LMNTRIX XDR powered by Artemis - agentic AI that hunts, investigates, and responds.
Unified XDR platform with embedded AI analyst (Artemis) and intelligent assistant (LISA). Built to eliminate blind spots, automate response, and accelerate outcomes.
Detection & Analytics
- Proprietary ML/AI models + UEBA power detection across all domains.
- 95 % fewer false positives. MTTD under 1 minute.
- Full-fidelity network forensics and deception alerts reveal hidden attacker behavior.
Response & Playbooks
- Prebuilt and custom automation for endpoint, identity, cloud, mobile and OT.
- Containment, rollback, isolation and DFIR—without rebuilding or reimaging.
- 30 min or less response time for over 90 % of incidents.
Hyper Converged Platform
- Thirteen integrated modules running natively under one console.
- Normalized data lake ingests from agents, sensors, APIs, web, SaaS, OT and third-party sources.
- Runs on your infrastructure or cloud, scales globally.
Human Centered Intelligence
- Built-in threat hunting, analyst workflows, detection context and Attack Rehearsal.
- Our SOC team works as your team—24/7, at no extra cost.
- Noise-free dashboards guide decisions, not bury them.
Identity Native & OT Aware
- Identity detection is core — not an addon. We stop lateral movement, privilege abuse, compromise.
- OT and IoMT support with deception, NDR, endpoints and deep packet storage, without disrupting operations.
Integration & Ecosystem
- Plug-and-play connectors and APIs for SIEM, SOAR, WAF, identity providers and threat feeds.
- Prebuilt dashboards for rapid insight.
- Open API ecosystem—build your own automations, integrations and rules.
Here’s the thing.
You don’t need more tools. You need fewer — smarter — ones.
LMNTRIX XDR isn’t a stitched-together stack of modules. It’s a single, intelligent platform built to ingest everything, think across every threat surface, and act instantly.
Our AI strips away the noise. Our playbooks automate the grind. Our analysts back your team 24/7 — no surprise costs, no red tape.
The Result?
Faster detection. Smarter response. Broader coverage. Lower cost.
That’s what it means to do XDR right.
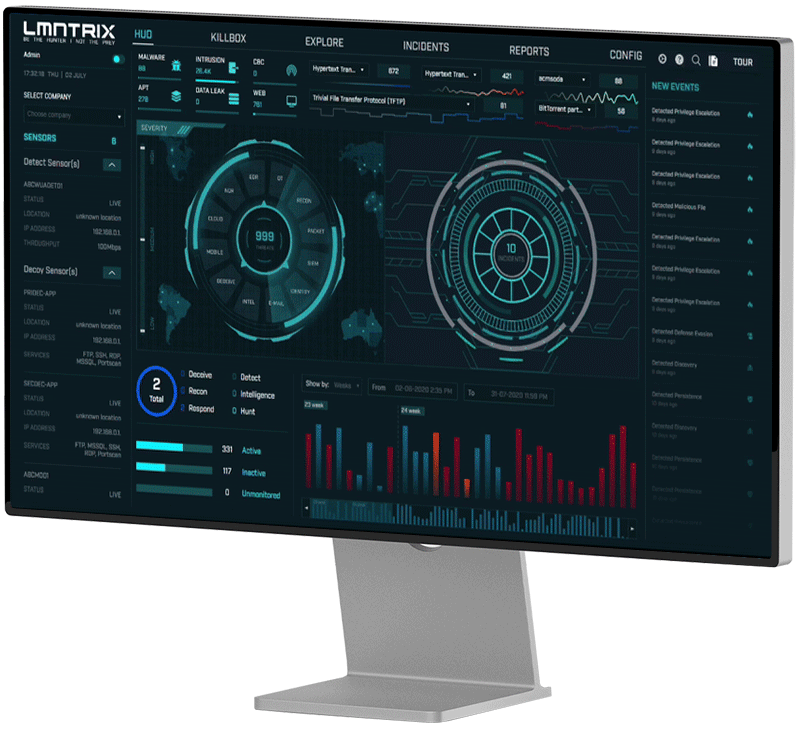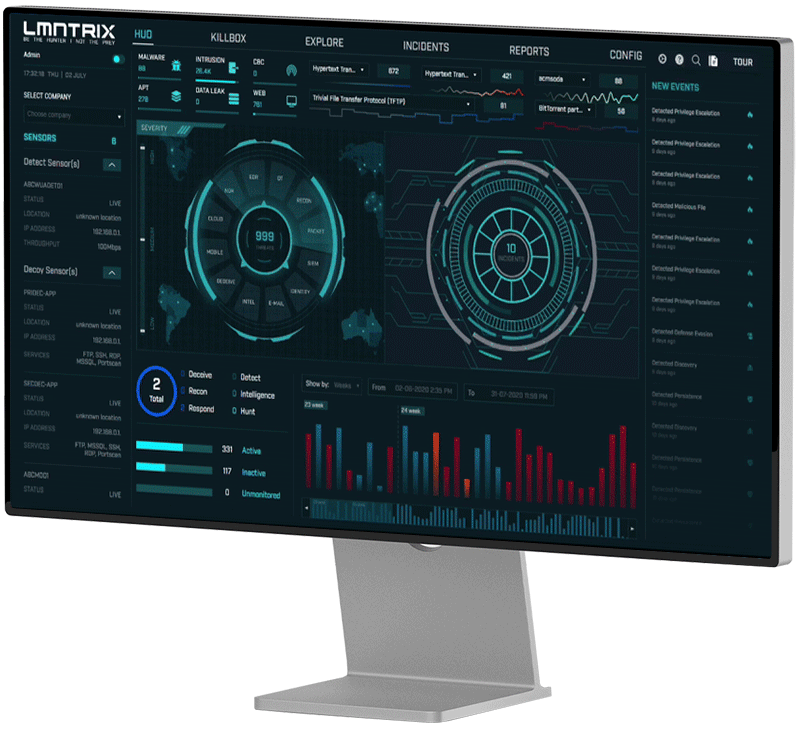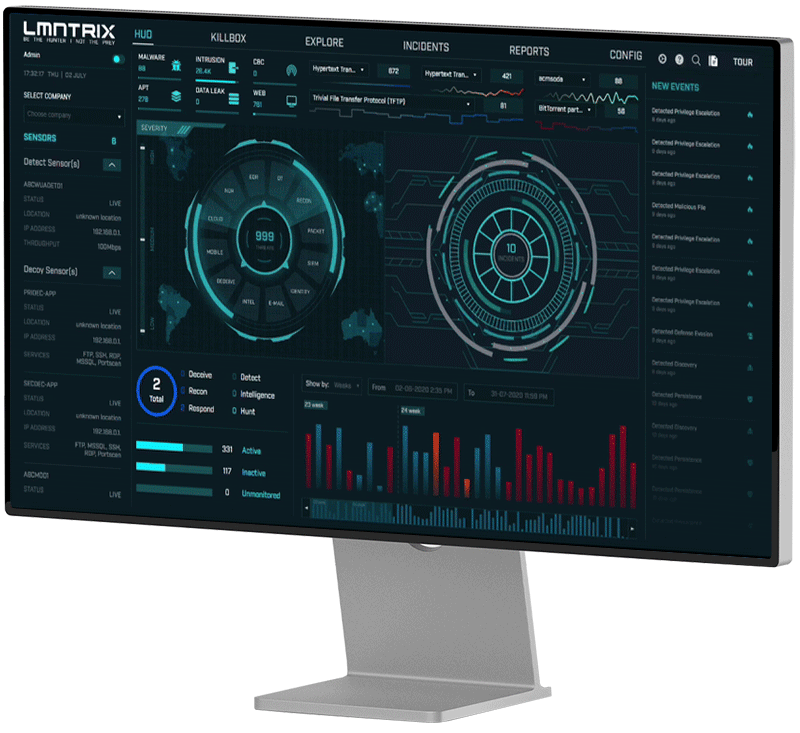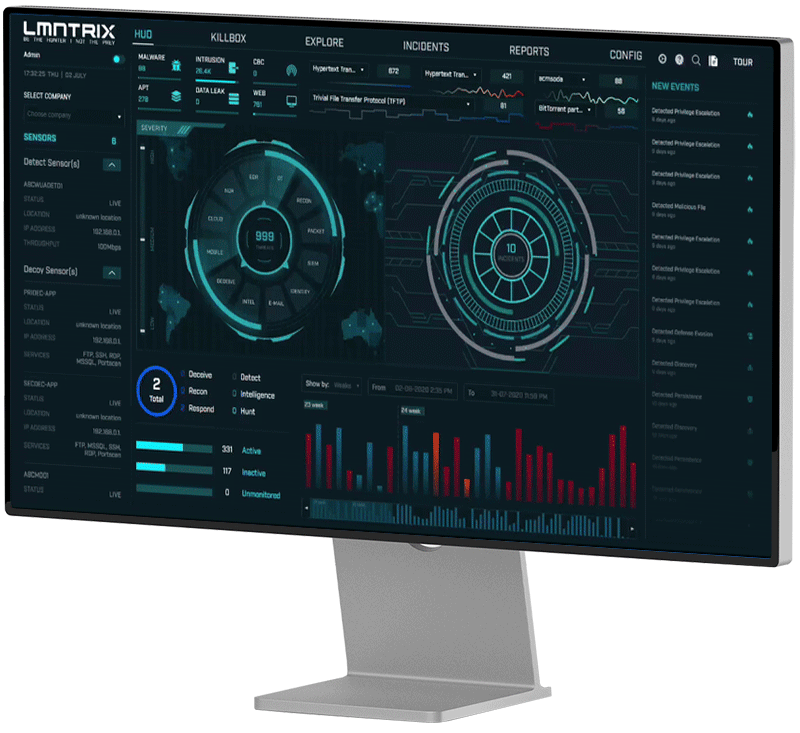
The Next Frontier for Detection and Response
XDR unlike any other
Fortify. Automate. Supercharge. Extend protection from the endpoint to the cloud with complete visibility, military-grade protection, and automated response. Discover the power of hyper-converged LMNTRIX XDR.
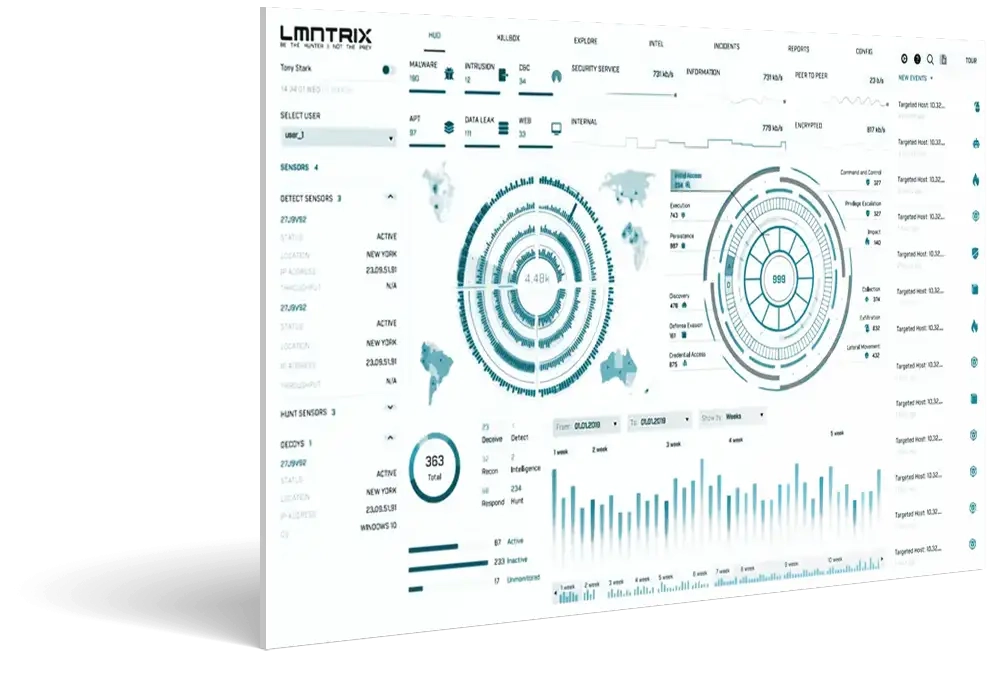

