Stop Threats in Minutes, Not Days
24/7 Threat Protection for the Modern Enterprise
Managed Detection and Response (MDR)
Stop attacks 24/7 with continuous monitoring, proactive threat hunting, alert triage, investigation and response built on LMNTRIX XDR.
24/7 Monitoring and Response
Surgical Remediation
Unlimited DFIR
Proactive Threat Hunting
Leverage our proprietary Hunt Cycle - Survey, Secure, Detect, Respond to shine a light into the darkest corners, leaving adversaries with nowhere to hide.
Reduce TCO with Instant ROI
5 x Faster MTTD & MTTR
Managed Extended Detection and Response
Unpacking core capabilities and offerings in each of the 4 pillars
MANAGED
24/7 Monitoring: Around-the-clock oversight by
cybersecurity experts.
Continuous Improvement: Regular updates and tuning of security systems.
Configuration & Maintenance: Service delivery team supporting optimal performance of purchased modules.
EXTENDED
Holistic Coverage: Integration across email, web, network, cloud, endpoint environments.
Advanced Analytics: Use of AI and machine learning to detect sophisticated threats.
Threat Intelligence: Leveraging global threat data to anticipate and counteract attacks.
DETECTION
Incident Validation: Expert validation and detailed reports for confirmed threats.
Behavioral Analysis: Detect anomalies through user and entity behavior analytics, and deception strategies.
Automated Threat Hunting: Continuous searching for potential threats using
advanced tools.
RESPONSE
Immediate Containment: Rapid action to isolate and
neutralize threats.
Guided Remediation: Expert support and guidance for resolving security incidents.
Incident Reporting: Detailed analysis and documentation of incidents for future prevention.
1
Detect < 1 Min
5
Investigate < 5 mins
30
Remediate<30 Mins
Every Second Counts
Reverse the adversary advantage with laser-accurate detection and lightning-fast investigation and response
- 1
Deploy
- 2
Detect
- 3
Investigate
- 4
Remediate
- 5
Report
Level Up with
Layers of Expertise
CYBER DEFENCE CENTER MANAGER

