LMNTRIX Recon™ — Deep & Dark Web Monitoring
Proactive Threat Visibility Beyond the Perimeter
In today’s threat landscape, your organization’s greatest risks may already be exposed — not inside your network, but outside of it. LMNTRIX Recon empowers you with unmatched visibility into the deep and dark web, identifying threats before they escalate into breaches.
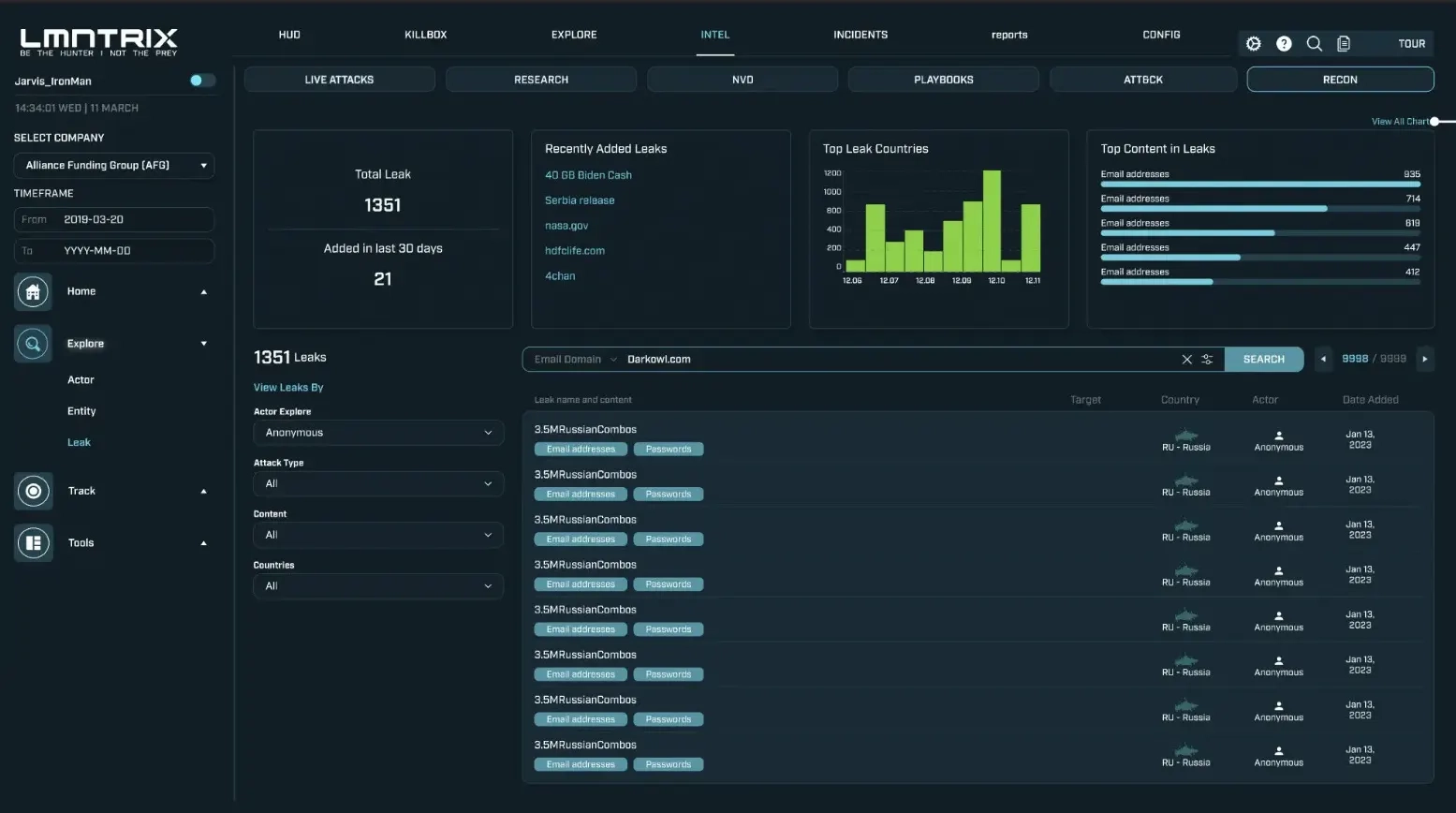
LMNTRIX Recon is a next- generation external threat monitoring service purpose-built to detect and alert on sensitive data exposures, stolen credentials, adversarial intent, and digital risks that lie beyond traditional security perimeters. By combining automated intelligence with analyst- driven validation, Recon provides actionable, context-rich insights into cybercriminal activity targeting your brand, employees, partners, and customers.
