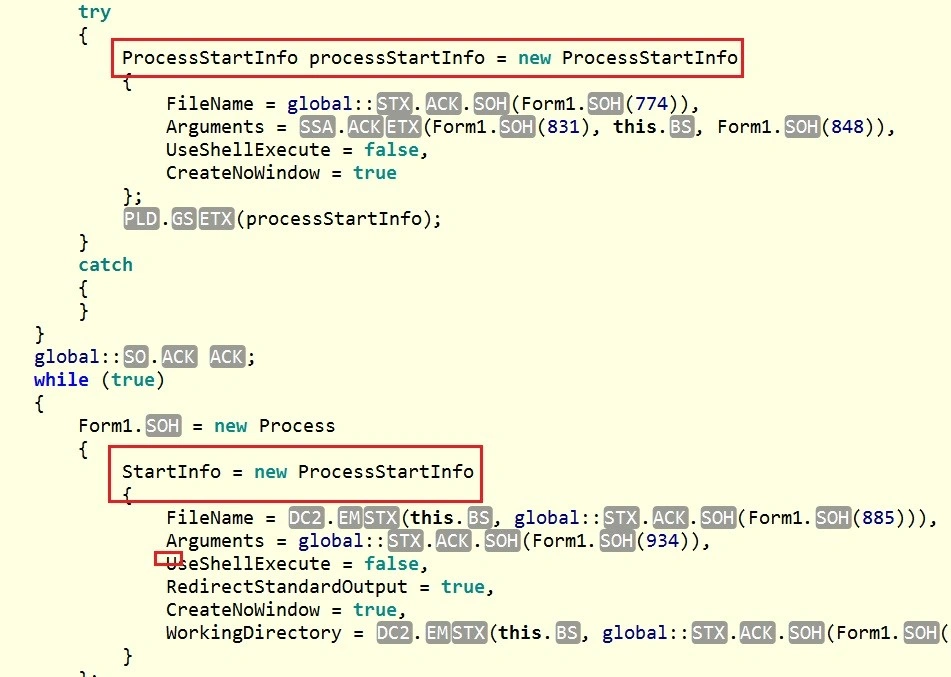
Dynamic analysis
As with all dynamic analysis, the first step is to open the malware:![]()
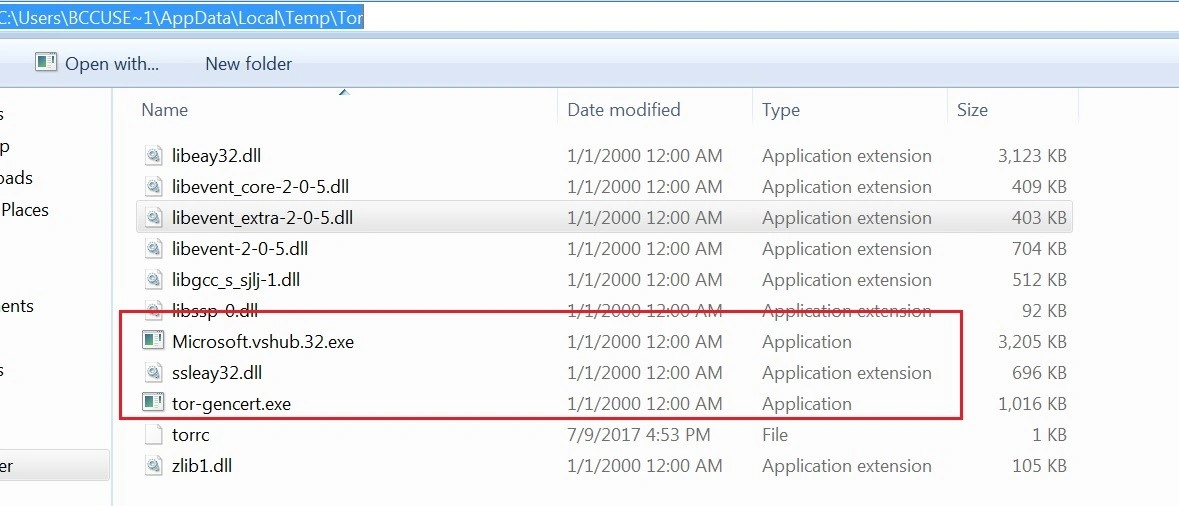
Once triggered, it contacts multiple Tor domains in order to download and execute ‘Microsoft.vshub.32.exe’:
| File Name | Microsoft.vshub.32.exe |
| File size | 3.12 MB |
| Md5sum | bc301e7d26c4ed498e9f966996fc4370 |
| Sha1 hash | dcdb0deca2ed47b78263631addea0e07af51b4da |
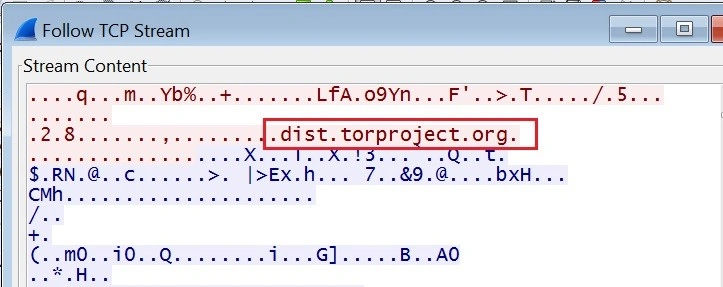
