LMNTRIX SIEM™
Reimagining SIEM for a Post-Breach, Cloud-First World
SIEMat the Speed of Light.
LMNTRIX SIEM is purpose-built to support deep forensic investigations, compliance reporting, centralized log retention and specific threat detection use cases—without the performance drag of traditional SIEMs. While legacy SIEM solutions rely on heavy log ingestion and rules-based detection (often generating alert fatigue), LMNTRIX takes a fundamentally different approach.
We prioritize high-fidelity telemetry from our proprietary XDR stack—spanning endpoint, network, cloud, and identity—over generic log data for real-time detection and response. LMNTRIX SIEM is deployed only when needed, ensuring that your security team operates at peak efficiency without the overhead of unnecessary alerts or complexity.
WhyLMNTRIX SIEM?
Post-Breach Visibility Without the Noise
Intelligent Over Traditional
Security-as-a-Service Flexibility
Codified Detection Expertise
KeyCapabilities
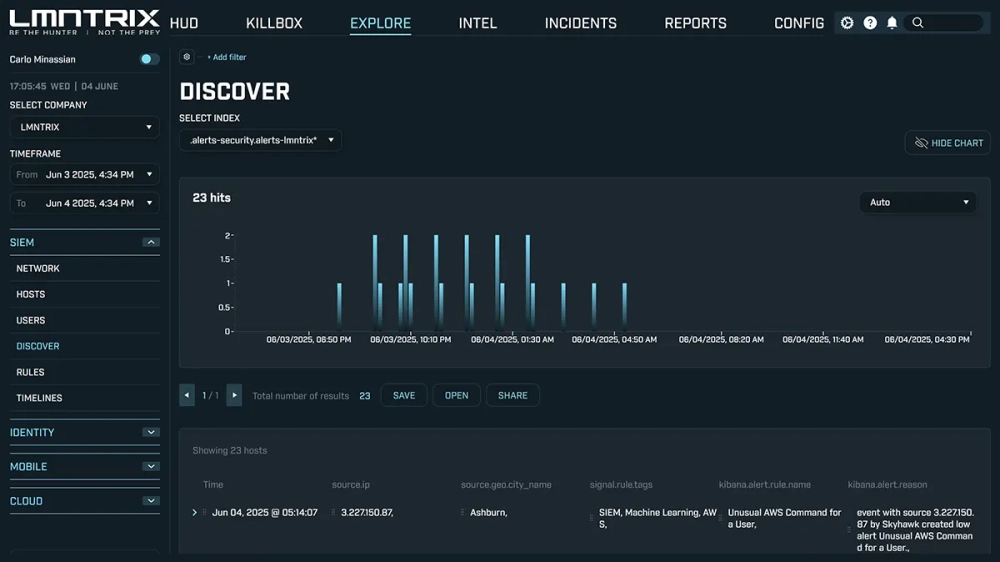
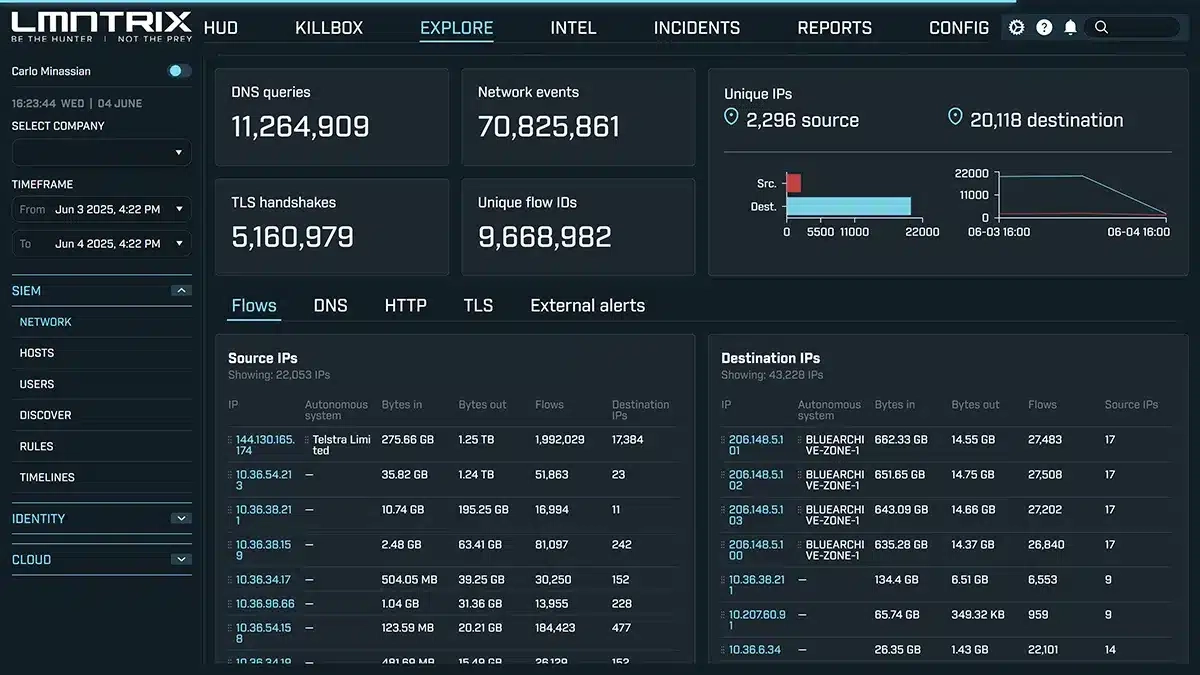
Centralized LogCollection & Correlation
Behavioral Analytics& AI Detection
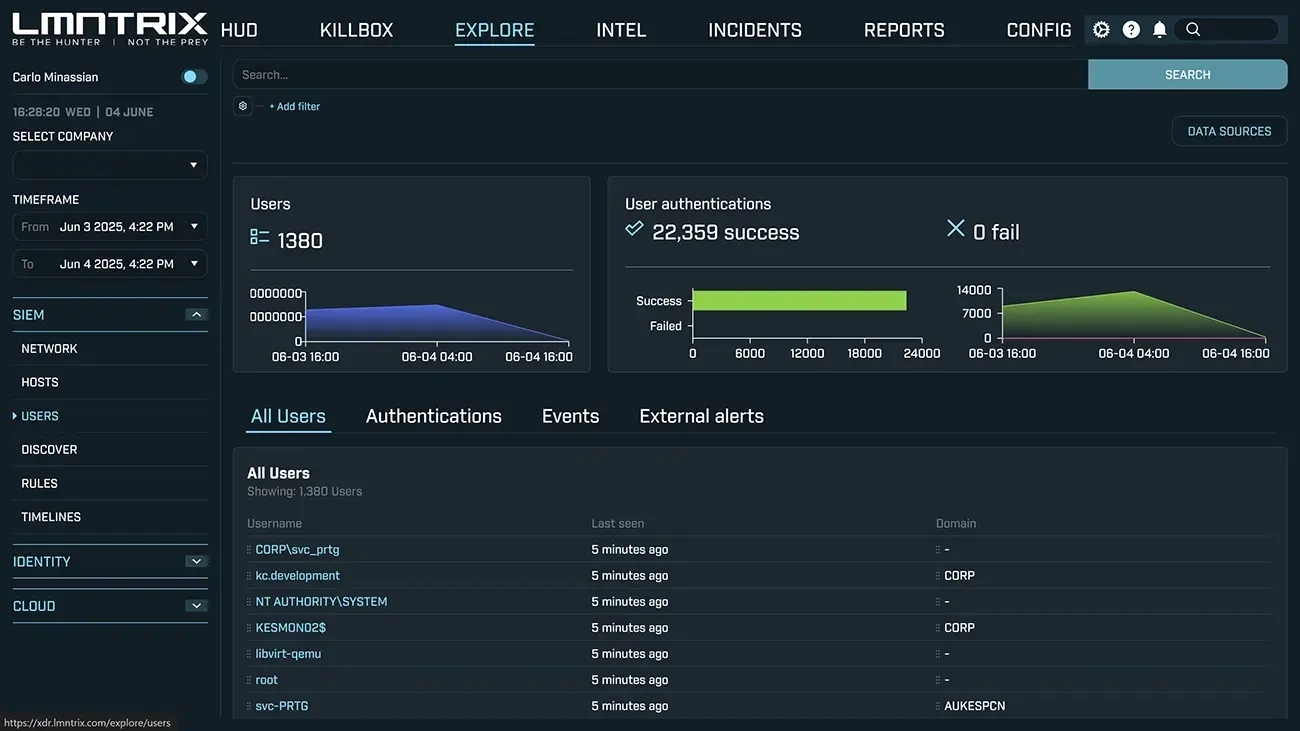
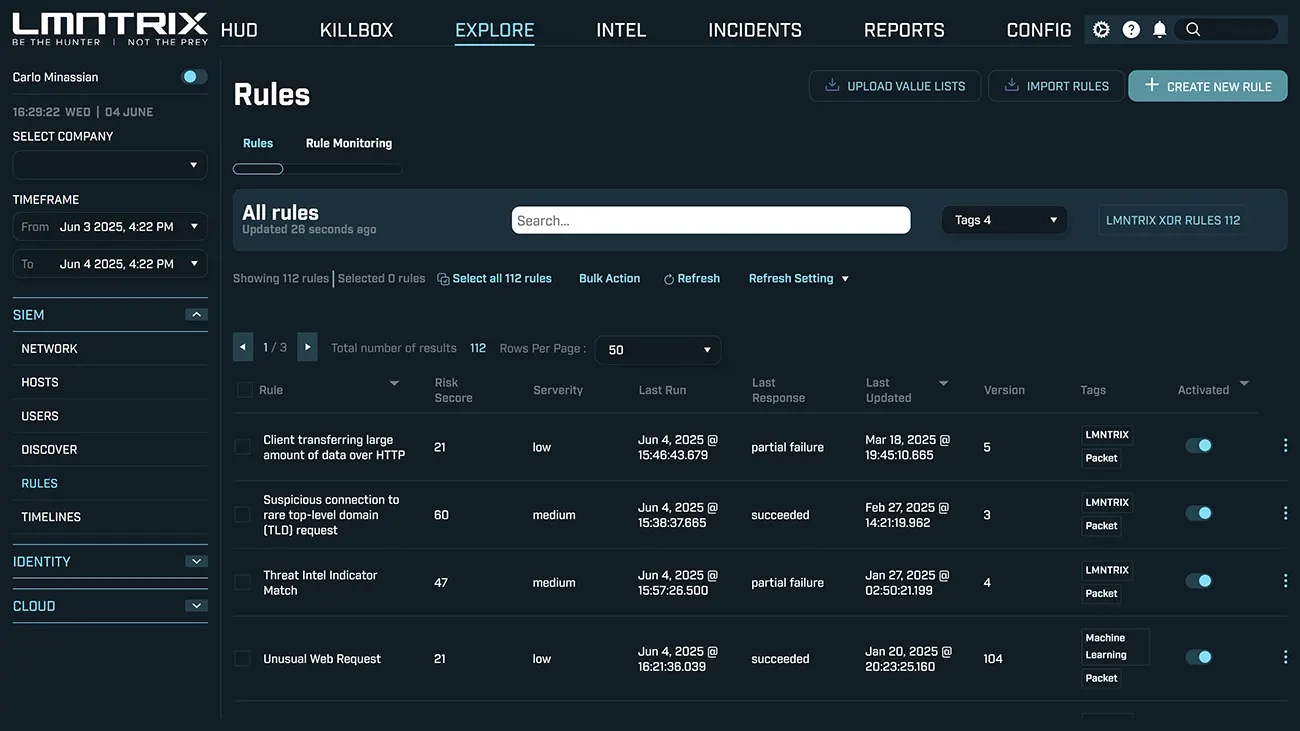
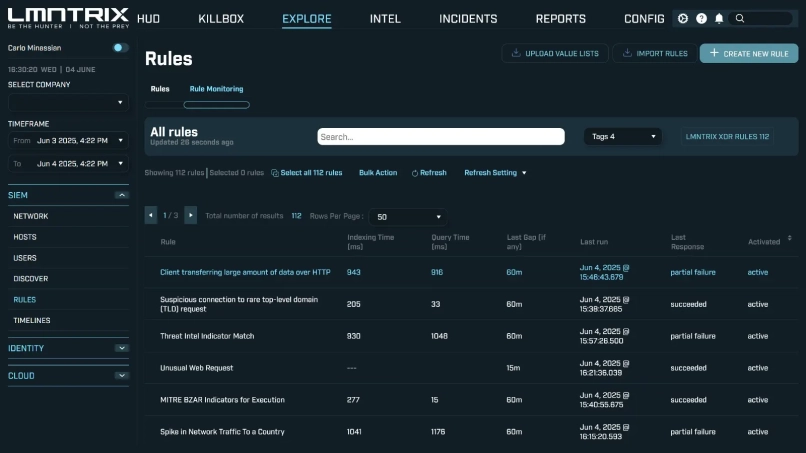
Codified DetectionRules
Deploy preconfigured, MITRE ATT&CK-aligned rulesets or build custom detections tailored to your environment.
