LMNTRIX Endpoint Security
Secure Every Endpoint. Stop Every Breach.
Endpoint Protection Redefined: Protect Your Endpoints with AI-Driven Detection and Response – Powered by LMNTRIX XDR
Endpoint ProtectionRedefined
The LMNTRIX Endpoint Security is a foundational component of the LMNTRIX XDR platform, engineered to deliver powerful endpoint protection through a unified approach that combines Next-Generation Antivirus (NGAV) and Endpoint Detection and Response (EDR). This module moves beyond traditional endpoint security to provide proactive, multi-layered defense against modern cyber threats.
The NGAV element leverages AI-driven analytics to detect and block known and unknown threats in real time, including ransomware, malicious macros, and file-less attacks. Meanwhile, the EDR component provides deep, real-time visibility into endpoint activity, enabling rapid identification of anomalous behaviors, forensic investigation, and automated or manual response to incidents. Seamlessly integrated into both cloud and on-premises environments, LMNTRIX Endpoint Security ensures your endpoints remain secure with minimal disruption.
Whether you're defending against targeted adversaries or managing security across a distributed workforce, LMNTRIX Endpoint Security aligns with your operational objectives and delivers unparalleled endpoint resilience.
Valueto Your Organization
Real-Time Threat Prevention and Detection
Uses AI and machine learning to identify threats—including file-less malware and ransomware—at the point of execution.
Complete Endpoint Visibility
Centralized monitoring across all endpoints (EUCs and servers) provides actionable intelligence for improved decision-making.
Accelerated Incident Response
Automated threat detection, isolation, and remediation significantly reduce response time.
Proactive Threat Hunting
Deployment Scope

Endpoint Definition
Covers any machine, including end-user computing (EUC) devices and servers, whether hosted on-premises or in the cloud.

Supported Operating Systems

System Requirements
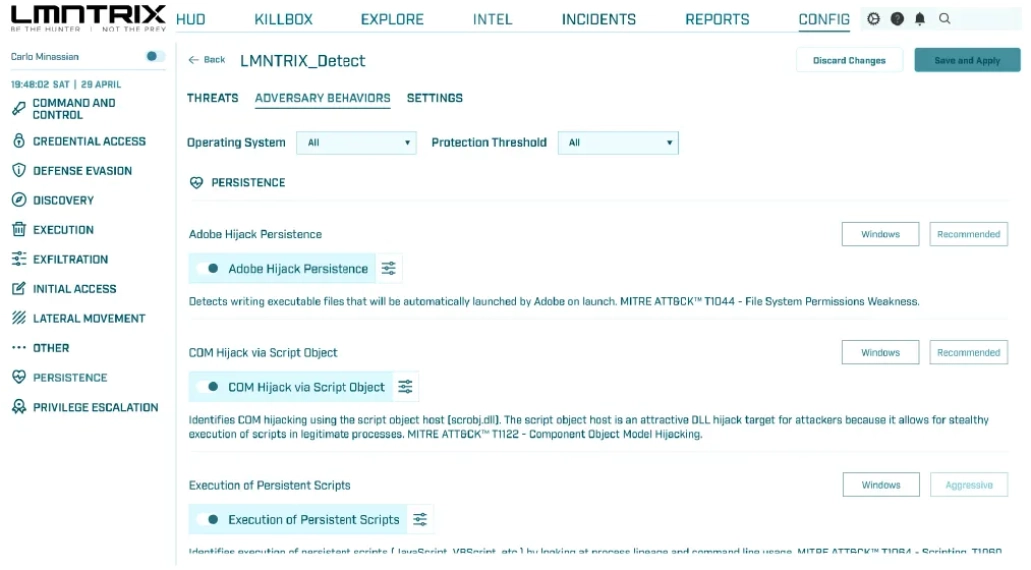
Key Capabilities
Threat Detection &Prevention
Real-time Detection
of Exploits, Malware, and File-less Attacks
Adversary Tradecraft Prevention
Ransomware Prevention
Malicious Macro Blocking
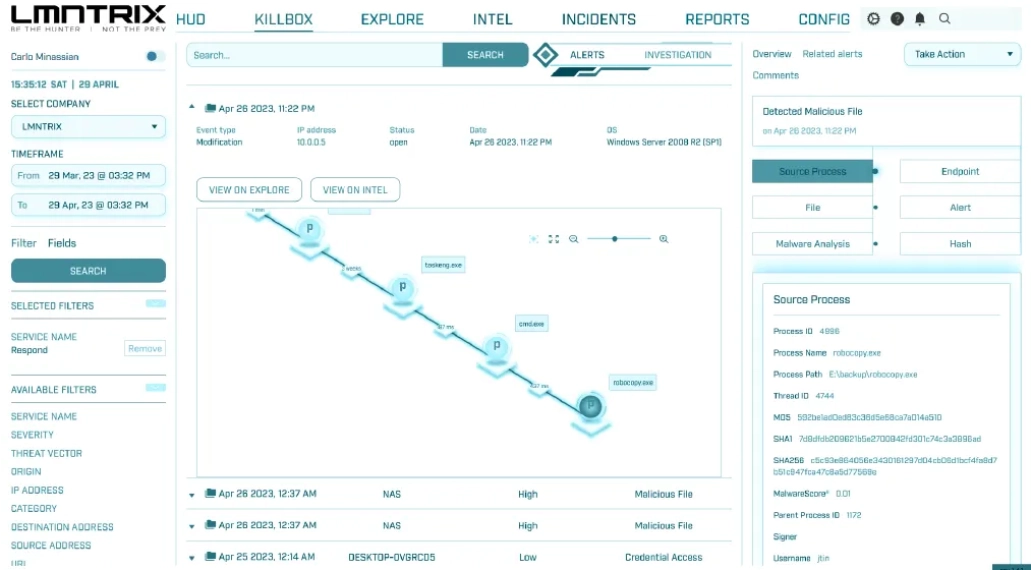

Incident Response& Forensics
Root Cause Analysis
Reconstructs attack paths and origin
Post-Breach Forensics
Breach Validation
Threat Hunting& Analysis
Encrypted & In-Memory Attack Detection
Proactive Threat Hunting
Behavioral Tracking & Alerting
Deep System Analysis
Remediation& Containment
File Classification & Disposition
Automated/manual handling of suspicious files
Threat Blocking & Quarantine
Endpoint Security FAQ
Endpoint Security
What is endpoint security software?
