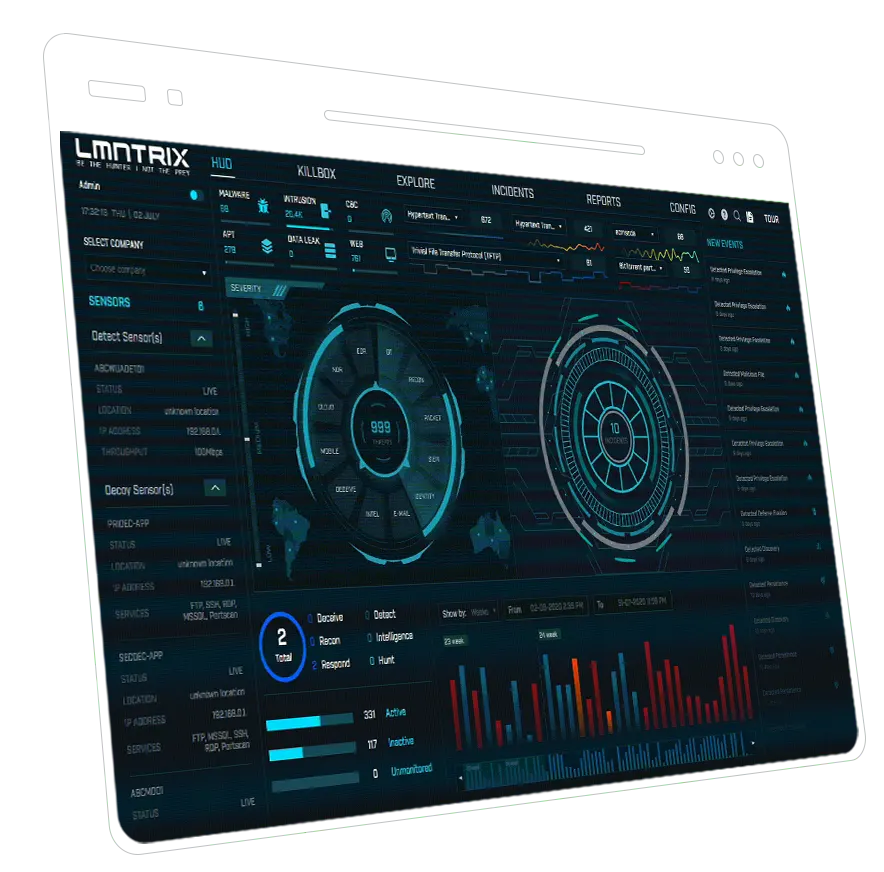
How we protect
small and large enterprises
We know that every day you have everything on the line, and that with so much at risk it can seem like adversaries have all the advantages. Together we can take the power back. Where other cybersecurity providers see a vendor and a customer, we see a united team of defenders who are stronger as one.
Faster Investigations
0
x
Reduction in Alerts
0
%
Lower Cost
0
%