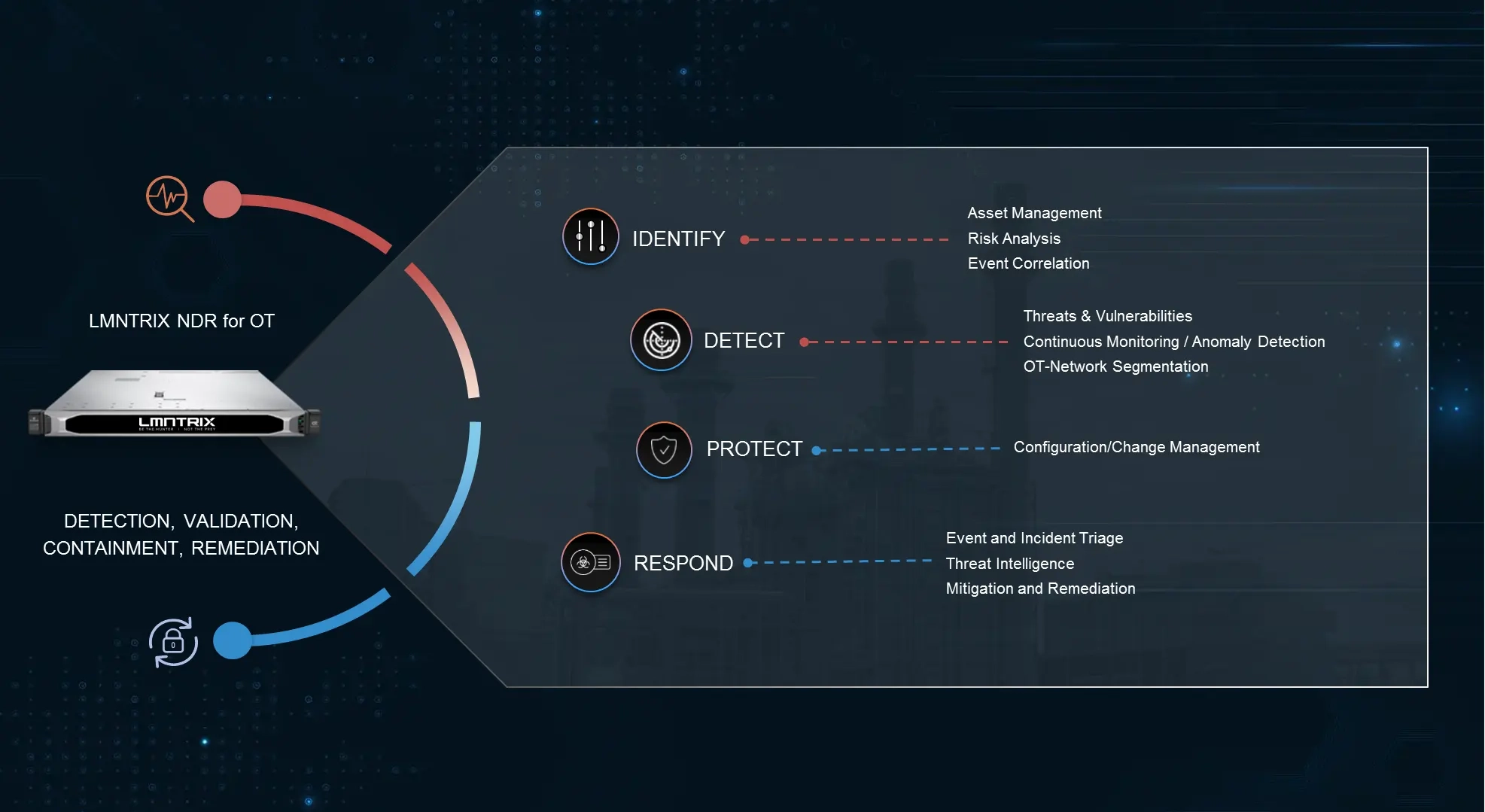
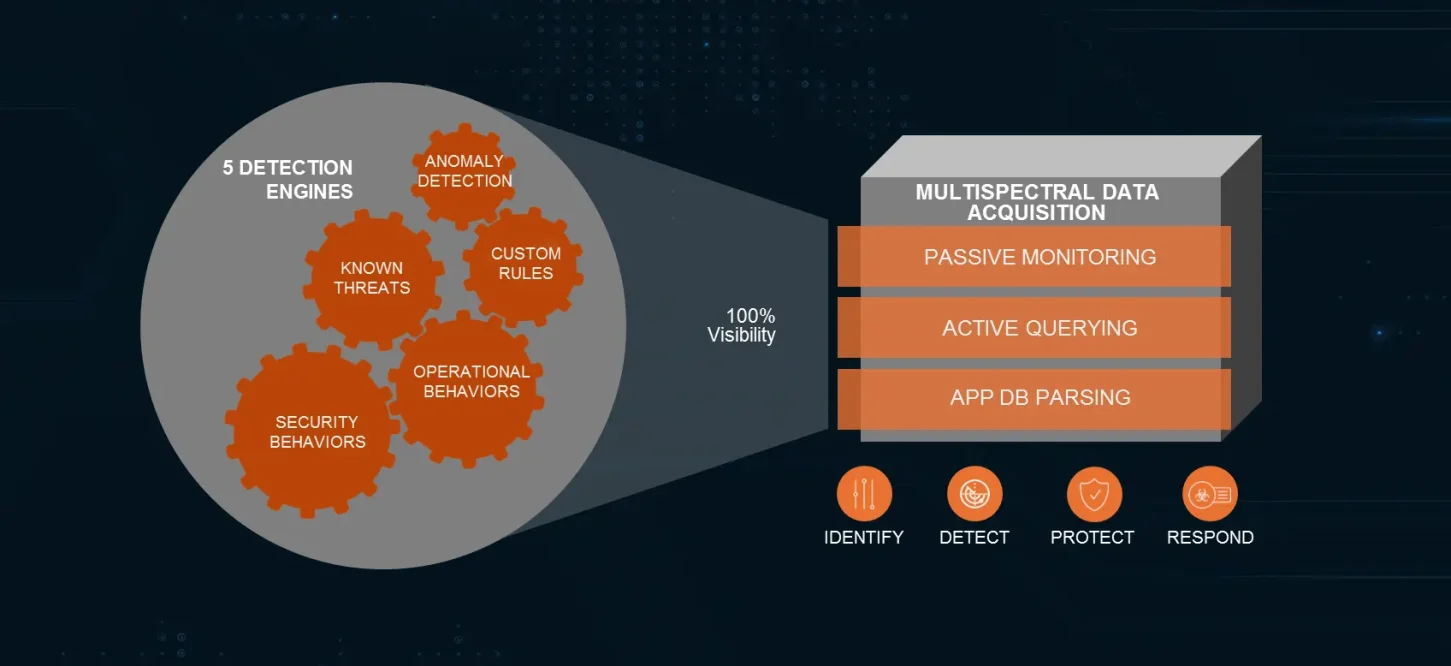
LMNTRIX OT — Operational Technology Security
Protecting What Runs the World: Your Industrial Infrastructure
Critical infrastructure is under siege—from ransomware gangs to nation-state actors targeting industrial control systems. LMNTRIX OT Security is purpose-built to defend ICS, SCADA, and other OT environments from modern cyber threats without disrupting operations. We deliver multi-layered detection, asset visibility, deception-based defense, and seamless IT-OT integration—all as part of the LMNTRIX XDR platform.
Our solution closes the security gap between traditional enterprise networks and industrial systems, giving you real-time situational awareness and automated response across your entire cyber-physical environment.
WhyLMNTRIX OT Security?
Comprehensive Threat Detection & Response
Detect unauthorized access, zero-days, malware, and insider threats across your OT network in real time.
