LMNTRIX AAV™ - Automated Attack Validation
Continuously Simulate Real-World Attacks. Stay One Step Ahead.
The best defense is a good offense.
Why LMNTRIX AAV?
Proactive Risk Discovery

Actionable Intelligence, Not Just Reports
Affordable, Continuous Validation

On Your Schedule
Red Team Expertise On Demand
CoreCapabilities
Realistic AttackSimulation
Continuous& On-Demand Testing
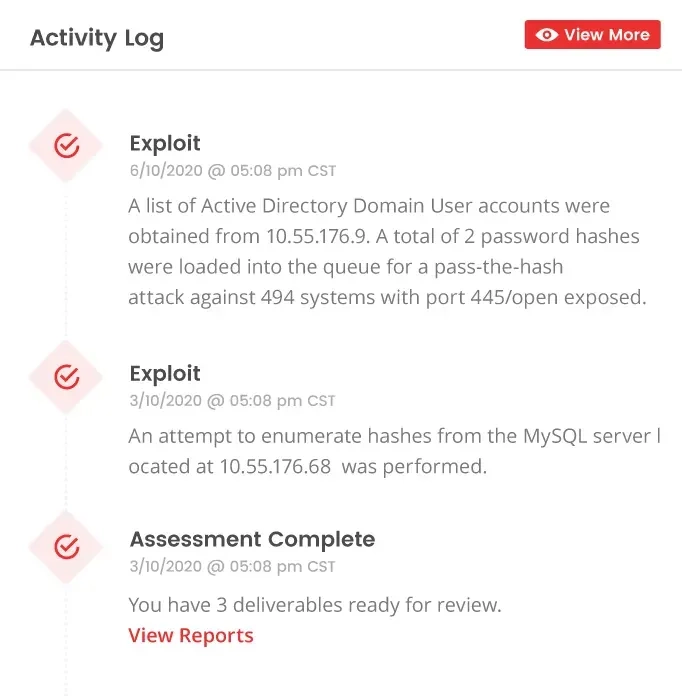
Safe Exploitation& Real-Time Monitoring
Service & Credential Discovery
Exfiltration & MITM Simulation
Comprehensive Reporting & Guidance
Purple Team Collaboration
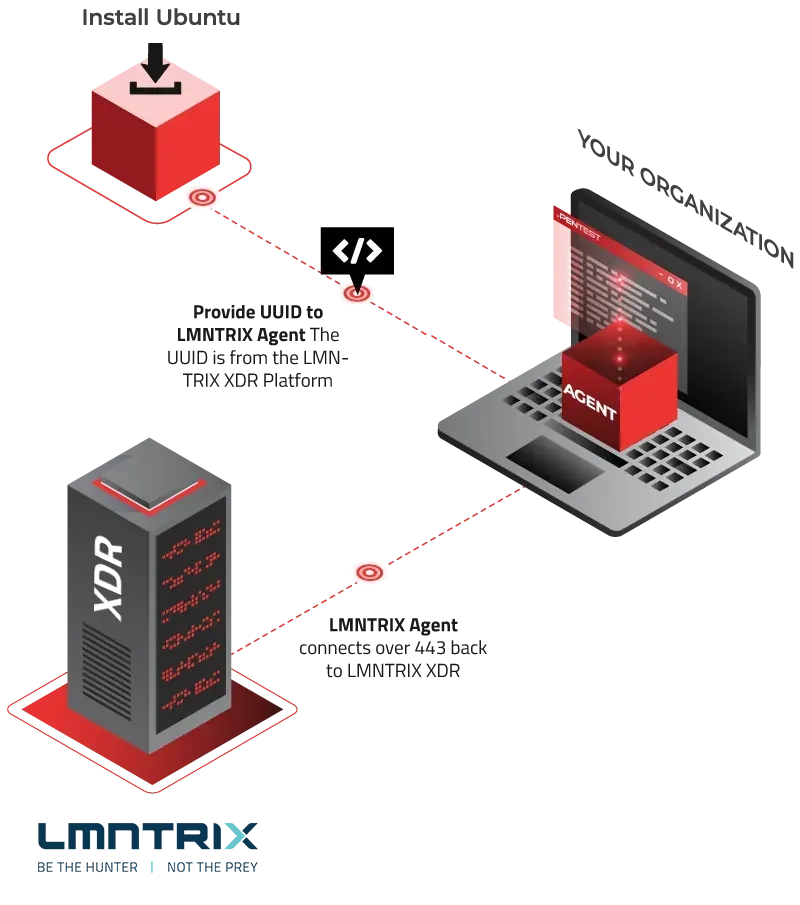
How ItWorks
Deploy Agent
Schedule Tests
Simulate Attacks
Correlate with SIEM
Remediate & Re-Test
Top Use Cases
- Continuous security posture validation
- Pre-audit compliance assurance (PCI DSS, ISO 27001, etc.)