Benefits Advancing Your Organization
A solution that support your entire organization and its strategic objectives.
CISO
Reduced MTTD and MTTR: Dramatically lower detection and response time.
Comprehensive Threat Coverage: Ensure no threats bypass perimeter defenses.
Strategic Oversight: Gain unparalleled visibility into security operations.
IT / CYBER TEAM
Efficiency Boost: Reduce false positives by 95%. Focus on
real threats. Less staff burnout.
Rapid Incident Response:
Speed up remediation processes to minutes.
Unified Management: Manage all security tools from a single, integrated platform. Reduce onboarding and training times for new team members.
CFO
Cost Savings: Eliminate the need for multiple security tools, reducing IT workloads.
Speed to Value: Quick deployment and immediate impact on security posture.
Resource Optimization: Achieve more with current team, reducing the need for additional headcount
Transparency You Can See. Results You Can Measure.
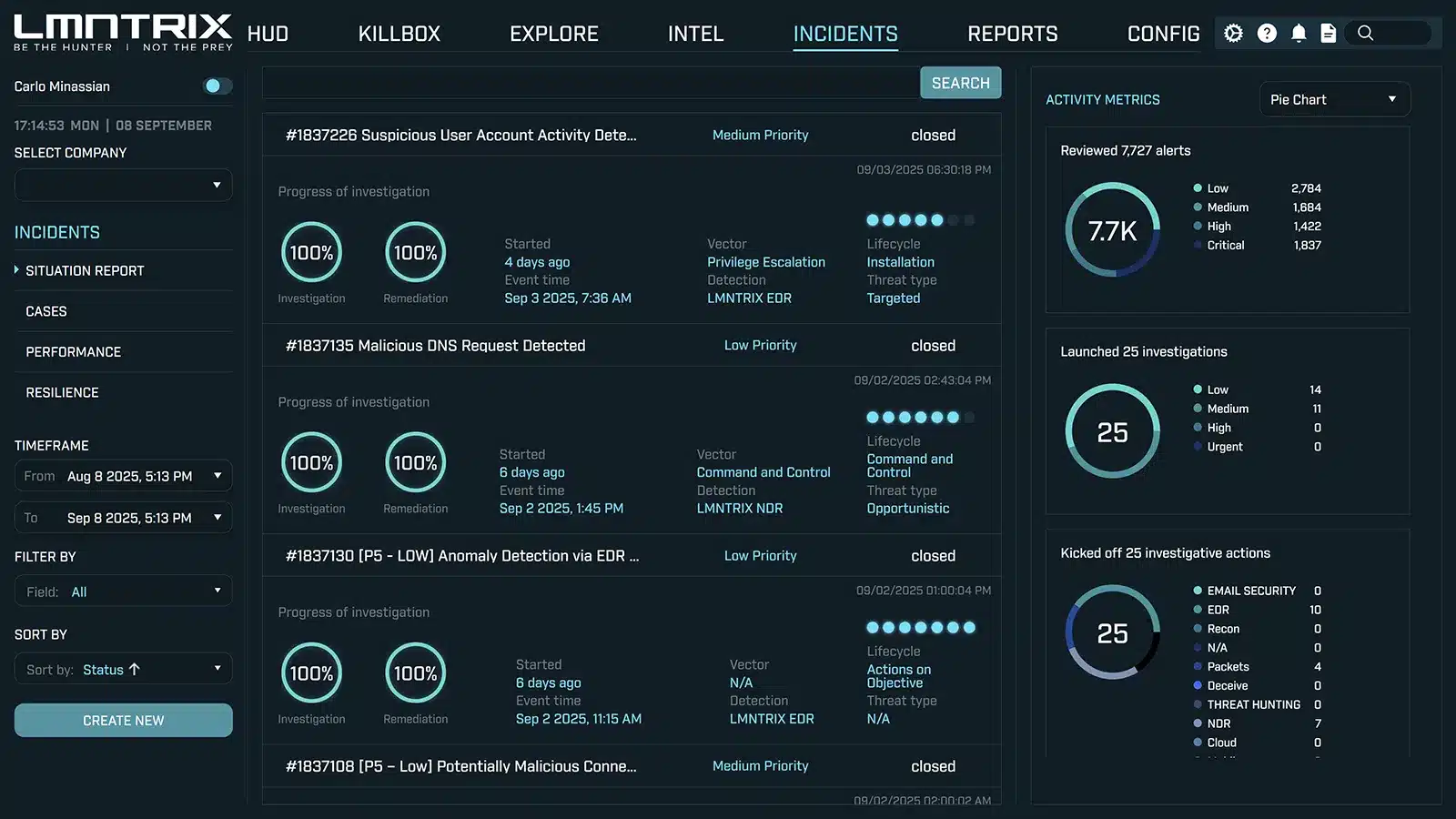
Visibility Without the Noise
See every investigation and outcome at a glance. From suspicious account activity to malicious DNS requests, each case is tracked end-to-end with progress indicators, timelines, and resolution details.
Metrics That Matter
Alerts reviewed - filtered down to only what truly matters.