Endpoint security software consists of applications or tools installed on endpoint devices such as laptops, desktops, and servers to protect them from a wide array of cyber threats. These threats include malware, ransomware, exploits, live attacks, and malicious scripts that aim to steal data, cause financial loss, or disrupt systems and operations. By securing each individual device connected to a network, endpoint security software plays a crucial role in an organization’s overall cybersecurity strategy, preventing attackers from infiltrating the network through vulnerable endpoints.
What is considered an endpoint?
An endpoint refers to any device that serves as a point of entry or exit within a network, where communications originate or are received. Unlike network devices that merely relay or route data (like routers or switches), endpoints are the devices that actively participate in network communications. Examples include desktops, laptops, smartphones, tablets, servers, and Internet of Things (IoT) devices. In essence, an endpoint is any device that can connect to a network and is capable of sending or receiving data.
Are servers considered endpoints?
Yes, servers are considered endpoints within a network infrastructure. They play a vital role by hosting applications, storing data, and providing services to other devices. Servers, often running operating systems like Linux, are just as susceptible to cyber threats as other endpoints. Therefore, it’s essential to deploy robust security solutions on servers to ensure they are protected against malware, unauthorized access, and other cyber attacks, just like any other endpoint device.
What is next-gen endpoint protection?
Next-generation endpoint protection refers to advanced security solutions that proactively predict, prevent, and respond to cyber threats using cutting-edge technologies. Unlike traditional antivirus software that relies on signature-based detection, next-gen solutions employ machine learning, artificial intelligence, and behavioral analysis to monitor all activities within a network—including system kernel and user space operations. By evaluating patterns and identifying anomalies in real-time, these tools can detect and neutralize threats early, even those that have not been previously identified. This proactive approach enhances the ability to catch sophisticated attacks like zero-day exploits, fileless malware, and advanced persistent threats (APTs) before they can cause significant harm.
What is an endpoint protection platform?
An Endpoint Protection Platform (EPP) is an integrated security solution that combines multiple protective technologies into a single, unified agent deployed on endpoint devices. Its primary functions include preventing, detecting, and responding to threats across various attack vectors. Powered by machine learning and automation, an EPP offers real-time threat prevention and detection, swiftly eliminates identified threats through automated, policy-driven responses, and provides comprehensive visibility into endpoint activities. This includes full-context, real-time forensics that help security teams understand the nature and progression of attacks, enabling them to respond more effectively.
What is endpoint management software?
Endpoint management software refers to tools that enable organizations to centrally manage, monitor, and secure all endpoint devices within their network. By deploying agents on each device, administrators can use a management console to oversee various aspects such as software updates, security policy enforcement, threat monitoring, and response actions. This centralized approach eliminates the need for multiple disparate tools and add-ons, streamlining administrative tasks and ensuring consistent security measures are applied across all endpoints.
What is the best endpoint protection?
The most effective endpoint protection combines advanced technologies within a single, autonomous agent to defend against a broad spectrum of cyber threats. This includes integrating both static analysis (examining code before execution) and behavioral AI (monitoring actions during execution) to protect against file-based malware, fileless attacks, malicious scripts, and memory exploits. Such solutions operate continuously, whether the endpoint is online or offline, ensuring constant protection. Evaluations by independent organizations, like the MITRE ATT&CK framework, can help identify leading solutions by assessing factors such as detection rates, response capabilities, and reliance on automation versus human analysis. The best endpoint protection systems minimize missed detections, maximize high-quality threat identifications, and automate responses to neutralize threats swiftly and effectively.
What is EDR?
Endpoint Detection and Response (EDR) is a cybersecurity solution that focuses on monitoring endpoint devices to detect suspicious activities and potential threats in real time. EDR tools collect and analyze data on every activity and event occurring on endpoints, such as process executions, network connections, and file modifications. By correlating this information, EDR provides critical context that helps identify advanced threats that may bypass traditional security measures. Upon detecting a threat, EDR solutions can automate response actions like isolating the infected device from the network, stopping malicious processes, or alerting security personnel, thereby containing the threat swiftly.