- Purple teaming and SOC effectiveness assessment
- Cost-effective penetration test replacement
- Executive risk reporting and board visibility
Battle-Testedfor Every Environment
Whether you manage 5 or 5,000 IPs, LMNTRIX AAV is scalable and configurable to fit your architecture and risk appetite—ensuring that every critical asset is validated against real-world threats.
"We don’t wait for a breach to test defenses—we attack first so adversaries don’t get the chance."
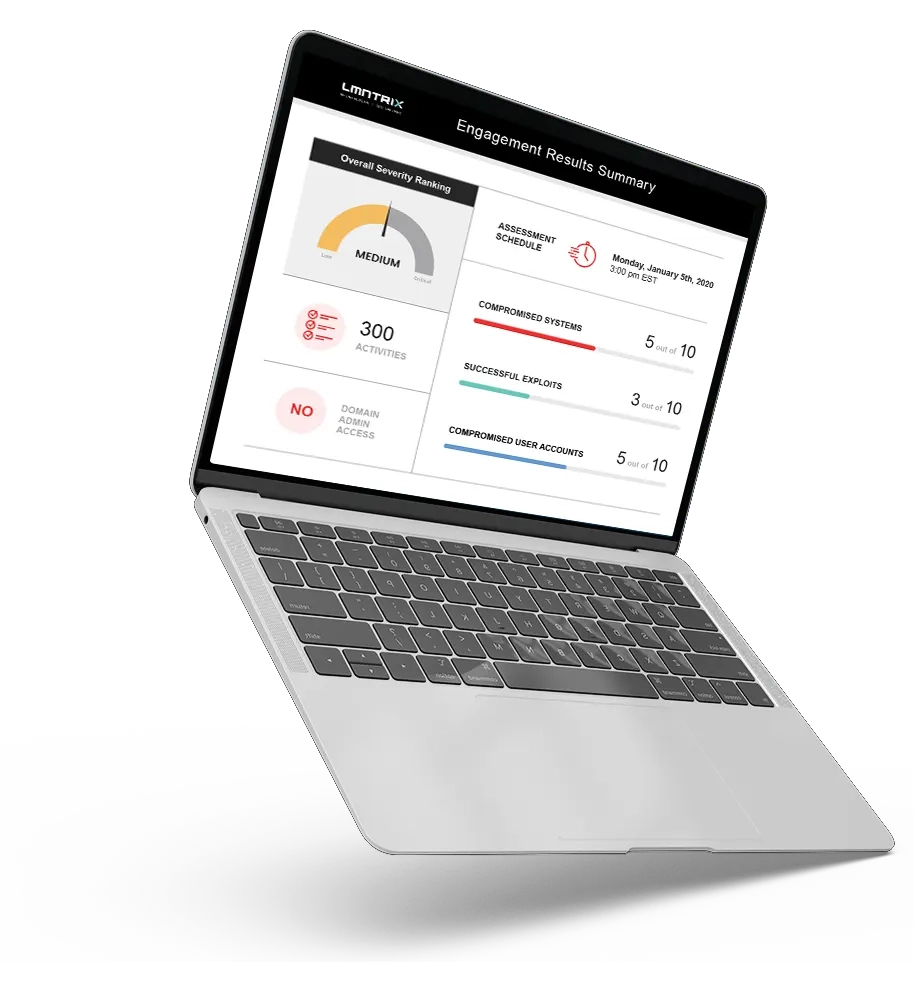