Extended
Natively unify Machine and Underground Intelligence, NGAV, EDR, NDR, Network Forensics, Cloud Security, Mobile Threat Defense, Security Analytics, Identity protection, with Deceptions Everywhere.
Detection
Detect threats missed by existing security controls, and turn previously siloed data into high-fidelity, cross-domain attack indicators, insights and alerts to surface the most sophisticated threats.
Response
Turn XDR incidents into action. Automate integrated response actions across the LMNTRIX XDR platform and 3rd party security products to shutdown the most advanced attacks from endpoint to cloud - all from a single console.
Forensics
Identify the root cause of threats to prevent future incidents.
Superior Detection - Unmatched Response - Open Without Compromise
Under the hood of yourManaged XDR

NGAV+EDR
Endpoint technology that focuses on detecting and responding to security threats on devices such as desktops, laptops and servers. Uses advanced analytics and machine learning algorithms to analyze endpoint device activity and identify potential security threats.

NDR
Advanced analytics and machine learning algorithms to analyze network traffic and identify abnormal behavior or patterns that may indicate a security threat.
Cloud

Deceptions
Also known as Moving Target Defense, it involves continuously changing or randomizing the system or network's attack surface, such as by changing IP addresses, ports, software configurations, or other system parameters with the use of decoys, breadcrumbs and traps.