Enhanced Visibility & Asset Protection
Regulatory Compliance & Risk Reduction
Seamless IT-OT Security Convergence
Core Capabilities
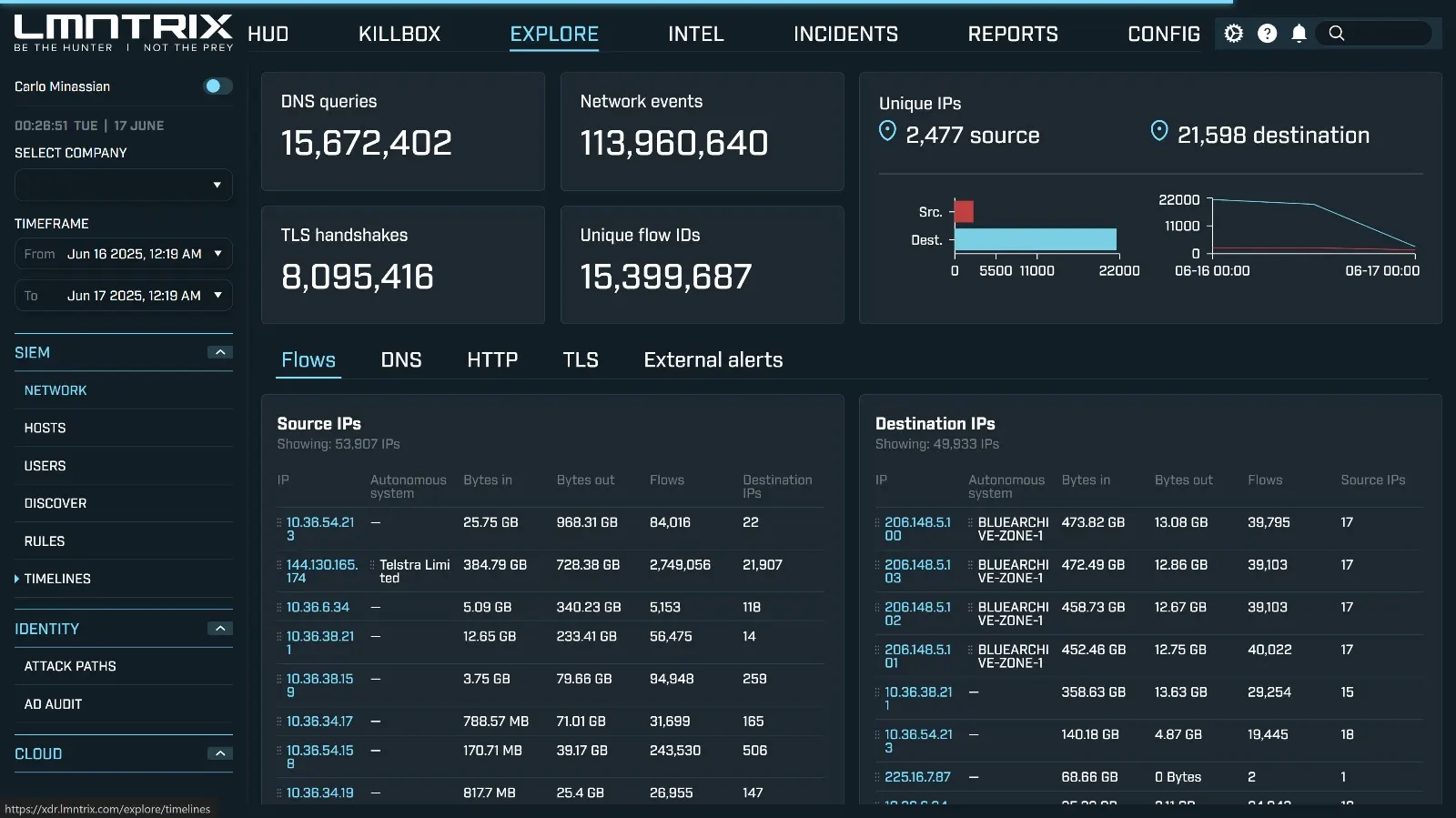
Comprehensive Asset Discovery & Visibility
Complete OT Asset Inventory: Automated discovery and mapping of all industrial devices
Unauthorized Device Detection: Identify and alert on rogue devices connecting to OT networks
Network Topology Mapping: Visual representation of industrial network architecture and connections
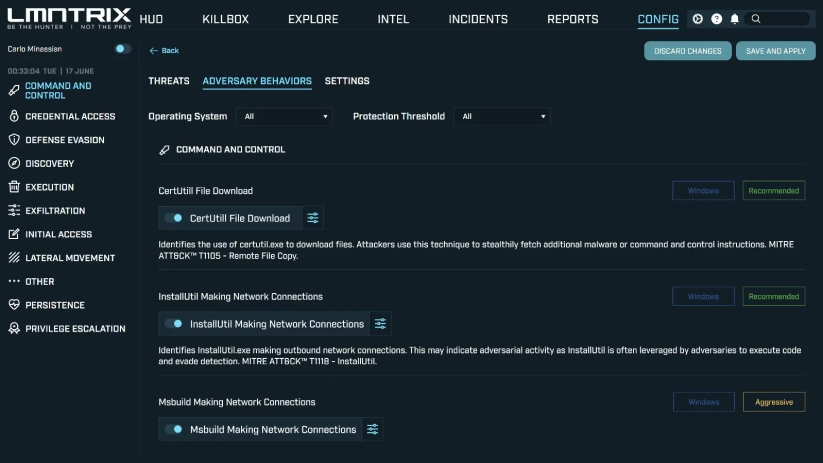
Advanced Threat Detection for ICS/SCADA
Network Segmentation & Anomaly Detection
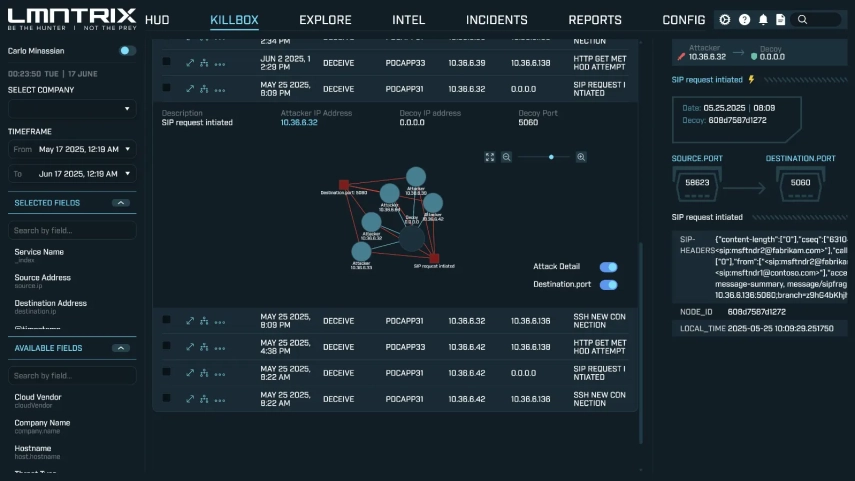
Industrial Deception Technology
OT-Specific Decoys
SCADA Honeypots
Threat Intelligence Gathering
Early Warning System
Specialized EndpointSecurity for OT
Windows & Linux Support
Protection for OT systems running standard operating systems