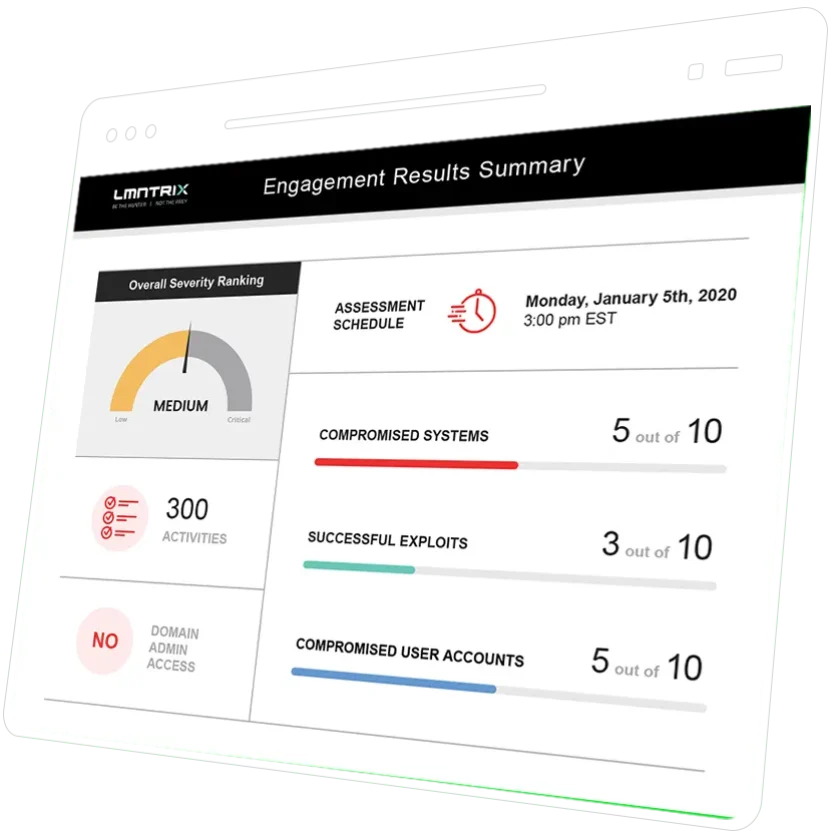
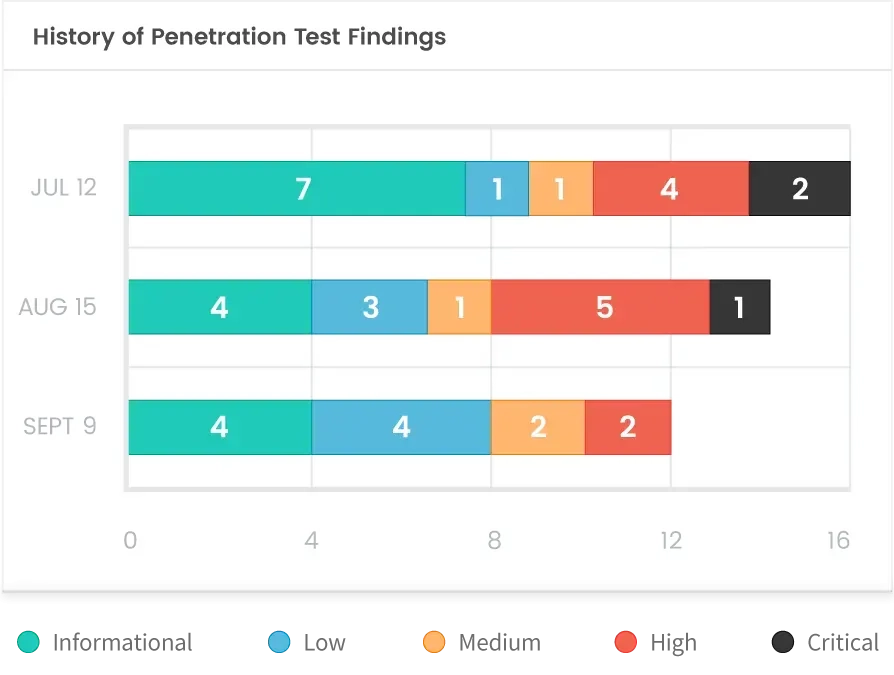
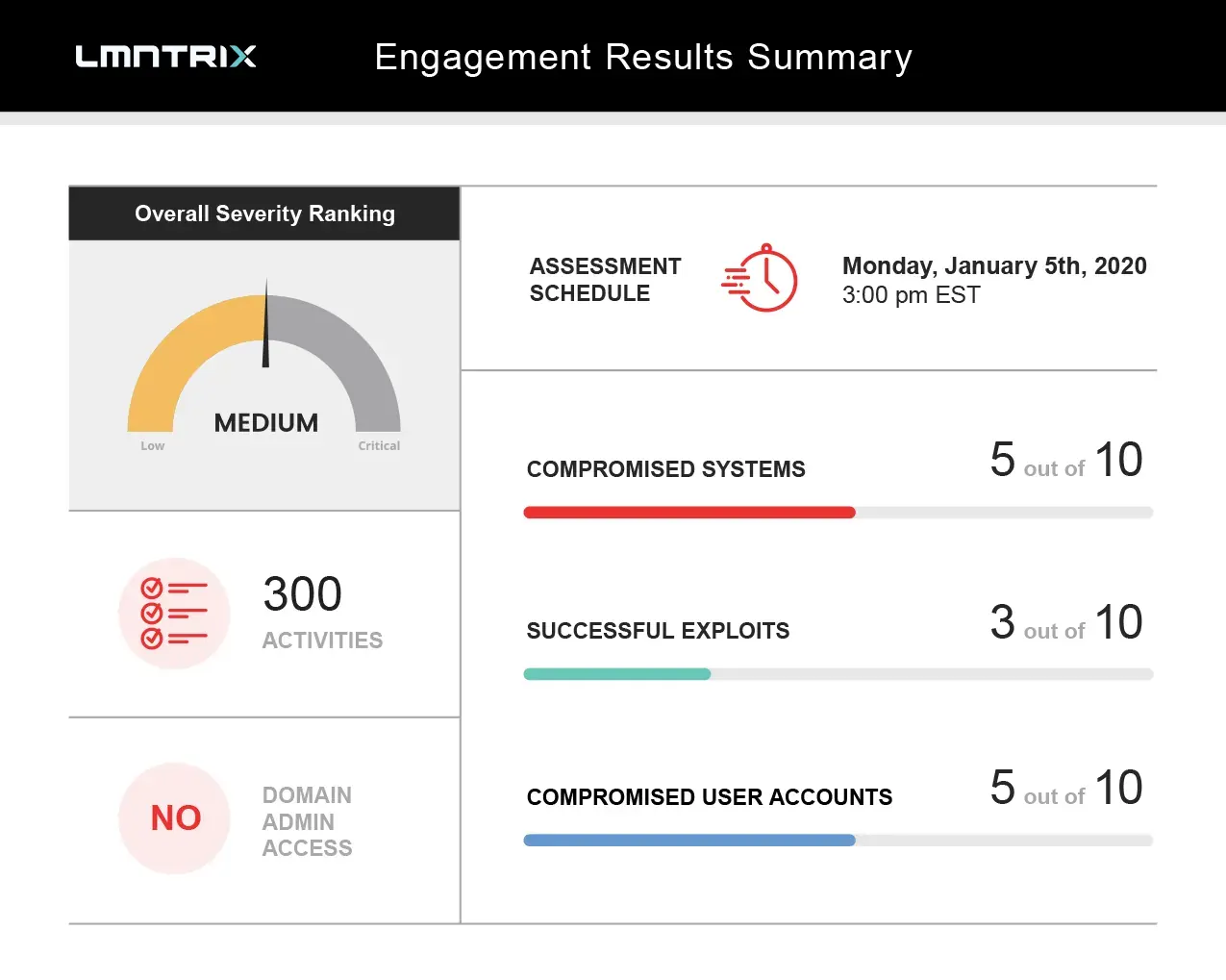
Quality Reportsto Share With the Team
LMNTRIX generates a report for you and your team to review within 48 hours after the penetration test is complete.