Intelligence

SIEM

Recon
The Game Changer
You’re ready for advanced protection
and that means XDR
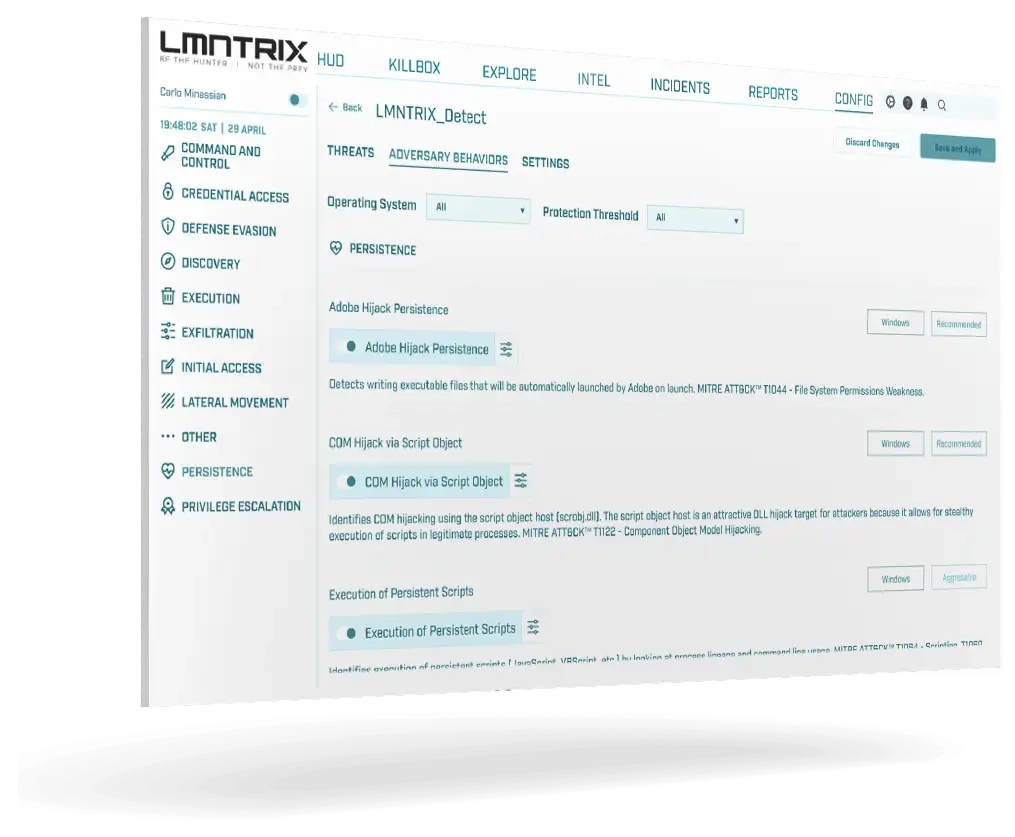
- Endpoint Security (LMNTRIX EDR)
- Network Security (LMNTRIX NDR)
- Mobile Security (LMNTRIX MOBILE)
- IoT & OT Security (LMNTRIX OT)
- Identity Protection (LMNTRIX IDENTITY)
- Network Forensics (LMNTRIX PACKETS)
- Moving Target Defense (LMNTRIX DECEIVE)
- Underground Intelligence (LMNTRIX RECON)
- SIEM & Security Analytics (LMNTRIX SIEM)
- SIEM Rules
- Incident Management
- ML-Driven Threat Detection
- Proactive Threat Hunting
- Automated Root Cause Analysis
- Flexible Response
- Integrated Threat Intelligence
- Integrated Policy Management
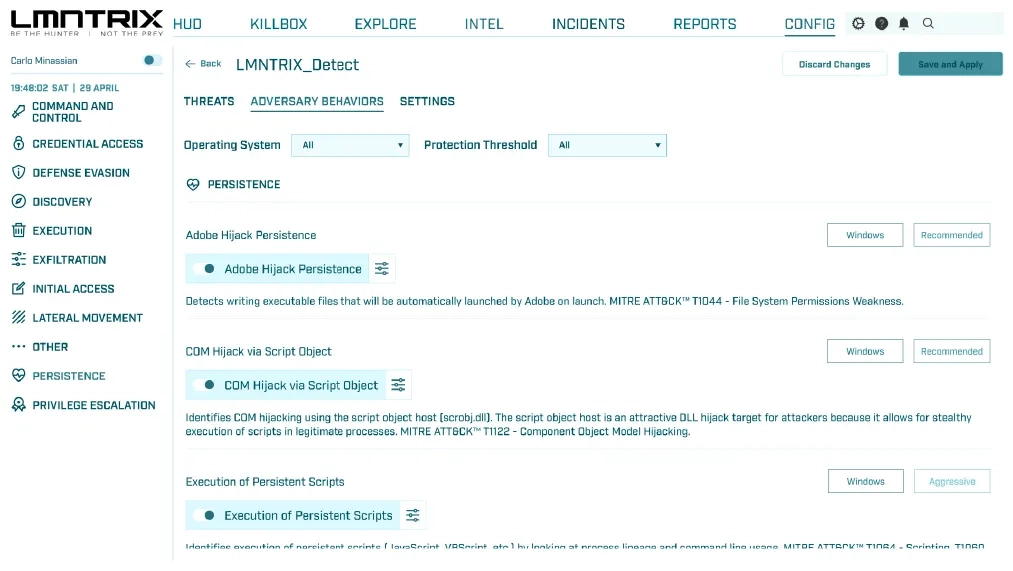
Endpoint Security (LMNTRIX EDR)
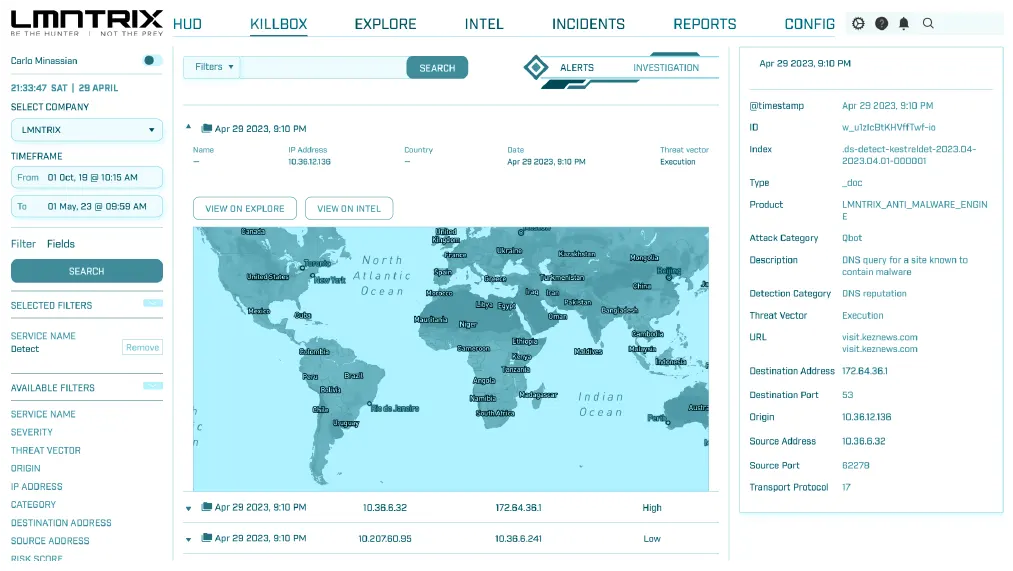
Network Security (LMNTRIX NDR)
Our NDR technology combines machine learning and behavioral analytics to identify and respond to even the most elusive threats in real-time. With comprehensive visibility into network traffic, you can proactively detect and stop attacks before they cause damage, ensuring the security and continuity of your business operations.