Operating across forums, marketplaces, social channels, and hidden networks (Tor, I2P, IRC), LMNTRIX Recon delivers early warnings of data leaks, phishing infrastructure, and threat actor interest — allowing you to take swift, informed action before damage is done.
Why LMNTRIX Recon?

Zero False Positives
Zero Excuses
Recon delivers what others don’t: verified, relevant, and deep threat intelligence.
360° Visibility
CoreCapabilities
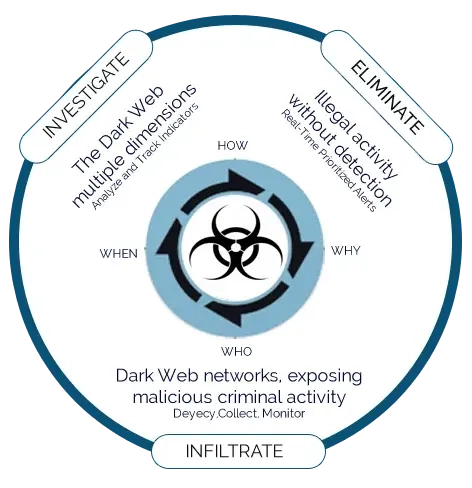
Deep & DarkWeb Monitoring
Credential LeakDetection
Brand & Domain Protection
Detection of phishing sites, lookalike domains, and impersonations
Third-Party RiskVisibility
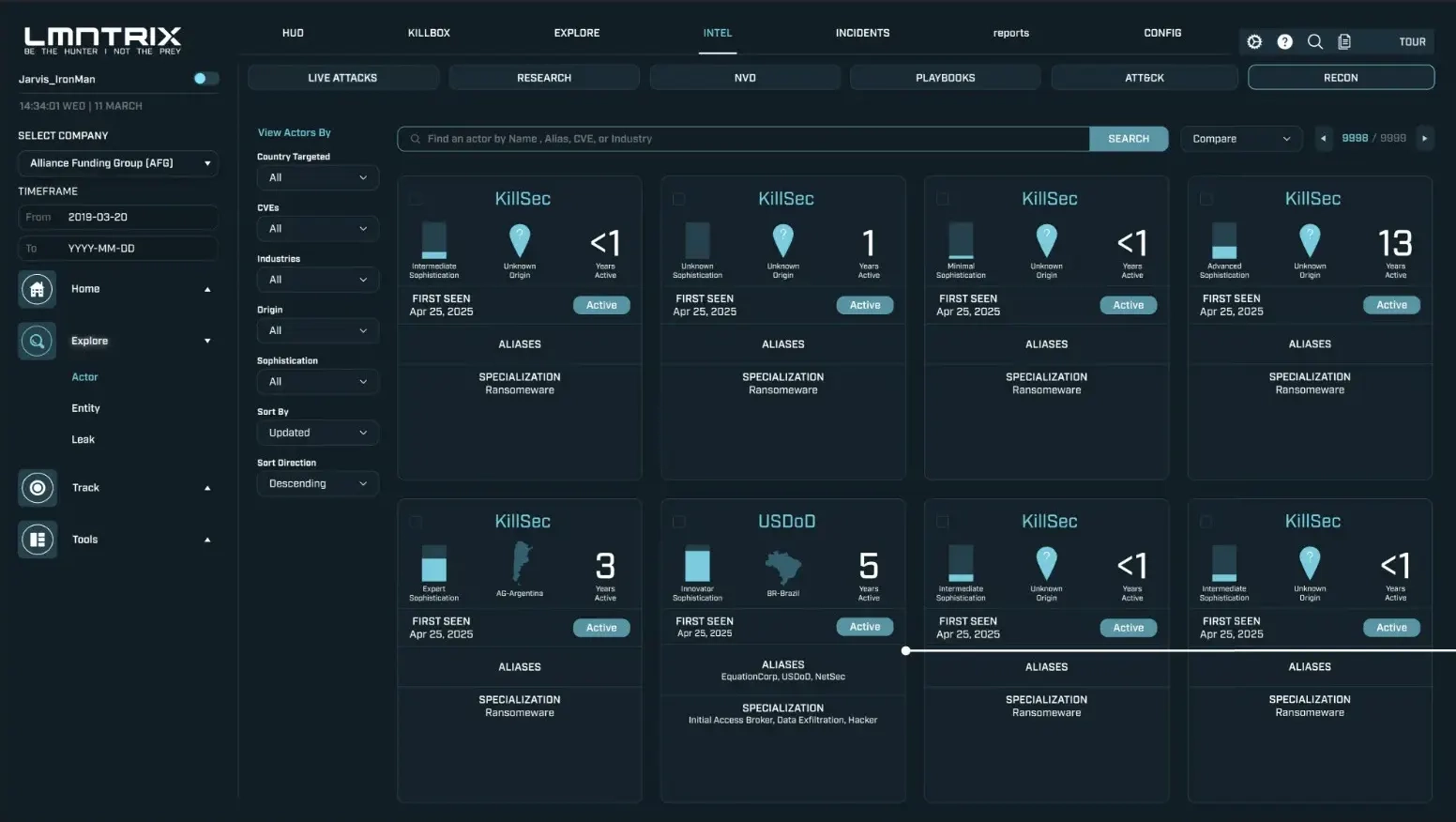
Threat ActorMonitoring
Discover adversarial interest before attacks happen:
Actionable IntelligenceAlerts