Investigations launched-mapped to severity and urgency.
Investigative actions taken - spanning email, endpoint, network, and deception layers.
Security incidents uncovered -targeted, non targeted.
Remediation actions identified - network, endpoint
Accountability Built-In
- Threat vector (e.g. privilege escalation, command-and-control)
- Threat type (targeted, opportunistic, etc.)
- Lifecycle stage when it was stopped
- Progress of investigation and remediation (always 100% closed, not “in limbo”)
Measurable Outcomes for Leadership
Incident Management That Goes Beyond Alerts
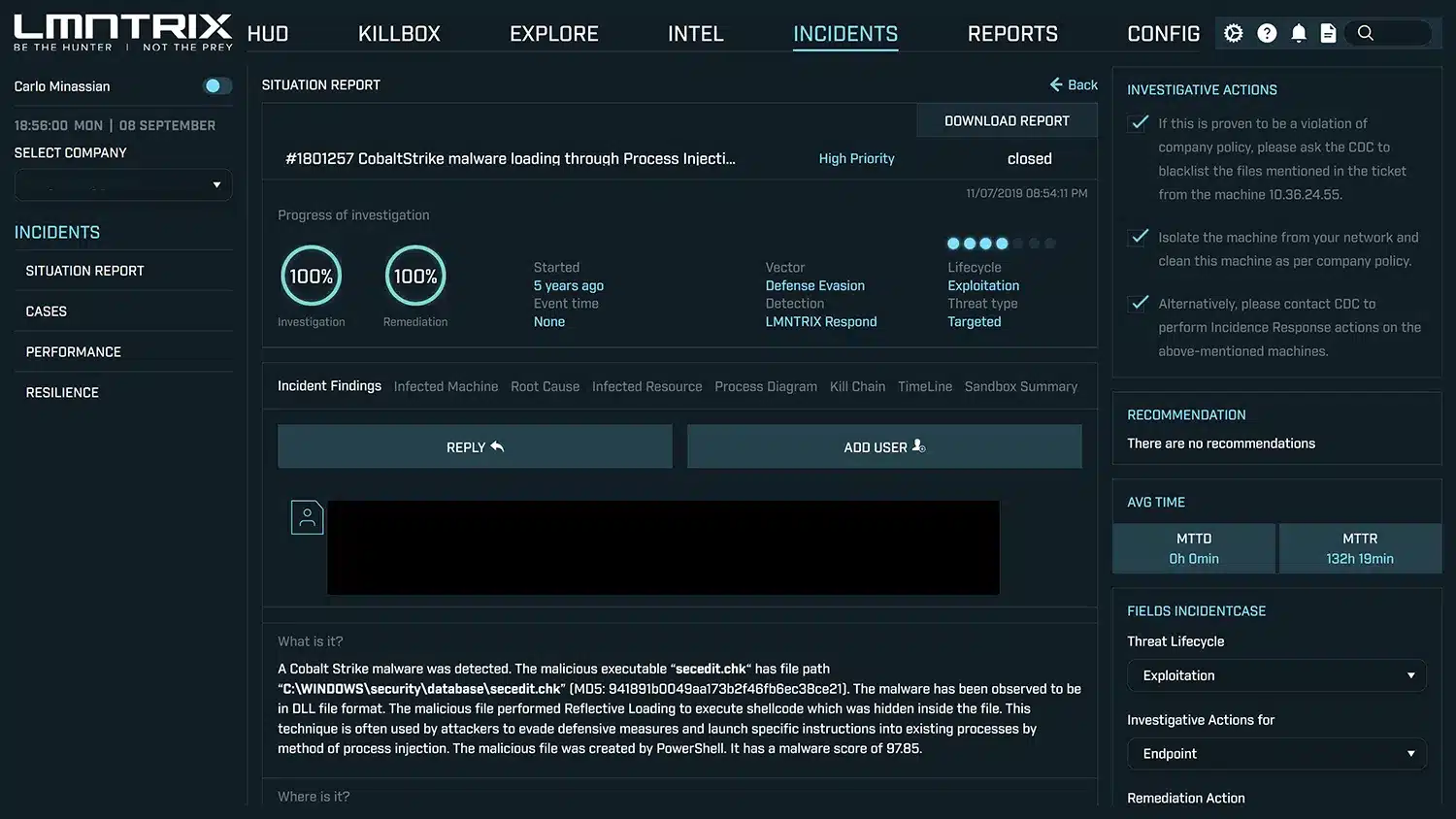
Breach Validation
Threat Containment
Once validated, LMNTRIX takes swift action to contain the threat at its source. Whether it’s isolating an endpoint, cutting off a malicious process, or blocking a command-and-control connection, containment prevents attackers from moving laterally or escalating further.
Transparent Case Management
- Progress indicators for investigation and remediation (so you know where things stand)
- Lifecycle mapping (installation, command-and-control, production, etc.)
- Threat vector and type (privilege escalation, targeted, opportunistic, etc.)
- Timestamps, host and IP details, command lines, and detection method