Below we see the specific Tor domains that Karo calls out to: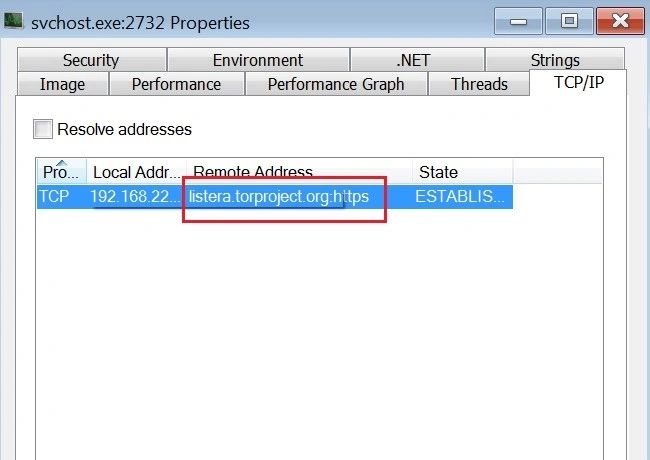
![]()
Next, microsoft.vshub.32.exe uses cmd.exe, to initiate a ping request – our sample favoured Google Chrome – to connect to several more Command and Control (C2) servers:
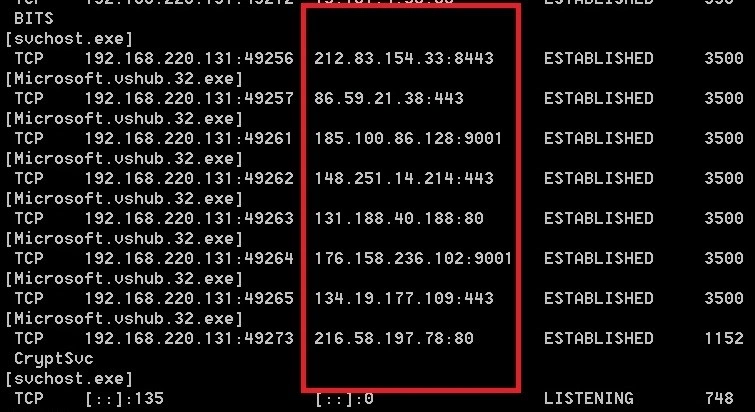
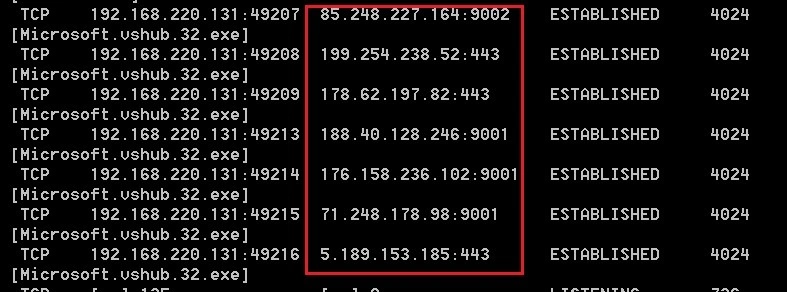
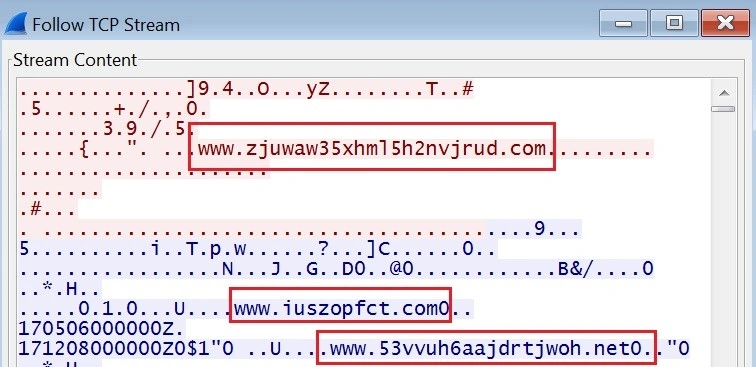
When network traffic is viewed in the pcap file, we see even more domains: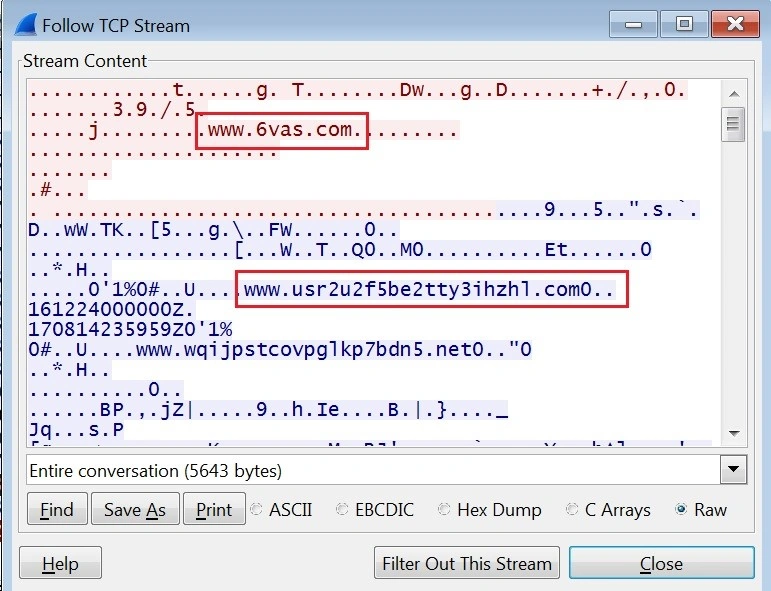
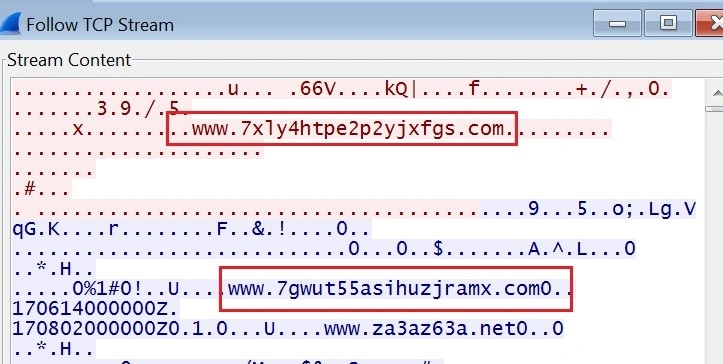