Delivered through the LMNTRIX XDR
Key Use Cases
Early Warning System for data theft, attack planning, and VIP impersonation
Supply Chain Intelligence to spot risks in connected entities
Cyber Insurance Readiness and regulatory compliance support
Brand & Reputation Management through proactive monitoring
Security Awareness & Policy Enforcement for HR and executive protection

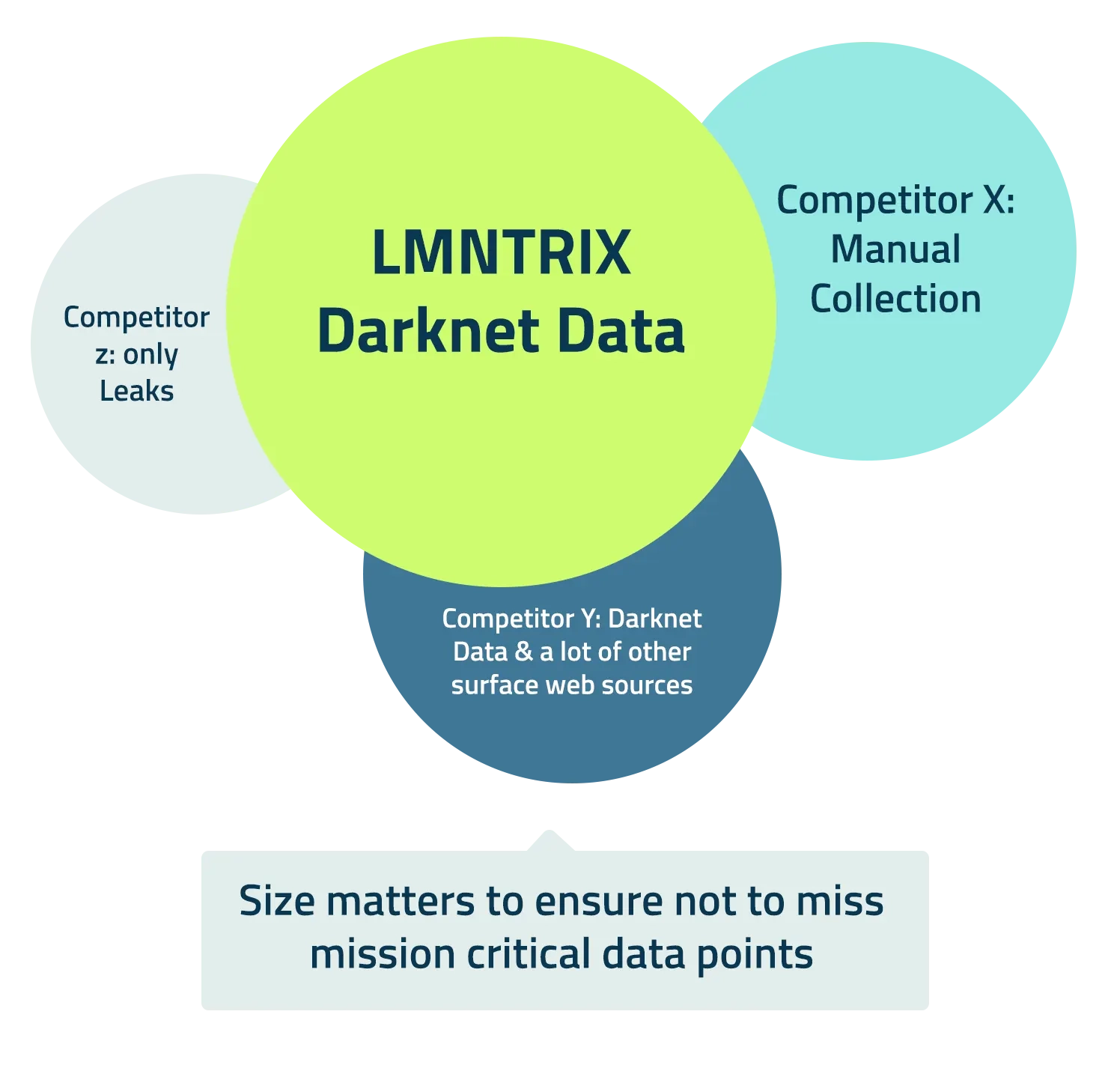
Our Approach: Intelligence Meets Innovation
99.9%
uptime
47
8x
Faster search efficiency
Recon Subscription Tiers
| Tier | Keywords Monitored | Monthly Queries | Ideal for |
|---|---|---|---|
| Basic | 5 | Upto 10 | Small teams or pilot deployments |
| Basic+ | 20 | Upto 40 | SME threat coverage |
| Bronze | 50 | Up to 100 | Mid-market organizations |
| Silver | 150 | Up to 300 | Enterprises |
| Gold | 250 | Up to 500 | Large/global organizations |
| Platinum | Unlimited | Unlimited | Highly targeted industries |
Architecture & Incident Flow
Detect
Analyze
Respond
Client Readiness
Recon in Numbers
16 Billion
Email addresses indexed
900+ Million
250 Million
13 Million
Over 1 Million
Compromised IPs discovered daily
900+ million documents, upto 15 million added daily
665,017,716
Unique TOR Pages
307,067
IRC Records
1,000,600
FTP & OpenNIC Records
6,939,244
Unique I2P & Zero Net Pages
665,017,716
Telegram Records (across 600+ groups)
9,298,939
Data Leakrecords
382,413
3,497,572
Authenticated Site pages
16 Billion
Email Addresses
25 Million
Crypto-wallets
9 Million
Credit Cards
2 Million
Social Security Numbers
LMNTRIX Recon FAQs
LMNTRIX Recon
What is LMNTRIX Recon?
