Identity Protection That Goes Beyond IAM
Secure the keys to your kingdom. LMNTRIX Identity delivers continuous, AI-driven monitoring and response for identity-based threats across Active Directory, Azure AD, and hybrid environments.
Identityis your new perimeter
LMNTRIX Identity is engineered to protect your organization’s most critical asset: its users and their credentials. With identity-based attacks now the primary method for initial access and lateral movement in modern breaches, this module adds a critical layer of visibility, detection, and response.
Unlike traditional IAM or MFA tools, LMNTRIX Identity focuses on the behaviour and risks associated with user and privileged account activity—not just access control. By monitoring in real time, detecting anomalies, and deploying deception-based early warning traps, this module empowers your security operations team to neutralize identity threats before they impact your business.
It integrates seamlessly with Active Directory (AD), Azure AD, and cloud identity providers, using AI-powered behavioral baselining to detect risky logins, privilege escalations, lateral movement opportunities, and policy misconfigurations.
Whether you’re navigating a hybrid, multi-cloud, or legacy environment, LMNTRIX Identity is your line of defense against the fastest-growing threat vector in cybersecurity.
Valueto Your Organization
Proactive Threat Detection
Comprehensive Identity Visibility
Behavioural Analytics for Anomaly Detection
Privileged Account Security
Actionable Risk Management
Deployment Scope

Protected Identity Definition
Pricing Model

Supported Environments

Deployment
Lightweight agents and API integrations ensure minimal performance impact, managed via the LMNTRIX XDR platform.