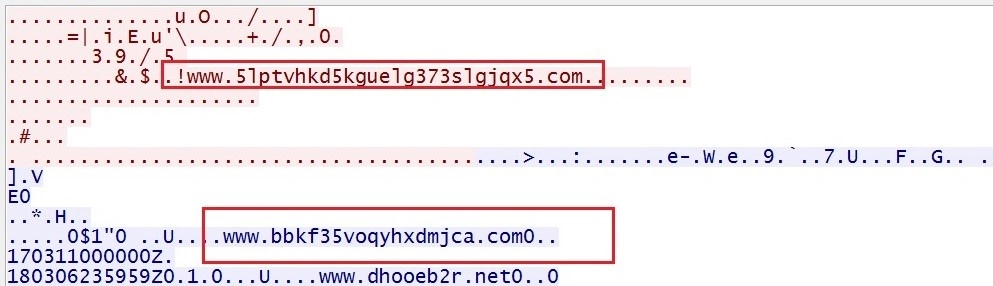
When this process is complete, the encryption starts. Our sample displayed the following ransom demand via Google Chrome: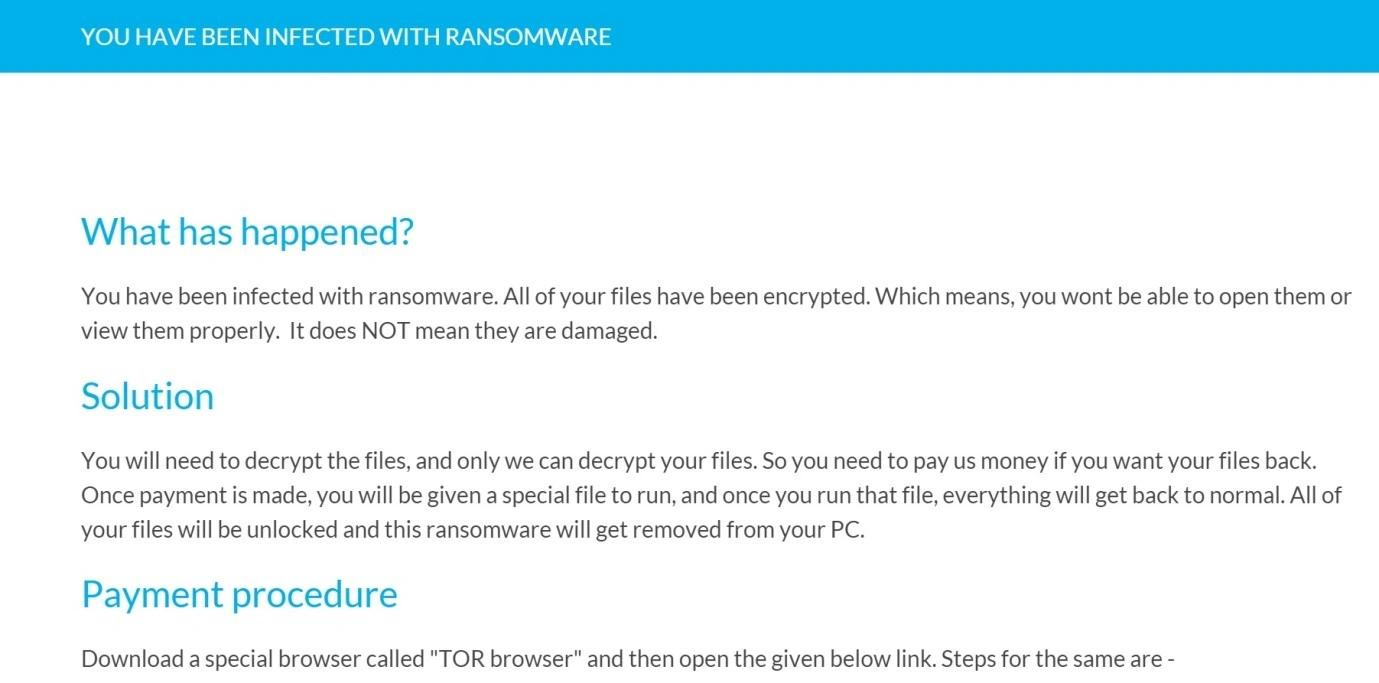
Another demand was also displayed on the machine’s desktop: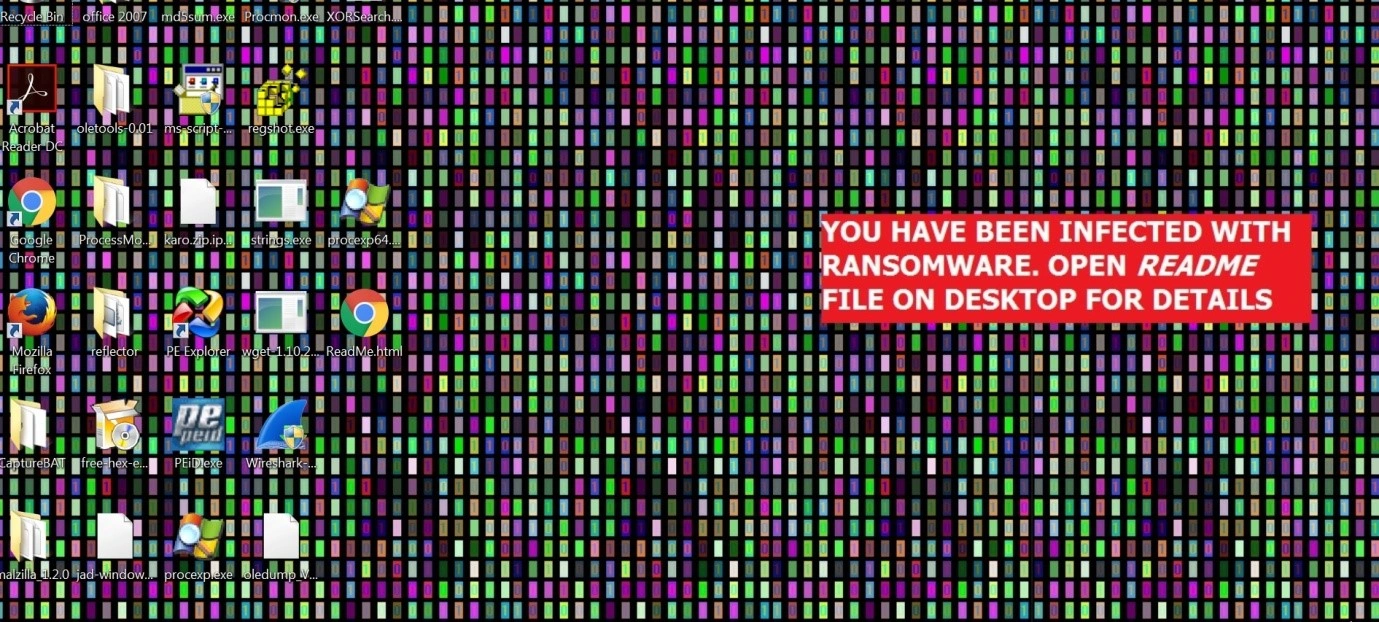
To achieve this, the following files were dropped onto the user’s system:
C:\users\<User-name>\Appdata\Local\Temp
C:\users\<User-name>\Appdata\Local\Temp\Tor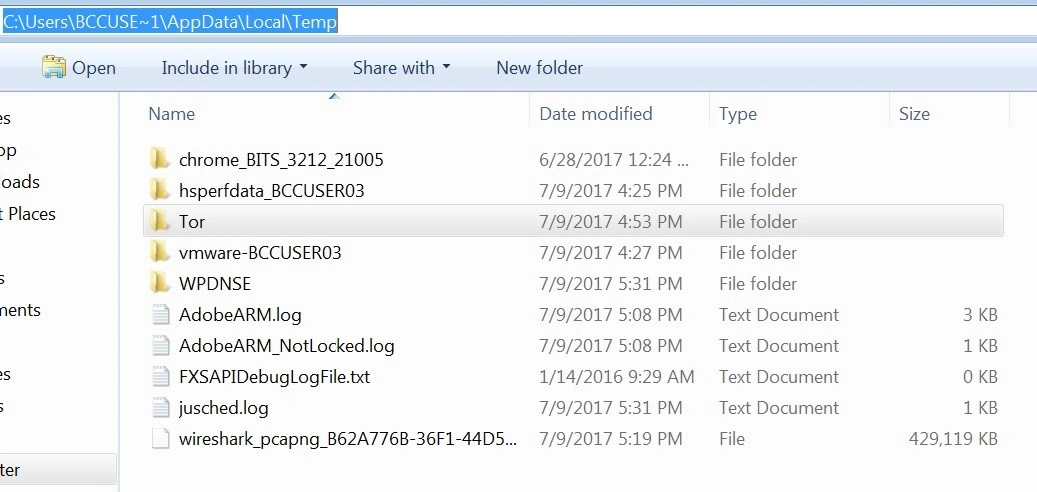
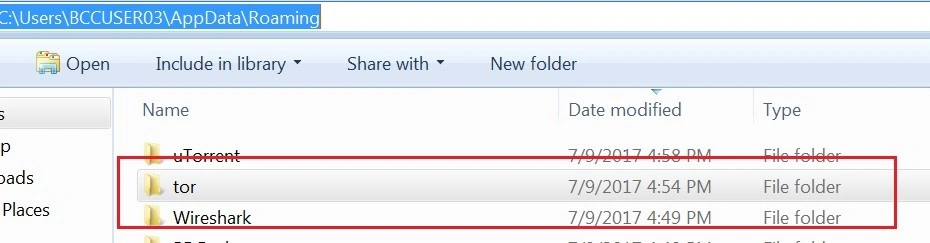