- Executive Summary
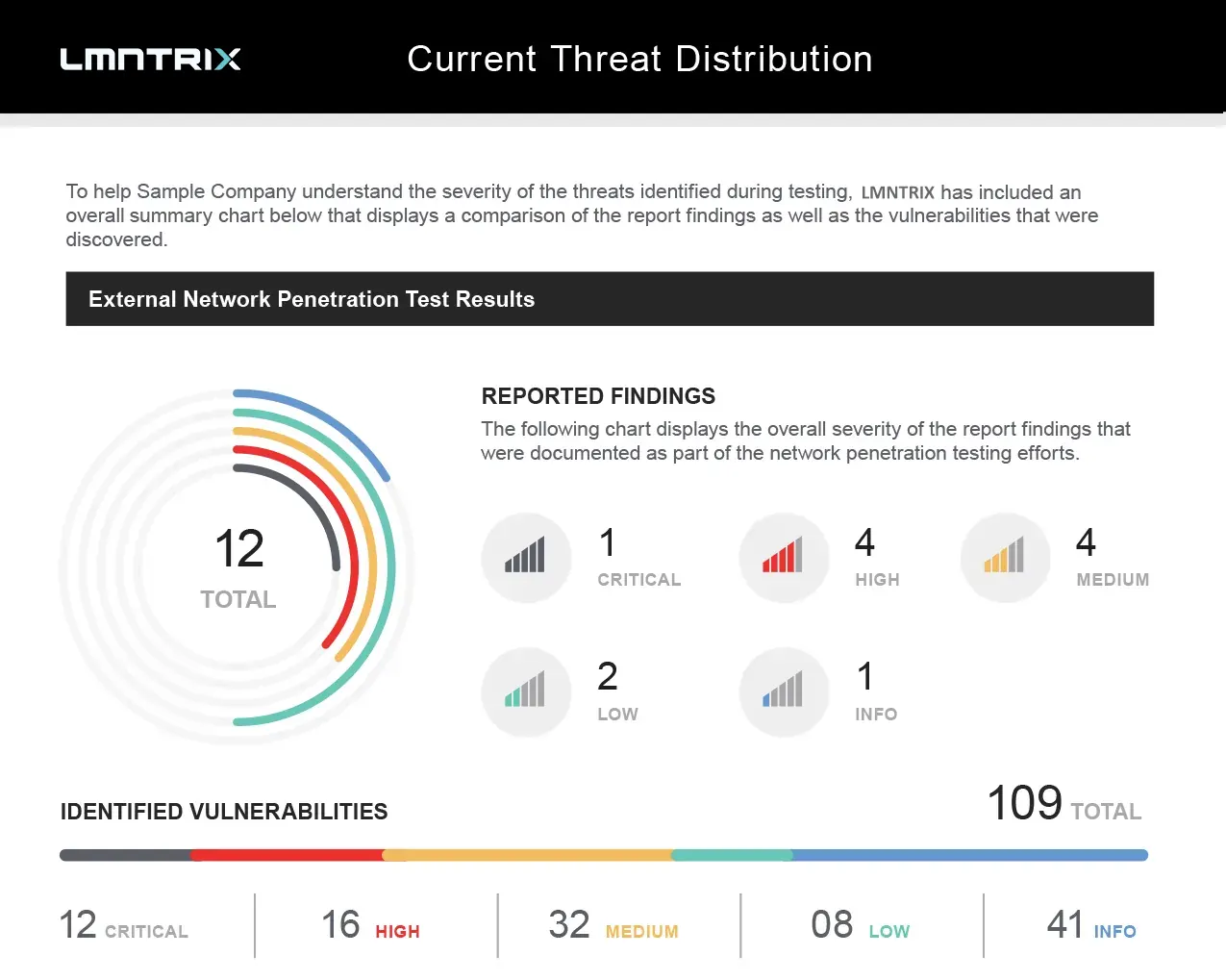
- Current Threat Distribution
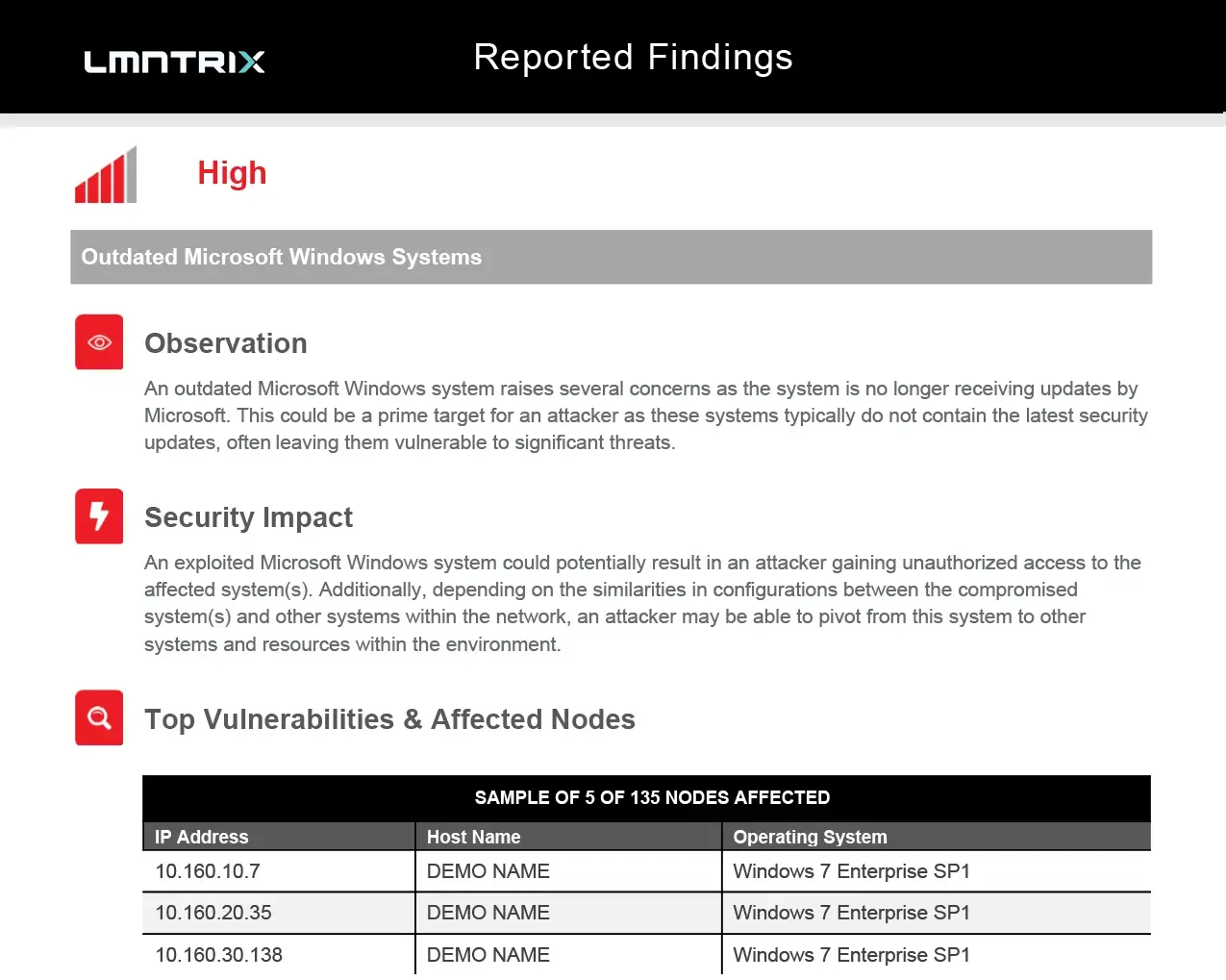
- Report Findings
Ready to Validate Your Defenses?
Schedule your first attack simulation and experience the power of continuous, automated penetration testing—backed by global expertise and 24/7 operational insight.
LMNTRIX AAV FAQs
Automated Attack Validation (AAV)
What is network penetration testing?
Network penetration testing is a security test where experts try to hack into an organization’s computer network to find vulnerabilities and weaknesses. It’s like a “mock” hack to see if a hacker could get in and cause damage. The goal is to identify any problems and fix them before a real hacker can take advantage. It’s basically a way to check the security of an organization’s network.
What is LMNTRIX AAV?