What is Active EDR?
Active Endpoint Detection and Response (Active EDR) enhances traditional EDR by adding real-time context and automated response capabilities without requiring constant human oversight. Active EDR solutions continuously track and contextualize all activities on a device, enabling them to identify malicious actions as they happen. By understanding the relationships between processes and events, Active EDR can automate the necessary responses to neutralize threats immediately. This technology also facilitates efficient threat hunting by allowing security analysts to search using a single Indicator of Compromise (IOC), streamlining the investigation process.
What is XDR?
Extended Detection and Response (XDR) is an evolution of EDR that expands threat detection and response capabilities beyond endpoints to include multiple native security layers such as networks, cloud workloads, servers, and more. XDR also aggregates and correlates data from various 3rd party sources, providing a unified view of threats across the entire IT ecosystem through a single interface. This comprehensive visibility enhances the ability to detect complex, multi-vector attacks and accelerates triage, investigation, and remediation efforts. By automating data collection and analysis across multiple security domains, XDR helps security analysts respond to threats more quickly and effectively before they can escalate.
How is XDR different from SOAR?
Security Orchestration, Automation, and Response (SOAR) platforms are designed for mature security operations centers (SOCs) to create and execute complex, multi-step workflows (playbooks) that automate responses across an integrated ecosystem of security tools via APIs. SOAR solutions are typically complex, requiring significant resources to implement and maintain.
In contrast, XDR offers a more streamlined, user-friendly approach, often described as “SOAR-lite.” XDR platforms provide out-of-the-box integrations and automate simpler response actions without the need for extensive coding or playbook development. While SOAR focuses on deep customization and orchestration across many tools, XDR emphasizes ease of use and quick deployment, offering automated threat detection and response capabilities that are accessible to organizations without a highly mature SOC.
What is the LMNTRIX EDR agent?
The LMNTRIX EDR agent is a lightweight software component installed on endpoint devices—including desktops, laptops, servers, and virtual environments—that provides autonomous protection against cyber threats. Operating at the kernel level of the operating system, the agent monitors all processes and activities in real time. Utilizing technologies like Dynamic Behavioral Tracking, it observes and records detailed information about each event, including the origin of processes, file and registry changes, network connections, and other forensic data. This comprehensive monitoring enables the agent to detect and respond to threats autonomously, even without an active internet connection, providing continuous protection for the endpoint.
How do you implement endpoint security?
Implementing endpoint security involves deploying security agents or software across all endpoint devices within an organization. This process includes installing the endpoint protection solution on each device, ensuring proper configuration, and aligning it with the organization’s security policies. Once deployed, security teams can use centralized management tools to monitor alerts, perform threat hunting, and apply both local and global security policies. Regular updates, ongoing monitoring, and periodic assessments are essential to maintain the effectiveness of the endpoint security measures and adapt to new and emerging threats.
Is endpoint security an antivirus?
While antivirus software is a component of endpoint security, modern endpoint protection encompasses a much broader range of security measures. Traditional antivirus solutions primarily rely on signature-based detection to identify known malware, which can be insufficient against new or sophisticated threats. Endpoint security solutions offer advanced capabilities such as behavioral analysis, machine learning, and real-time threat detection and response. They protect against a wide variety of threats, including malware, ransomware, zero-day exploits, and fileless attacks. Therefore, while antivirus is part of endpoint security, comprehensive endpoint protection provides a more robust defense by addressing the limitations of traditional antivirus software.
What is considered an endpoint in endpoint security?
An endpoint in endpoint security is any device that connects to a network and can send or receive data, serving as a point of entry or exit for network communications. Examples of endpoints include:
- Desktops and Laptops: Commonly used computing devices in workplaces.
- Mobile Devices: Smartphones and tablets used for both personal and business purposes.
- Wearables: Smartwatches and other connected wearable technology.
- Internet of Things (IoT) Devices: Smart devices like sensors, cameras, and appliances.
- Point-of-Sale (POS) Systems: Devices used in retail for processing transactions.
- Medical Devices: Connected equipment used in healthcare settings.
- Printers and Multifunction Devices: Networked office equipment.
- Servers and Virtual Machines: Physical and virtual systems providing services and resources.
As technology evolves, the number and variety of endpoints continue to grow, increasing the potential attack surface for cyber threats. This expansion makes securing endpoints more critical than ever, as they often represent the frontline defense against unauthorized access and data breaches. Modern endpoint security must address the unique challenges posed by diverse devices, including mobile and IoT devices, to ensure comprehensive protection.
What are the primary benefits of using LMNTRIX for cloud security and protecting cloud workloads?
LMNTRIX provides robust cloud security solutions that offer several key benefits for protecting cloud workloads:
- Comprehensive Protection: Safeguards cloud assets against a wide range of threats, including malware, zero-day exploits, and advanced persistent threats.
- Real-Time Visibility: Offers continuous monitoring and real-time insights into cloud workloads, enabling proactive threat detection.