- Analyst communications, so your team stays in the loop
Collaborative Workflow
Clear Outcomes
Why It Matters
Alerts reviewed - filtered down to only what truly matters.
Reduced Breach Impact — fast containment keeps attackers from spreading
Full Transparency — you see the same data our analysts see
Actionable Intelligence - validated incidents with context you can use
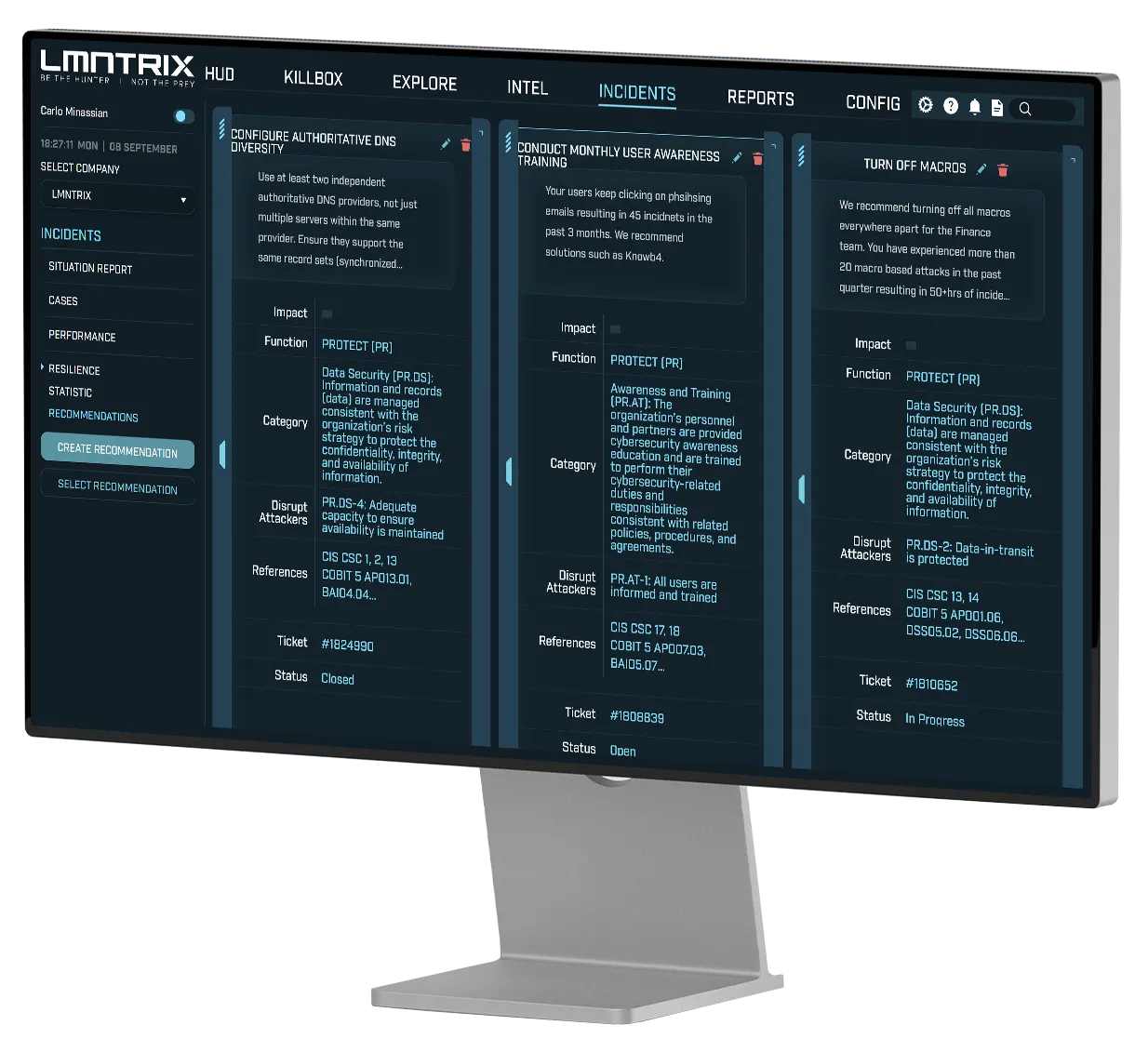
Prevent Future Breaches with Actionable Insights
What Makes It Different
Root-Cause Clarity
Targeted, High-Impact Guidance
Disrupt Attackers and Empower Your Defenders
Data-Driven Justification
Continuous Improvement Loop
Built into Every Incident, Every Day
Real-Time Performance. Real-Time Results.
You can’t improve what you don’t measure. That’s why LMNTRIX MDR includes automated performance measurement and reporting—built directly into the service.
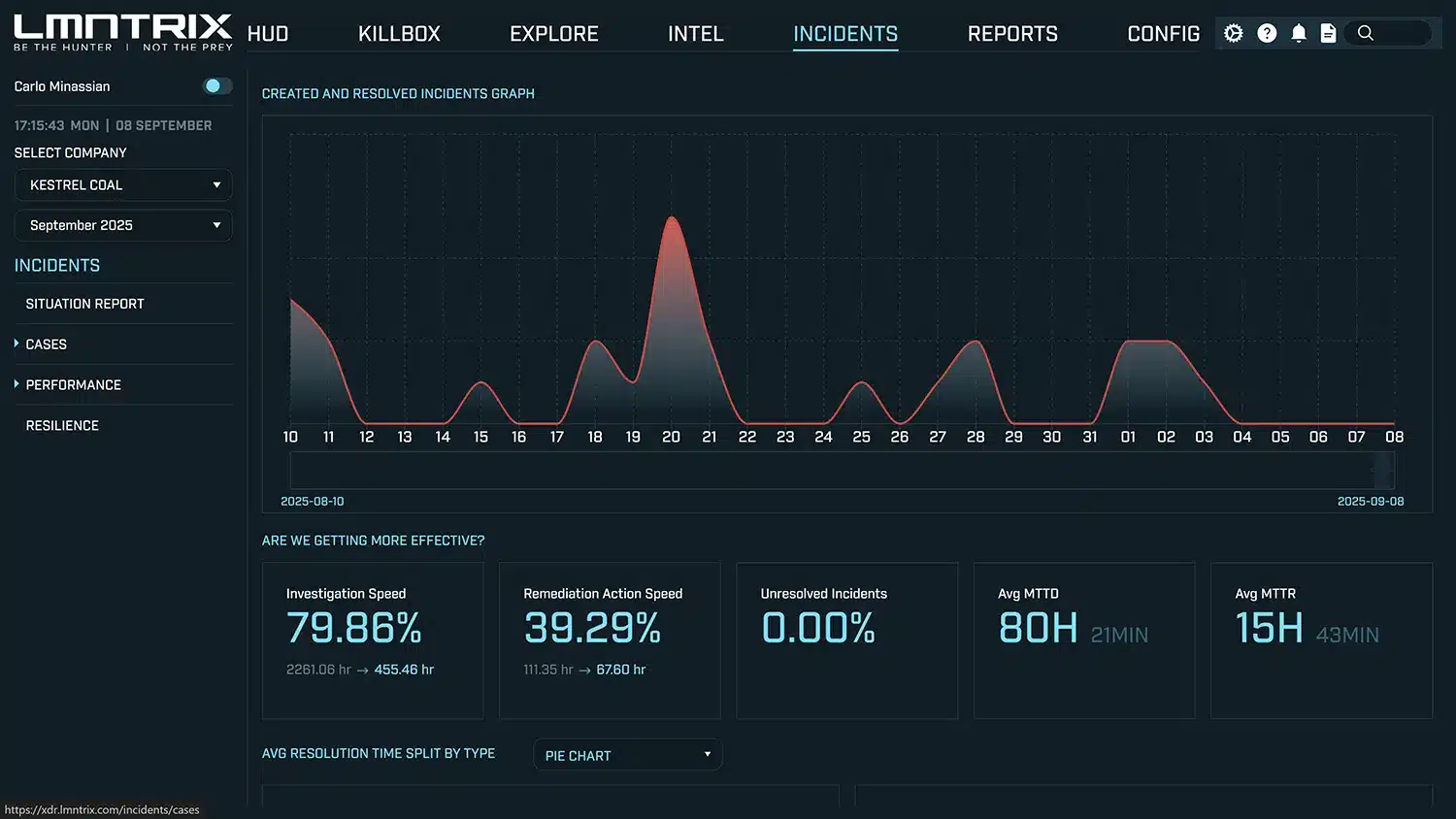
See How We’re Protecting You, in Numbers
| Metric | What It Tells You |
|---|---|
| Investigation Speed | How quickly our analysts validate and act on alerts. |
| Remediation Action Speed | How fast threats are contained and neutralized. |
| Unresolved Incidents | Clear accountability—every case closed and verified. |
| MTTD / MTTR | Industry-standard benchmarks: time to detect and time to remediate. |