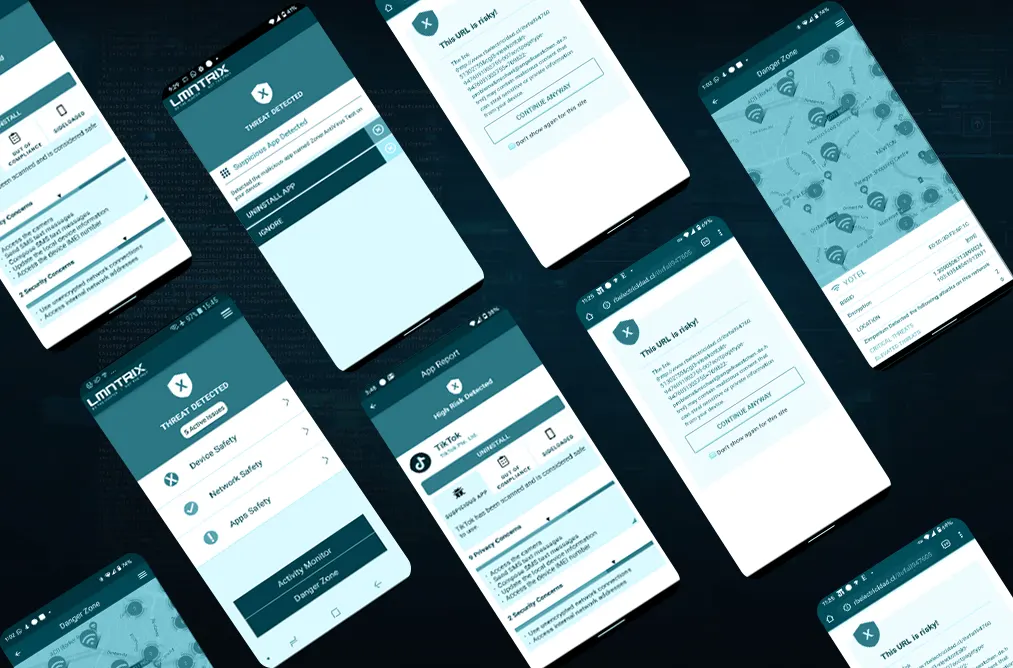
Mobile Security (LMNTRIX MOBILE)
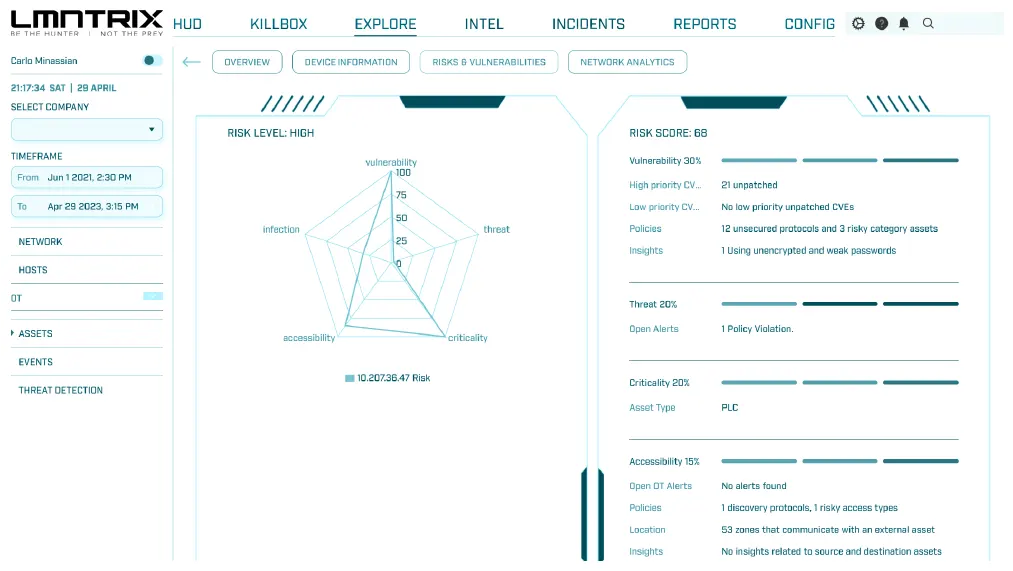
IoT and OT Security (LMNTRIX OT)
Identity Protection (LMNTRIX IDENTITY)
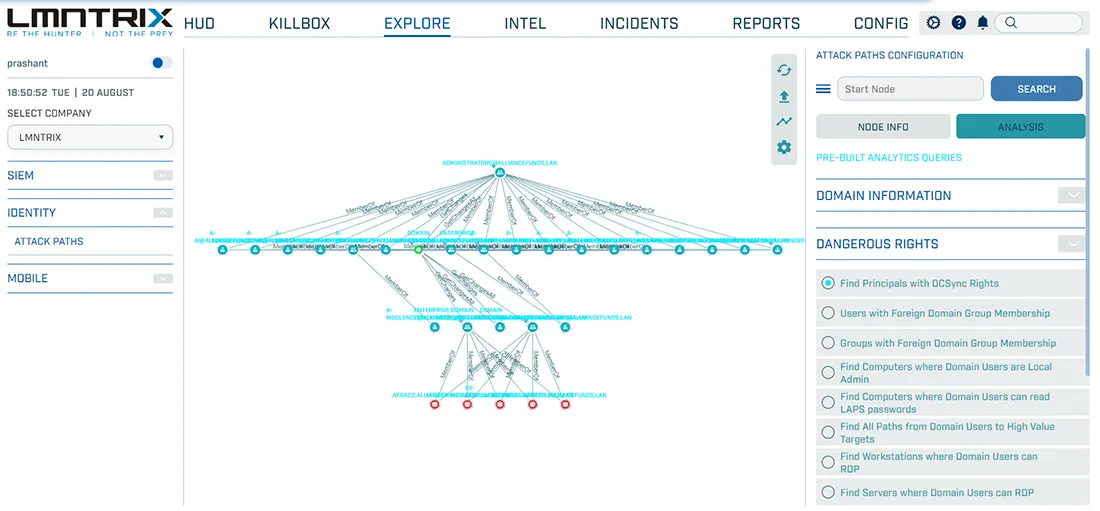
Network Forensics (LMNTRIX PACKETS)
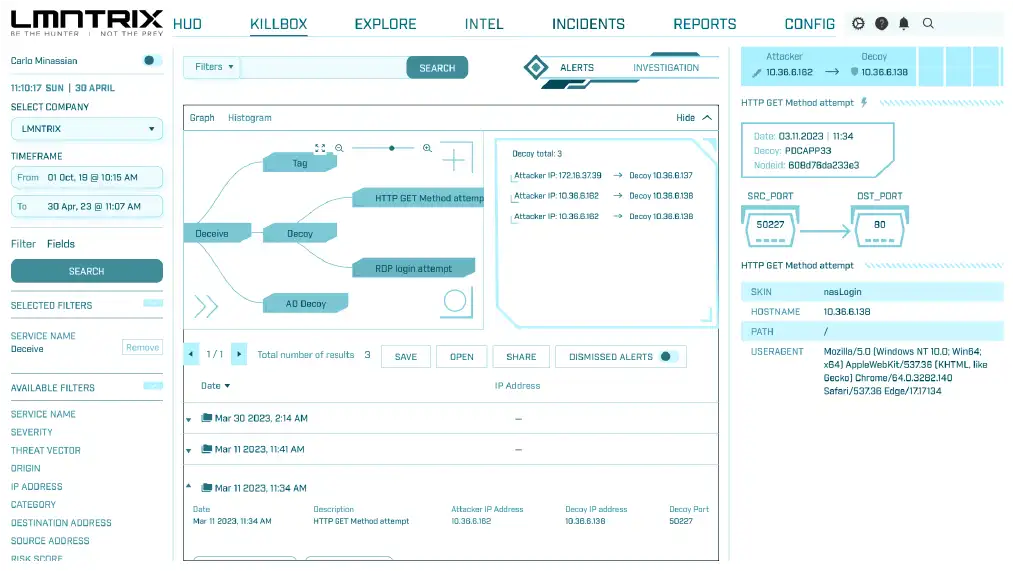
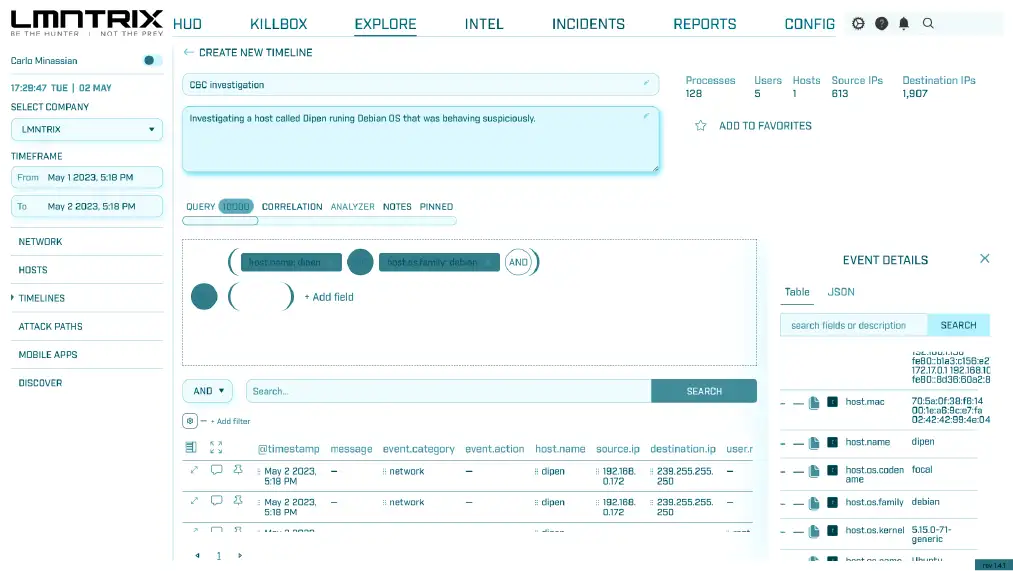
Moving Target Defense (LMNTRIX DECEIVE)
Continuously change or randomizing the system or network's attack surface, such as by changing IP addresses, ports, software configurations, or other system parameters with the use of decoys, breadcrumbs and traps.
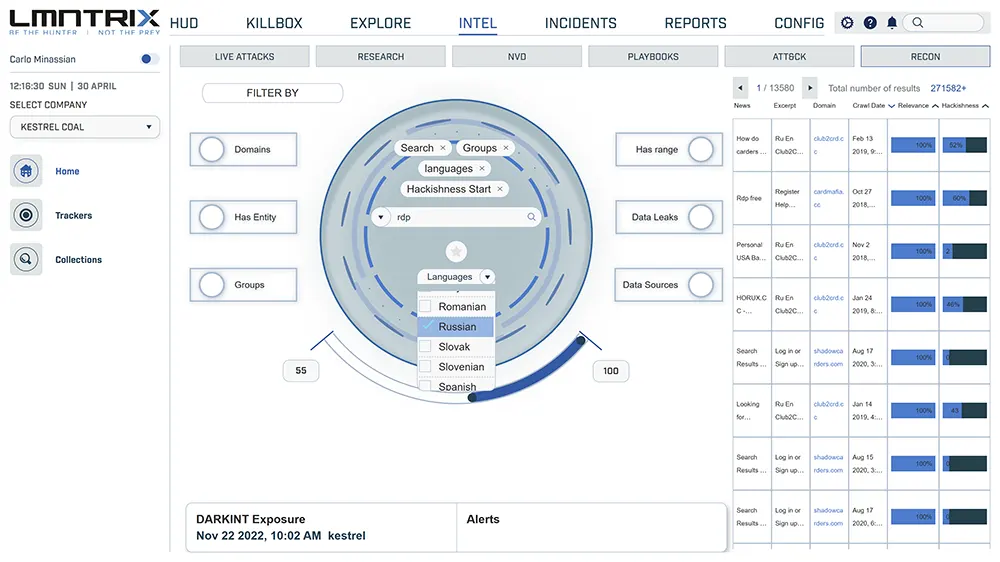
Underground Intelligence (LMNTRIX RECON)
Shine a light on the deep and dark web by using our intelligence, knowledge and proprietary techniques to your advantage.
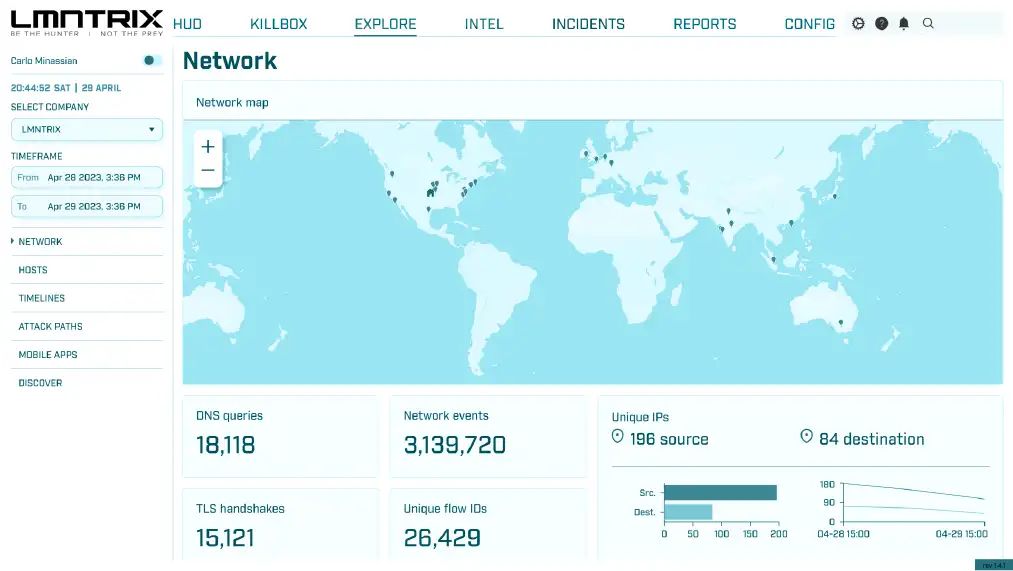
SIEM & Security Analytics (LMNTRIX SIEM)
