INFOGRAPHICS
How to become a CISO what a F100 CISO looks like
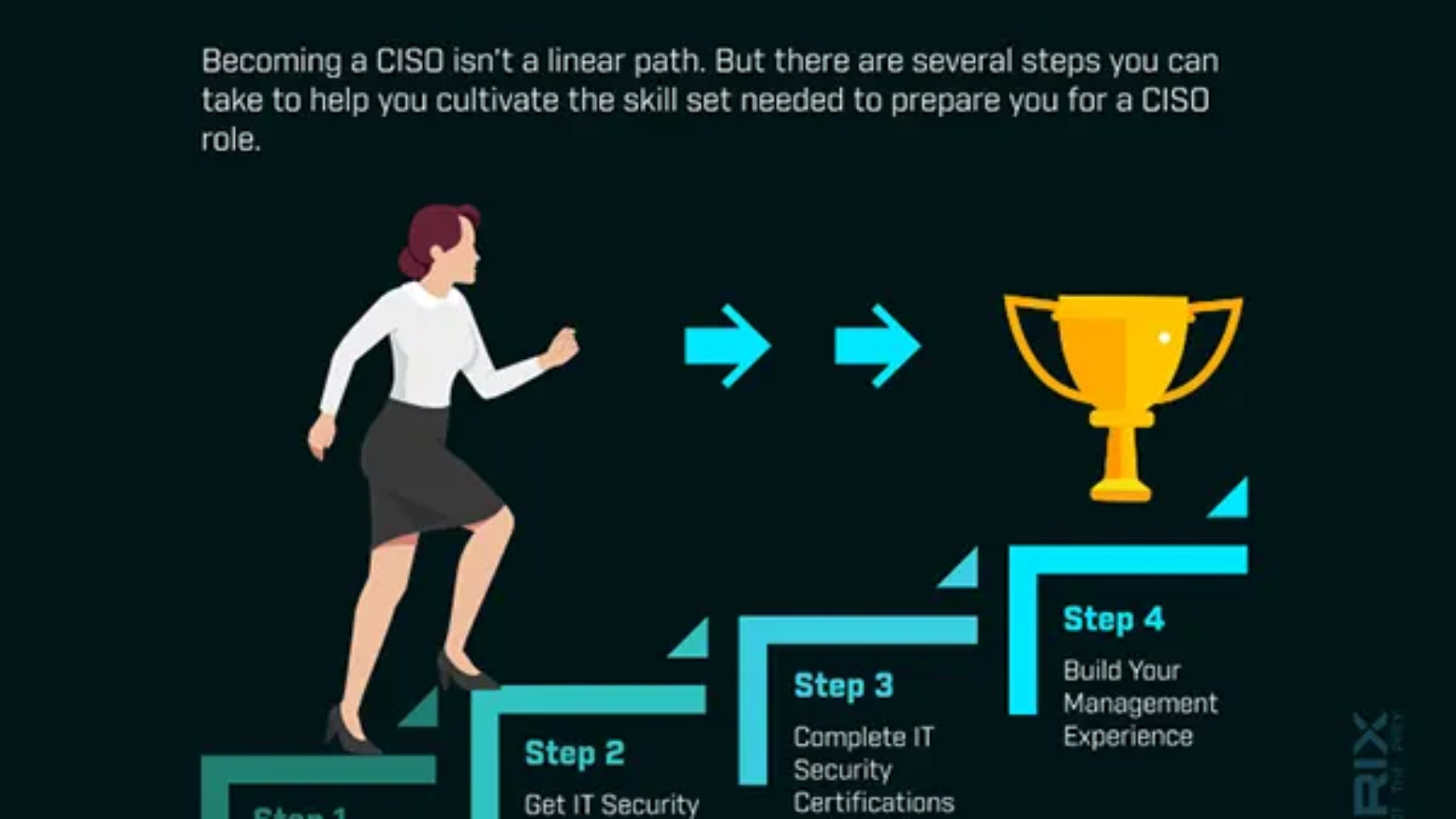
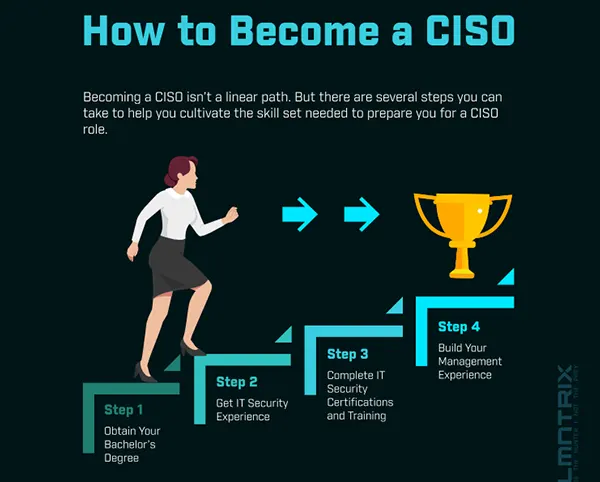
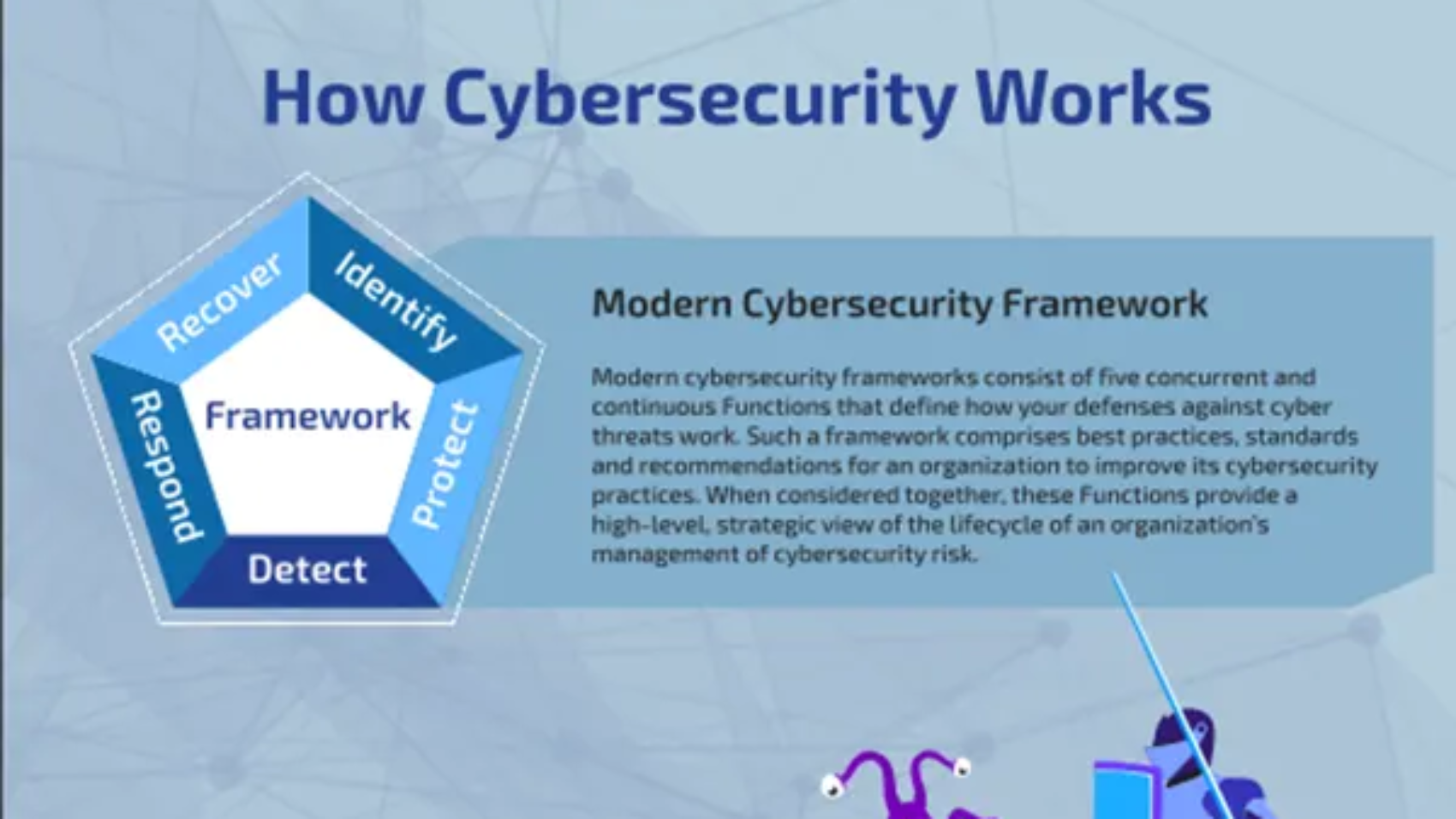
The chief information security officer (CISO) is the executive responsible for an organization's information and data security. While in the past the role has been rather narrowly defined along those lines, these days the title is often used interchangeably with CSO and VP of security, indicating a more expansive role in the organization.
Ambitious security pros looking to climb the corporate latter may have a CISO position in their sights. Using this fun infographic, let's take a look at what you can do to improve your chances of snagging a CISO job, and what your duties will entail if you land this critical role. And if you're looking to add a CISO to your organization's roster, perhaps for the first time, you'll want to view this as well.