Below is a list of indicators of compromise (IOCs):
IP Addresses:
212.83.154.33
86.59.21.38
185.100.86.128
148.251.14.214
131.188.40.188
176.158.236.102
134.19.177.109
216.58.197.78
85.248.227.164
199.254.238.52
178.62.197.82
188.40.128.246
176.158.236.102
71.248.178.98
5.189.153.185
Domains:
6vas[.]com
usr2u2f5be2tty3ihzhl[.]com
zjuwaw35xhml5h2nvjrud[.]com
7xly4htpe2p2yjxfgs[.]com
51ptvhkd5kguelg373slgjqx5[.]com
Dropped file locations:
C:\users\<User-name>\Appdata\Local\Temp
C:\users\<User-name>\Appdata\Local\Temp\Tor
MD5 hashes:
51c7fff87a2fc5d62a31990643a5083c
bc301e7d26c4ed498e9f966996fc4370
Here is where I’d usually list the specific steps one can take to mitigate their exposure to Karo, but I’ve just about run out of ways to say “don’t open suspicious emails, keep your software up-to-date, and back up your files”. Instead, here is a list of things named ‘Karo’:
• Ethnic groups in Ethiopa and Indonesia
• A radio station in Oregon
• A sweet syrup made of corn
• A native New Zealand shrub
• Highly-ranked samurai officials in feudal Japan