Real-TimeDashboards & Visualizations
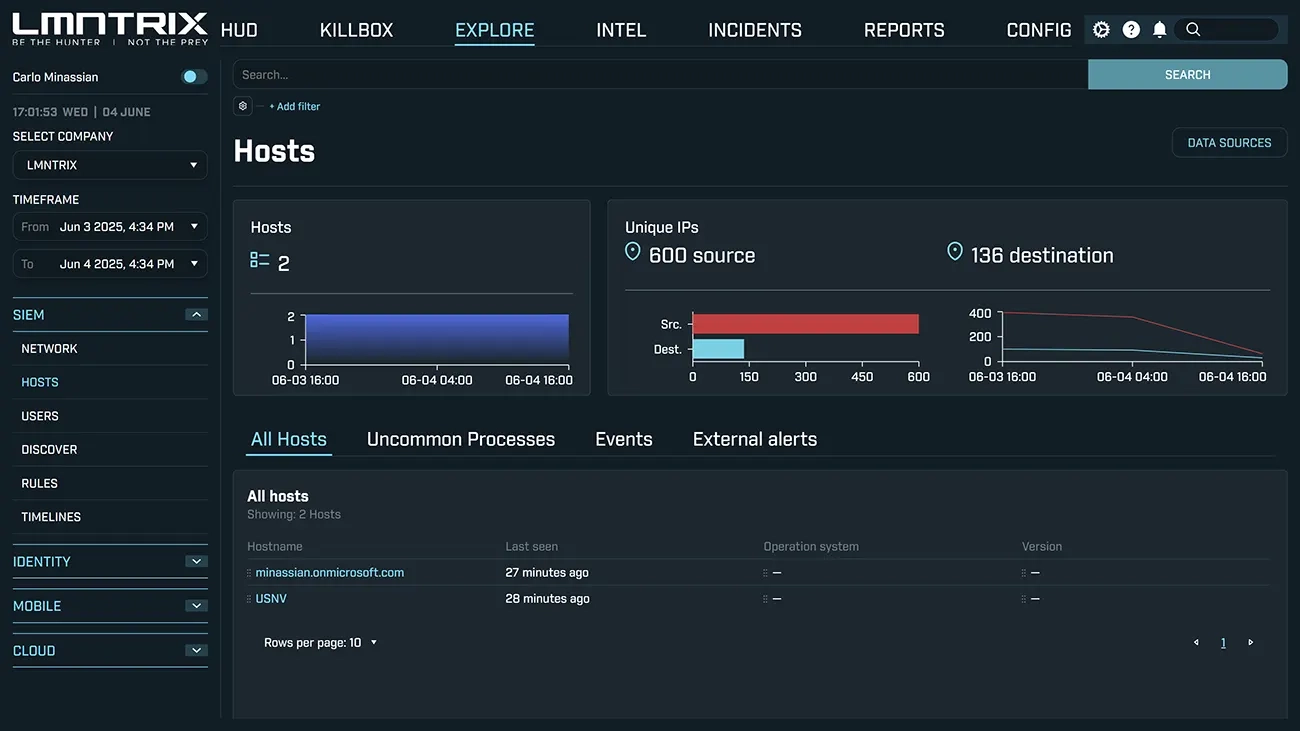
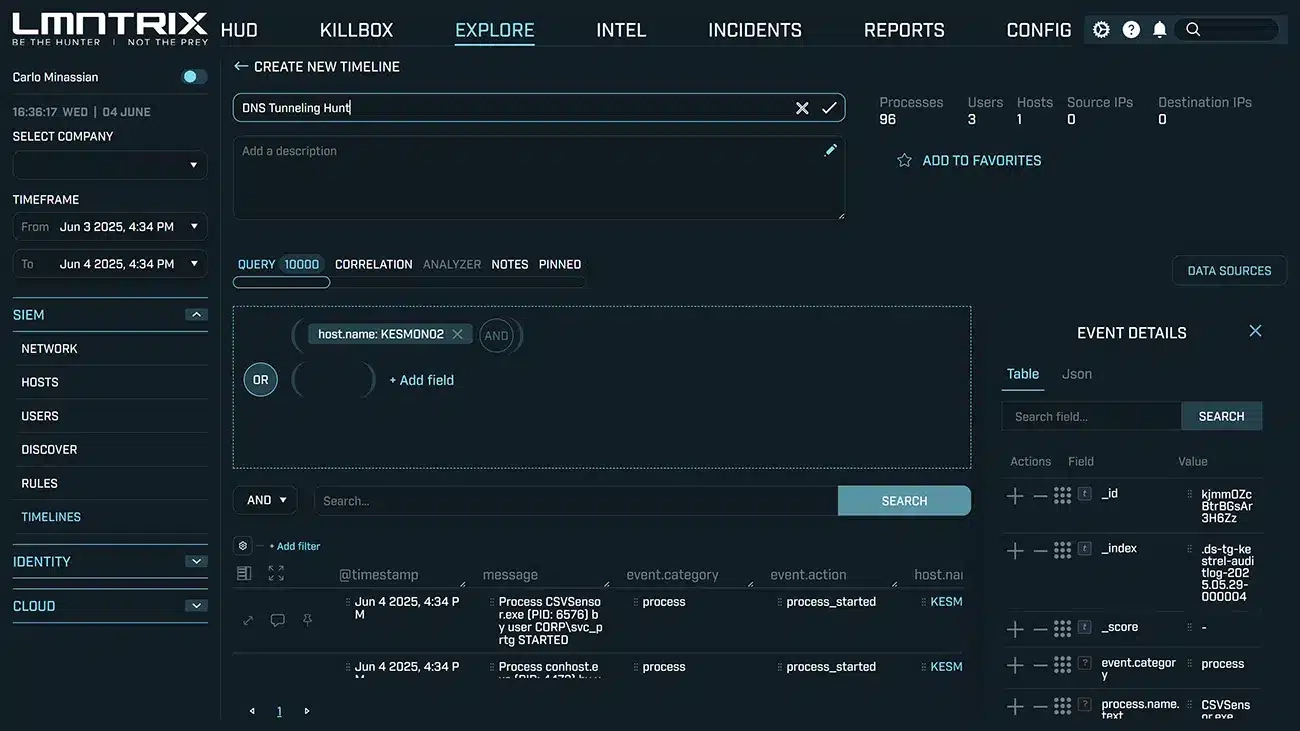
Forensic Search& Sub-Second Querying
Threat Intelligence Integration

Graph-Based Threat Analysis
Uncover hidden relationships between users, events, and devices using our graph analytics engine. See the big picture—instantly.