Compliance
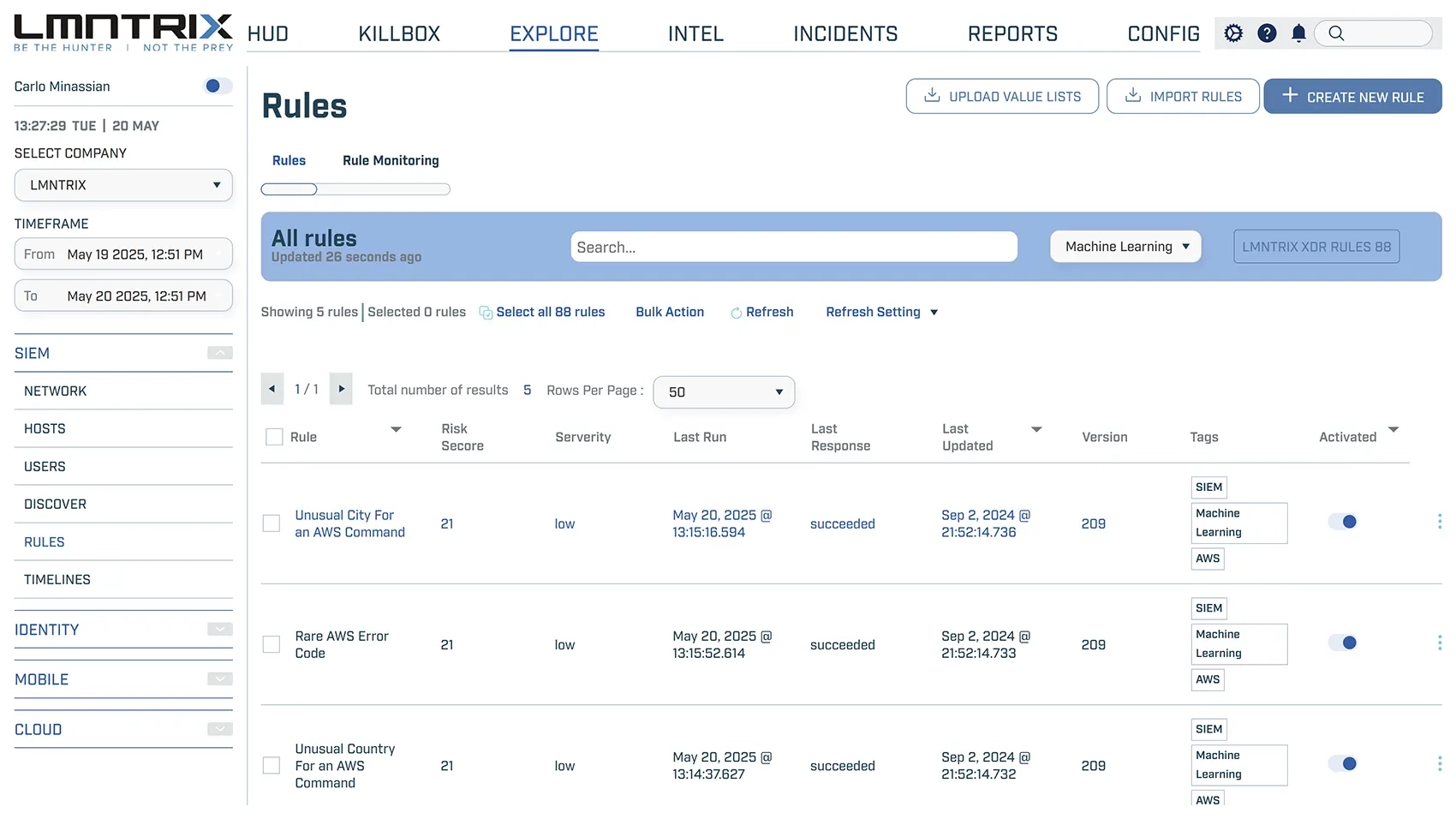
Core Capabilities
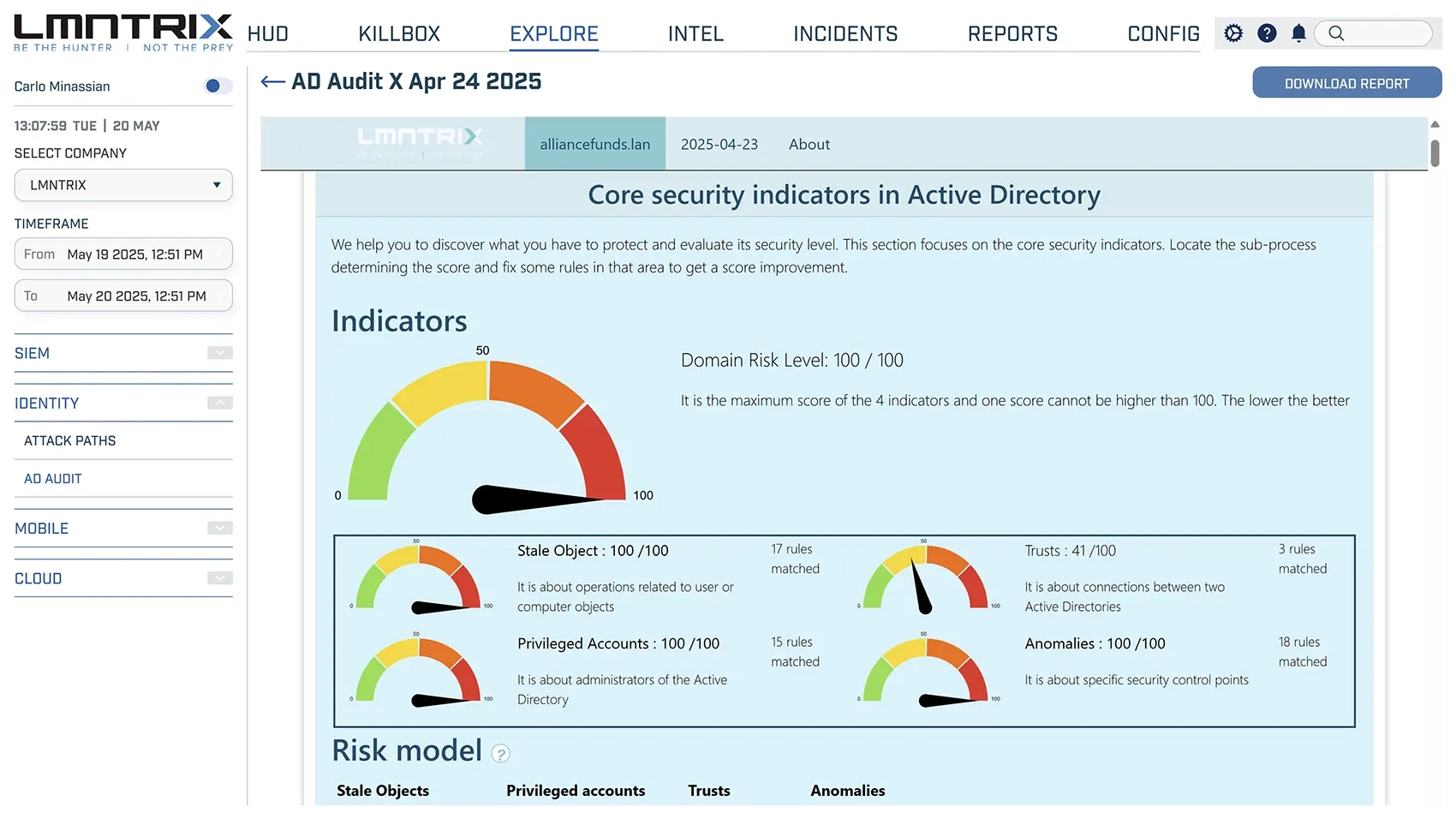
Active Directory (AD) Audit & Hygiene
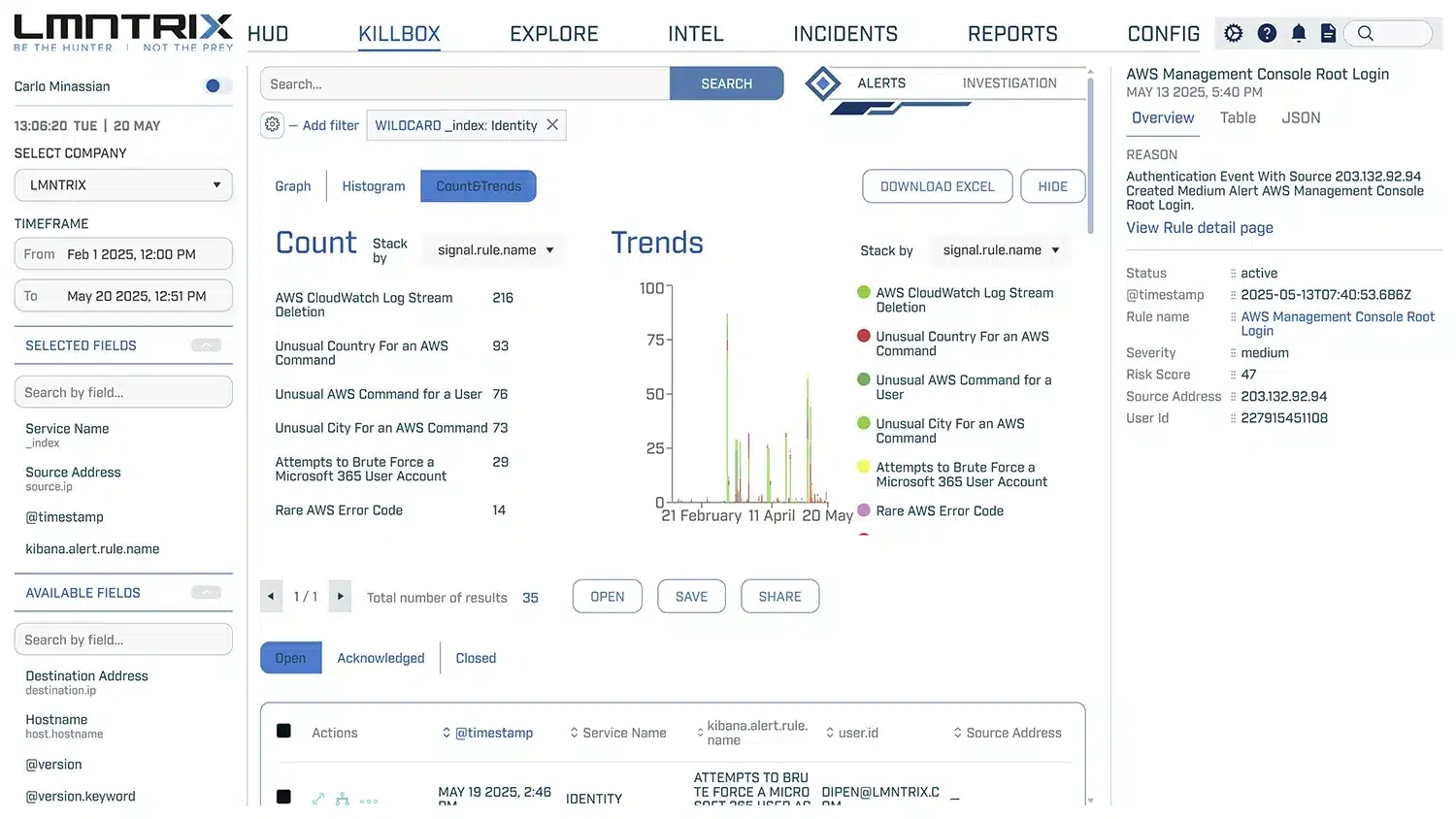
Identity Threat Detection& Response (ITDR)
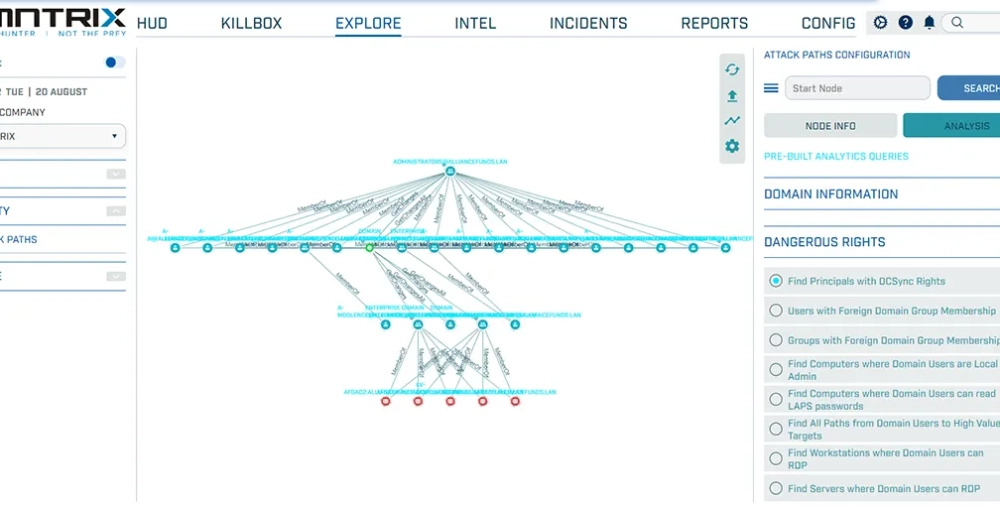
Attack Path Mapping & Analysis
Analyzes user relationships, permissions, and group memberships
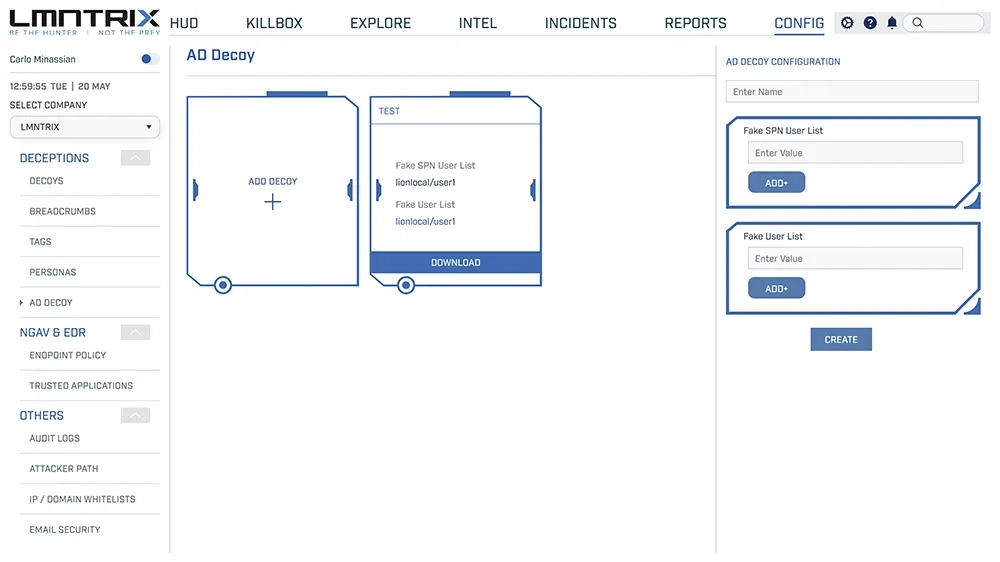
AD Deception (Credential & Service Decoys)
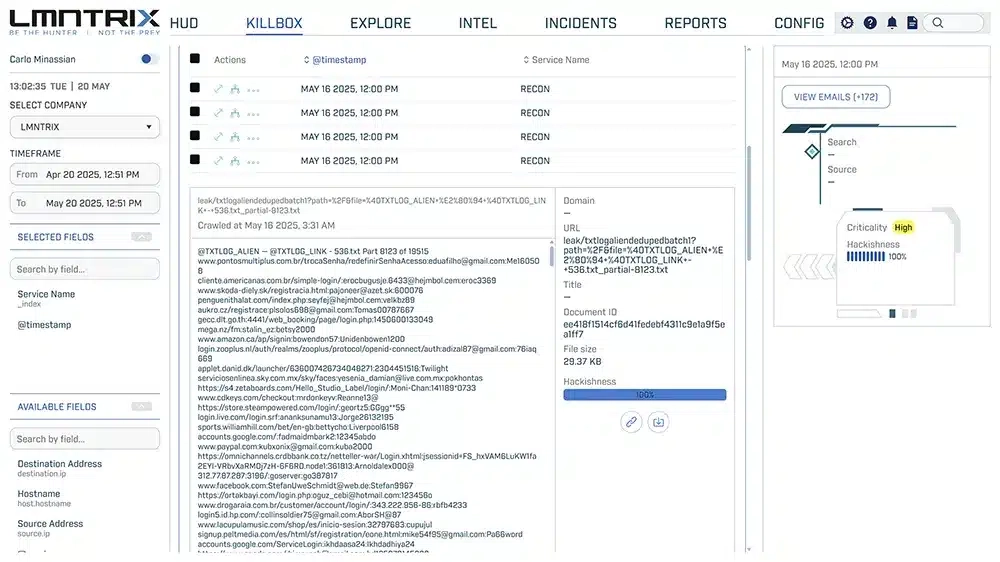
LMNTRIX RECON – Credential Breach Monitoring
Identity FAQs
LMNTRIX Identity
What is LMNTRIX Identity?
LMNTRIX Identity is a subscription feature of LMNTRIX XDR. The Identity enables hyper-accurate detection of identity-based threats, extends MITRE ATT&CK® coverage, and halts novel attacks using multiple advanced techniques.
Comprised of five key service elements that provides a comprehensive intelligence-led identity threat identification, management, and response solution that halts novel identity-based attacks using multiple advanced techniques:
- AD Audit: Applies Active Directory audits with deep visibility across user accounts, access levels, and activities.
- IATDR: Identity and access threat detection & response.
- Attack Paths: Detects chains of abusable privileges and user behaviors, creating direct and indirect connections between computers and users.
- AD Decoy: Uses decoy credentials and services for the detection of attack reconnaissance activity.
- Identity Recon: Employs Darknet Credential Breach Monitoring.
What is the LMNTRIX Identity “Identity and Access Threat Detection & Response (IATDR)” service?
Identity and Access Threat Detection & Response (IATDR) service is designed to protect organizations from attacks that target user identities and access privileges, by using our Identity detection rules and advanced machine learning jobs to identify suspicious activity related to user accounts, and taking swift action against suspicious behavior.
Key features of IATDR include:
- Data Collection: IATDR collects Identity & Access data from you environments, such as Azure EntraID ,Microsoft 365, AD, AWS, Okta, GCP and Google Workspace.
- Identity Detection Rules: Over 125 identity detection rules are continuously monitoring Identity & Access threats across multiple platforms, assessing various factors to ensure comprehensive protection, including:
- User Activity (e.g. Failed login attempts exceeding a certain threshold within a timeframe, Accessing resources outside of normal business hours or location…)
- User Attributes (e.g. High-privilege accounts attempting to access low-privilege resources, Users with recent password resets trying to access sensitive data…)
- Device Characteristics: (e.g. Login attempts from unknown or unauthorized devices)
- Machine Learning Jobs: Identity machine learning (ML) adds another layer of sophistication to Identity threat detection, our Identity Machine learning analyses Users Behavior, Automates the Anomaly Detection, and Reduces False Positives.