Detection-Only Mode
Non-disruptive monitoring for critical production systems
Proxy Support
Control Server Protection
OT-FocusedSIEM & Analytics
Industrial Log Management
Custom OT Dashboards
ML-Enhanced Detection
Long-Term Retention
Rapid Investigation
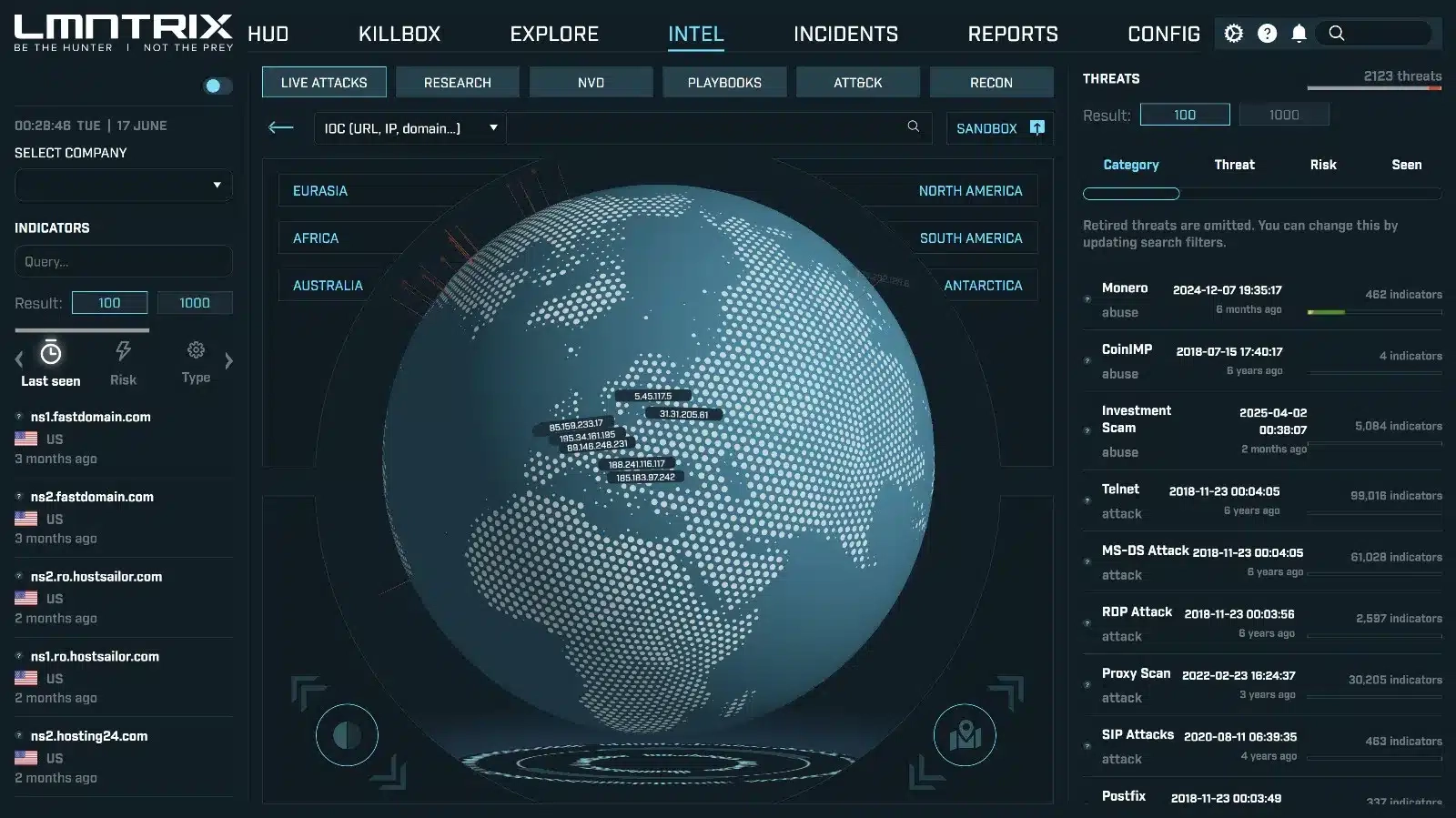
IndustrialThreat Intelligence
Global Threat Feeds
Attack Correlation
Vulnerability Intelligence
Industry-Specific Insights
Prioritized alerts on ICS/SCADA vulnerabilities
Automated Response & Containment
Compliance & Risk Management
Industry Use Cases
Manufacturing & Industrial Production
Protect assembly lines, robotics, and production control systems from cyberattacks that could halt operations, damage equipment, or compromise product quality.
Key Protections:
Energy & Utilities
Key Protections:
Water & Wastewater Treatment
Key Protections:
Oil & Gas Operations
Key Protections:
Transportation Systems
Chemical & Pharmaceutical
Key Protections:
Technical Architecture
Multi-Layer Detection Architecture
Network Layer
Out-of-band monitoring of all SCADA activity independent of device logging capabilities
Protocol-aware analysis supporting 15+ industrial protocols
Traffic metadata analysis with deep packet inspection
Network segmentation validation between IT and OT environments
Device Layer
Asset discovery and fingerprinting for complete inventory management
Device behavior baselining to detect operational anomalies
Configuration monitoring to identify unauthorized changes
Vulnerability assessment for industrial control systems
Application Layer
Industrial application monitoring for SCADA, HMI, and engineering workstations
Process integrity validation to detect cyber-physical attacks
Quality monitoring integrity
Deployment & Integration Model
Agent Deployment: Recommended for corporate endpoints in prevention mode and OT/HMI systems in detection mode only.