Scalable Cloud-Native Architecture
Compliance& Audit Support
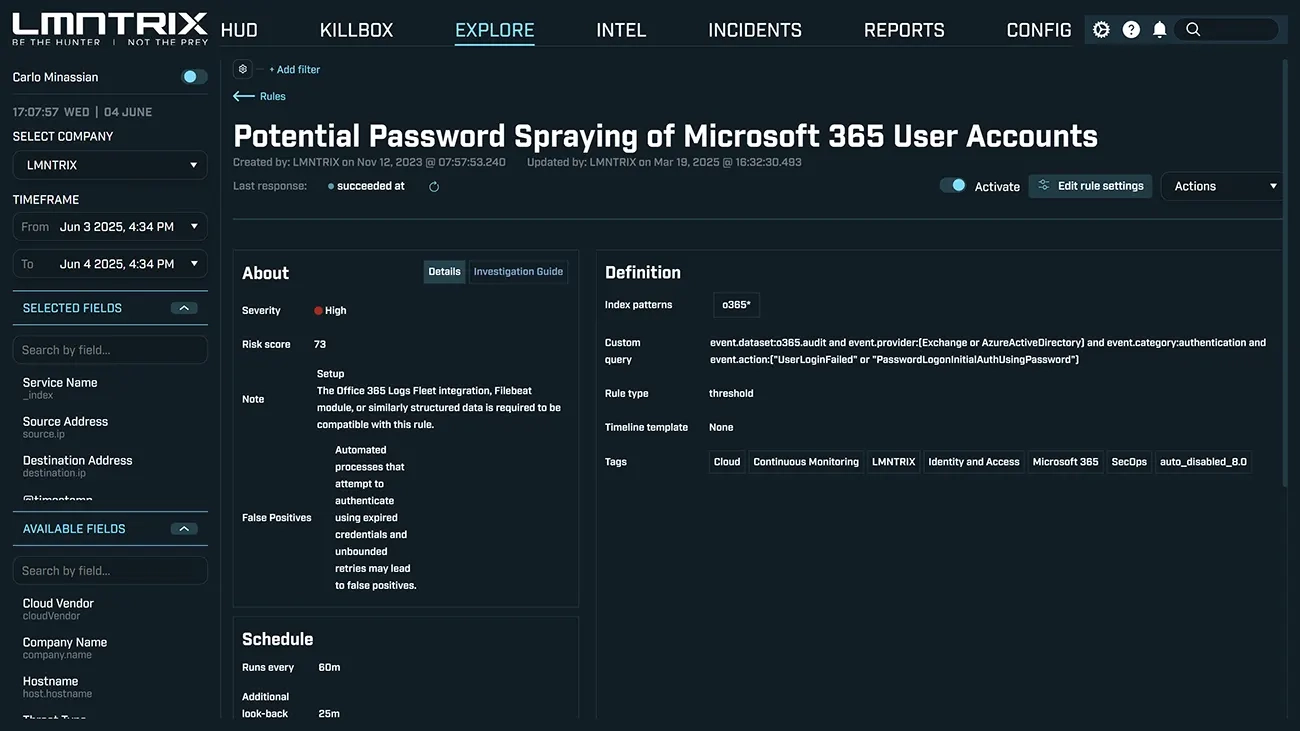
Security Teams Use LMNTRIX SIEM To

Built by Practitioners,Powered by Experience.



Our Integrations
Connect, Collect and Contain with integrations

Use Cases
LMNTRIX Managed Extended Detection & Response
Safeguard your business from cloud to endpoint threats and enhance your security posture with a reliable MXDR partner.
Explore Use Cases (link to Use Cases page)
Compare LMNTRIX

Get Started with LMNTRIX SIEM
Whether you’re replacing a legacy SIEM, need forensic capability on-demand, or require advanced log management for compliance—LMNTRIX SIEM delivers unmatched speed, precision, and scalability.
LMNTRIX SIEM FAQs
LMNTRIX Security Information and Event Management (SIEM)
What is LMNTRIX SIEM?
LMNTRIX SIEM is a subscription feature of LMNTRIX XDR that provides a security solution for monitoring, detecting, and responding to security threats. It’s built on LMNTRIX XDR and integrates data from various sources for comprehensive threat detection and response.
How does LMNTRIX SIEM work?
LMNTRIX SIEM works by collecting, storing, and analyzing security data from logs, events, and metrics across multiple sources in your network. It uses LMNTRIX XDR for indexing, searching visualization and analysis of data. Users can write custom detection rules, use machine learning for anomaly detection, and build dashboards to monitor security events in real-time.
What data sources can LMNTRIX SIEM ingest?
LMNTRIX SIEM can ingest a wide variety of data sources, including logs from network devices, endpoint agents, cloud services, operating systems, and application logs. Commonly used integrations include AWS CloudTrail, Azure, Google Cloud, Zeek, and Sysmon.
How does LMNTRIX SIEM compare to other SIEM solutions?
Yes, LMNTRIX SIEM supports real-time detection. It allows users to configure real-time alerts by writing detection rules and leverages machine learning models to detect anomalies in real-time. This is useful for identifying suspicious activities as they happen and responding swiftly.
Does LMNTRIX SIEM support real-time detection?