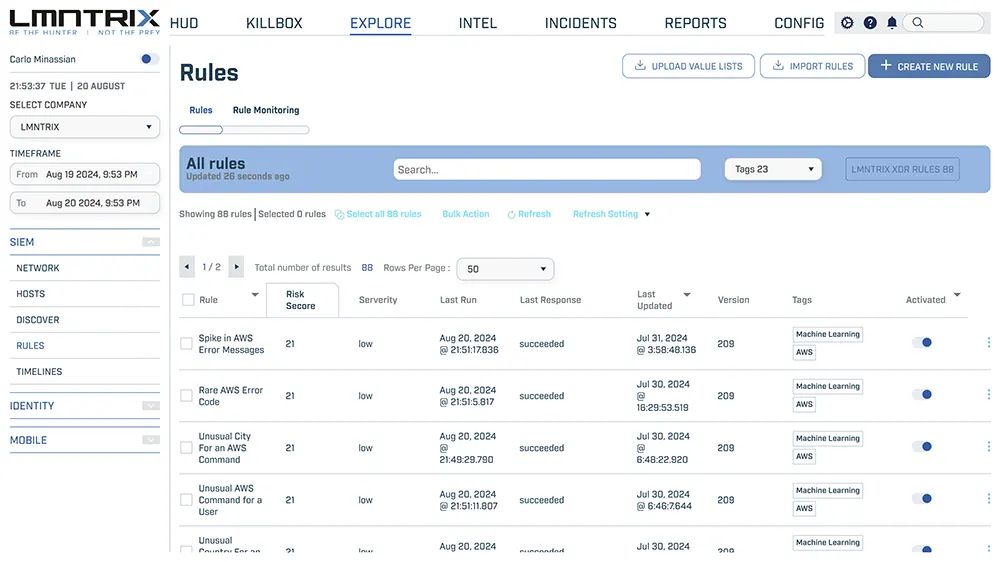
SIEM Rules
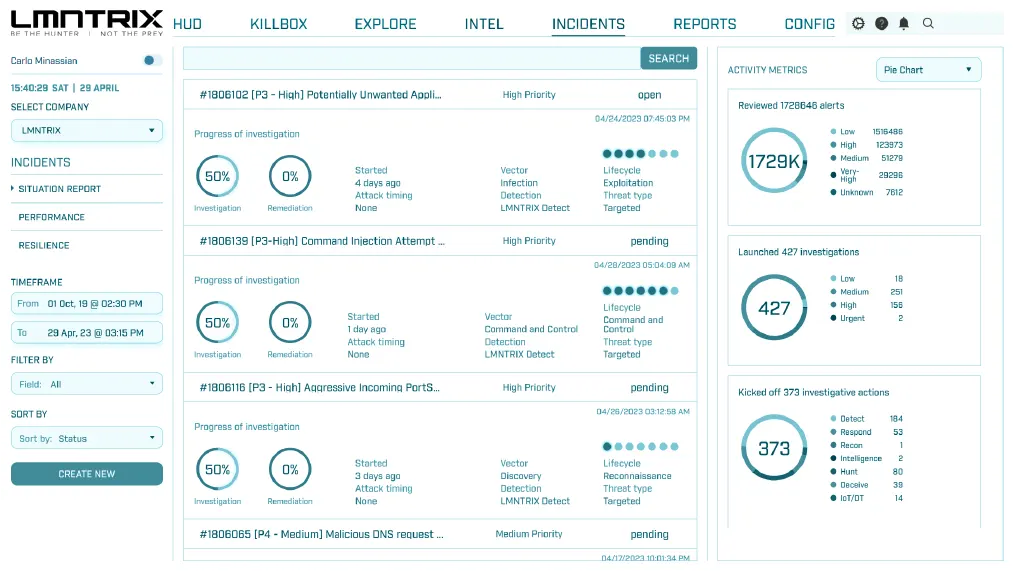
Incident Management
ML-Driven Threat Detection
Proactive Threat Hunting
Automated Root Cause Analysis
Flexible Response
Integrated Threat Intelligence (LMNTRIX INTELLIGENCE)
Integrated Policy Management
Comprehensive Threat
Prevention, Detection and Response
LMNTRIX XDR
Block endpoint, network, cloud and mobile attacks with a proven, lightweight next-gen agent, network sensors and APIs
NGAV, EDR, Mobile Threat Defense, Identity
NDR + Network Forensics + SIEM
Machine & Underground Intelligence
Full Visibility & ML-Driven Detection
Find stealthy threats with the solution that achieved the best combined MITRE ATT&CK detection & protection scores
Machine Learning and Analytics
Rogue Device Discovery & Asset Management
Vulnerability Assessment
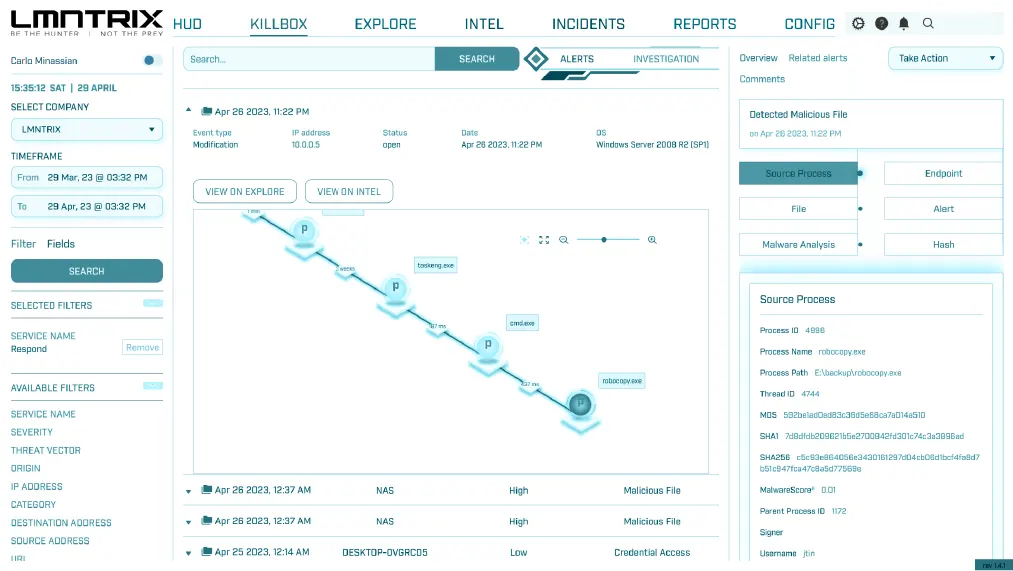
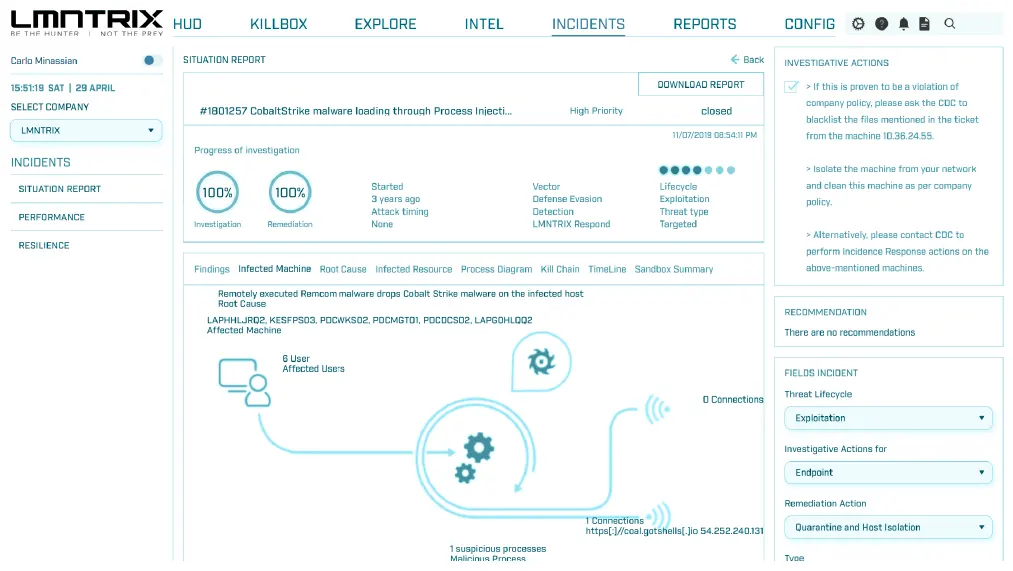
Accelerated Investigations
Quickly analyze attacks by grouping alerts into incidents and viewing rich investigate context