Quantifiable Security Outcomes
We don’t just say we’re fast—you’ll see the numbers. From reduced dwell time to faster containment, your dashboard shows the measurable impact of LMNTRIX MDR on your risk exposure.

Transparent Reporting

Continuous Improvement
Designed for Security Leaders
Whether you’re reporting to the board, an auditor, or simply want to track ROI on your security investments, our dashboards make it simple. Live data proves your SOC is working - every hour of every day.



Our Integrations
Connect, Collect and Contain with integrations
Use Cases
LMNTRIX Managed Detection & Response


Compare LMNTRIX
Related Resources

Customer Story: AFG
Mid-tier financial services firm turns the tables on the hackers and gains context to improve security decision-making while enhancing security protection in every business system

Active Defense Webinar
Experience how our XDR platform can revolutionize your security posture through a live demonstration. Discover the proactive approaches and advanced defense mechanisms integral to our Active Defense strategies.
How We Protect
small and large enterprises
Why clients love working with LMNTRIX
You’re ready for advanced protection
and that means XDR







Don't just take our word for it...

Leader

Leader

Open Source Excellence

Top 250 MSSP Companies In The World

Users Choice Award
Top Rated Security



Ready to take the next steps with LMNTRIX MXDR ?
The choice is yours: see LMNTRIX in an on demand demo or set up a customized demo or request a quote.