In network penetration tests, several attempts are made to exploit security vulnerabilities with the ultimate goal of gaining access to data and systems. These exploit attempts include targeting patching deficiencies, authentication weaknesses, misconfigurations, and even users (via man-in-the-middle attacks). After an initial compromise, post-exploitation activities occur, which typically include privilege escalation, lateral movement, and enumeration of accessible resources to find sensitive data.
How is LMNTRIX SIEM priced?
LMNTRIX SIEM follows a tiered pricing model based on daily data ingestion capacity. Costs are primarily associated with the underlying LMNTRIX XDR (storage and compute resources) as well as any additional premium services such as 24/7 monitoring and incident response. Subscription options can start at 1GB/day to 100+GB/day ingestion.
Can LMNTRIX SIEM handle cloud environments?
Yes, LMNTRIX SIEM is designed to handle multi-cloud environments. It supports ingestion of cloud logs from major providers like AWS, Microsoft Azure, and Google Cloud. Additionally, it provides cloud-native monitoring and security tools to protect cloud workloads.
How customizable is LMNTRIX SIEM?
LMNTRIX SIEM is highly customizable. Users can create custom dashboards, detection rules, and data visualizations to meet specific security monitoring needs. Its open architecture also allows integration with other tools and data sources, making it adaptable for different environments.
What are the key features of LMNTRIX SIEM?
LMNTRIX SIEM offers features such as centralized log management, threat detection and analysis, visualizations, customizable dashboards, pre-built and custom detection rules, and machine learning for anomaly detection. These features make it a comprehensive tool for monitoring security data in real-time and responding to threats.
How does LMNTRIX SIEM leverage machine learning for threat detection?
LMNTRIX SIEM uses machine learning to detect anomalies by establishing baselines for normal behavior across data sources. It can then flag deviations from this baseline as potential threats. For example, it might detect unusual login patterns or data exfiltration attempts. These models can be customized or used out-of-the-box and are continuously updated to adapt to new patterns.
What is the LMNTRIX Common Schema (LCS), and how does it benefit LMNTRIX SIEM?
The LMNTRIX Common Schema (LCS) is a data model that standardizes the way security data is ingested and organized within LMNTRIX XDR and SIEM. LCS makes it easier to correlate data across different sources, providing a unified view of events. This schema ensures consistent field names, which simplifies analysis and allows for more effective searches and visualizations.
How does LMNTRIX SIEM support event sources not supported out of the box?
LMNTRIX offers parser development at no extra cost for all LMNTRIX SIEM clients. Parser development can take anywhere from few days to few weeks to complete depending on the complexity of the event source.
How does LMNTRIX SIEM handle data storage and scalability?
LMNTRIX SIEM is built on the LMNTRIX XDR platform, which is designed for scalability. It handles large volumes of data by distributing it across clusters. This makes it suitable for organizations of various sizes, from small businesses to large enterprises. LMNTRIX’s architecture allows for horizontal scaling, which means adding more nodes to increase capacity.
What are the deployment options for LMNTRIX SIEM?
LMNTRIX SIEM is offered as a cloud-based SaaS subscription inclusive of platform operations and maintenance. Optional SIEM alert monitoring and incident response is available from LMNTRIX or one of our certified partners.
How long does LMNTRIX SIEM retain our data?
The standard configuration of LMNTRIX SIEM retains data online for 90 days and archived for 9 months. This gives clients access to a total of one year data. Additional online and archive capacity is available on request.
How does LMNTRIX SIEM integrate with other LMNTRIX XDR tools?
LMNTRIX SIEM is fully integrated with the LMNTRIX XDR, including for search and storage, visualization, containment, incident management and for data ingestion. This integration allows users to build a seamless workflow for collecting, processing, storing, and analyzing security data in one unified platform.
Does LMNTRIX SIEM provide alerting capabilities?
Yes, LMNTRIX SIEM offers alerting features through LMNTRIX XDR, allowing users to set up alerts based on custom rules. These alerts can be sent to various channels, such as email, Slack, or custom webhooks. Additionally, alerting rules can be configured to trigger responses based on specific threat indicators, enabling faster remediation.
What types of organizations benefit most from using LMNTRIX SIEM?
LMNTRIX SIEM is particularly beneficial for medium to large enterprises with complex IT infrastructures and multiple data sources. It is also suitable for organizations that need a scalable, flexible, and customizable security solution that can aid in compliance reporting and post breach forensics and incident response.
