
To any Windows Admins reading this post, stop now, download the latest Patch Tuesday installment and then come back.
In this Tuesday’s release, Microsoft pushed out patches for 48 issues and, incredibly, more than half of them were marked as ‘Critical’.
Among them was one critical vulnerability (CVE-2017-8620) that caught many in the security community off-guard – the “Windows Search” Remote Execution vulnerability. On successful exploitation, an attacker can perform privilege escalation on the effected system… and its wormable.
Let’s take a look:
Vulnerability Description
According to Microsoft, the vulnerability exploitation takes place when an attacker sends a specially crafted message to the Windows search service. In an enterprise environment, the risk is particularly high as an SMB connection can help an attacker exploit the vulnerability and move laterally through a network.
If successfully exploited, the vulnerability allows the attacker to take complete control of the target system.
We’ve seen a similar vulnerability in the past (CVE-2017-8543) but in this case, there was no mention of ‘Denial of Service’ in its assessment. This latest vulnerability affecting the Windows Search function, however, has security researchers worried it could be the new ‘Wannacry’. This is due to the fact the vulnerability is wormable and has the capability to perform Denial of Service attacks on the victim system. Additionally, this even effects the latest versions of Windows.
Vulnerable Versions
Windows 10 (All versions)
Windows 8 (All Versions)
Windows 8.1 (All Versions)
Windows RT 8.1 (All versions)
Windows Server 2008 (All versions)
Windows Server 2012 (All versions)
Windows Server 2012 R2 (All versions)
Windows Server 2016 (All versions)
Recommendations
Microsoft has released a security patch for this critical vulnerability. If you haven’t already, downloaded it here.
Another solution Microsoft has suggested is that Windows admins disable the “Windows Search” function to avoid any wormable attack exploiting Remote Code Execution in Windows Search. This disables all applications from accessing the Windows Search function. The steps to do so are below: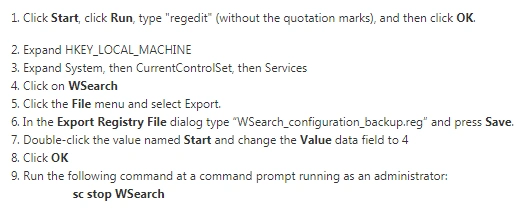
Conclusion
Any wormable vulnerability poses an incredible threat to organisations as one successful exploitation can easily spread through the entire network infrastructure. It is recommended to patch Windows as soon as possible. Additionally, disabling the Windows Search function will further mitigate the risk from such an attack.