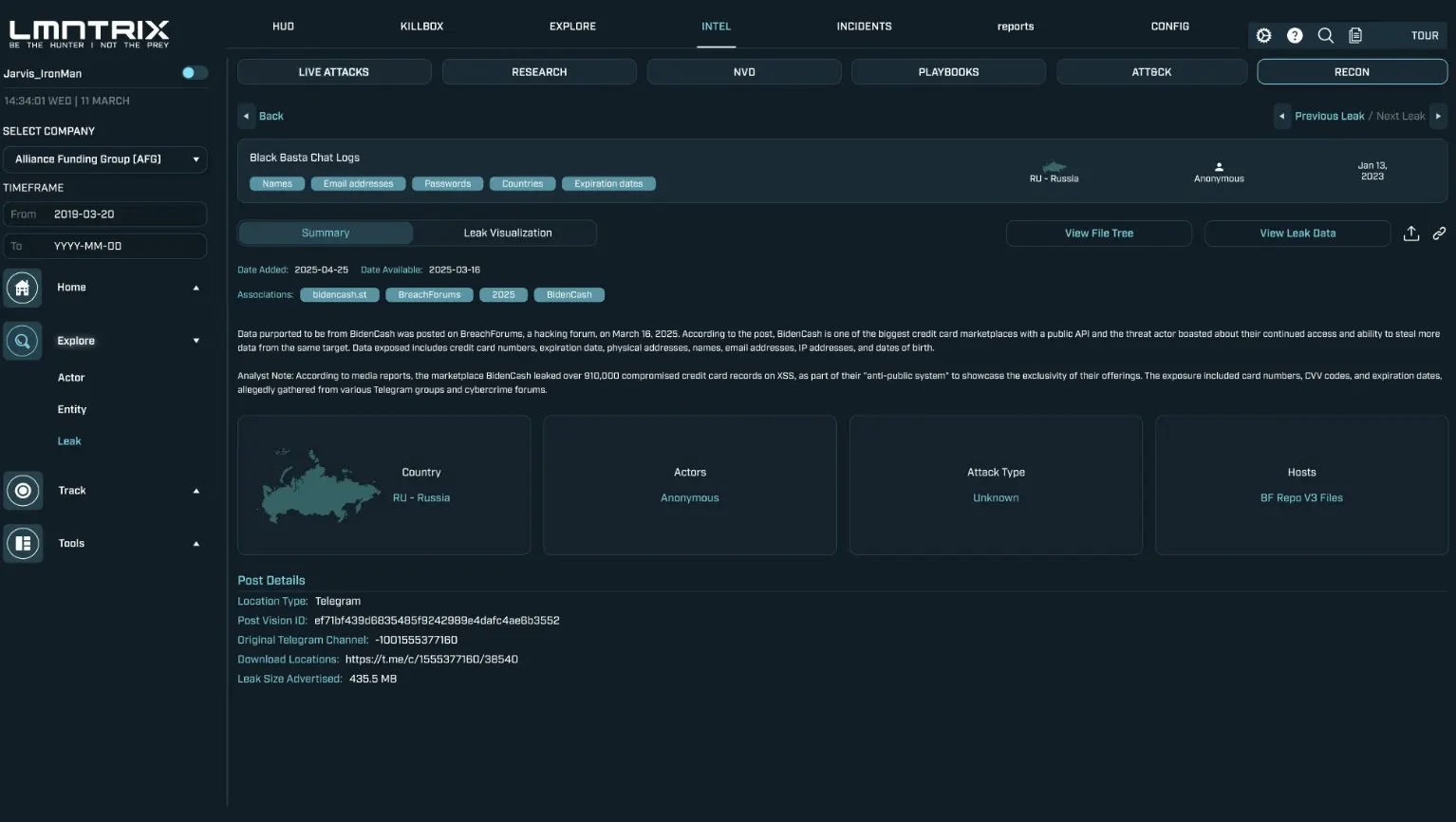
LMNTRIX Recon is a subscription feature of LMNTRIX XDR that delivers powerful early warnings of hacking and fraud attacks via a sophisticated cyber intelligence platform. Scanning a wide range of sources (e.g. deep and dark web, cyber-crime forums, IRC channels, social media, app stores, paste sites), it provides near-real-time alerts about cyber-threats.
By converting security intelligence into actionable data, the LMNTRIX Recon enables our Customer’s to detect unknown threats and minimize their dangerous exposure.
LMNTRIX Recon also provides an option for an upfront 2-day Quick Scan or a thorough 15-day Exposure Analysis to help baseline the Client’s threat exposure to the deep and dark web prior to initiating the monitoring service.
We identify your data as it accesses criminal command-and-control servers from multiple geographies that national IP addresses cannot access
What outcome does a subscription to LMNTRIX Recon provide?