- Automated Threat Detection and Response: Utilizes AI and machine learning to identify and respond to threats autonomously, reducing the time to mitigate risks.
- Seamless Integration: Easily integrates with major cloud service providers like AWS, Azure, and Google Cloud, ensuring consistent security across multi-cloud environments.
- Operational Efficiency: Simplifies security management with centralized control and automated processes, freeing up resources for other strategic initiatives.
By leveraging these capabilities, organizations can enhance their cloud security posture, protect sensitive data, and maintain compliance with regulatory requirements.
What is the role of AI and machine learning in LMNTRIX's cybersecurity solutions?
Artificial intelligence (AI) and machine learning (ML) are foundational to LMNTRIX’s cybersecurity solutions, enabling advanced threat detection, prevention, and response capabilities. Here’s how they contribute:
- Automated Threat Detection: AI and ML algorithms analyze vast amounts of data to identify patterns and anomalies indicative of cyber threats, including previously unknown or zero-day attacks.
- Adaptive Defense: The systems continuously learn from new data, adapting to evolving threat landscapes without requiring manual updates or intervention.
- Reduced False Positives: Intelligent analysis helps distinguish between legitimate activities and malicious behavior, minimizing false alarms and allowing security teams to focus on genuine threats.
- Real-Time Response: AI-powered automation enables immediate action against detected threats, such as isolating affected devices or terminating malicious processes, thereby limiting potential damage.
- Scalability: Machine learning models can handle the increasing volume and complexity of data as organizations grow, ensuring consistent security coverage.
Overall, AI and machine learning enhance the effectiveness and efficiency of cybersecurity measures, providing robust protection against sophisticated cyber threats.
Are Norton and Symantec the same?
Norton and Symantec are brands associated with traditional antivirus solutions that have been widely used for endpoint protection. Historically, these products have relied on signature-based detection methods, where known malware signatures are used to identify and block threats. While they have been effective against known threats, this approach has limitations in detecting new or rapidly evolving malware.
In contrast, modern cybersecurity solutions like LMNTRIX have moved beyond signature-based detection. LMNTRIX employs advanced technologies such as static machine learning analysis and dynamic behavioral analysis to protect against a broader spectrum of threats. By evaluating files and processes in real time—both before execution and during runtime—without relying on signature databases, LMNTRIX can detect and neutralize zero-day exploits and fileless attacks that traditional antivirus products might miss.
Additionally, LMNTRIX ‘s approach reduces the need for frequent updates and system scans that can consume network bandwidth and impact system performance. This results in more efficient and effective endpoint protection, better suited to address the complexities of today’s cyber threat landscape.
How does LMNTRIX Endpoint Security work?
How does LMNTRIX work?
LMNTRIX operates by leveraging patented technology designed to safeguard enterprises against a wide spectrum of cyber threats. It employs a multi-vector approach that integrates both pre-execution and on-execution artificial intelligence (AI) technologies.
- Pre-Execution Static AI: Before any file or application is executed, LMNTRIX uses Static AI to analyze it for malicious characteristics. This proactive analysis effectively replaces traditional antivirus applications by detecting and blocking threats before they can initiate any harmful actions.
- On-Execution Behavioral AI: While applications are running, LMNTRIX monitors real-time behaviors using Behavioral AI. This allows the system to detect and respond to anomalous activities associated with sophisticated threats such as fileless attacks, exploits, malicious macros, harmful scripts, cryptominers, ransomware, and other advanced cyber attacks.
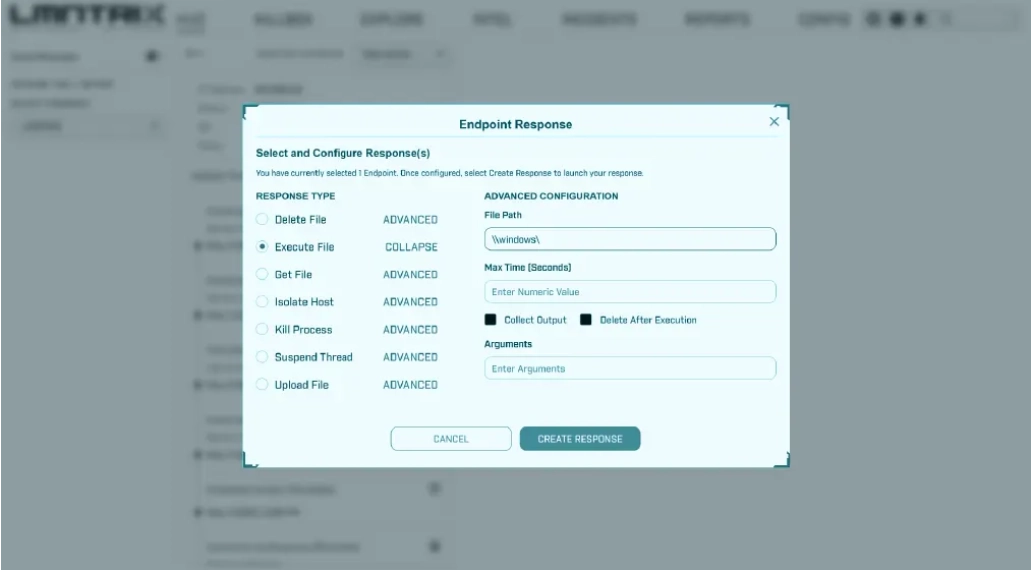
One of the standout features of LMNTRIX is its ability to respond to threats within milliseconds, significantly reducing the dwell time of attacks to nearly zero. The platform offers a comprehensive set of response capabilities, including:
- Alerting: Generating immediate notifications to inform security teams of detected threats.