Incident Management
Root Cause Analysis & Cross-Data Insights
Live Terminal for Direct Endpoint Access
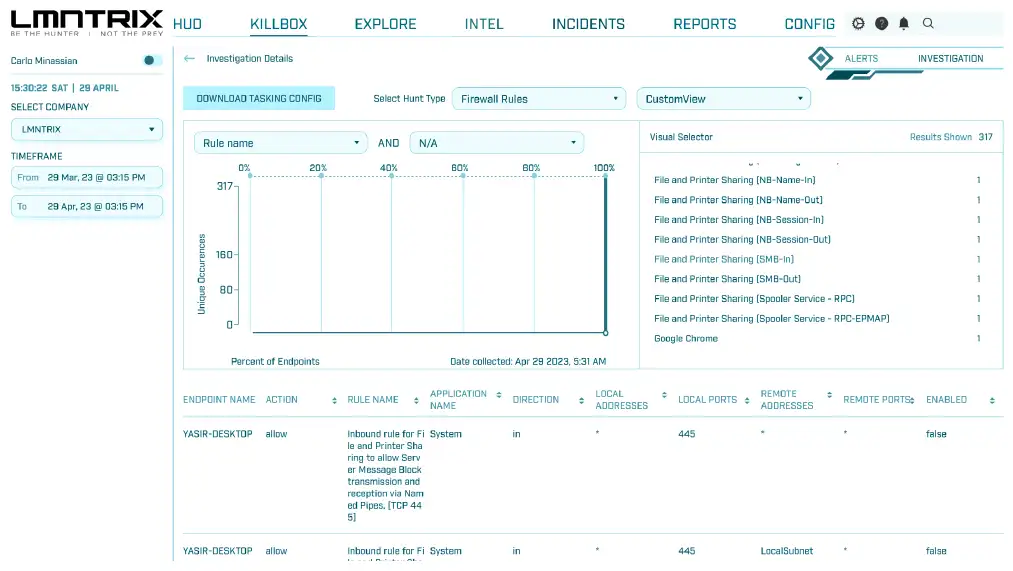
Active Threat Hunting
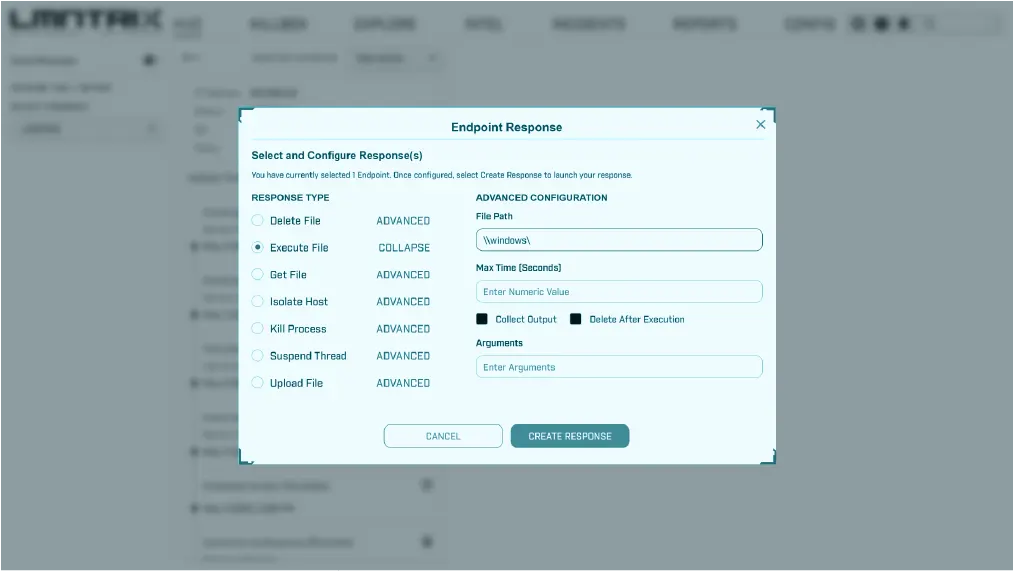
Swiftly contain fast moving threats across key enforcement points
Search and Destroy
Script Execution
File Block, Quarantine, Removal, Device Isolation
Automatic Containment Across Network & Cloud
LMNTRIX is compatible with
The cybersecurity tools you already have
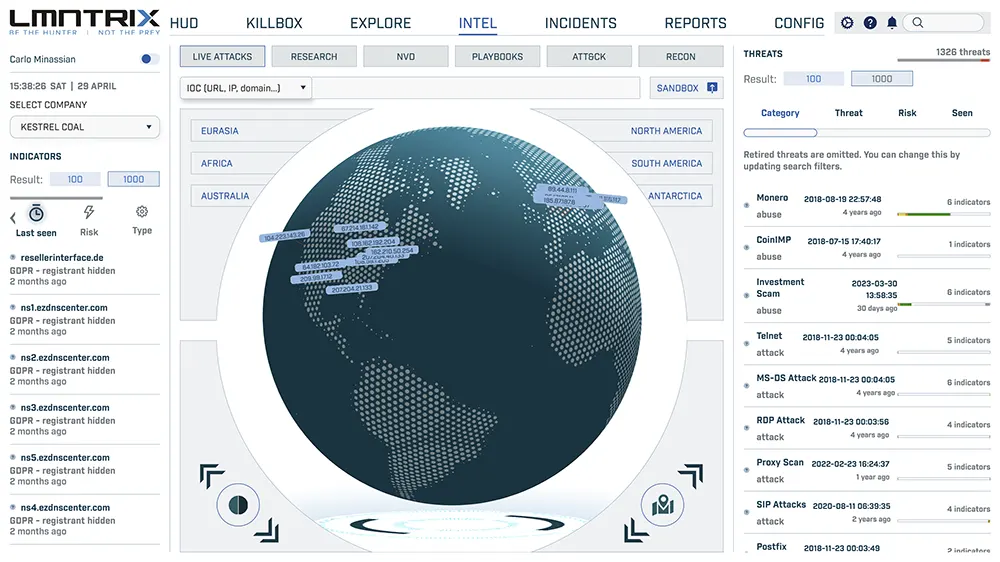
We detect far more threat vectors because we cover more tech. LMNTRIX is compatible with a growing list of security telemetry providers such as those below, and many others. We can provide the technology you need from our award-winning portfolio, or our XDR can leverage your existing cybersecurity technologies to detect and respond to threats. Telemetry is automatically consolidated, correlated, and prioritized with insights from the LMNTRIX tech stack and the LMNTRIX Threat Intelligence.