- Deep and Dark Web Threat Alerting: Proactive and automated monitoring for your organizations stolen or compromised data and alerting you when data is
- Compromised Data Tracking, Incident Response & Reporting: Track and triage incidents and better manage risk.
- Holistic Threat Intelligence Program Development.
- Compromised Data Trending & Peer/Industry Benchmarking: Gain insight into your organization’s current threat posture while benchmarking it against your peers and the industries that you serve.
- HR and Policy Enforcement – Cyber Education & Awareness.
- Targeted Individual and Repeat Offender Monitoring.
What are the subscription levels to LMNTRIX Recon?
LMNTRIX Recon offers two subscription levels:
1- Basic: Provides monitoring for credentials exposure only. I.E. usernames and passwords
2- Premium: Provides monitoring for all data types in multiple languages including HUMINT. This includes the following exposure types:
i. Credentials
ii. Personas
iii. Breaches
iv. Physical
v. Source Code
vi. Hacktivism
vii. Botnets
viii. Vulnerabilities
b. Legal & Compliance
i. Mobile Apps
ii. Employees
iii. Data Loss
iv. Publicly Identifiable Information (PII)
c. Reputation & Revenue Loss
i. Product Information
ii. Contracts
iii. Brand Abuse
iv. Brand
v. Executive Profiles
The LMNTRIX Recon Premium subscription level offers six (6) service levels to select from:
| Service Level | Total Number of Keywords | Total Number of Queries per Month |
| Basic | 5 | Up to 10 |
| Basic+ | 20 | Up to 40 |
| Bronze | 50 | Up to 100 |
| Silver | 150 | Up to 300 |
| Gold | 250 | Up to 500 |
| Platinum | Unlimited | Unlimited |
What are the use cases or actionable intelligence delivered by LMNTRIX Recon?
The following are the uses cases for LMNTRIX Recon:
Internal Operations & Management
- Holistic Threat Intelligence Program Development
- Proactive & Automated Security Management
- High Value Target (HVT) Monitoring
- Targeted Individual and Repeat Offender Monitoring
- Reduce Incident Response Times
- Policy Enforcement
- Cyber Education & Awareness
- Identify trends and potential exposure points within your supply chain
- Share threat intelligence and support corporate supply chain management and security policies
- Understand how your organization’s threat posture compares to your industry peers and competitors
- Demonstrate a comprehensive approach to loss prevention and educate through the deployment of external security monitoring services
How does LMNTRIX Recon work?
We monitor the following 24/7, 365 days a year:
- Hidden Criminal Chat Rooms (280 forums)
- Private Websites
- Peer-to-Peer Networks
- IRC (Internet Relay Chat) Channels
- Social Media Platforms
- Black Market Sites
- 640,000+ botnets
On average, we identify and report on more than 1 million compromised IP addresses and more than 80,000 compromised emails every day.
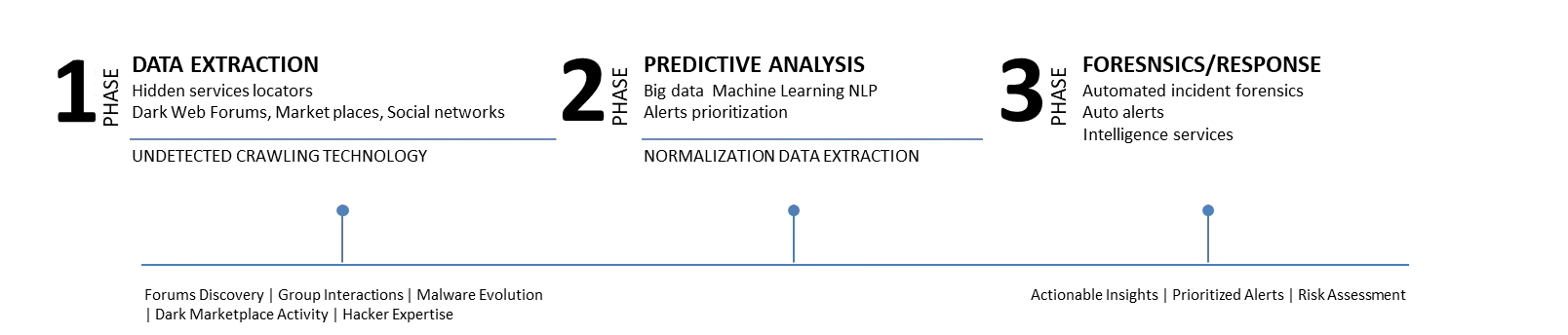
- Detect – LMNTRIX Recon constantly scans a wide range of sources for threat intelligence across the deep, and dark web. It also uses existing search engines to gather additional valuable information (“piggybacking”). All this data is gathered by a proprietary browsing solution that overcomes obstacles in the dark web i.e. anti-bot technologies and stores it on the LMNTRIX XDR.