Protocol Coverage: Unmatched support for industry standards, including BACNet, DNP3, IEC-104, S7, OPC, MMS, ICCP, and many more.
Cloud-Connected: Secure XDR integration for remote monitoring and management
XDR Platform: Unified security operations across IT and OT environments
Industrial Systems: Direct integration with major PLC, DCS, and SCADA platforms
Compliance & Standards
Regulatory Frameworks Supported
NIST Cybersecurity Framework: Complete implementation guidance and controls
IEC 62443: Industrial automation and control systems security standards
NERC CIP: North American electric reliability standards
ISO 27001/27002: Information security management systems
COBIT: Control objectives for information and related technologies
Industry Standards Compliance
NIST SP 800-82: Guide to industrial control systems security
CISA Guidelines: Critical infrastructure cybersecurity best practices
TSA Pipeline Security: Transportation Security Administration requirements
FDA Guidelines: Medical device cybersecurity requirements
Customer Success Metrics
99.9% Uptime
95% Reduction
80% Decrease
100% Protocol
Chief Information Security Officer
Global Manufacturing Company
Director of Cybersecurity
Major Utility Company
LMNTRIX OT FAQs
LMNTRIX OT
What is LMNTRIX OT?
LMNTRIX OT is a subscription feature of LMNTRIX XDR that provides OT and IoT security capability designed to enhance visibility, security, and monitoring of industrial control systems (ICS) and critical infrastructure.
What industries does LMNTRIX OT serve?
LMNTRIX OT serves industries such as energy, manufacturing, utilities, transportation, oil and gas, and healthcare, focusing on environments with critical infrastructure.
What is the primary function of LMNTRIX OT?
The primary function is to provide real-time visibility, threat detection, and anomaly detection for OT and IoT environments, helping organizations monitor and protect their industrial networks.
How does LMNTRIX OT support industrial cybersecurity?
LMNTRIX OT uses network detection & response (NDR), network traffic monitoring, behavioral analytics, machine learning, endpoint detection & response, threat intelligence and deceptions to detect threats and anomalies in industrial control systems, helping prevent cyber incidents and operational disruptions.
What are the key components of LMNTRIX OT' solution?
Key components include LMNTRIX NDR for OT, LMNTRIX Packets for OT, LMNTRIX EDR for OT, LMNTRIX Deceive for OT and LMNTRIX Intelligence for OT.
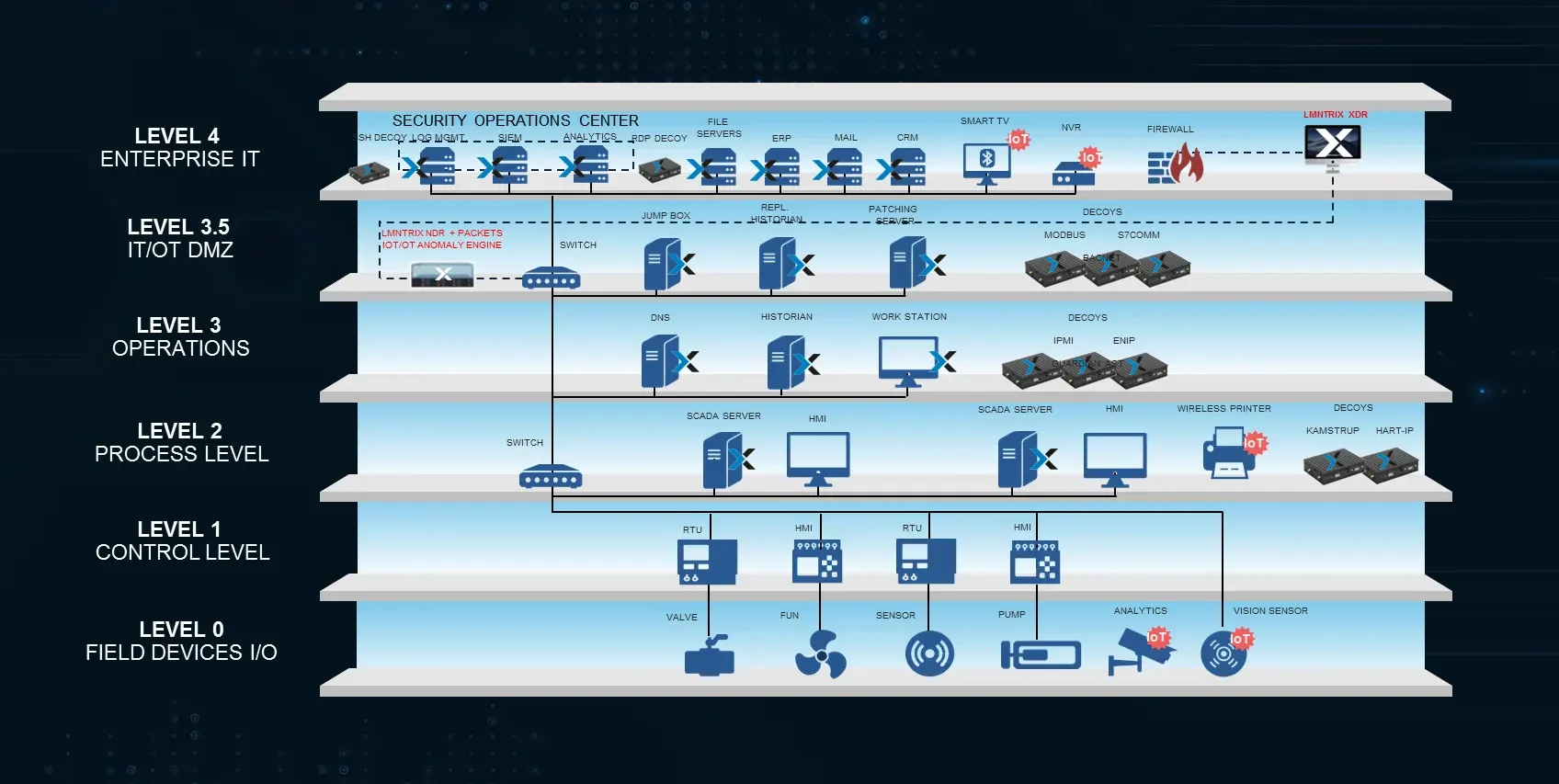
Where on a typical OT network are LMNTRIX OT components deployed?