- Process Termination: Stopping malicious processes before they can cause further damage.
- Quarantining: Isolating infected files to prevent the spread of malware.
- Remediation: Reversing unauthorized changes made by malicious activities.
- Network Isolation: Disconnecting affected devices from the network to contain threats.
- Remote Shell Access: Providing secure remote access for deeper investigation and remediation.
By combining these advanced technologies and rapid response features, LMNTRIX delivers comprehensive protection that adapts to the evolving cyber threat landscape.
What are the top features of the LMNTRIX platform?
The LMNTRIX XDR (Extended Detection and Response) platform offers a suite of advanced features designed to provide robust and comprehensive cybersecurity solutions:
- Advanced Threat Hunting: Utilizing tools like Killbox, LMNTRIX automates the correlation of security events, enabling analysts to quickly identify the root causes of incidents. This reduces investigation times and enhances the efficiency of threat hunting operations.
- Automated and Rapid Response: The platform is engineered to minimize the time an attacker can remain undetected. Automated response capabilities include real-time alerting, process termination, file quarantine, and system rollback to restore compromised data.
- Unified Integration: LMNTRIX consolidates multiple security functions into a single, cohesive platform. This integration provides a future-proof solution that surpasses traditional antivirus software by addressing a broader range of threats across various environments.
- Behavioral AI Technology: Pioneering the use of behavioral AI since 2015, LMNTRIX employs machine learning algorithms to analyze behaviors and detect anomalies in real-time. This enhances the detection of sophisticated threats that may evade signature-based detection methods.
- Scalability and Ease of Use: The platform offers global scalability and user-friendly interfaces, ensuring that organizations can effectively manage security across large and diverse environments without compromising performance.
- Real-Time Cyber Defense: Operating at speeds and scales beyond human capability, LMNTRIX provides instantaneous defense against cyberattacks with higher accuracy than manual efforts.
- Compliance Support: LMNTRIX assists organizations in meeting industry standards and regulatory requirements by supporting various compliance frameworks and providing detailed security documentation.
- Comprehensive Cloud Security: Extending protection to cloud environments, the platform offers endpoint protection, incident response tools, identity detection and response, insider threat detection, attack surface management, and advanced security analytics.
By integrating these features, LMNTRIX delivers a holistic cybersecurity solution capable of addressing modern threats across diverse infrastructures.
Does LMNTRIX protect me while I am disconnected from the internet (such as during traveling)?
Yes, LMNTRIX continues to protect your device even when it is offline or disconnected from the internet. The LMNTRIX agent installed on your endpoint operates independently, utilizing locally stored AI models and analysis techniques to detect and prevent malware threats in real-time without requiring an active internet connection.
However, while the agent maintains protection on the device, the central management console’s ability to monitor and manage that specific endpoint is limited during the period of disconnection. Administrative visibility and certain remote functionalities will resume once the device reconnects to the internet, at which point the agent will synchronize updates and logs with the console.
Is LMNTRIX an antivirus?
LMNTRIX functions as more than a traditional antivirus solution. It is an autonomous cybersecurity platform designed to protect against a comprehensive range of attacks, from common malware to advanced persistent threats (APTs), whether your device is online or offline.
While it fulfills and exceeds the requirements typically associated with enterprise antivirus solutions—validated by industry authorities like MITRE, Gartner, and Forrester—LMNTRIX extends its capabilities beyond basic antivirus functions. It serves as a complete replacement for legacy antivirus, next-generation antivirus (NGAV), and Endpoint Detection and Response (EDR) tools. Additionally, it offers extensive protection across various environments, including endpoints, cloud services, containers, mobile devices, IoT devices, and data assets.
LMNTRIX can operate alongside other security tools if desired, providing flexibility in your security infrastructure while delivering comprehensive prevention, detection, and response capabilities that surpass traditional antivirus software.
How does LMNTRIX differ from other antivirus software?
LMNTRIX distinguishes itself from traditional antivirus software through several key innovations:
- AI-Driven Detection: Unlike traditional antivirus solutions that rely on signature-based detection, LMNTRIX employs advanced artificial intelligence and machine learning algorithms. This enables real-time detection and neutralization of threats, including zero-day exploits and sophisticated malware that signature-based methods may miss.
- Multi-Vector Security: LMNTRIX provides holistic protection across multiple vectors, not just endpoints. It secures cloud workloads, containers, mobile devices, and IoT devices within a unified platform, addressing diverse enterprise security needs.
- Automated Rapid Response: The platform is designed to minimize attack dwell time through automated response features. These include instant alerting, process termination, file quarantine, and system rollback, allowing for immediate remediation without manual intervention.