- Analyze – LMNTRIX Recon analyzes, categorizes, and prioritizes cyber threats in real time using proprietary, patent-pending data mining algorithms and unique machine learning capabilities to focus intelligence on what is important to you.
- Respond – After ensuring relevancy and existence of a cyber threat, the information goes through a false positive assessment and classification process by our intrusion analysts before an incident ticket is created and escalated to the Client.
Note: LMNTRIX Recon does not provide any remediation services, as we only provide monitoring for the deep & dark web (not clear web).
What type of threats or incidents does LMNTRIX Recon produce?
LMNTRIX Recon delivers the following types of incidents:
- Attack indications – Hackers use websites, forums, and social media to plan and coordinate attacks. Our system detects and alerts you of these plans that are found through the cyber-space, e.g. the company name in target lists, or a bid for attacking the company in hackers’ forums.
- Data Leakage – Secret data often leaks from the organization. Leaks can happen from hackers who penetrated the organization, or even frustrated or careless employees. Even the most advanced DLP can’t provide 100% certainty about data safety. Our system finds your leaked secret data and lets you know, giving you a chance to protect yourself from it being used in future attacks, e.g. credentials that might be used for logging in to your employees’ accounts, secret documents about the company’s projects, information about the company’s internal network.
- Brand Security – Social media has become an important arena for branding, marketing and communicating with Customer’s. Many hackers create and manage fake accounts and applications to seduce innocent Customer’s and steal their personal data and even hurt your company’s reputation. Our system detects and alerts you about imitating fake pages, profiles, applications, and even posts aimed at hurting your reputation.
- Phishing – One of the most common social-engineering attacks is phishing, done by spear-phishing e-mails or phishing sites. In order to execute this attack, the hacker must first open a fake domain to host the phishing site or send the spear phishing e-mail. Our system offers early detection for potential phishing domains soon after registration, and allows you the time to prepare and prevent the attack.
- Exploitable Data – Our unique methodology allows us to detect and report about information indexed by search engines that is exploitable by hackers. High-level hackers find this information and use it to piece together sophisticated cyber-attacks. Examples include published web vulnerabilities, information about your internal confidential network, databases, and software used –including exact version numbers.
- VIP Protection – Your company’s VIPs are some of your most important assets. Holding the most valuable experience and sensitive data about the company, their protection is high priority. Our system detects and alerts you about potential attacks on your VIPs, secret data that leaked from a VIP (e.g. secret documents, passwords), and fake VIP profiles in social media and other websites.
What are client responsibilities for onboarding LMNTRIX Recon?
Customer is responsible for completing the data collection sheet with accurate information about their business and respected keywords that are to be used during the deep & dark web monitoring service.
These include: products, assets, supply chain, company name(s), domain name(s), IP ranges, executive profiles, publicly identifiable information, source code, etc that they would like monitored.
Related Resources

SOC Modernization & the Role of XDR
Presentation

How to Select an MDR Provider
Whitepaper
How We Protect
small and large enterprises
Why clients love working with LMNTRIX
You’re ready for advanced protection
and that means XDR







Don't just take our word for it...

Leader

Leader

Open Source Excellence

Top 250 MSSP Companies In The World

Users Choice Award
Top Rated Security



Ready to take the next steps with LMNTRIX MXDR ?
The choice is yours: see LMNTRIX in an on demand demo or set up a customized demo or request a quote.