Using the Purdue model below we can see where each of the LMNTRIX OT security functions are deployed:
LMNTRIX NDR and Packets for OT are deployed on a SPAN or TAP port at level 3.5 and inspects traffic from all lower levels. Both NDR and Packets sensors can be deployed on the same machine as depicted in the below architecture or on separate machines.
LMNTRIX EDR for OT can be seen deployed on all workstations and servers including the SCADA servers, Historian, DNS, Patching servers, and Jump box.
Finally, Decoys from LMNTRIX Deceive for OT can be seen deployed at Levels 2, 3 and 3.5 using a variety of protocols including Modbus, S7comm, Bacnet, IPMI, ENIP, Guardian AST, Kamstrup, and Hart-ip.

Is LMNTRIX OT superior to other OT security solutions?
Yes, LMNTRIX OT is considered far superior to point product OT security solutions as it supports both IT and OT environments using the same solution while providing protection against multiple threat vectors (endpoint, network, lateral movement, encrypted attacks) and is completely operationalised and delivered with LMNTRIX MDR as standard capability.
Unlike other vendor OT security solutions, the LMNTRIX architecture and technology stack provides complete support for ICS/SCADA environments.
The LMNTRIX multi-vector and holistic architecture detects any threat to the SCADA application, process or network, providing granular visibility of SCADA traffic and facilitating attack forensics:
- We monitor and record all SCADA activity out-of-band and independent of the ability of SCADA devices to send logs
- We baseline normal behavior and alert on deviations from the baseline to prevent undesired network operations based upon policy
- With our integrated network and endpoint threat forensics together with deceptions everywhere we reveal the entire sequence of an attack event
- All security and events related to our architecture are centrally managed, providing a complete view across your enterprise and control networks
- We support the industry’s most extensive support of ICS/SCADA-specific protocols including BACNet, DNP3, IEC-60870-5-104, IEC 60870-6 (ICCP), IEC 61850, MMS, Modbus, OPC, Profinet, S7 (Siemens) and many others
- We detect and prevent exploits of ICS vulnerabilities with SCADA IDS signatures and on the endpoint using exploit prevention using hardware assisted control flow integrity (HA-CFI), closing the window of exposure between vulnerable and patched systems.
- We detect lateral movement using SCADA specific deceptions
- We recommend LMNTRIX EDR to be installed on all Corporate endpoints in Prevention Mode. However, LMNTRIX EDR for OT recommended deployment is on all PCN endpoints (Control/HMI Servers) in Detection Mode only – Not Prevention. It can be installed on any device permitted that supports Windows, Linux, Mac and Solaris. Recommended but not required on Control Servers and HMIs. Not recommend on any other PCS components.
- Our network sensors can utilise a full range of threat detection capabilities including deceptions, IDS, anti-malware, and sandboxing to detect inbound threats to SCADA networks
In summary our architecture provides a complete IT-OT security solution that protects the corporate network past the perimeter, the bridge between IT and OT networks and operator workstations and SCADA devices within the OT network.
What is LMNTRIX NDR for OT, and what does it do?
LMNTRIX NDR for OT is a network sensor that provides network visibility, asset inventory, vulnerability assessment, and threat detection for OT and IoT environments.
How does LMNTRIX NDR for OT detect threats?
It uses machine learning, behavioral analysis, and signature-based detection to identify unusual patterns, known vulnerabilities, and potential threats in OT and IoT networks.
What is LMNTRIX Packets for OT, and what does it do?
LMNTRIX Packets primary use case is post breach forensics as it captures and retains OT meta-data traffic for minimum 30 days and makes it available to investigators. The other use case for LMNTRIX Packets is the detection of slow and advanced attacks using a combination of retrospection, anomaly detection and threat hunting.
What is LMNTRIX Deceive for OT, and what does it do?
LMNTRIX Deceive for OT is designed to detect the presence of threat actors that have a foot hold within OT networks and are looking to move laterally.