- Alignment with Industry Frameworks: By mapping its detection and response capabilities to the MITRE ATT&CK® framework, LMNTRIX ensures its strategies align with recognized industry standards, enhancing the effectiveness of threat detection and response.
- Advanced Threat Hunting: Tools like Killbox automate complex tasks such as event correlation and root cause analysis, improving the efficiency and speed of threat investigations.
- Proven Effectiveness: Positive user reviews and industry accolades validate LMNTRIX’s superior performance compared to traditional antivirus solutions, demonstrating its ability to address modern cyber threats effectively.
By integrating these advanced features into a single platform, LMNTRIX offers a comprehensive and future-proof cybersecurity solution that significantly outperforms traditional antivirus software.
Can I use the LMNTRIX platform to replace my current AV solution?
Yes, you can use LMNTRIX to replace your current antivirus solution. It is designed to serve as a complete replacement for traditional antivirus software, offering advanced protection that covers and exceeds the capabilities of legacy systems. If preferred, LMNTRIX can also operate alongside existing security tools, such as Microsoft Defender, providing flexibility during transition periods or in environments where layered security is desired.
Which products can LMNTRIX help me replace?
LMNTRIX XDR can replace several types of security products within your organization’s cybersecurity infrastructure:
- Traditional Antivirus Solutions: LMNTRIX EDR serves as a full replacement for legacy antivirus software with advanced AI-driven protection.
- Next-Generation Antivirus (NGAV) and EDR Tools: LMNTRIX EDR’s integrated detection and response capabilities eliminate the need for separate NGAV and Endpoint Detection and Response tools.
- Network Traffic Analysis (NTA) Tools: LMNTRIX Packets can replace traditional NTA products by providing comprehensive network traffic visibility and analysis.
- Network Visibility Appliances: LMNTRIX Packets can replace devices like Forescout by offering integrated network visibility and device management.
- Network Detection & Response (NDR): LMNTRIX NDR can replace devices such as Fire Eye Network & Email Security appliances, Cisco IDS and Threat Grid and Cisco Umbrella combined, Darktrace, Extrahop or VectraAI.
- Network Forensic Tools: LMNTRIX Packets can replace solutions such as FireEye Network Forensics, RSA Netwitness Packets, and EnCase
- Threat Intelligence Platform (TIP): LMNTRIX Intelligence eliminates the need for FireEye Mandiant Advantage Security Operations, Threat Intelligence, Anomaly, ThreatQuotient and Recorded Future.
- Deception Technology: LMNTRIX Deceive replaces vendors such as Attivo, TrapX, and Illusive Networks.
- Deep & Darknet Intelligence: LMNTRIX Recon offers similar capability to Digital Shadows, SixGill, Intsights, FireEye Mandiant Advantage Security Operations, and Recorded Future.
- Security Information & Event Management (SIEM): LMNTRIX SIEM delivers SIEM, UEBA and Analytics functions in a single platform and is a direct replacement for vendors such as Splunk, FireEye Helix, Exabeam and Securonix.
- Managed Detection & Response: LMNTRIX MDR is far superior to log based for MDR vendors such as FireEye Mandiant Managed Defense, Cisco MDR, Expel, Proficio, ArcticWolf, Rapid7, Sophos and others listed in the Gartner MDR Market Guide.
- Extended Detection & Response: LMNTRIX XDR with 12 native security functions is far superior to EDR and log based XDR vendors such as Microsoft, SentinalOne, CrowdStrike, Sophos, and TrendMicro.
- Dedicated Threat Hunting Platforms: With advanced threat hunting capabilities, it eliminates the need for standalone threat hunting solutions.
By consolidating these functions, LMNTRIX simplifies your security stack, reduces complexity, and enhances overall protection.
Can LMNTRIX protect endpoints if they are not connected to the cloud?
Yes, LMNTRIX is designed to protect endpoints even when they are not connected to the cloud or the internet. The LMNTRIX agent performs both static and dynamic behavioral analyses locally on the endpoint, enabling it to detect and prevent threats without relying on cloud connectivity. When the endpoint reconnects to the internet, the agent synchronizes with the LMNTRIX cloud for updates and to upload logs and events to the central management console.
What detection capabilities does LMNTRIX EDR have?
LMNTRIX EDR employs a multi-layered detection strategy utilizing several advanced engines:
- Reputation Engine: Assesses the trustworthiness of files and processes based on known threat intelligence.
- Static AI Engine: Analyzes files before execution to detect malicious characteristics.
- Behavioral AI Engine: Monitors real-time behaviors of running processes to identify anomalies and malicious activities.
- Active Endpoint Detection and Response (ActiveEDR): Continuously records endpoint activities to detect sophisticated threats through context-aware analysis.
These cascading engines work together to detect and prevent various types of attacks at different stages, providing comprehensive security coverage.
Does LMNTRIX provide malware prevention?
Yes, LMNTRIX offers robust malware prevention. Its Endpoint Protection Platform (EPP) uses Static AI to analyze executable files before they run, replacing the need for traditional, easily bypassed signature-based methods. The platform also examines files like PDFs and Microsoft Office documents for embedded malicious code. By employing on-agent machine learning models, LMNTRIX effectively detects both common and novel malware without relying on large signature databases.