LMNTRIX AAV is a subscription feature of LMNTRIX XDR. LMNTRIX AAV is a scripted network penetration testing platform that runs the exact same steps and processes performed by a security consultant doing a live pentest. This includes technical tasks such as host discovery, service enumeration, vulnerability analysis, exploitation, post-exploitation, privilege escalation and lateral movement, as well as documentation and reporting.
LMNTRIX AAV combines the knowledge of multiple highly skilled penetration testers along with numerous tools and techniques used in the industry by penetration testers with over a decade of experience and certifications.
How does LMNTRIX AAV differ from a vulnerability assessment?
A vulnerability assessment simply informs an organization about the vulnerabilities that are present within its environment. However, a vulnerability assessment does not attempt to exploit those vulnerabilities to determine the potential impact of successfully exploiting those vulnerabilities. This is not a flaw with vulnerability scanners; they just simply aren’t designed to do this.
LMNTRIX AAV differs in that it is able to perform exploitation and post-exploitation techniques to demonstrate to customers how successfully exploiting a vulnerability could potentially lead to further access to systems and/or confidential data leakage within their environment.
What is the biggest difference between LMNTRIX AAV compared to a traditional network penetration test?
Traditional penetration tests are extremely time-consuming, whereas LMNTRIX AAV can run numerous tools simultaneously, wait for them to complete, automatically analyze the results, and determine its next move. This saves a significant amount of time from simply running one command at a time. Furthermore, LMNTRIX AAV reduces the time spent reporting from 6 hours (average between reporting, QA, etc.) to less than a minute. That’s a 29,900% speed increase per assessment that it saves.
What is involved in a network penetration test?
In network penetration tests, several attempts are made to exploit security vulnerabilities with the ultimate goal of gaining access to data and systems. These exploit attempts include targeting patching deficiencies, authentication weaknesses, misconfigurations, and even users (via man-in-the-middle attacks). After an initial compromise, post-exploitation activities occur, which typically include privilege escalation, lateral movement, and enumeration of accessible resources to find sensitive data.
What are the benefits of network penetration testing for an organization?
Some of the benefits of network penetration testing include the following:
- Prioritizing the remediation of critical security weaknesses
- Understanding how an attacker could gain access to sensitive data or systems
- Meeting compliance and regulatory requirements
- Testing and improving incident response procedures
- Validating the effectiveness of security controls
What kind of reports and deliverables can be expected from a network penetration test?
It is common to expect an executive summary, technical report, and a vulnerability report (or spreadsheet) as part of the final deliverables for a network penetration test. These reports are specifically tailored toward executive and technical audiences to help understand the risks that the environment poses to the organization
Does LMNTRIX AAV cover MITRE ATT&CK types?
The platform does indeed actually replicate some of the attacks documented in the MITRE ATT&CK framework, and the reporting structure includes references to the framework at the moment.
Are automated penetration testing tools as effective as manual penetration testing?
While automated tools provide faster and more consistent results, manual testing may uncover complex vulnerabilities that automated tools might miss. A combined approach often provides the best results specially where web application or API testing is required.
How often should automated penetration testing be performed?
Automated penetration testing can be conducted on a continuous or periodic basis. Many organizations choose to run tests weekly or monthly to maintain up-to-date vulnerability assessments.
How is LMNTRIX AAV priced?
LMNTRIX AAV is priced according to the total number of internal and external IPs to be tested at any one time. IPs reset each month until the end of the subscription. Unused IPs do not roll over to the following month or subscription. Clients can upgrade to the next IP block during the first 10 months of their subscription and only pay the difference. Each assessment consumes IPs and will automatically deduct from the allocated monthly IP count until the reset date.
Can LMNTRIX AAV integrate with other security tools?
Yes, LMNTRIX AAV offers integration with popular SIEMs, ticketing systems, and other security tools to streamline workflows.
Does LMNTRIX AAV support internal and external network testing?
Yes, LMNTRIX AAV can test both internal and external networks, allowing organizations to identify vulnerabilities from both an insider and outsider perspective.
What is the reporting process like for LMNTRIX AAV?
LMNTRIX AAV provides comprehensive reports that include vulnerability details, impact assessment, and remediation suggestions. Reports are generated in various formats for easy sharing and compliance.
Can LMNTRIX AAV perform post-exploitation activities?