LMNTRIX Deceive for OT weaves a deceptive layer over your entire network – every endpoint, server and network component is coated with deceptions. The moment an attacker penetrates your network, they are in an illusive world where all the data is unreliable. If attackers cannot collect reliable data, they cannot make decisions. And if they cannot make decisions, the attack is paralysed. This approach provides the following benefits:
- No false positives – every alert is treated as a major incident and escalated to you
- Turn the tables on the bad guys!
- Change the economics of cyber defence by shifting the cost to the attacker
The intent of the service is to address insider threats and advanced human adversaries that are now on your network moving laterally stealing data and actively working to elevate their privileges. Existing solutions such as SIEM, IPS, EDR, Sandboxes, NextGen Firewalls, Web and Email Gateways are defenseless against this threat vector. By deploying deceptions everywhere, we are able to address this difficult threat vector.
LMNTRIX Deceive changes the asymmetry of cyber warfare, by focusing on the weakest link in a targeted attack – the human team behind it. Targeted attacks are orchestrated by human teams. And humans are always vulnerable. Advanced attackers rely on one simple fact – that what they see is real and that the data they collect is reliable. Firewall, Anti-virus, EDR, Sandbox, IDS, and intelligence feed technologies generate so much data that the signal is lost.
Attackers prowling a target network look for juicy content. They browse Active Directory for file servers and explore file shares looking for documents, try default passwords against network devices and web services, and scan for open services across the network.
LMNTRIX Deceive is a cloud-based service running off the LMNTRIX XDR where deceptions are deployed from, alerts reviewed, notifications configured and devices managed from.
LMNTRIX Deceive incorporates 4 types of deceptions. These are Decoys, Breadcrumbs, Tags, and Personas. Each is designed to address a different insider threat and human adversary threat type and together they form a powerful defense.
What is LMNTRIX EDR for OT, and what does it do?
LMNTRIX EDR for OT is a part of LMNTRIX XDR designed to provide advanced security capabilities across an organization’s OT environment. Built on the foundation of the LMNTRIX XDR, the LMNTRIX EDR for OT focuses specifically on endpoint protection, threat detection, and incident response within OT and ICS environments. It is commonly used in cybersecurity applications to safeguard OT infrastructure, monitor for security threats, and facilitate rapid response to potential incidents.
What are the Key Functions of LMNTRIX EDR for OT?
- Endpoint Detection and Response (EDR):
- The LMNTRIX EDR for OT includes NGAV and EDR capabilities, allowing it to monitor, detect, and respond to threats on Windows and Linux endpoints in real-time. It provides visibility into endpoint activities and can detect suspicious behaviors, malicious software, and lateral movement across a network.
- EDR capabilities are bolstered by machine learning models, which can identify anomalies and detect threats like ransomware, malware, and other endpoint attacks.
- Threat Prevention:
- LMNTRIX EDR for OT uses prevention policies to block known threats before they impact systems. This includes malware prevention features that can stop malware and ransomware execution, along with behavioral detection to identify potentially harmful actions that may not be associated with known malware.
- Centralized Management and Configuration:
- The LMNTRIX EDR for OT is managed through LMNTRIX XDR, allowing centralized deployment and configuration across all OT monitored endpoints. This enables administrators to easily roll out updates, change security policies, and monitor agent health from a single interface.
- Data Collection and Analysis:
- Beyond security monitoring, the agent can also collect logs, metrics, and events from endpoints, which are then stored in LMNTRIX XDR for analysis and visualization. This comprehensive data collection supports a wide range of security analytics and observability use cases.
- Intrusion Detection:
- LMNTRIX EDR for OT can act as an intrusion detection system (IDS), monitoring network traffic and system activities for signs of unauthorized access or other indicators of compromise. This includes leveraging MITRE ATT&CK techniques to detect and map potential threats.
- Incident Response:
- The LMNTRIX EDR for OT facilitates automated and manual response actions. Security teams can isolate infected machines, terminate malicious processes, or quarantine suspicious files directly from the Elastic Security platform, helping contain threats quickly.
Does LMNTRIX EDR for OT provide proxy support?
Yes, the LMNTRIX EDR for OT supports connectivity through proxy servers. It can be configured to use proxies such as HTTP Connect (HTTP 1) and SOCKS5 proxies, which are helpful in OT environments where direct internet access is restricted. Proxy settings can be configured in various ways, depending on the deployment method.
What are the benefits of using LMNTRIX EDR for OT?
- Unified Platform: Combines data collection, analysis, and security into a single solution, which streamlines operations and simplifies security infrastructure.
- Scalability: Designed to support environments of varying sizes, from small businesses to large enterprises with distributed networks.
- Advanced Detection: Uses machine learning and behavioral analytics to identify both known and unknown threats, reducing reliance on signature-based detection alone.
- Integration with LMNTRIX XDR: Offers seamless integration with other LMNTRIX XDR components, enabling full IT and OT observability, logging, and performance monitoring alongside security functions.
What are the Use Cases for LMNTRIX EDR for OT?
- Endpoint Protection: Protects OT workstations, servers, and other endpoints from a wide range of threats.
- Security Operations: Provides OT SOC teams with tools for monitoring, investigating, and responding to security incidents.
- Compliance Monitoring: Helps meet compliance requirements by logging OT endpoint activities and storing them securely in LMNTRIX XDR for auditing.