Is LMNTRIX's machine learning feature configurable?
Yes, the machine learning algorithms used by LMNTRIX are directly configurable by customers using 3 available models. The AI models are developed and trained by LMNTRIX’s data science team to ensure optimal performance across all environments. Updates to these models are periodically deployed through agent software updates, eliminating the need for customers to train or customize the AI within their own environments.
Can LMNTRIX detect in-memory attacks?
Yes, LMNTRIX can detect in-memory attacks. By integrating with hardware-based technologies like Intel® Threat Detection Technology (Intel TDT), LMNTRIX gains accelerated memory scanning capabilities. This allows the platform to efficiently identify and respond to malicious activities that occur directly in system memory, which are often missed by traditional security solutions.
Is LMNTRIX a HIDS/HIPS product/solution?
LMNTRIX functions as both a Host-based Intrusion Detection System (HIDS) and a Host-based Intrusion Prevention System (HIPS) by monitoring and protecting individual hosts from malicious activities. Additionally, it extends beyond traditional HIDS/HIPS capabilities by offering Endpoint Detection and Response (EDR), threat hunting, asset inventory, device hygiene monitoring, and other advanced security features, providing a comprehensive security solution.
Is LMNTRIX cloud-based or on-premises?
LMNTRIX XDR is a Cloud-Based (SaaS) solution hosted in the cloud, such as on Amazon AWS.
Does LMNTRIX offer solutions for mobile devices?
Yes, LMNTRIX provides security solutions for mobile devices through the LMNTRIX Mobile agent, which extends advanced threat detection and prevention to iOS, Android and Chromebook devices. Features include Mobile Threat Defense, integration with Mobile Device Management (MDM) solutions, easy deployment, and compatibility with various mobile operating systems. The Mobile Agent complements existing MDM solutions by adding robust security capabilities without replacing current device management tools.
Can LMNTRIX help with securing remote work environments?
Absolutely, LMNTRIX is well-suited for securing remote work environments. The platform offers:
- Remote Shell Access: Secure remote access to endpoints for troubleshooting and management without physical contact.
- Automated Threat Response: Rapid detection and remediation of threats without the need for on-site intervention.
- Centralized Management: Unified policy enforcement and visibility across all remote devices.
- Advanced Threat Detection: AI-driven technologies to protect remote workers from sophisticated attacks.
These features enable organizations to maintain strong security across diverse and dispersed remote workforces.
Does LMNTRIX offer protection against insider threats?
Yes, LMNTRIX provides protection against insider threats through:
- Behavioral Analytics: Monitoring user activities for anomalies and suspicious behaviors.
- Real-Time Alerts: Immediate notification of potential insider threat activities.
- Integration and Automation: Enhanced SOAR capabilities and threat prioritization through integrations.
- Best Practices: Recommendations for robust access control policies, employee training, and fostering a culture of security awareness.
This comprehensive approach helps detect, prevent, and respond to insider threats effectively.
How does LMNTRIX ensure the security of IoT devices?
LMNTRIX secures IoT devices by:
- Continuous Monitoring: Using its NDR, Packets, Deceptions and Endpoint Protection Platform to detect and respond to threats targeting IoT devices.
- XDR Platform Coverage: Extending protection to IoT devices through behavioral AI and unified security management.
- Network Quarantine: Utilizing network containment features to quarantine and prevent communication with unmanaged or unsecured devices.
This multi-faceted approach addresses the unique challenges of securing IoT devices within an enterprise environment.
What kind of reporting features does LMNTRIX offer?
LMNTRIX provides a variety of reporting features, including:
- Monthly Reports: Detailed insights into threats, unmitigated issues, and new agent installations.
- On-demand Reports: Tailored reports based on specific data fields, OS versions, and applications.
- Annual Business Review Meetings: Reports are delivered during annual business review meetings that are designed for executives and stakeholders.
Availability of specific features may depend on your LMNTRIX plan and configuration.
Does LMNTRIX offer any forensics capabilities?
Yes, LMNTRIX offers unlimited DFIR capabilities through our CDC at no extra cost, which allows:
- Automated and Manual Data Collection: Gathering forensic artifacts across the network.
- Auto-Parsing of Artifacts: Extracting meaningful information for analysis.
- Integration with Real-Time Telemetry: Combining forensic data with live telemetry for comprehensive incident understanding.
- Scalability: Conducting DFIR activities efficiently across large environments.
DFIR capabilities are limited to your subscription levels. For example, without LMNTRIX Packets, our network forensics capability will be very limited.
How does LMNTRIX handle false positives?
LMNTRIX manages false positives by:
- Behavioral Analysis: Utilizing AI to accurately distinguish between legitimate and malicious activities.
- Detailed Incident Information: Providing insights into detections to aid in assessment.
- Exclusion Management: Allowing careful creation of exclusions with guidance from LMNTRIX Support.
- False Positive Submission: Enabling customers to submit suspected false positives for review.
- Security Solution Tuning: Offering recommendations to align detection engines with organizational needs.
Consulting LMNTRIX Support is advised for uncertainties or assistance in managing false positives.