- Fine-tuning: Regularly review and adjust rules to ensure optimal balance between identifying real threats and avoiding false positives.
What are the use cases for LMNTRIX Identity IATDR?
- Compromised Account Detection: IATDR detects the login attempt as a deviation from the user’s baseline behavior and triggers an alert
- Privilege Escalation and Lateral Movement Attempts
- Insider Threats: detect unusual data access patterns, such as downloading large amounts of data outside of work hours
- Brute-Force Login Attempts: pre-defined rules can detect these brute-force attempts and automatically lock down the account after exceeding a certain number of failed attempts
- Zero-Day Attacks: machine learning algorithms can identify anomalous user behavior that deviates from established patterns, even if it doesn’t match a pre-defined rule
How do I configure AWS identity data for LMNTRIX Identity IATDR?
Collect AWS CloudTrail data, this data contain account activity across your AWS infrastructure.
Setup
- Create S3 bucket.
- Create an SQS queue in the same AWS Region using Amazon SQS console.
- Replace the access policy attached to the queue with the following queue policy
{
“Version”: “2008-10-17”,
“Id”: “cloudtrail_ID”,
“Statement”: [
{
“Sid”: “__owner_statement”,
“Effect”: “Allow”,
“Principal”: {
“Service”: “s3.amazonaws.com”
},
“Action”: “SQS:*”,
“Resource”: “arn:aws:sqs:us-east-1:227915451108:<queue-name>”,
“Condition”: {
“StringEquals”: {
“aws:SourceAccount”: “<account-id>”
},
“ArnLike”: {
“aws:SourceArn”: “arn:aws:s3:::<bucket-name>”
}
}
}
]
}
Make sure to change the <sqs-queue-arn> and <bucket-name> to match your SQS queue Amazon Resource Name (ARN) and S3 bucket name.
- Configure S3 Bucket
We’ll need to ensure our bucket is configured correctly by modifying the event notification properties. To do this, we’ll navigate to Amazon S3 -> $BucketName -> Properties -> Event notifications -> Create event notification:

Under Event Types, we can select the type of events for which we would like to receive notifications to our SQS queue:

We’ll also need to select the queue where events will be published:

- Configure CloudTrail Logs to S3 Bucket
- Create an IAM user account for LMNTRIX-SIEM and have sufficient access to Amazon S3 and Amazon SQS:
{
“Version”: “2012-10-17”,
“Statement”: [
{
“Sid”: “cloudtrialpolicy”,
“Effect”: “Allow”,
“Action”: [
“sqs:DeleteMessage”,
“s3:GetObject”,
“sqs:ChangeMessageVisibility”,
“sqs:ReceiveMessage”,
“sqs:SendMessage”,
“s3:ListBucket”,
“s3:GetBucketLocation”
],
“Resource”: [
“arn:aws:s3:::*/*”,
“arn:aws:s3:::<bucket-name>”,
“arn:aws:sqs:<region>:<owner-account-id>:<queue-name>”
]
}
]
}
- Share the following with LMNTRIX
- [S3] Bucket ARN
- Region Name
- [SQS] Queue URL
- SQS ARN
- Access Key ID
How do I configure Azure identity data for LMNTRIX Identity IATDR?
Microsoft Office 365:
Collect data from Office 365 and Azure AD activity logs exposed by the Office 365 Management Activity API.
Setup
enable Audit Log and register an application in Microsoft Entra ID (formerly known as Azure Active Directory, once the application is registered:
- Note Application (client) ID and the Directory (tenant) ID in the registered application’s Overview page.
- Create a new secret to configure the authentication of your application:
- Navigate to Certificates & Secrets
- Click New client secret and provide some description to create new secret.
- Note the Value.
- Add permissions to your registered application. Please check O365 Management API permissions for more details.
- Navigate to API permissions page and click Add a permission
- Select Office 365 Management APIs tile from the listed tiles.
- Click Application permissions.
- Under ActivityFeed, select Read permission. This is minimum required permissions to read audit logs of your organization as provided in the documentation. Optionally, select ActivityFeed.ReadDlp to read DLP policy events.
- Click Add permissions.
- If Read permission under Microsoft.Graph tile is not added by default, add this permission.
- After the permissions are added, the admin has to grant consent for these permissions.
Microsoft Entra ID:
Collect data from
- Sign-in logs: Information about sign-ins and how your users use your resources.
- Identity Protection logs: Information about user risk status and the events that change it.
- Provisioning logs: Information about users and group synchronization to and from external enterprise applications.
- Audit logs: Information about changes to your tenant, such as users and group management, or updates to your tenant’s resources.
Setup Microsoft EntaID:
- Diagnostic setting to export logs from Microsoft EntaID to Event Hubs
- Event Hub to store in-flight logs exported by Microsoft EntaID
- Storage Account Container to store information about logs consuming
How do I configure GCP identity data for LMNTRIX Identity IATDR?
Collect audit logs of administrative activities and accesses within your Google Cloud resources
Setup: set up a Service Account with a Role and a Service Account Key to access data on your GCP project
- Service Account: create a Service Account. A Service Account (SA) is a particular type of Google account intended to represent a non-human user who needs to access the GCP resources
- Role privileges:
- metricDescriptors.list
- timeSeries.list
- subscriptions.consume
- subscriptions.create *
- subscriptions.get
- topics.attachSubscription *
- Service Account Keys
Now, with your brand new Service Account (SA) with access to Google Cloud Platform (GCP) resources, you need some credentials to associate with it: a Service Account Key.
From the list of SA:
- Click the one you just created to open the detailed view.
- From the Keys section, click “Add key” > “Create new key” and select JSON as the type.
- Download and store the generated private key securely (remember, the private key can’t be recovered from GCP if lost).
- The Project Id : the Google Cloud project ID where your resources exist.
- Credentials File: Save the JSON file with the private key in a secure location of the file system.
- Share the following with LMNTRIX
- Project Id
- Credentials File
- Subscription Name: the short subscription name here, not the full-blown path with the project ID. You can find it as “Subscription ID” on the Google Cloud Console
- Topic: Name of the topic where the logs are written to.
Google Workspace:
Collect data from the different Google Workspace audit reports APIs.
Setup
- In order to Collect data from the Google Reports API you must:
- Have an administrator account.
- Set up a ServiceAccount using the administrator account. https://support.google.com/workspacemigrate/answer/9222993?hl=en
- Set up access to the Admin SDK API for the ServiceAccount. https://support.google.com/workspacemigrate/answer/9222865?hl=en
- Enable Domain-Wide Delegation for your ServiceAccount. https://developers.google.com/admin-sdk/reports/v1/guides/delegation
- This integration will make use of the following oauth2 scope:
- https://www.googleapis.com/auth/admin.reports.audit.readonly
- download your service account credentials as a JSON file and share with LMNTRIX
- Click the Advanced option of Google Workspace Audit Reports. The default value of “API Host” is https://www.googleapis.com. The API Host will be used for collecting admin, drive, groups, login, saml, and user accounts logs.
How do I configure Okta identity data for LMNTRIX Identity IATDR?
Collects events from the Okta API, specifically reading from the Okta System Log API.
Types Of Authentications
- API Key: In this type of authentication, we only require an API Key for authenticating the client and polling for Okta System Logs.
- Oauth2: In this type of authentication, we require the following information:
- Your Okta domain URL. [ Example: https://dev-123456.okta.com ]
- Your Okta service app Client ID.
- Your Okta service app JWK Private Key
- The Okta scope that is required for OAuth2. [ By default this is set to okta.logs.read which should suffice for most use cases ]
Steps to acquire Okta Oauth2 credentials:
- Acquire an Okta dev or user account with privileges to mint tokens with the * scopes.
- Log into your Okta account, navigate to Applications on the left-hand side, click on the Create App Integration button and create an API Services application.
- Click on the created app, note down the Client ID and select the option for Public key/Private key.
- Generate your own Private/Public key pair in the JWK format (PEM is not supported at the moment) and save it in a credentials JSON file or copy it to use directly in the config.
How do I configure On-premise AD identity data for LMNTRIX Identity IATDR?
Collects Identity events from your Active Directory by deploying LMNTRIX-Identity-Agent on each Active directory server.
What is the LMNTRIX Identity “Attack Paths”?
The Attack Paths module is designed to assess and analyze the security posture of Active Directory (AD) environments. By mapping out relationships and permissions within AD, Attack Paths enables security professionals to identify and visualize potential attack paths, privilege escalation vectors, and lateral movement opportunities.