Yes, LMNTRIX AAV includes post-exploitation capabilities, which allow it to simulate data exfiltration, privilege escalation, and lateral movement to understand the potential impact of vulnerabilities.
How does LMNTRIX AAV ensure that automated testing doesn’t disrupt normal business operations?
LMNTRIX AAV uses safe testing methods and configurable settings to minimize the risk of disruption, allowing organizations to control the intensity and scope of tests.
Is it possible to customize attack scenarios in LMNTRIX AAV?
Yes, LMNTRIX AAV allows users to customize attack scenarios and adjust the scope of the testing to focus on specific environments or assets.
What are the key requirements for deploying LMNTRIX AAV in an organization?
LMNTRIX AAV requires minimal setup, typically involving a virtual appliance or cloud-based deployment, and access permissions to relevant network segments.
Does LMNTRIX AAV support cloud environment testing?
Yes, LMNTRIX AAV can perform penetration testing across cloud environments, identifying vulnerabilities in services such as AWS, Azure, and Google Cloud Platform.
How does LMNTRIX AAV prioritize vulnerabilities?
LMNTRIX AAV uses risk scoring based on factors such as exploitability, impact, and severity to prioritize vulnerabilities in its reports.
Can LMNTRIX AAV conduct automated social engineering attacks?
No. LMNTRIX AAV focuses primarily on technical vulnerabilities, it cannot simulate social engineering as part of its broader attack scenarios.
How does automated penetration testing help with regulatory compliance?
Automated testing can help organizations meet compliance requirements by providing consistent vulnerability assessments and detailed reports for standards like PCI-DSS, HIPAA, and GDPR.
Is it safe to use automated penetration testing in a live production environment?
While automated tools aim to be non-disruptive, it’s recommended to perform tests during low-traffic periods or in a staging environment when possible to minimize risks.
Can automated penetration testing tools identify zero-day vulnerabilities?
Automated tools are generally effective at detecting known vulnerabilities; however, they may not be able to identify unknown (zero-day) vulnerabilities without updated exploit libraries.
Does LMNTRIX AAV offer role-based access control (RBAC)?
Yes, LMNTRIX AAV includes RBAC features to ensure that only authorized personnel can access sensitive test results and configuration settings.
Can automated penetration testing tools replace vulnerability scanners?
Automated penetration testing tools offer more comprehensive assessments by simulating actual attacks, while vulnerability scanners typically identify vulnerabilities without attempting exploitation. Both tools complement each other.
How does LMNTRIX AAV handle sensitive data encountered during testing?
LMNTRIX AAV adheres to data protection best practices, ensuring that sensitive information is handled securely and that test data is stored and encrypted according to industry standards.
Is it possible to schedule recurring tests with LMNTRIX AAV?
Yes, LMNTRIX AAV supports scheduled testing, allowing organizations to run penetration tests on a recurring basis, such as weekly, monthly, or quarterly.
What steps should organizations take after receiving an automated penetration testing report?
After a test, organizations should review the findings, prioritize remediation based on risk, and apply recommended fixes. Retesting can be performed to verify that vulnerabilities are resolved.
How do automated penetration testing tools compare to red teaming exercises?
Automated tools focus on finding technical vulnerabilities, while red teaming includes social engineering and operational tactics. Red teaming services such as the LMNTRIX Red Teaming involves more comprehensive and creative attack simulations.
What training is needed to use automated penetration testing tools like LMNTRIX AAV?
These tools are designed to be user-friendly, with intuitive interfaces and detailed documentation. Basic cybersecurity knowledge is helpful, but extensive training is usually not required for standard operation.
Related Resources

Automated Attack Validation Buyer’s Guide
White Paper

LMNTRIX AAV - The best defense is a good offense.
Presentation

Automated Attack Validation - Datasheet
Datasheet
How We Protect
small and large enterprises
Why clients love working with LMNTRIX
You’re ready for advanced protection
and that means XDR







Don't just take our word for it...

Leader

Leader

Open Source Excellence

Top 250 MSSP Companies In The World

Users Choice Award
Top Rated Security



Ready to take the next steps with LMNTRIX MXDR ?
The choice is yours: see LMNTRIX in an on demand demo or set up a customized demo or request a quote.