How can LMNTRIX SIEM assist with compliance requirements?
LMNTRIX SIEM provides auditing capabilities and data retention options that help organizations meet compliance requirements for standards like GDPR, HIPAA, and PCI DSS. Its ability to store and analyze logs, along with its alerting and reporting functions, can support compliance audits and investigations by tracking and documenting security events.
What support options are available for LMNTRIX SIEM?
The standard subscription to LMNTRIX SIEM includes 24/7 support. This provides clients 24/7 access to LMNTRIX’s cyber defense centre, security updates, and guidance for deployment, configuration, and optimization.
How does LMNTRIX SIEM handle threat intelligence?
LMNTRIX SIEM standard configuration includes integration with LMNTRIX Intelligence which is made up of over 300 threat feeds from open source, commercial and our own sensor network. LMNTRIX SIEM can also integrate with threat intelligence feeds, such as open-source feeds or commercial threat intelligence platforms. Users can ingest threat data to enrich their security logs with additional context, such as IP reputation, and correlate events against known threat indicators for enhanced detection capabilities.
Does LMNTRIX SIEM support multi-tenancy for MSSPs?
Yes, LMNTRIX SIEM supports multi-tenancy features, making it suitable for Managed Security Service Providers (MSSPs). MSSPs can manage multiple client environments within a single LMNTRIX deployment while maintaining data segregation and security.
What are LMNTRIX SIEM’s capabilities for endpoint security?
LMNTRIX SIEM can collect events from any 3rd party endpoint security solution and it integrates with the LMNTRIX EDR, which provides endpoint detection and response (EDR) capabilities. This agent enables real-time monitoring of endpoint activities, such as process creation, file access, and network connections. LMNTRIX SIEM can use this data to detect malicious behaviors and respond to endpoint threats.
How does LMNTRIX SIEM handle data ingestion and parsing?
Data ingestion in LMNTRIX SIEM is facilitated by LMNTRIX Data Shippers (LDS), which collect and parse data from various sources. LDS are lightweight data shippers for specific log types, which also offers advanced filtering and transformation. LDS allow LMNTRIX to standardize data formats and enrich logs before storing them in LMNTRIX XDR.
What are some common use cases for LMNTRIX SIEM?
LMNTRIX SIEM is used for various security purposes, including network monitoring, threat hunting, insider threat detection, anomaly detection, and compliance monitoring. It is also useful for centralized log management, where it collects logs from multiple sources for unified analysis and rapid incident response.
How customizable are the detection rules in LMNTRIX SIEM?
Detection rules in LMNTRIX SIEM are highly customizable. Users can build custom rules based on their unique security needs and specific environments. LMNTRIX provides a detection rule builder that allows analysts to specify conditions, thresholds, and alerting actions, which enables tailored detection capabilities.
Does LMNTRIX SIEM support automated response actions?
Yes, LMNTRIX SIEM can trigger automated response actions through integrations with SOAR platforms or by using custom webhooks to initiate responses. For example, it can send an alert to an orchestration tool that automates actions like blocking an IP, disabling a user account, or isolating a compromised endpoint.
What are some limitations of LMNTRIX SIEM?
While LMNTRIX SIEM is powerful and flexible, some limitations include:
- Steep Learning Curve: It may require a solid understanding of the LMNTRIX XDR to set up and maintain effectively.
- Custom Configuration: Out-of-the-box functionality may not be sufficient for some users, necessitating significant customization.
- Data Volume Costs: High data ingestion volumes can lead to increased costs due to storage and compute requirements, especially in large environments.
Related Resources

2025 SIEM Buyer's Guide
Whitepaper
XDR BUYER'S GUIDE FOR THE MODERN SOC
Whitepaper
How We Protect
small and large enterprises
Why clients love working with LMNTRIX
You’re ready for advanced protection
and that means XDR







Don't just take our word for it...

Leader

Leader

Open Source Excellence

Top 250 MSSP Companies In The World

Users Choice Award
Top Rated Security



Ready to take the next steps with LMNTRIX MXDR ?
The choice is yours: see LMNTRIX in an on demand demo or set up a customized demo or request a quote.