The LMNTRIX EDR for OT offers a comprehensive security solution within the LMNTRIX XDR ecosystem, providing flexible deployment options, powerful detection capabilities, and integrated response tools to secure and monitor endpoint devices in real-time. It’s a key component of LMNTRX’s broader XDR (Extended Detection and Response) strategy.
What is the role of LMNTRIX XDR in LMNTRIX OT?
LMNTRIX XDR is a cloud-based platform that provides LMNTRIX OT with centralized management, monitoring, scalability, automation, analytics and incident management capabilities, allowing users to manage and analyze security data across multiple sites from a single interface.
How does LMNTRIX OT integrate with existing IT and OT security solutions?
LMNTRIX OT integrates with SIEMs, firewalls, ticketing systems, and network management tools to provide a seamless cybersecurity framework for both IT and OT environments.
Does LMNTRIX OT support endpoint security for OT and IoT devices?
Yes, LMNTRIX EDR for OT is focused on Nextgen Antivirus and Endpoint Detection & Response capability to provide endpoint security in OT environments.
How is LMNTRIX OT deployed in an industrial environment?
Deployment of the NDR and Packets sensors are on SPAN/TAP ports behind the OT firewall. EDR agent are deployed on all Windows and Linux machines while Deceptions are deployed on appliances or VMs within an OT environment to represent fake OT assets. All of these on premise solutions are securely managed and monitored by LMNTRIX XDR via an encrypted connection.
Does LMNTRIX OT support remote monitoring?
Yes, with LMNTRIX XDR, users can perform remote monitoring and management across multiple locations, providing real-time insights from any internet-connected device.
What kind of training is required to use LMNTRIX OT?
LMNTRIX OT is delivered with Managed Detection & Response (MDR) however LMNTRIX also offers training to help users understand platform functionalities, manage deployments, and respond to security incidents effectively.
Can LMNTRIX OT scale with my organization’s needs?
Yes, LMNTRIX OT is designed for scalability, with features like distributed architecture and cloud-based management to support organizations of varying sizes.
How does LMNTRIX OT handle firmware updates and software patches?
LMNTRIX provides regular updates for software and threat detection signatures, which can be applied manually or automatically, depending on the deployment configuration.
How does LMNTRIX OT assist with regulatory compliance?
LMNTRIX OT helps organizations meet compliance standards (e.g., NERC CIP, IEC 62443, GDPR) by providing continuous monitoring, asset management, and reporting capabilities.
Does LMNTRIX OT provide vulnerability management?
Yes, LMNTRIX OT includes vulnerability assessment tools that help identify and prioritize vulnerabilities in OT and IoT assets for remediation.
How does LMNTRIX OT protect sensitive data?
LMNTRIX OT uses encryption, role-based access control (RBAC), and secure data storage practices to protect sensitive data within the platform.
What threat intelligence capabilities does LMNTRIX OT offer?
LMNTRIX OT provides integrated threat intelligence with real-time data feeds, enabling users to stay updated on the latest OT and IoT threats and vulnerabilities.
How does LMNTRIX OT support incident response?
The platform enables rapid incident detection, alerting, and automated reporting, allowing security teams to respond swiftly to potential threats.
Can LMNTRIX OT identify and classify assets on the network?
Yes, it includes automated asset discovery and inventory, which helps organizations gain visibility into all OT and IoT devices on their network.
What are LMNTRIX OT’ visualization and reporting capabilities?
LMNTRIX OT offers customizable dashboards, reports, and visualizations to help users monitor network status, view alerts, and analyze security trends.
Does LMNTRIX OT offer API integrations?
Yes, LMNTRIX OT provides API access for integration with other security tools, enabling data sharing and streamlined workflows.
How does LMNTRIX OT handle encrypted traffic?
LMNTRIX OT can monitor encrypted traffic flows for abnormal patterns but requires integration with decryption tools for deep packet inspection.
Can LMNTRIX OT simulate attacks for testing purposes?
While LMNTRIX OT is focused on monitoring and detection, it can support integration with external tools for vulnerability testing and simulation.
Does LMNTRIX OT support predictive analytics?
Yes, it uses machine learning algorithms to identify potential risks and predict future anomalies based on historical data.
How does LMNTRIX OT handle network segmentation?
LMNTRIX OT provides network mapping and traffic analysis to help organizations design and monitor network segmentation policies for improved security.
What is the role of machine learning in LMNTRIX OT?
Machine learning is used for anomaly detection, behavioral analysis, and predictive threat detection, which enhances the platform’s ability to identify new or evolving threats.
What types of notifications or alerts can LMNTRIX OT generate?
LMNTRIX OT supports real-time alerting via email, SMS, and SIEM integrations, and alerts can be customized based on event type, severity, and frequency.
Related Resources

Industrial Control System Security Guide
White Paper
How We Protect
small and large enterprises
Why clients love working with LMNTRIX
You’re ready for advanced protection
and that means XDR







Don't just take our word for it...

Leader

Leader

Open Source Excellence

Top 250 MSSP Companies In The World

Users Choice Award
Top Rated Security



Ready to take the next steps with LMNTRIX MXDR ?
The choice is yours: see LMNTRIX in an on demand demo or set up a customized demo or request a quote.