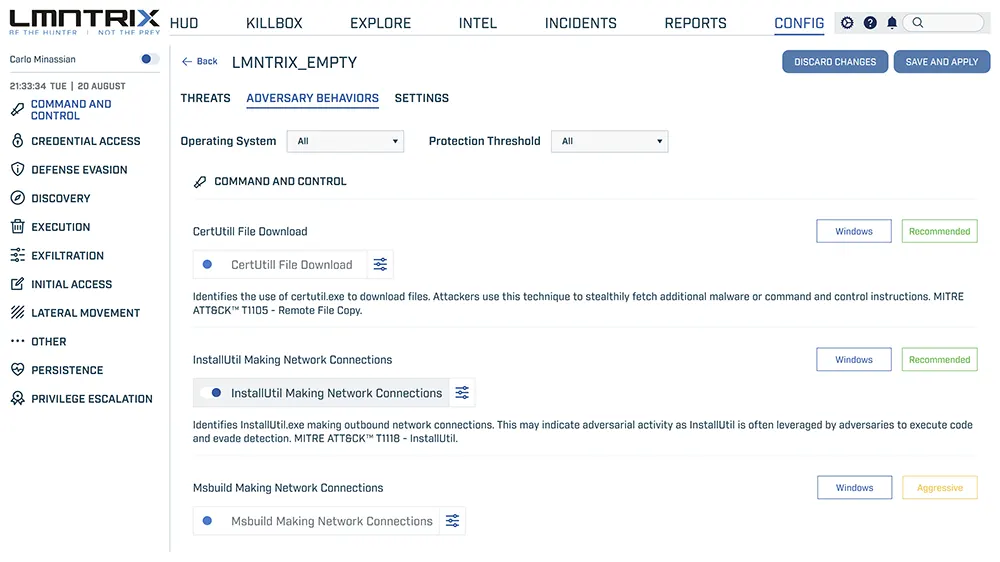
How We Protect
LMNTRIX wasn’t built to check boxes. It was built to solve the problems modern security teams actually face: alert fatigue, tool sprawl, slow response, identity blind spots, and threats that slip past traditional detection.
Here’s what we stand for:
Multi-Agent Architecture
No-Code Automations
Unified by design, not acquisition
Built-in, not bolted-on
Artemis is embedded within the core engine. LISA is built into the workflow. No add-ons. No surprise licenses.
Smart analytics, human focus
Response that moves at machine speed
Identity-native from the start
Coverage that’s actually complete
Built to lower your cost and complexity
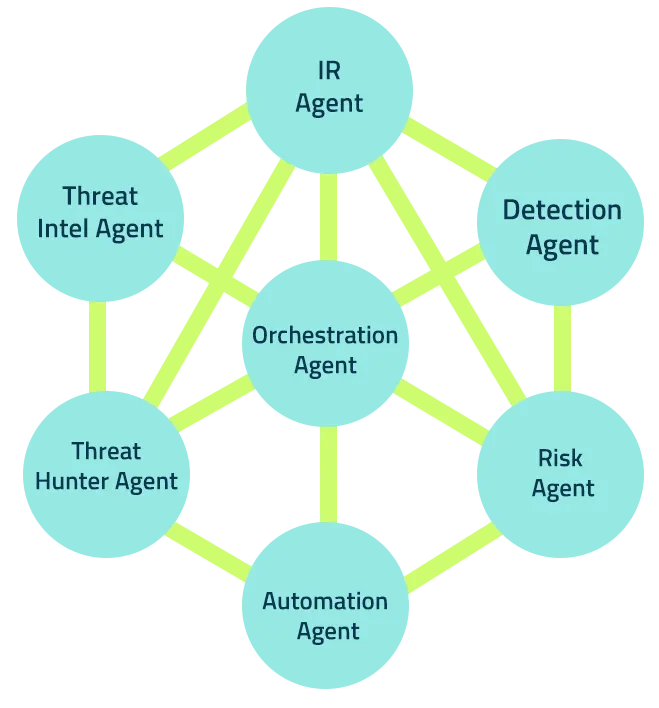
How LMNTRIX Beats the Competition