Key features Attack Paths include:
- Attack Path Mapping: Attack Paths identifies and maps out potential attack paths within AD environments, helping users understand how attackers could compromise their network.
- Relationship Analysis: Attack Paths analyzes relationships between users, groups, computers, and other objects in AD to uncover security vulnerabilities and misconfigurations.
- Visualization: Attack Paths provides a graphical interface for visualizing the complex relationships and attack paths discovered during analysis, enhancing understanding and decision-making.
- Data Collection: Attack Paths collects data from AD environments using Attack Path sensor, a stealthy data collection tool designed to minimize its footprint and avoid detection by security monitoring tools.
- Custom Querying: Users can perform custom queries and analyses within Attack Paths to investigate specific aspects of their AD environment and identify security risks.
What are the use cases for LMNTRIX Identity “Attack Paths”?
- Security Assessment: Attack Paths is used to assess the security posture of AD environments, identifying vulnerabilities and weaknesses that could be exploited by attackers.
- Penetration Testing: Penetration testers leverage Attack Paths to simulate real-world attack scenarios, uncovering security flaws and evaluating the effectiveness of security controls.
- Red Teaming: Red Teamers use Attack Paths to perform comprehensive security assessments, testing the organization’s defenses and incident response procedures.
- Vulnerability Management: Attack Paths helps prioritize remediation efforts by identifying and prioritizing security vulnerabilities, misconfigurations, and excessive permissions within AD environments.
How do I deploy LMNTRIX Identity “Attack Paths”?
Attack Paths relies on a sensor for data collection from AD environments. Attack Paths sensor collects various types of data from AD environments, including information about users, groups, computers, permissions, and group memberships.
Pre-requisites:
- .Net Framework 4.0 or higher
- Need to run it on AD server.
- Open secure.lmntrix.com via 443 on firewall.
Installation Steps:
- Extract the AttackerPathsSensor.zip
- Open the command prompt in Administrator mode and redirect to the extracted folder path.
- Execute the command below to install the service on Windows Server. The installer will copy the required files in to into C:\Program Files\AttackerPathsSensor folder and create the windows service.
InstallSvc.cmd i (Refer below image)

Once the installation is completed. “AttackerPathsSensorSvc” windows service automatically starts.
Uninstallation Steps:
- Open the command prompt in Administrator mode and redirect to the installer folder path.
- Execute the command below to uninstall the service on windows server. Installer will stop the service and remove the files from c:\Program Files\AttackerPathsSensor folder and delete the folder as well.
InstallSvc.cmd u (Refer below image)

Why ChooseLMNTRIX Identity?
- Delivers capabilities beyond traditional IAM and MFA
- Uses deception and threat intelligence to detect attacks earlier
- Integrates with your identity stack—no rip and replace
- Combines detection, risk scoring, and automated response
- Backed by LMNTRIX’s expert Cyber Defense Center (CDC)

Related Resources
How We Protect
small and large enterprises
Why clients love working with LMNTRIX
You’re ready for advanced protection
and that means XDR







Don't just take our word for it...

Leader

Leader

Open Source Excellence

Top 250 MSSP Companies In The World

Users Choice Award
Top Rated Security



Ready to take the next steps with LMNTRIX MXDR ?
The choice is yours: see LMNTRIX in an on demand demo or set up a customized demo or request a quote.