Can LMNTRIX detect and prevent supply chain attacks?
Yes, LMNTRIX can detect and prevent supply chain attacks through:
- Advanced AI Detection: Real-time identification of malicious activities stemming from compromised third-party components.
- Automated Response: Immediate actions like quarantining and blocking threats.
- Real-World Effectiveness: Proven ability to thwart supply chain attacks, such as blocking trojanized installers from known software providers.
- Industry Alignment: Mapping to the MITRE ATT&CK® framework to stay ahead of emerging tactics.
- Underground Monitoring: LMNTRIX Recon monitors your supply chains and alerts you of possible breaches that could directly impact your business.
Additionally, LMNTRIX emphasizes best practices like supplier due diligence and robust security controls to mitigate supply chain risks.
How does LMNTRIX protect against malware and ransomware attacks?
LMNTRIX protects against malware and ransomware through:
- Advanced Detection Techniques: Using AI and machine learning to identify both known and unknown threats.
- Auto-Scanning of Removable Media: Scanning external devices to prevent malware introduction.
- Rapid Response: Mandating swift remediation actions to contain threats.
Continuous updates and enhancements ensure LMNTRIX stays ahead of evolving malware and ransomware threats.
How does LMNTRIX's AI technology adapt to new, emerging threats?
LMNTRIX adapts to emerging threats by:
- Continuous Learning: Updating AI and machine learning models to recognize new threat patterns.
- Multi-Vector Approach: Securing various environments to detect threats across different vectors.
- Industry Framework Alignment: Staying aligned with the MITRE ATT&CK® framework for updated tactics and techniques.
- Countering AI-Powered Threats: Detecting sophisticated threats, including those leveraging AI, by identifying unique indicators.
- Innovation and Updates: Investing in research and regularly enhancing the platform’s capabilities.
This dynamic approach ensures LMNTRIX remains effective against the constantly evolving threat landscape.
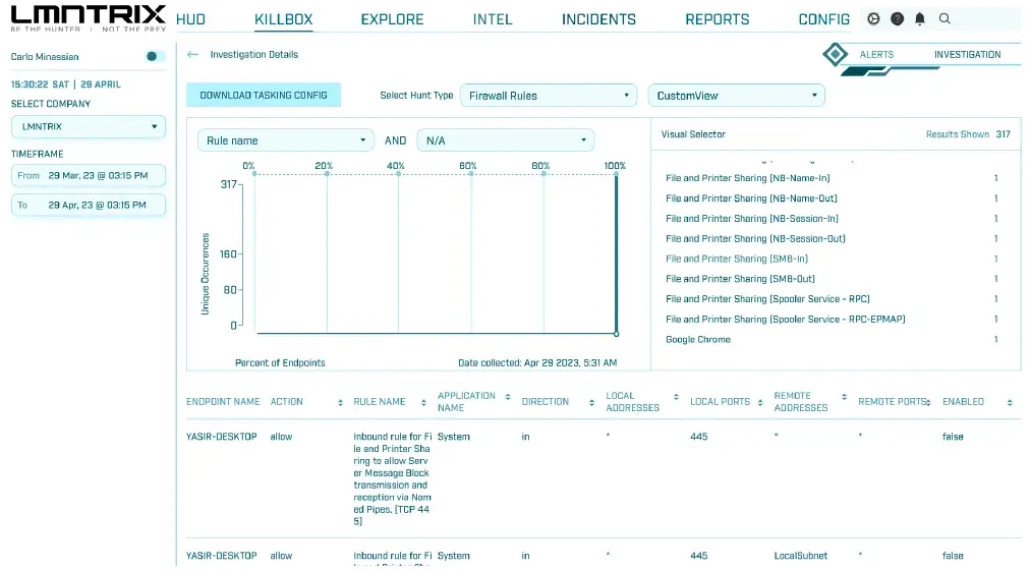
Does LMNTRIX offer any kind of firewall protection?
No, LMNTRIX relies on the built in Windows firewall protection that allows administrators to:
- Manage Endpoint Firewall Settings: Control network traffic to and from endpoints via the management console.
- Define Rules and Policies: Create and apply firewall rules using tags that represent policies.
While there are current limitations on FQDN rules and category-based blocking, LMNTRIX continues to enhance firewall capabilities to meet diverse security needs.
Does LMNTRIX EDR offer any kind of File Integrity Monitoring or DLP protection?
No, LMNTRIX relies on 3rd party solutions for FIM and DLP features. LMNTRIX EDR is exclusively focused on NGAV and EDR functions.
Why ChooseLMNTRIX Endpoint Security?

Related Resources

EDR : Putting The X Factor in XDR
White Paper
How We Protect
small and large enterprises
Why clients love working with LMNTRIX
You’re ready for advanced protection
and that means XDR







Don't just take our word for it...

Leader

Leader

Open Source Excellence

Top 250 MSSP Companies In The World

Users Choice Award
Top Rated Security



Ready to take the next steps with LMNTRIX MXDR ?
The choice is yours: see LMNTRIX in an on demand demo or set up a customized demo or request a quote.