Agentic AI, not just automation
While others bolt on LLMs or basic playbooks, LMNTRIX runs Artemis — an embedded multi-agent system that handles alert triage, enrichment, correlation, and response like a Tier 1–2 analyst. All backed by LISA, your always-on assistant.

Built-in, not bolted on

Intelligence designed for humans

Response that doesn’t pause

Real coverage, real scale

Faster, more effective SOC for less
Competitive Feature Comparison
| Capability | LMNTRIX XDR | Palo Alto Cortex | SentinelOne Singularity | CrowdStrike Falcon |
|---|---|---|---|---|
| Agentic AI Investigations | ✅ Artemis + LISA handle Tier 1–2 autonomously | ❌ Rule-based SOAR | ❌ Basic LLM integration | ⚠ Limited AI triage |
| ChatOps Collaboration | ✅ Native Slack/Teams via LISA | ❌ No | ⚠ Limited in-app | ⚠ Falcon assistant UI |
| Human-AI Fusion | ✅ Built-in escalation + feedback loop | ❌ | ❌ | ❌ |
| Unified multi vector coverage | 13 native modules running hyper converged | AI powered modules | Endpoint + network + cloud | Endpoint + cloud + identity |
| Identity-native detection | Identity is core: compromise, lateral, escalation | Partial (via acquisition) | Ingests identity telemetry | Identity protection module |
| Automation & response | One-click containment, rollback, DFIR included | Module-based SOAR | Marketplace automations | Agent-driven remediation |
| Network & OT threat detection | Full packet NDR, deception, OT integration | Cloud posture + logs | Network visibility via agents | Broad, but limited OT support |
| Human friendly alerting | Contextual, consensus-based alerts & hunts | AI scoring & alerts | Developer-query tools | Lightweight agent dashboard |
Meet Artemis & LISA

Artemis
The LMNTRIX Agentic AI Engine
Autonomous threat hunting and triage
Real-time alert investigation and root cause analysis
Context-based risk scoring
Adaptive learning from analyst feedback
Execution of automated response across your stack

LISA
LMNTRIX Intelligent Security Assistant
ChatOps-powered investigation delivery
Human-in-the-loop escalation
Conversational alert review and response approval
Instant access to context and case history
Seamless handoff between automation and analysts
1
Detect < 1 Min
5
Investigate < 5 mins
30
Remediate<30 Mins
How It Works
- 1
Ingest
- 2
Analyze & Investigate
- 3
Collaborate via ChatOps
- 4
Act & Automate
- 5
Learn & Report
Built-in Response,
Not Add-on
- Endpoint quarantine, identity isolation, cloud misconfig fix
- Automation + manual override
- DFIR and rollback included
Customer Outcomes & ROI
Deploy in days
Automate > 90%
Cut MTTR
Reduce
Enable analysts
Experience Agentic XDR — Automated. Intelligent. Collaborative.
How We Protect
small and large enterprises
Why clients love working with LMNTRIX
You’re ready for advanced protection
and that means XDR







Don't just take our word for it...

Leader

Leader

Open Source Excellence

Top 250 MSSP Companies In The World

Users Choice Award
Top Rated Security



Ready to take the next steps with LMNTRIX MXDR ?
The choice is yours: see LMNTRIX in an on demand demo or set up a customized demo or request a quote.